Disable https on public IP
-
How do I disable the web server from listening on my public IP?
-
You don't the firewall rules do not allow access out of the box from the wan side. The web gui listens on all interfaces.
If you do not want access to the web gui from the wan, do not put in rules that allow it. If you do not want to allow access from your lan side networks to access web gui via the wan IP or any other lan side IP, then put in rules to block it, etc.
-
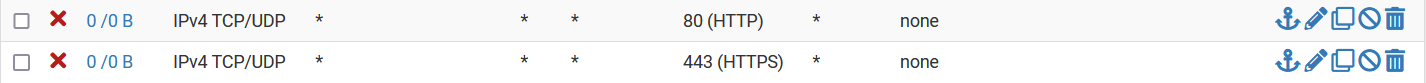
@johnpoz I have these rules on my WAN, and I am still able to connect to the public IP.
-
By default the wan blocks all unsolicited inbound traffic, all interfaces do.. Default Deny is pfsense default.. The wan out of the box has no rules on it - all access from outside would be blocked. If you are accessing your gui from the wan side, then you must of put in a rule to allow it either on the wan or floating.
You would be able to access the public IP from any lan side device yes - since default is any any, and your public IP falls under any ;)
What other rules on the wan do you have? Or floating tab? Are you actually testing from external - go to can you see me . org for example.
Or go to the grc port scanner.. Testing access to your public IP from the local side is not valid test for what can be accessed from outside pfsense. If you don't want local devices hitting your wan IP, then you need to put block rules on your lan side interfaces. The "this firewall" is a good alias to use. Since it would include all your pfsense IPs wan, lan, vlan, optX, etc. This can keep client on lan from accessing optX IP as well as wan IP.
edit: Here maybe this example will help.
Here from my lan - my gui listens on 8443.. I can access my pfsense wan IP from lan, because there is any any rule that allows my lan to go anywhere, any IP any port.
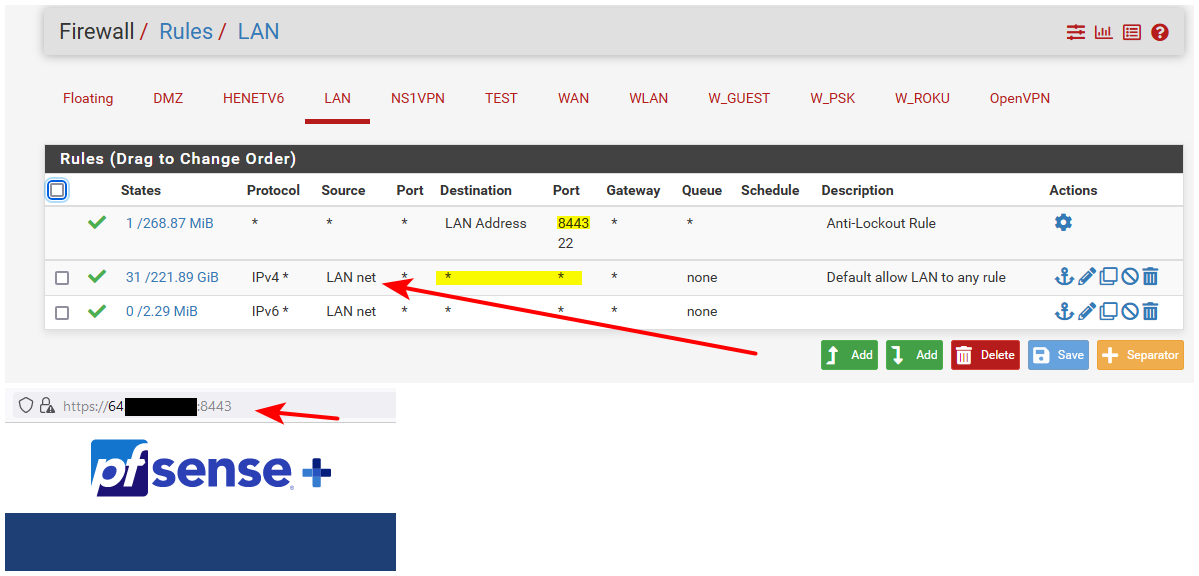
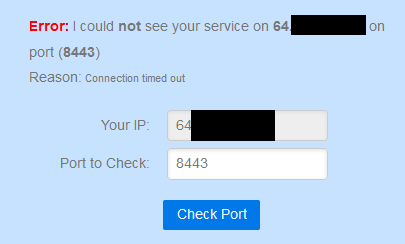
But from the WAN side.. I have no rules that allow that access.. So its blocked.
-
I think that's what my issue was - hitting the public-facing ip from my LAN.