Ikev2 vpn with windows 10
-
Hello,
really sorry to bother with such basic thing for you guys. I am new user of pfsense. I am trying it out before buying the hardware model. For testes i installed it in a vsphere VM.
I wanted to check functionality for vpn.
I failed setting up l2tp/psk , no idea how to do that i tried few tutorials from internet but it still does not work.
Then i tried this tutorial
https://blog.andreev.it/?p=3617#Android_6x_Marshmallow
for ikev2 vpn and this looks quite ok. I did it at my friends setup where his client was macOS, its working fine there.
In my scenario i use windows 10 20H2 as the client and vpn is established, but i can't ping neither the internet nor the client on the vpn lan side.
Could anyone help me troubleshoot/fix this ?
After connecting to the VPN my windows route table looks like this:For vpn network i gave: 192.168.40.0 /24 IPv4 Route Table =========================================================================== Active Routes: Network Destination Netmask Gateway Interface Metric 0.0.0.0 0.0.0.0 192.168.111.1 192.168.111.254 4496 0.0.0.0 0.0.0.0 On-link 192.168.40.1 26 127.0.0.0 255.0.0.0 On-link 127.0.0.1 4556 127.0.0.1 255.255.255.255 On-link 127.0.0.1 4556 127.255.255.255 255.255.255.255 On-link 127.0.0.1 4556 192.168.40.1 255.255.255.255 On-link 192.168.40.1 281 192.168.81.0 255.255.255.0 On-link 192.168.81.1 4516 192.168.81.1 255.255.255.255 On-link 192.168.81.1 4516 192.168.81.255 255.255.255.255 On-link 192.168.81.1 4516 192.168.111.0 255.255.255.0 On-link 192.168.111.254 4496 192.168.111.218 255.255.255.255 On-link 192.168.111.254 4241 192.168.111.254 255.255.255.255 On-link 192.168.111.254 4496 192.168.111.255 255.255.255.255 On-link 192.168.111.254 4496 224.0.0.0 240.0.0.0 On-link 127.0.0.1 4556 224.0.0.0 240.0.0.0 On-link 192.168.81.1 4516 224.0.0.0 240.0.0.0 On-link 192.168.111.254 4496 224.0.0.0 240.0.0.0 On-link 192.168.40.1 26 255.255.255.255 255.255.255.255 On-link 127.0.0.1 4556 255.255.255.255 255.255.255.255 On-link 192.168.81.1 4516 255.255.255.255 255.255.255.255 On-link 192.168.111.254 4496 255.255.255.255 255.255.255.255 On-link 192.168.40.1 281 =========================================================================== Persistent Routes: Network Address Netmask Gateway Address Metric 0.0.0.0 0.0.0.0 192.168.111.1 Default ===========================================================================
LAN 192.168.26.1
WAN 192.168.111.218 // dhcp
Windows client ip 192.168.111.254can't ping
ping 8.8.8.8Pinging 8.8.8.8 with 32 bytes of data:
Request timed out.
Request timed out.can't ping interal server in LAN of pfsense
192.168.26.10 is another vm in portgroup with lan of pfsense. this vm can ping internet as it uses 192.168.26.1(pfsense lan) ip as GW.I checked this :
https://forum.netgate.com/topic/106511/ikev2-successfully-connects-but-doesn-t-route-traffic-through-tunnel/3Name : VPN2HOME
ServerAddress : 192.168.111.218
AllUserConnection : False
Guid : {809F789F-FC06-4668-939C-27DBF7694906}
TunnelType : Ikev2
AuthenticationMethod : {Eap}
EncryptionLevel : Custom
L2tpIPsecAuth :
UseWinlogonCredential : False
EapConfigXmlStream : #document
ConnectionStatus : Disconnected
RememberCredential : False
SplitTunneling : False
DnsSuffix :
IdleDisconnectSeconds : 0But this is already ok.
log from pfsense:==> ipsec.log <== May 31 22:13:34 pfsense charon[63100]: 11[IKE] <con-mobile|27> sending DPD request May 31 22:13:34 pfsense charon[63100]: 11[IKE] <con-mobile|27> queueing IKE_DPD task May 31 22:13:34 pfsense charon[63100]: 11[IKE] <con-mobile|27> activating new tasks May 31 22:13:34 pfsense charon[63100]: 11[IKE] <con-mobile|27> activating IKE_DPD task May 31 22:13:34 pfsense charon[63100]: 11[ENC] <con-mobile|27> generating INFORMATIONAL request 0 [ ] May 31 22:13:34 pfsense charon[63100]: 11[NET] <con-mobile|27> sending packet: from 192.168.111.218[4500] to 192.168.111.254[4500] (80 bytes) May 31 22:13:34 pfsense charon[63100]: 11[NET] <con-mobile|27> received packet: from 192.168.111.254[4500] to 192.168.111.218[4500] (80 bytes) May 31 22:13:34 pfsense charon[63100]: 11[ENC] <con-mobile|27> parsed INFORMATIONAL response 0 [ ] May 31 22:13:34 pfsense charon[63100]: 11[IKE] <con-mobile|27> activating new tasks May 31 22:13:34 pfsense charon[63100]: 11[IKE] <con-mobile|27> nothing to initiate May 31 22:13:35 pfsense charon[63100]: 11[NET] <con-mobile|27> received packet: from 192.168.111.254[4500] to 192.168.111.218[4500] (80 bytes) May 31 22:13:35 pfsense charon[63100]: 11[ENC] <con-mobile|27> parsed INFORMATIONAL request 6 [ D ] May 31 22:13:35 pfsense charon[63100]: 11[IKE] <con-mobile|27> received DELETE for ESP CHILD_SA with SPI 45877e0a May 31 22:13:35 pfsense charon[63100]: 11[IKE] <con-mobile|27> closing CHILD_SA con-mobile{10} with SPIs c056fdcc_i (0 bytes) 45877e0a_o (0 bytes) and TS 0.0.0.0/24|/0 === 192.168.40.1/32|/0 May 31 22:13:35 pfsense charon[63100]: 11[IKE] <con-mobile|27> sending DELETE for ESP CHILD_SA with SPI c056fdcc May 31 22:13:35 pfsense charon[63100]: 11[CHD] <con-mobile|27> CHILD_SA con-mobile{10} state change: INSTALLED => DELETING May 31 22:13:35 pfsense charon[63100]: 11[IKE] <con-mobile|27> CHILD_SA closed May 31 22:13:35 pfsense charon[63100]: 11[CHD] <con-mobile|27> CHILD_SA con-mobile{10} state change: DELETING => DELETED May 31 22:13:35 pfsense charon[63100]: 11[CHD] <con-mobile|27> CHILD_SA con-mobile{10} state change: DELETED => DESTROYING May 31 22:13:35 pfsense charon[63100]: 11[ENC] <con-mobile|27> generating INFORMATIONAL response 6 [ D ] May 31 22:13:35 pfsense charon[63100]: 11[NET] <con-mobile|27> sending packet: from 192.168.111.218[4500] to 192.168.111.254[4500] (80 bytes) May 31 22:13:35 pfsense charon[63100]: 16[NET] <con-mobile|27> received packet: from 192.168.111.254[4500] to 192.168.111.218[4500] (80 bytes) May 31 22:13:35 pfsense charon[63100]: 16[ENC] <con-mobile|27> parsed INFORMATIONAL request 7 [ D ] May 31 22:13:35 pfsense charon[63100]: 16[IKE] <con-mobile|27> received DELETE for IKE_SA con-mobile[27] May 31 22:13:35 pfsense charon[63100]: 16[IKE] <con-mobile|27> deleting IKE_SA con-mobile[27] between 192.168.111.218[192.168.111.218]...192.168.111.254[192.168.111.254] May 31 22:13:35 pfsense charon[63100]: 16[IKE] <con-mobile|27> IKE_SA con-mobile[27] state change: ESTABLISHED => DELETING May 31 22:13:35 pfsense charon[63100]: 16[IKE] <con-mobile|27> IKE_SA deleted May 31 22:13:35 pfsense charon[63100]: 16[ENC] <con-mobile|27> generating INFORMATIONAL response 7 [ ] May 31 22:13:35 pfsense charon[63100]: 16[NET] <con-mobile|27> sending packet: from 192.168.111.218[4500] to 192.168.111.254[4500] (80 bytes) May 31 22:13:35 pfsense charon[63100]: 16[IKE] <con-mobile|27> IKE_SA con-mobile[27] state change: DELETING => DESTROYING May 31 22:13:35 pfsense charon[63100]: 16[CFG] <con-mobile|27> lease 192.168.40.1 by 'gregzon' went offline May 31 22:13:43 pfsense charon[63100]: 16[NET] <28> received packet: from 192.168.111.254[500] to 192.168.111.218[500] (544 bytes) May 31 22:13:43 pfsense charon[63100]: 16[ENC] <28> parsed IKE_SA_INIT request 0 [ SA KE No N(FRAG_SUP) N(NATD_S_IP) N(NATD_D_IP) V V V V ] May 31 22:13:43 pfsense charon[63100]: 16[CFG] <28> looking for an IKEv2 config for 192.168.111.218...192.168.111.254 May 31 22:13:43 pfsense charon[63100]: 16[CFG] <28> candidate: 192.168.111.218...0.0.0.0/0, ::/0, prio 1052 May 31 22:13:43 pfsense charon[63100]: 16[CFG] <28> found matching ike config: 192.168.111.218...0.0.0.0/0, ::/0 with prio 1052 May 31 22:13:43 pfsense charon[63100]: 16[IKE] <28> received MS NT5 ISAKMPOAKLEY v9 vendor ID May 31 22:13:43 pfsense charon[63100]: 16[IKE] <28> received MS-Negotiation Discovery Capable vendor ID May 31 22:13:43 pfsense charon[63100]: 16[IKE] <28> received Vid-Initial-Contact vendor ID May 31 22:13:43 pfsense charon[63100]: 16[ENC] <28> received unknown vendor ID: 01:52:8b:bb:c0:06:96:12:18:49:ab:9a:1c:5b:2a:51:00:00:00:02 May 31 22:13:43 pfsense charon[63100]: 16[IKE] <28> 192.168.111.254 is initiating an IKE_SA May 31 22:13:43 pfsense charon[63100]: 16[IKE] <28> IKE_SA (unnamed)[28] state change: CREATED => CONNECTING May 31 22:13:43 pfsense charon[63100]: 16[CFG] <28> selecting proposal: May 31 22:13:43 pfsense charon[63100]: 16[CFG] <28> no acceptable ENCRYPTION_ALGORITHM found May 31 22:13:43 pfsense charon[63100]: 16[CFG] <28> selecting proposal: May 31 22:13:43 pfsense charon[63100]: 16[CFG] <28> no acceptable ENCRYPTION_ALGORITHM found May 31 22:13:43 pfsense charon[63100]: 16[CFG] <28> selecting proposal: May 31 22:13:43 pfsense charon[63100]: 16[CFG] <28> no acceptable INTEGRITY_ALGORITHM found May 31 22:13:43 pfsense charon[63100]: 16[CFG] <28> selecting proposal: May 31 22:13:43 pfsense charon[63100]: 16[CFG] <28> proposal matches May 31 22:13:43 pfsense charon[63100]: 16[CFG] <28> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 May 31 22:13:43 pfsense charon[63100]: 16[CFG] <28> configured proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 May 31 22:13:43 pfsense charon[63100]: 16[CFG] <28> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 May 31 22:13:43 pfsense charon[63100]: 16[IKE] <28> sending cert request for "CN=internal-ca, C=NL, ST=NH, L=Hoofddorp, O=xDlabs, OU=Infra" May 31 22:13:43 pfsense charon[63100]: 16[ENC] <28> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(CHDLESS_SUP) N(MULT_AUTH) ] May 31 22:13:43 pfsense charon[63100]: 16[NET] <28> sending packet: from 192.168.111.218[500] to 192.168.111.254[500] (481 bytes) May 31 22:13:43 pfsense charon[63100]: 16[NET] <28> received packet: from 192.168.111.254[4500] to 192.168.111.218[4500] (580 bytes) May 31 22:13:43 pfsense charon[63100]: 16[ENC] <28> parsed IKE_AUTH request 1 [ EF(1/4) ] May 31 22:13:43 pfsense charon[63100]: 16[ENC] <28> received fragment #1 of 4, waiting for complete IKE message May 31 22:13:43 pfsense charon[63100]: 16[NET] <28> received packet: from 192.168.111.254[4500] to 192.168.111.218[4500] (580 bytes) May 31 22:13:43 pfsense charon[63100]: 16[ENC] <28> parsed IKE_AUTH request 1 [ EF(3/4) ] May 31 22:13:43 pfsense charon[63100]: 16[ENC] <28> received fragment #3 of 4, waiting for complete IKE message May 31 22:13:43 pfsense charon[63100]: 16[NET] <28> received packet: from 192.168.111.254[4500] to 192.168.111.218[4500] (244 bytes) May 31 22:13:43 pfsense charon[63100]: 16[ENC] <28> parsed IKE_AUTH request 1 [ EF(4/4) ] May 31 22:13:43 pfsense charon[63100]: 16[ENC] <28> received fragment #4 of 4, waiting for complete IKE message May 31 22:13:43 pfsense charon[63100]: 07[NET] <28> received packet: from 192.168.111.254[4500] to 192.168.111.218[4500] (580 bytes) May 31 22:13:43 pfsense charon[63100]: 07[ENC] <28> parsed IKE_AUTH request 1 [ EF(2/4) ] May 31 22:13:43 pfsense charon[63100]: 07[ENC] <28> received fragment #2 of 4, reassembled fragmented IKE message (1728 bytes) May 31 22:13:43 pfsense charon[63100]: 07[ENC] <28> parsed IKE_AUTH request 1 [ IDi CERTREQ N(MOBIKE_SUP) CPRQ(ADDR DNS NBNS SRV ADDR6 DNS6 SRV6) SA TSi TSr ] May 31 22:13:43 pfsense charon[63100]: 07[IKE] <28> received cert request for unknown ca with keyid 4a:5c:75:22:aa:46:bf:a4:08:9d:39:97:4e:bd:b4:a3:60:f7:a0:1d May 31 22:13:43 pfsense charon[63100]: 07[IKE] <28> received cert request for "CN=internal-ca, C=NL, ST=NH, L=Hoofddorp, O=xDlabs, OU=Infra" May 31 22:13:43 pfsense charon[63100]: 07[IKE] <28> received cert request for unknown ca with keyid 5c:b8:69:fe:8d:ef:c1:ed:66:27:ee:b2:12:0f:72:1b:b8:0a:0e:04 May 31 22:13:43 pfsense charon[63100]: 07[IKE] <28> received cert request for "CN=pfsense.greg.labs, C=NL, ST=NH, L=Hoofddorp, O=xDlabs, OU=Infra" May 31 22:13:43 pfsense charon[63100]: 07[IKE] <28> received 69 cert requests for an unknown ca May 31 22:13:43 pfsense charon[63100]: 07[CFG] <28> looking for peer configs matching 192.168.111.218[%any]...192.168.111.254[192.168.111.254] May 31 22:13:43 pfsense charon[63100]: 07[CFG] <28> candidate "con-mobile", match: 1/1/1052 (me/other/ike) May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> selected peer config 'con-mobile' May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> initiating EAP_IDENTITY method (id 0x00) May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> processing INTERNAL_IP4_ADDRESS attribute May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> processing INTERNAL_IP4_DNS attribute May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> processing INTERNAL_IP4_NBNS attribute May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> processing INTERNAL_IP4_SERVER attribute May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> processing INTERNAL_IP6_ADDRESS attribute May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> processing INTERNAL_IP6_DNS attribute May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> processing INTERNAL_IP6_SERVER attribute May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> peer supports MOBIKE, but disabled in config May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> authentication of '192.168.111.218' (myself) with RSA signature successful May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> sending end entity cert "CN=pfsense.greg.labs, C=NL, ST=NH, L=Hoofddorp, O=xDlabs, OU=Infra" May 31 22:13:43 pfsense charon[63100]: 07[ENC] <con-mobile|28> generating IKE_AUTH response 1 [ IDr CERT AUTH EAP/REQ/ID ] May 31 22:13:43 pfsense charon[63100]: 07[ENC] <con-mobile|28> splitting IKE message (1568 bytes) into 2 fragments May 31 22:13:43 pfsense charon[63100]: 07[ENC] <con-mobile|28> generating IKE_AUTH response 1 [ EF(1/2) ] May 31 22:13:43 pfsense charon[63100]: 07[ENC] <con-mobile|28> generating IKE_AUTH response 1 [ EF(2/2) ] May 31 22:13:43 pfsense charon[63100]: 07[NET] <con-mobile|28> sending packet: from 192.168.111.218[4500] to 192.168.111.254[4500] (1236 bytes) May 31 22:13:43 pfsense charon[63100]: 07[NET] <con-mobile|28> sending packet: from 192.168.111.218[4500] to 192.168.111.254[4500] (404 bytes) May 31 22:13:43 pfsense charon[63100]: 07[NET] <con-mobile|28> received packet: from 192.168.111.254[4500] to 192.168.111.218[4500] (96 bytes) May 31 22:13:43 pfsense charon[63100]: 07[ENC] <con-mobile|28> parsed IKE_AUTH request 2 [ EAP/RES/ID ] May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> received EAP identity 'gregzon' May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> initiating EAP_MSCHAPV2 method (id 0x9E) May 31 22:13:43 pfsense charon[63100]: 07[ENC] <con-mobile|28> generating IKE_AUTH response 2 [ EAP/REQ/MSCHAPV2 ] May 31 22:13:43 pfsense charon[63100]: 07[NET] <con-mobile|28> sending packet: from 192.168.111.218[4500] to 192.168.111.254[4500] (112 bytes) May 31 22:13:43 pfsense charon[63100]: 07[NET] <con-mobile|28> received packet: from 192.168.111.254[4500] to 192.168.111.218[4500] (144 bytes) May 31 22:13:43 pfsense charon[63100]: 07[ENC] <con-mobile|28> parsed IKE_AUTH request 3 [ EAP/RES/MSCHAPV2 ] May 31 22:13:43 pfsense charon[63100]: 07[ENC] <con-mobile|28> generating IKE_AUTH response 3 [ EAP/REQ/MSCHAPV2 ] May 31 22:13:43 pfsense charon[63100]: 07[NET] <con-mobile|28> sending packet: from 192.168.111.218[4500] to 192.168.111.254[4500] (144 bytes) May 31 22:13:43 pfsense charon[63100]: 07[NET] <con-mobile|28> received packet: from 192.168.111.254[4500] to 192.168.111.218[4500] (80 bytes) May 31 22:13:43 pfsense charon[63100]: 07[ENC] <con-mobile|28> parsed IKE_AUTH request 4 [ EAP/RES/MSCHAPV2 ] May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> EAP method EAP_MSCHAPV2 succeeded, MSK established May 31 22:13:43 pfsense charon[63100]: 07[ENC] <con-mobile|28> generating IKE_AUTH response 4 [ EAP/SUCC ] May 31 22:13:43 pfsense charon[63100]: 07[NET] <con-mobile|28> sending packet: from 192.168.111.218[4500] to 192.168.111.254[4500] (80 bytes) May 31 22:13:43 pfsense charon[63100]: 07[NET] <con-mobile|28> received packet: from 192.168.111.254[4500] to 192.168.111.218[4500] (112 bytes) May 31 22:13:43 pfsense charon[63100]: 07[ENC] <con-mobile|28> parsed IKE_AUTH request 5 [ AUTH ] May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> authentication of '192.168.111.254' with EAP successful May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> authentication of '192.168.111.218' (myself) with EAP May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> IKE_SA con-mobile[28] established between 192.168.111.218[192.168.111.218]...192.168.111.254[192.168.111.254] May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> IKE_SA con-mobile[28] state change: CONNECTING => ESTABLISHED May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> scheduling rekeying in 24778s May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> maximum IKE_SA lifetime 27658s May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> peer requested virtual IP %any May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> reassigning offline lease to 'gregzon' May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> assigning virtual IP 192.168.40.1 to peer 'gregzon' May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> peer requested virtual IP %any6 May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> no virtual IP found for %any6 requested by 'gregzon' May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> building INTERNAL_IP4_SUBNET attribute May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> building UNITY_SPLIT_INCLUDE attribute May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> building INTERNAL_IP4_DNS attribute May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> building UNITY_DEF_DOMAIN attribute May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> building UNITY_SPLITDNS_NAME attribute May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> building UNITY_BANNER attribute May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> looking for a child config for 0.0.0.0/0|/0 ::/0|/0 === 0.0.0.0/0|/0 ::/0|/0 May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> proposing traffic selectors for us: May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> 0.0.0.0/24|/0 May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> proposing traffic selectors for other: May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> 192.168.40.1/32|/0 May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> candidate "con-mobile" with prio 2+2 May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> found matching child config "con-mobile" with prio 4 May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> selecting proposal: May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> no acceptable ENCRYPTION_ALGORITHM found May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> selecting proposal: May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> no acceptable ENCRYPTION_ALGORITHM found May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> selecting proposal: May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> no acceptable ENCRYPTION_ALGORITHM found May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> selecting proposal: May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> no acceptable INTEGRITY_ALGORITHM found May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> selecting proposal: May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> proposal matches May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> received proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> configured proposals: ESP:AES_GCM_16_128/NO_EXT_SEQ, ESP:AES_GCM_12_128/NO_EXT_SEQ, ESP:AES_GCM_8_128/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/NO_EXT_SEQ May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> selecting traffic selectors for us: May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> config: 0.0.0.0/24|/0, received: 0.0.0.0/0|/0 => match: 0.0.0.0/24|/0 May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> config: 0.0.0.0/24|/0, received: ::/0|/0 => no match May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> selecting traffic selectors for other: May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> config: 192.168.40.1/32|/0, received: 0.0.0.0/0|/0 => match: 192.168.40.1/32|/0 May 31 22:13:43 pfsense charon[63100]: 07[CFG] <con-mobile|28> config: 192.168.40.1/32|/0, received: ::/0|/0 => no match May 31 22:13:43 pfsense charon[63100]: 07[CHD] <con-mobile|28> CHILD_SA con-mobile{11} state change: CREATED => INSTALLING May 31 22:13:43 pfsense charon[63100]: 07[CHD] <con-mobile|28> using AES_CBC for encryption May 31 22:13:43 pfsense charon[63100]: 07[CHD] <con-mobile|28> using HMAC_SHA2_256_128 for integrity May 31 22:13:43 pfsense charon[63100]: 07[CHD] <con-mobile|28> adding inbound ESP SA May 31 22:13:43 pfsense charon[63100]: 07[CHD] <con-mobile|28> SPI 0xc225b254, src 192.168.111.254 dst 192.168.111.218 May 31 22:13:43 pfsense charon[63100]: 07[CHD] <con-mobile|28> adding outbound ESP SA May 31 22:13:43 pfsense charon[63100]: 07[CHD] <con-mobile|28> SPI 0x1d6154cc, src 192.168.111.218 dst 192.168.111.254 May 31 22:13:43 pfsense charon[63100]: 07[IKE] <con-mobile|28> CHILD_SA con-mobile{11} established with SPIs c225b254_i 1d6154cc_o and TS 0.0.0.0/24|/0 === 192.168.40.1/32|/0 May 31 22:13:43 pfsense charon[63100]: 07[CHD] <con-mobile|28> CHILD_SA con-mobile{11} state change: INSTALLING => INSTALLED May 31 22:13:43 pfsense charon[63100]: 07[ENC] <con-mobile|28> generating IKE_AUTH response 5 [ AUTH CPRP(ADDR SUBNET U_SPLITINC DNS U_DEFDOM U_SPLITDNS U_BANNER) N(ESP_TFC_PAD_N) SA TSi TSr ] May 31 22:13:43 pfsense charon[63100]: 07[NET] <con-mobile|28> sending packet: from 192.168.111.218[4500] to 192.168.111.254[4500] (304 bytes) May 31 22:13:46 pfsense charon[63100]: 15[NET] <con-mobile|28> received packet: from 192.168.111.254[4500] to 192.168.111.218[4500] (80 bytes) May 31 22:13:46 pfsense charon[63100]: 15[ENC] <con-mobile|28> parsed INFORMATIONAL request 6 [ D ] May 31 22:13:46 pfsense charon[63100]: 15[IKE] <con-mobile|28> received DELETE for ESP CHILD_SA with SPI 1d6154cc May 31 22:13:46 pfsense charon[63100]: 15[IKE] <con-mobile|28> closing CHILD_SA con-mobile{11} with SPIs c225b254_i (0 bytes) 1d6154cc_o (0 bytes) and TS 0.0.0.0/24|/0 === 192.168.40.1/32|/0 May 31 22:13:46 pfsense charon[63100]: 15[IKE] <con-mobile|28> sending DELETE for ESP CHILD_SA with SPI c225b254 May 31 22:13:46 pfsense charon[63100]: 15[CHD] <con-mobile|28> CHILD_SA con-mobile{11} state change: INSTALLED => DELETING May 31 22:13:46 pfsense charon[63100]: 15[IKE] <con-mobile|28> CHILD_SA closed May 31 22:13:46 pfsense charon[63100]: 15[CHD] <con-mobile|28> CHILD_SA con-mobile{11} state change: DELETING => DELETED May 31 22:13:46 pfsense charon[63100]: 15[CHD] <con-mobile|28> CHILD_SA con-mobile{11} state change: DELETED => DESTROYING May 31 22:13:46 pfsense charon[63100]: 15[ENC] <con-mobile|28> generating INFORMATIONAL response 6 [ D ] May 31 22:13:46 pfsense charon[63100]: 15[NET] <con-mobile|28> sending packet: from 192.168.111.218[4500] to 192.168.111.254[4500] (80 bytes) May 31 22:13:46 pfsense charon[63100]: 15[NET] <con-mobile|28> received packet: from 192.168.111.254[4500] to 192.168.111.218[4500] (80 bytes) May 31 22:13:46 pfsense charon[63100]: 15[ENC] <con-mobile|28> parsed INFORMATIONAL request 7 [ D ] May 31 22:13:46 pfsense charon[63100]: 15[IKE] <con-mobile|28> received DELETE for IKE_SA con-mobile[28] May 31 22:13:46 pfsense charon[63100]: 15[IKE] <con-mobile|28> deleting IKE_SA con-mobile[28] between 192.168.111.218[192.168.111.218]...192.168.111.254[192.168.111.254] May 31 22:13:46 pfsense charon[63100]: 15[IKE] <con-mobile|28> IKE_SA con-mobile[28] state change: ESTABLISHED => DELETING May 31 22:13:46 pfsense charon[63100]: 15[IKE] <con-mobile|28> IKE_SA deleted May 31 22:13:46 pfsense charon[63100]: 15[ENC] <con-mobile|28> generating INFORMATIONAL response 7 [ ] May 31 22:13:46 pfsense charon[63100]: 15[NET] <con-mobile|28> sending packet: from 192.168.111.218[4500] to 192.168.111.254[4500] (80 bytes) May 31 22:13:46 pfsense charon[63100]: 15[IKE] <con-mobile|28> IKE_SA con-mobile[28] state change: DELETING => DESTROYING May 31 22:13:46 pfsense charon[63100]: 15[CFG] <con-mobile|28> lease 192.168.40.1 by 'gregzon' went offlineI also installed strongswan on androind samsung s10e. VPN was established, i could reach internet, etc. But i could not ping a server in vpn Lan (192.168.26.10)
Is this normal that if i am connected to vpn with two devices (pc windows 10 - 192.168.40.2) , android phone (192.168.40.1) they can't ping eachother ?Any tips/hints etc, much appreciated, thank you.
Greg
-
i also added now new section in phase 2
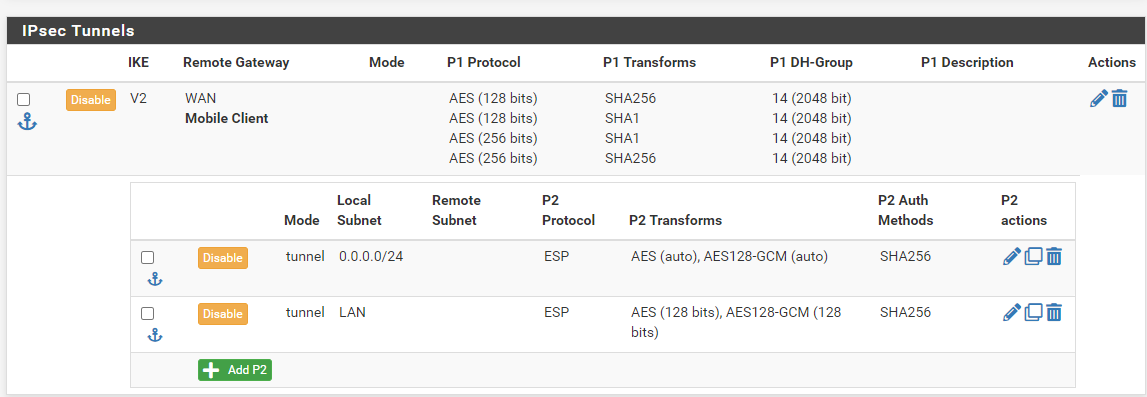
And my adroid phone can reach the server in pfsense lan. But my windows client still can't do it.few minutes ago, i have connected again on windows client.
and i can ping the pfsense lan interface (192.168.26.1) and server (192.168.26.10)
but it can't ping internet still.PS C:\Users\Greg-Admin> ping 192.168.26.10 Pinging 192.168.26.10 with 32 bytes of data: Reply from 192.168.26.10: bytes=32 time=1ms TTL=127 Reply from 192.168.26.10: bytes=32 time=1ms TTL=127 Ping statistics for 192.168.26.10: Packets: Sent = 2, Received = 2, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 1ms, Maximum = 1ms, Average = 1ms Control-C PS C:\Users\Greg-Admin> ping 192.168.1.1 Pinging 192.168.1.1 with 32 bytes of data: Reply from 192.168.1.1: bytes=32 time<1ms TTL=64 Ping statistics for 192.168.1.1: Packets: Sent = 1, Received = 1, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 0ms, Maximum = 0ms, Average = 0ms Control-C PS C:\Users\Greg-Admin> ping 8.8.8.8 Pinging 8.8.8.8 with 32 bytes of data: Control-CIf i will enable split tunnel
Get-VpnConnection -Name 'VPN2HOME' |Set-VpnConnection -SplitTunneling:$truethen my windows client, at least can reach internet again , but if i understand correctly, this means that the internet part is not getting via vpn ,but using my normal connection.