NAT trick over VPN to access LAN's on same range (avoid conflict)
-
Hello everyone,
Is it possible in any way to access both networks on LAN IP 192.168.2.0/24 at the same time without the conflict of same LAN's ? Is there a way to make custom translation to overcome this conflict, by using the different Tunnels ?
All the routers are pfSense, VPN's are site to site OpenVPN and are working, Virtual IP's as schematic. Access would be from LAN 16 on central.
Schematic Diagram:
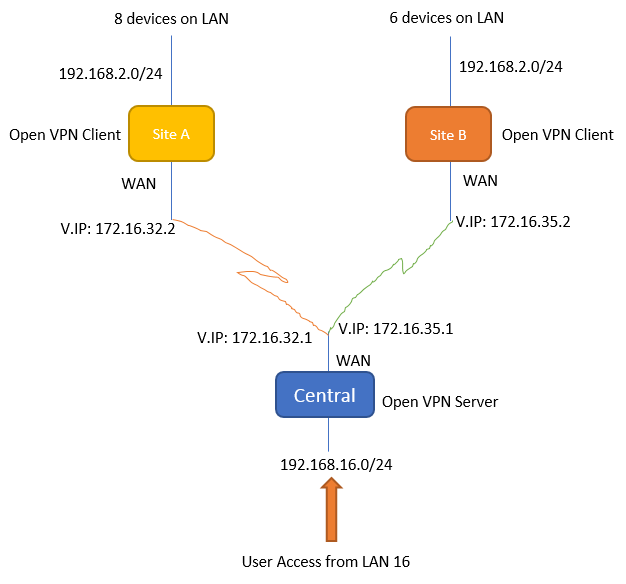
-
@bambos
The router can only use one route for the subnet 192.168.2.0/24.
So the only way without changing one remote LAN ist to use another address space on the local site and NAT it on the remote site to the LAN IPs using NAT 1:1. -
@viragomann Thanks for your comments.
Another address space on the local site what we mean ? Static route ?
And then 1:1 NAT to the tunel IP ?
Is outbound needed for this case ? -
@bambos
No, for instance you can simply add a NAT 1:1 on site B to the vpn interface, where external subnet is 10.125.10.0/24 and internal 192.168.2.0/24.On Central you have to add 10.125.10.0/24 to the remote sites instead of 192.168.2.0/24 in the site-to-site settings.
That's all you have to do. Now you can access e.g. 192.168.2.56 on site B by entering 10.125.10.56.
When 192.168.2.56 from B access a device at central site, the device sees access coming from 10.125.10.56. -
Does anyone know if it is possible to do DNS Rewrite on pfsense eg. like this PA documentation...
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-new-features/networking-features/dns-rewrite-dest-nat.html
-
@viragomann it works like a charm. can't thank you enough for your directions.
-
@brians pfsense can do DNS override if your WAN is dhcp, otherwise you have 2 options to set DNS, 1 for the system and 1 for the dhcp server for the dhcp clients on all LAN's
-
@bambos that’s not what the pa is doing in my link. On IPSec tunnels it can rewrite dns lookups for remote dns servers across 1:1 NAT,which changes the ip address of a lookup to reflect the new NAT’d 1:1 IP address.
-
@brians i don't know IPSec. most probably you can do something like this using openVPN. i suggest you start another threat in the correct forum section.