Static Route VS Outbound
-
@bambos
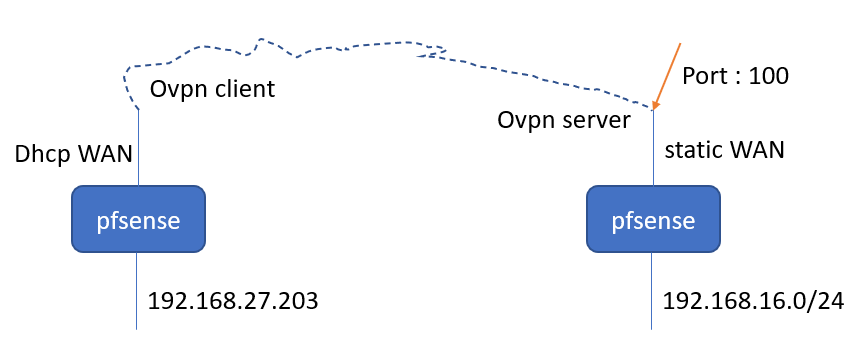
On the server you have only to forward the port 100 to 192.168.27.203. So it should pass over the VPN.On the client side you have to assign an interface to the OpenVPN client instance, if you didn't already do that.
Move the firewall rule from the OpenVPN tab over to the new VPN interface to allow the incoming traffic.
There must be no rule on the OpenVPN tab and no floating rule matching the forwarded traffic. -
@viragomann It seems that it's also needed to add an outbound rule on the server, for accessing the network 192.168.27.0/24 through the virtual interface of open VPN. Is not routing without that.
-
Why would you be forwarding anything if you have a site to site vpn?
There is no need to port forward in such a setup. All that would be needed is firewall rule to allow the traffic.
You say your site to site is working fine, so why are you wanting to port forward anything off the wan IPs? to get to something that should route through your vpn without any nat anyway..
-
@bambos said in Static Route VS Outbound:
It seems that it's also needed to add an outbound rule on the server, for accessing the network 192.168.27.0/24 through the virtual interface of open VPN. Is not routing without that.
No, if you obey strictly my suggestions, this is not necessary.
-
@johnpoz Hello and good morning,
I have an engineer from another country need to access the device on 192.168.27.203.
Since there is no static ip on the client WAN, the only static ip i have is on the WAN of the server. I hope that answering your question.
So i'm looking for a way to access this through the server. -
@viragomann i would try that. What rule i have to put on VPN Interface ? (There is already interface enabled since the site to site setup). Does it have to be allow the port, or allow all ?
-
@bambos
As I stated above, there must not be any pass rule on the OpenVPN tab and not any floating rule matching the forwarded traffic on the client.
You have to assign an interface to the OpenVPN client and add the proper pass rule there. It doesn't matter if this rule allows only the certain port or allow any. -
@bambos said in Static Route VS Outbound:
I hope that answering your question.
No - what does it matter what the wan IP is? Be it you have a site to site, or just a road warrior vpn even. There would be NO need for any sort of port forward.
What exactly are you accessing via this site to site, since you stated its working..
A site to site would route traffic for the different sites networks over the vpn, there would be no reason for any natting, if no natting - no port forward needed.
-
@johnpoz yes, you are right and we agree (if the user is connected to the LAN 16.)
In this case, we are talking about external user over internet.
The site to site is between the 2 LAN's 16 and 27. Both pfsense have routing to each other with no problem.
-
@bambos said in Static Route VS Outbound:
In this case, we are talking about external user over internet.
If the user is external, then the vpn does not come into play. If user X out on the internet vpns into site A, he would be able to route traffic over the vpn to site B, again no port forward needed.
You would just need to setup routing via the vpn to get to the tunnel network of say the road warrior connection to site A.
-
@johnpoz Thank you Sir. Well noted. To my understanding you reffering to a case when the outside user accessing through remote access VPN as client on the server. Right ?
-
Doesn't matter where the external user vpns into be it site A or site B. You can setup routing over the s2s vpn so that any remote client could access either site A or site B networks no matter which site they vpn into.
-
@viragomann Great is working as you described !! thanks a lot.
Now i'm just questioning my self, when the autocreated openVPN tab has to get a rule and why ?
-
The OpenVPN tab is an interface group including all OpenVPN instances you're are running on the box, clients and servers as well. It is created by pfSense, when you set up the first OpenVPN to handle the traffic simply.
But what you need here is the reply-to flag of pfSense. This needs to have a pass rule on a unique interface, so that it sees a distinct gateway, where responses have to be replied back. Therefor the reply-to doesn't work on interface group or floating rules.
-
@viragomann Good, thanks a lot for your support.
What about remote access open vpn instance on the server ? Does this need a rule on the OpenVPN tab ? or again needs an interface ?
-
@bambos
Best practice is to assign an interface to each OpenVPN instance in this case. So each rule hase clear mapping.
However, basically you may also assign rules to the OpenVPN tab which are applied to all OpenVPN instances then, but in any case you have to care that there is no rule matching the forwarded traffic you need to reply to the remote site.
So you may add a pass rule excluding port 100 in your example. -
@viragomann thank you very much Sir. You gave me hints to play more with some things now. I have some things to redo for test. No sleep tonight :)
-
@johnpoz Thanks for explaining everything. I tried what you suggested and is succesful. The only thing was that the remote user, couldn't been able to connect through a VPN Client, that's why i make it short term access using port 100. ok, now it's clear.