Routing between existing LAN's
-
Hello everyone, i'm facing an old and strange network implementation for industrial automation.
There are 4 different LAN's on that site !!!
On all LAN's we can connect through static or DHCP (there are routers with static routes for the next router).Let's say i'm not in a position to tear down the existing networks, but i will put some systems in parallel.
IF for example i put a 4 port pfsense device and i will get a DHCP lease from the 4 LAN's, I'm I able to access the networks ? And most important, Under NAT, we have outbound options, so if LAN1 is accessing LAN2, outbound NAT will translate to LAN2 address, so LAN 2 will see that the traffic is coming from the same network. Is this valid ? What else i can do in such case ? Thanks for any suggestions. -
@bambos said in Routing between existing LAN's:
(there are routers with static routes for the next router).
A drawing of this network would help us immensely
Problem you face bringing up a another router that is attached to these 4 different networks, is why would client on network A, talk to your pfsense to get to network B.
Without a drawing and some details, its really going to be impossible for anyone to help.
-
@johnpoz yes you are right. It's getting complicated. Please see below diagram. There are LAN 0 grey colour done with tp-link , dhcp working
Lan 2 green colour done with mikrotik , dhcp working
New LAN 44 will be the new LAN for my devices, and planning to access this with site to site VPN through my central VPN Server.The target is to access all networks. I guess is not possible to route traffic of network LAN0 through pfsense to LAN2, because default gateway is 192.168.0.254. But as a dhcp client on that network, i can access those networks from LAN44 if correct translations can be made.
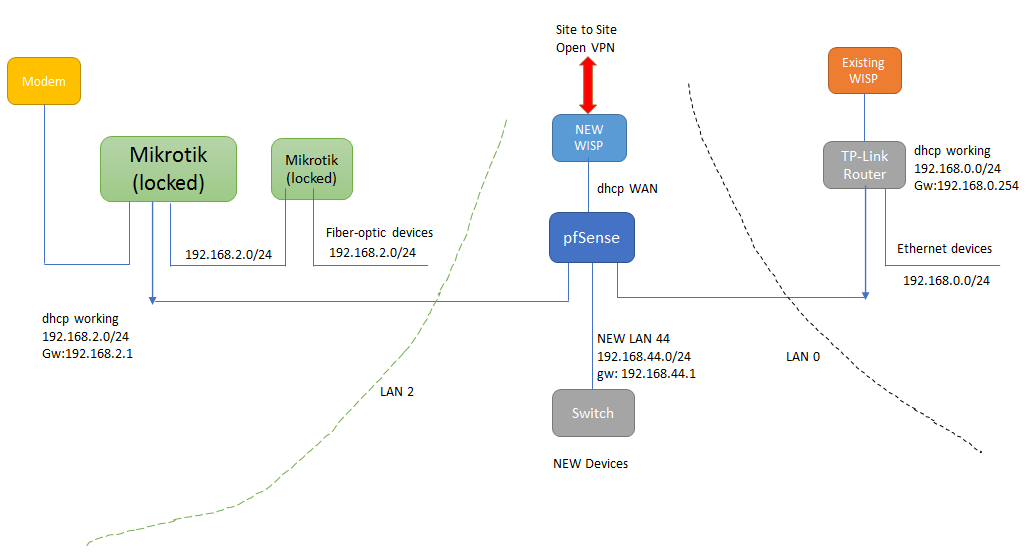
-
thought you said there were 4 different lans?
And they are all connected to different routers to provide internet?
All of your connections are going to come from this 44 lan.. Your not going to want say lan 2 to create connections into lan 44 or lan 0?
yeah your going to have to source nat for sure.. This would be done via outbound nats on pfsense into those different interfaces.
You seem to be on the right track with your natting. Your just going to need any traffic coming from lan 44 going to any of these other lans look like it came from device in that lan.. Ie pfsense IP in that network. To be honest once you setup a gateway on these interfaces, pfsense will treat them like wans and nat to the IP.. So really this would work out of the box almost. Your only thing you will want to do is setup pfsense to use your new wisp as its default internet connection.
Where you could have issue is if you want say lan 0 talking to lan 2 through pfsense.
-
@johnpoz Thank you very much for your comments.
There is another LAN / router on the LAN0 switch, but is DVR network for cameras. The server has 2 network cards, 1 is on DVR, the other is on LAN 0.
Existing WISP is for internet for LAN0
Modem is 4G connection but private m2m - no internet.
New Wisp is the internet i'm using for VPN site to site so i have remote access.I know that on such complicated and problematic networks, we can't do miracles. But i'm just examining what i can do better. I'm still learning pfSense... but more correctly, I start learning networking through pfSense, which is a great open-source project.
It seems that there is a difference if pfSense connect with dhcp on the foreign Lan's, or make it static with a pre-defined gateway. There are cases that can't outbound correctly when connect with dhcp, and needs outbound rule for sure. On some cases i have notice that if connected with static IP and pre-defined gateway, can outbound correctly without the outbound NAT rule. In both cases i have checked the routing table and is the same.
Also, now i understand the usage of outbound NAT and static route.
Outbound NAT rule is translation on the pfsense interfaces,
Static Route is a route creation for another network (far behind another router/routers) that is not directly attached on the pfSense, but we just show the correct route if there are many. What do you think ? -
@bambos said in Routing between existing LAN's:
but we just show the correct route if there are many. What do you think ?
Again are you trying to route traffic from lan 0 or lan 2 or something like that.. That is NOT going to work.. you would have to port forward..
Stuff talking from 44 to any other network is not an issue with just nat. Where you have a real complex mess is if you have lan 0 wanting to talk to 2 for example with pfsense inbetween that is not the default gateway and other routers that can not even do routing, and do not have a transit setup, etc..
The correct solution would be to dump that whole mess and set it up correctly!!
-
@johnpoz i realize that routing from 0 to 2 is not possible, because all the devices are replying through the default gateways, which are the respective routers in each lan.
BUT network 44 can go both on both networks through Outbound NAT.now, IF by luck i have access to tp-link or mikrotik, in theory we can make static routiings on each device to access the foreign LAN through the pfsense interface in their own LAN.
Now you agree ? :)Of course, dumping the whole mess is something i'm considering. My only issue is that on LAN2, there are some devices having static IP hardcoded in their firmware, so most probably network LAN2 is staying, all others will be transfered to network LAN 44.
-
@bambos said in Routing between existing LAN's:
IF by luck i have access to tp-link or mikrotik, in theory we can make static routiings
NO not really - not without setting up transit networks... You run into asymmetrical routing when you have clients on the the transit network. Ie lan 0... even if you setup a route on the mikrotik to go to pfsense to get to lan 2.. The return traffic would not go back to the mikrotik.. Asymmetrical, now you have issues with states. You have issues with clients saying WTF I sent this to my gateway at mac abc, why is return coming from mac xyz..
You can not have devices on a transit network (network that connects two or more routers) without either doing host routing on each device in the transits or doing nat on the downstream router and not actually doing routing.
It seems like I have to go over this every single day ;)
You can get traffic between 44 and your other vlans. And you could even have traffic between vlans with port forwarding, etc But its still a F'ing mess!
-
@johnpoz Hello Sir, i realize it's a mess, you are right. Assuming LAN2 devices can't be changed, they have to be in separate LAN 2. (hard-code static IP in firmware)
Assuming that device 192.168.2.10 on LAN 2 has to communicate on ports 502-508 with a device 192.168.0.4 on LAN 0, only this i need. Can you suggest a possible method might work ?
-
You would port forward ports 502-508 from lan 2 pfsense IP to 192.168.0.4, and also setup source natting (outbound nat)
So that 192.168.0.4 thinks its coming from the pfsense 192.168.0.X IP.
Now when 192.168.2.10 tries to talk to pfsense 192.168.2.x IP it would be sent to 192.168.0.4