no communication between VPN and Client LAN
-
Good morning,
thank you for your help.
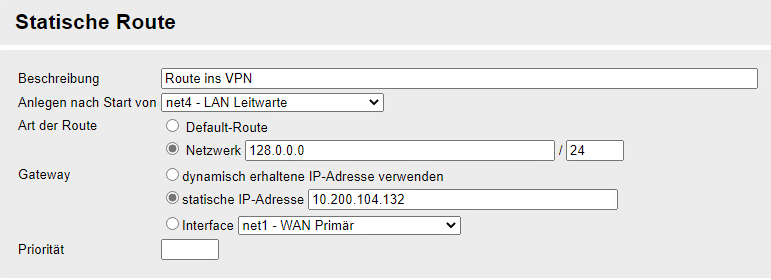
i will change the IP-range of the tunnel network to make it more reasonable.as far as I understand the pfSense(server) just has to work like a gateway to route the packets for the 10.200.104.0 network to the pfSense(client).
In addition, the router (insys MRX) on the 10.200.104 network must have static routing to route the packets for the tunnel to the pfSense(client).@viragomann said in no communication between VPN and Client LAN:
Which auth mode does the server use, SSL + user auth or user only?
The OpenVPN Server mode is "Remote Access (SSL/TLS)"
The OpenVPN client mode is "peer-to-peer (SSL/TLS)"On your location you should remove pfSense from the LAN and set up a transit network between the router and pfSense, if the router is capable of this is. Otherwise you can only go with masquerading.
This is a little bit complicated as the existing MRX Router is already a openVPN Server over the first Internet connection that should be replaced by the pfSense sometime, then the pfSense should provide an openVPN Server over the first Internet connection and an openVPN client over Starlink for redundancy. But for now i'm focusing on the client over Starlink thing.
-
@knausepeter said in no communication between VPN and Client LAN:
This is a little bit complicated as the existing MRX Router is already a openVPN Server over the first Internet connection that should be replaced by the pfSense sometime, then the pfSense should provide an openVPN Server over the first Internet connection and an openVPN client over Starlink for redundancy. But for now i'm focusing on the client over Starlink thing.
Not clear what this has to do with setting up a transit network. The only one question is if the router is cabable to handle multiple internal network segments.
You can to this on the same wire by VLANs, but I don't know if it is possible with your router. It would be the more reliable solution.Otherwise since for now, pfSense is the gateway for the VPN clients network you have either add a static route to each unique device on the LAN or do masquerading, as I already mentioned.
The static route on the router is not sufficient! -
@viragomann said in no communication between VPN and Client LAN:
Not clear what this has to do with setting up a transit network.
-that was just the explanation why neither the router, nor the pfSense can be removed from the network.
The only one question is if the router is cabable to handle multiple internal network segments.
-The MRX is capable of managin 5 local Ip networks according to the Datasheet.
Otherwise since for now, pfSense is the gateway for the VPN clients network you have either add a static route to each unique device on the LAN or do masquerading, as I already mentioned.
I have to admit, i don't have any experience with masquerading and don't really know what it is. From what i read on google i don't think, this is the right thing for me. Static routes sound better to me.
From my understanding if the local PC wants to send a Package, to a device in the VPN, it sends the package adressed to maybe 128.0.0.251 (i changed the VPN Adress range already but will stick with this for now to not make it even more confusing).
The Standard-gateway (MRX) receives the package but don't know the targeted network, so it has a static route, that sends all packages adressed to the VPN to the pfSense. The pfSense knows the network and will deliver the Package.
For the Answer the same procedure, The Device sends a package to the 10.200.104.0 Network which the VPN Server has no clue of, so it hast to route these packages also to the pfSense(client) which is the gateway between my local network and the VPN.These connections are already established and i can ping the pfSense in the local network and i can ping from within the VPN to every other device within the VPN. but not from within the VPN into the local network or vice versa...
-
@knausepeter said in no communication between VPN and Client LAN:
From my understanding if the local PC wants to send a Package, to a device in the VPN, it sends the package adressed to maybe 128.0.0.251 (i changed the VPN Adress range already but will stick with this for now to not make it even more confusing).
The Standard-gateway (MRX) receives the package but don't know the targeted network, so it has a static route, that sends all packages adressed to the VPN to the pfSense. The pfSense knows the network and will deliver the Package.
For the Answer the same procedure, The Device sends a package to the 10.200.104.0 Network which the VPN Server has no clue of, so it hast to route these packages also to the pfSense(client) which is the gateway between my local network and the VPN.Not exactly that. The VPN client has a route to 10.200.104.0, since you have to provide it in the server settings. And within OpenVPN you need an additional internal route (iroute) to direct the packets to the proper client.
So pfSense receives the packet and deliver it to the LAN device.If the communication you described from LAN to a VPN client might work, however the problem is the other direction. If a VPN client wants to access a device in the local network the request way goes
pfSense > LAN device.
and the response goes
LAN device > router > pfSense
This is called asyemmetric routing and will affect stateful connections like TCP. pfSense is a statefull firewall and might drop the packets, since they don't have the correct state. Don't know how your router is working.
However, that doesn't matter for ping which uses ICMP, since this is a stateless protocol.On pfSense you may play with sloppy state rules to get the packets pass. But don't know, if you get it work on your router.
When doing masquerading, the source IP in packets destined to a LAN device is translated into the LAN IP of pfSense using S-NAT. This way the LAN device sends responses back directily to pfSense, cause its destination is in its own subnet.
-
@viragomann said in no communication between VPN and Client LAN:
Not exactly that. The VPN client has a route to 10.200.104.0, since you have to provide it in the server settings. And within OpenVPN you need an additional internal route (iroute) to direct the packets to the proper client.
can you discribe this a little more where i have to put in what, maybe i have done something wrong here already.
On pfSense you may play with sloppy state rules to get the packets pass. But don't know, if you get it work on your router.
this is something i could try, can you tell me how? i'm pretty new to pfSense and some things are a bit above my level of experience.
When doing masquerading, the source IP in packets destined to a LAN device is translated into the LAN IP of pfSense using S-NAT. This way the LAN device sends responses back directily to pfSense, cause its destination is in its own subnet.
This sounds also like a good solution, but i have absolutely no clue how to do this.
Thank you very much for all your help!
-
can you discribe this a little more where i have to put in what, maybe i have done something wrong here already.
What you try to realize is described here in the pfSense docs: Configuring a Single Multi-Purpose OpenVPN Instance
On the server you have to add 10.200.104.0/24 to the "Local networks" to push the proper route to the clients.
Then you have to setup a CSO (VPN > OpenVPN > Client Specific Overrides) for the site-to-site. This overrides the settings for this client. Here you have to enter 10.200.104.0/24 into the "Remote Networks" box.
For the other settings follow the hints given.this is something i could try, can you tell me how?
That's a kind of hack and I don't use it.
If you do masquerading that isn't necessary.Masquerading is done by outbound NAT in pfSense.
Switch the outbound NAT into the hybride mode and save this.
Add a rule like this:
interface: LAN
source: <the vpn tunnel network or any if you need also other sources>
destination: LAN net
translation: interface address -
So I'm still not 100% successful, i have completely redone the OpenVPN Server after this tutorial: OpenVPN Site-to-Site Configuration Example with SSL/TLS
If the Server is configured as Peer-to-Peer (SSL/TSL) i got almost a connection between two sites. at least i can ping in and out of the tunnel.
Nevertheless, in the p2p configuration I'm not able to export .ovpn files to connect a third client.
in this post it say's that i should use p2p for connecting only 2 sites and access server otherwise: OpenVPN "remote access" vs "peer to peer"
If i change the server configuration to Access Server (SSL/TLS) the fields for "IPV4 remote networks" disappear and i can't communicate from one network into the tunnel or the other site. This is where i have been before.
At this point am completely lost, is there any tutorial i can follow or somebody who is willing to help me with this?
-
@knausepeter said in no communication between VPN and Client LAN:
If i change the server configuration to Access Server (SSL/TLS) the fields for "IPV4 remote networks" disappear
The reason for this behaviour should be evident.
You can find this setting in the CSO instead, as I already mentioned above. -
Yes, that's what I thought.
So once to make sure:-in the server configuration I enter under "IPv4 local network/s" all the total reachable local networks of all clients that I want to connect later.
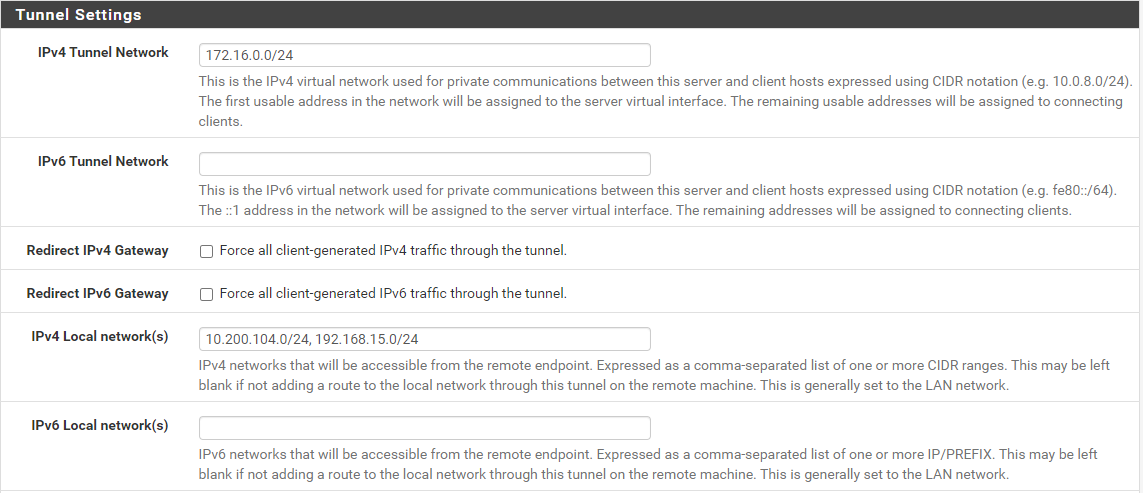
-In the respective CSO I then enter the corresponding local network address under "IPv4 remote Network/s".
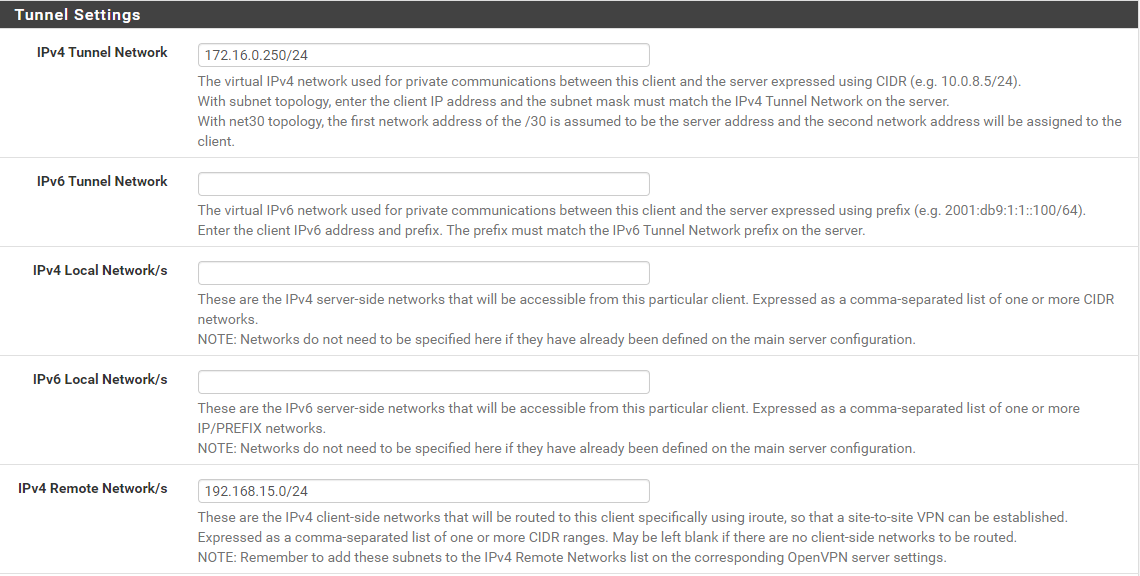
correct?
I have now reduced the configuration so that the pfSense in the office is set as the default gateway of the PC and at my second location a router connects as OpenVPN client, and has the network 192.168.15.0/24 under it with one PC.
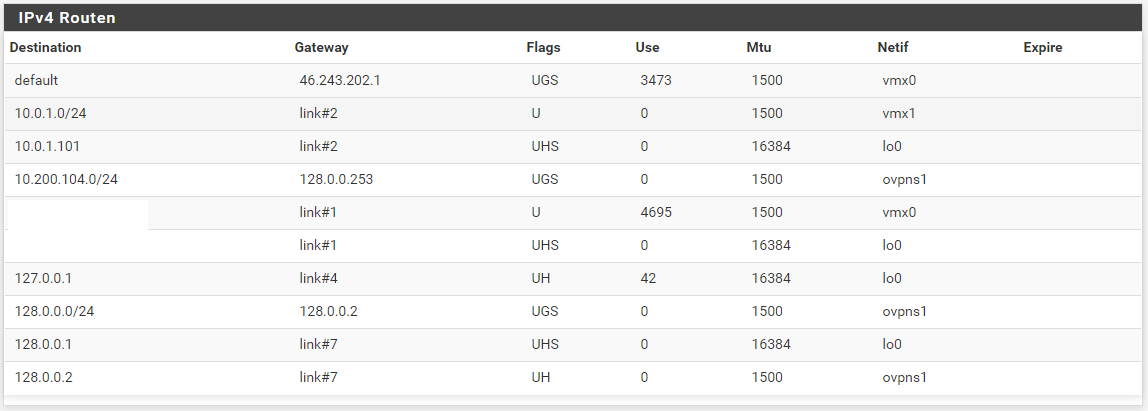
Under Status -> OpenVPN -> Routing tables I also see the correct routes.
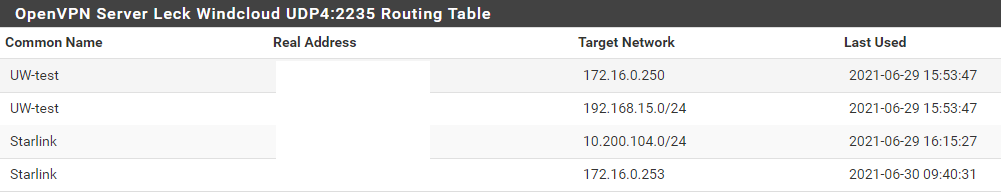
if i traceroute from the PC inside the office to the VPN client of the remote Router, i can see the first hop is the pfSense(client) and then nothing comes afterwards.
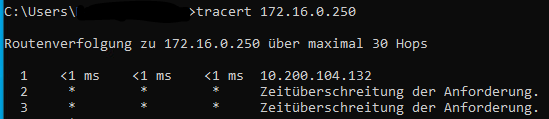
the same if i try to traceroute to the Server (172.16.0.1) BUT this worked when the Server was configured as peer-to-peer. I was able to ping from both local networks into the VPN but not through it.
What am i missing?
Thanks for all help.
-
@knausepeter said in no communication between VPN and Client LAN:
correct?
No. The CSO are only new server settings for a specific client.
That means you have to add specific tunnel network for this client first of all. Accordingly to the servers topology use a /30 mask or a single IP.
At local networks enter the networks you want to access from the client. If you're have subnet topology you will have to enter the servers tunnel network to enable communication with the other clients.
In the "Remote Networks" box enter the 10.200.104.0/24 so that OpenVPN can set the proper routes. -
sorry, I do not fully understand.
Which part so far is wrong? The server or the CSO config?
for the CSO config, i now have 2 client, each with one local network:
first client: LAN: 10.200.104.0/24 - VPN: 172.16.0.253
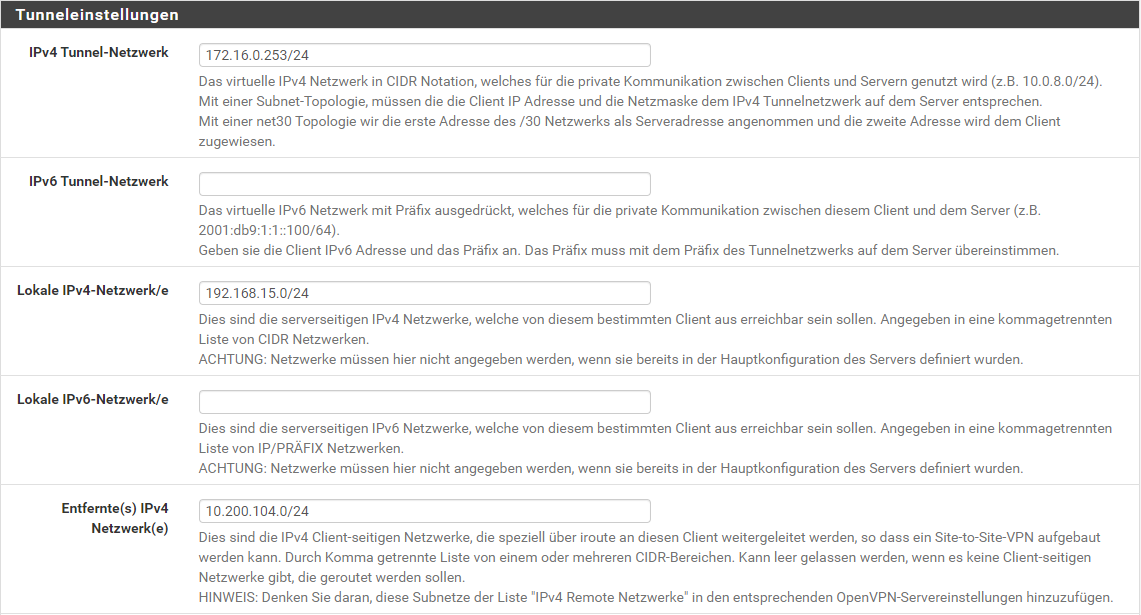
second client: LAN: 192.168.15.0/24 - VPN: 172.16.0.250
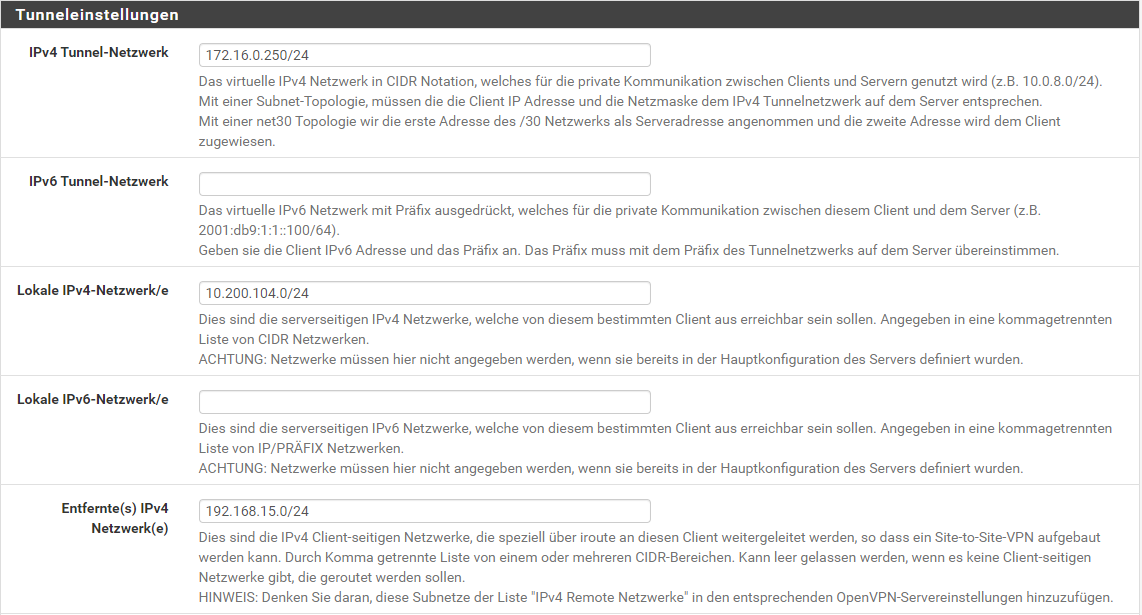
the server has no LAN attached to it, it is just the central point.
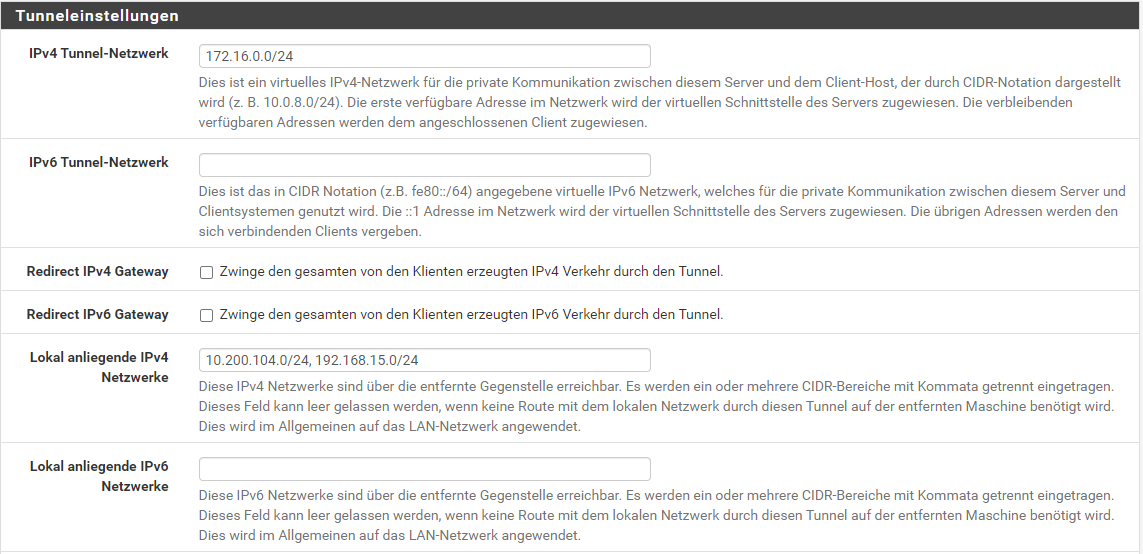
-
@knausepeter said in no communication between VPN and Client LAN:
for the CSO config, i now have 2 client, each with one local network:
Why two?
You need a CSO only for the local network with the Starlink connection, but not for access server clients. -
Why two?
You need a CSO only for the local network with the Starlink connection, but not for access server clients.
i made a new picture:
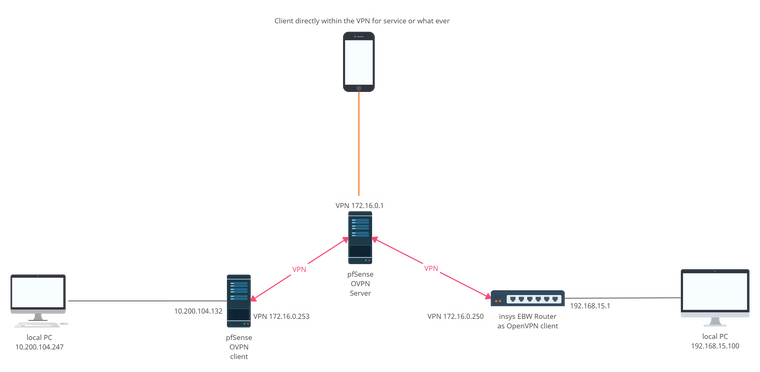
This is the current configuration as it is currently set up. i have my main network (10.200.104.0) and a remote network (192.168.15.0) later i will add many more remote networks that should all communicate with the main network but not with each other. These do not exist yet, but will be added in the future.
The smartphone should also be part of the VPN for service purposes, to get to the web interfaces in case of emergency (not mandatory but nice) could be an Android phone with OpenVPN connect app.
You can see in this picture, that i set the local pfSense as Standard gateway to sort out sources of error. And i changed the IP-Range of the VPN as mentioned above.
-
@knausepeter
With regard to your obvious troubles with CSO I want to repeat my suggestion from an upper post to put that VPN connection behind which you want to access servicse on a separate server.
Otherwise apart from CSO you need to enable communication between all VPN clients connected to the server, which might not be desired. It is not possible this way to control the traffic between the clients with firewall rules on pfSense, cause it doesn't pass the filter part.What are your concerns on running multiple OpenVPN servers?
-
@viragomann said in no communication between VPN and Client LAN:
What are your concerns on running multiple OpenVPN servers?
this whole setup will be much bigger in the future, i will explain what is planned in the future.
right now we have a Router at our local office that manages the local network as well as providing an openVPN server for all remote sites over the first internet connection. this is working fine.
Now my boss wants a second path for communication in case something happens to the first path like a power outage (we have emergency power but in case of a local power outage we would still have no internet).Now my boss read something about pfSense and was excited and bought a starlink dish and a super expensive server for the second VPN server.
The problem now is, that starlink cannot provide a static IP-adress and my boss don't want any dynDNS services. So we cannot run a Server at this location over Starlink because of the changing IP-adress.
But we have another server somewhere else with a static IP and pfSense installed so the idea is to set up the OpenVPN server there and tunnel from here to the server as well as from all other locations to that same server so we could establish a static connection this way over that server.
And it's my task to realize this

-
@knausepeter
Ok, but this long story doesn't bring any change to the conditions. You have multiple sites, one of them is the main location, the others I'll call branches. All branches should be able to access services in the main location, but don't need to talk to each other.Since the main location has a dynamic IP and hence cannot run the server, you want to set up a central VPN server, where the main and all branches should connect to via OpenVPN to enable the desired communication.
This is the server we're talking about.And now my question again is, why do you want run multiple VPN servers to realize this?
It doensn't matter if this is an expensive hardware or not at all. An OpenVPN server doesn't need much resources, so you can also run multiple instances on a small hardware, but easier to set up the routing between the connected clients.
Your option is to go with CSO as I mentioned in my first post here, but that doesn't seem to be familiar to your. -
@viragomann said in no communication between VPN and Client LAN:
Ok, but this long story doesn't bring any change to the conditions. You have multiple sites, one of them is the main location, the others I'll call branches. All branches should be able to access services in the main location, but don't need to talk to each other.
Since the main location has a dynamic IP and hence cannot run the server, you want to set up a central VPN server, where the main and all branches should connect to via OpenVPN to enable the desired communication.
This is the server we're talking about.
Exactly!
And now my question again is, why do you want run multiple VPN servers to realize this?
The new machine runs the pfSense among other things that should replace the "old" Router that is hosting the present VPN Server. In the future the pfSense machine should run 1 server, that connects to the main Internet and the client that connects to the remote server (what i'm trying to realise right now). Then the old router goes somewhere else.
As soon as my setup works, all the other locations will be moved to the pfsense.
to get back on topic, I think I'm close to a breakthrough, I just think I entered something wrong in the CSO, it can't be that much now.
do i have to enter something at the clientside pfSense openVPN config?
-
@knausepeter
Okay, however why do you still not respond to my question which I asked three times already?And why put you as much time in a mediocre solution and ignoring all drawbacks?
-
@viragomann said in no communication between VPN and Client LAN:
Okay, however why do you still not respond to my question which I asked three times already?
why do you want run multiple VPN servers to realize this?
because we need a guaranteed connection and if the first internet connection fails the remote sites must fall back to the second VPN connection, this would be a lesser problem, if our second internet connection had a static ip, but since starlink hasn't a static ip, this was our solution. This whole mess what i'm trying to do here is just for the emergency case. But i think i also answered this already (no offense)
And why put you as much time in a mediocre solution and ignoring all drawbacks?
good question, i keep asking this myself for days... because i try to realise what my managing director wants... do you have a better idea? i need to utilize the new fancy hardware and starlink...
-
@knausepeter
In order not to be misunderstood, I'm talking about running two OpenVPN servers on a unique pfSense box. This one which has a static public IP.
For instance you run one OpenVPN server on port 1194 for the branches and a second one as site-to-site on port 1195 for the client in the main location.This way you can properly route the traffic from one VPN server to the other one as well as to the client in main location and you are able to control the traffic by filter rules.