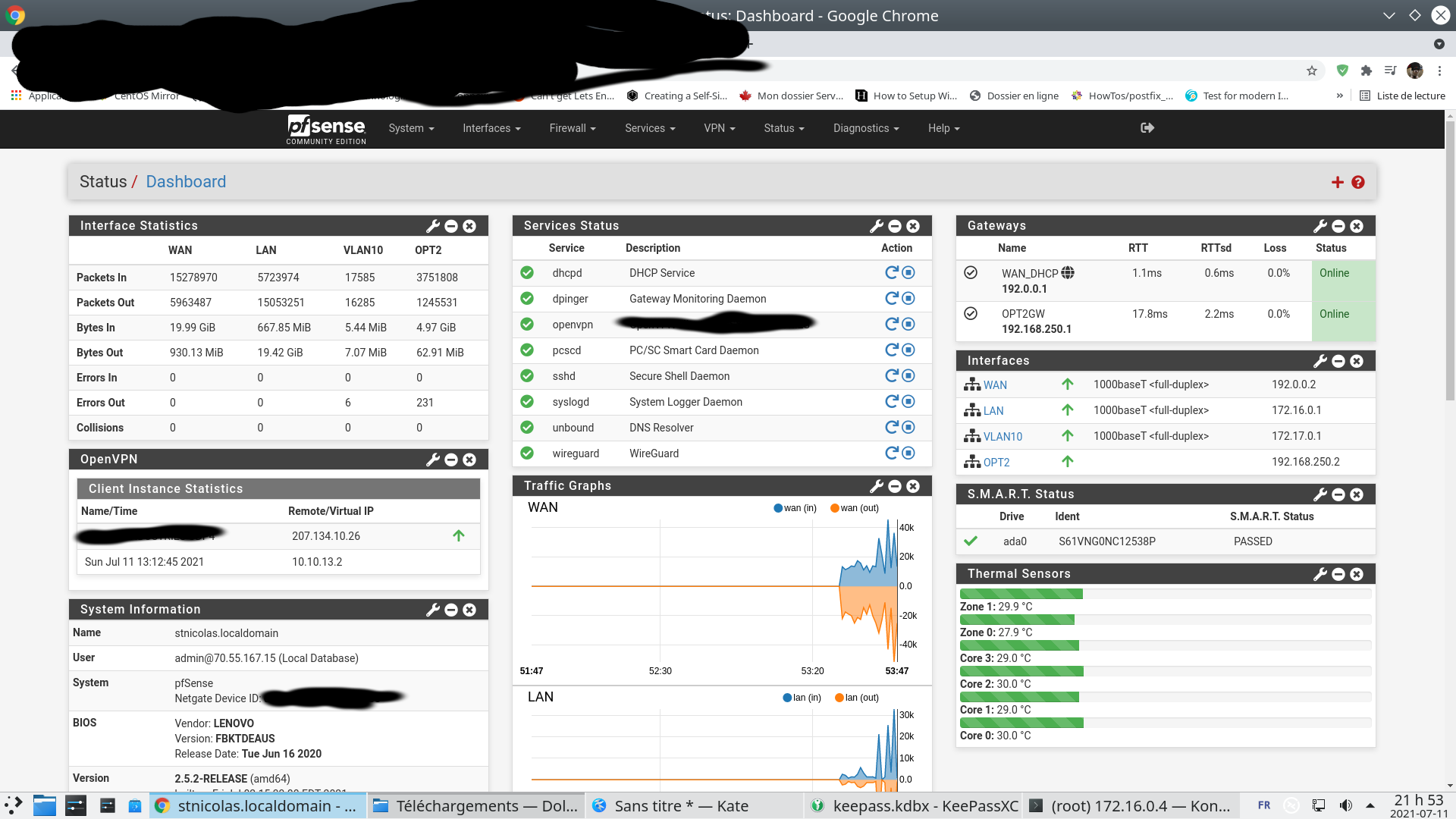
WireGuard site-to-site pfsense-to-pfsense no handshake?
-
@mikki-10
like i said do backup remove all vpn and start from scratch only wireguard!never know
anyway if problem just restore
have a good one
-
Hi I am on OPT18 as the next interface, not gonna happen over night, plus all the firewall rules, that is a big one

-
@mikki-10
i tested on 2 pfsense today with no ovpn
no problemive did the same procedure on pfsense main office with lot’s of ovpn nothing was going as expected so ! look like openvpn is messing some shit arround
-
There was a closed github issue like that but just with IPsec, same thing.
-
question your openvpn problematic
is it on the clients side ? if so just add
nobind in the *.ovpnnobind
that it
here’s the symptoms client connect but traffic is not goiing thru .
-
It is also site-to-site pfsense-to-pfsense, not sure if that will do anything for that.
And other clients eg windows or linux, work just fine, but again that is an other tunnel in this case, but thanks for the tip

-
@mikki-10
hahahaha
i did some more digging !
this is hilarious !
now my wireguard SITEA GATEWAY is the ip of SITEB
and my SITEB GATEWAY is the ip of SITEA !
when the handshake occur all gateway are online !! and ping goes on !absolutely ASOME OR RIDICULOUS
I PUT THE CONFIG BASE ON YOUR IPInterface - Site 1
Description: WG
IPv4: Static IPv4
MTU: 1420
IPv4 Address: 192.168.77.1/24Gateway- Site 1
Interface: WG
Name: WG_Gateway
IPv4 Address: 192.168.77.2/24Interface - Site 2
Description: WG
IPv4: Static IPv4
MTU: 1420
IPv4 Address: 192.168.77.2/24Gateway- Site 2
Interface: WG
Name: WG_Gateway
IPv4 Address: 192.168.77.1/24 -
@mikki-10
My SITEA
-
-
Super nice, seems like we were able to help eachother out a bit then

I redid some of the steps, I now have one tunnel all working now!
-
Hello,
I also have the same problem, site to site impossible with Wireguard on pfsense in version 2.5.2.
You mentioned OpenVPN, Wireguard and IPSEC in the conversation, is your last messages for solving the problem about Wireguard? -
yes the problem is solve with wireguard just read the complete post
-
I have succeeded, in addition to adding the gateways on the interfaces, we must add the static routes.
If you follow the netgate documentation everything should be automatic :D ! -
already mentionned in that post
static routing is up there
just read carefully
every thing is there
-
Updated documentation is something we are working on
-
@yazur I will try to do my best to sum it up :)
- Create a tunnel, on Site 1 and Site 2, eg change the port number if you do not like the default value, generate the keys for the site, it follows the setup as below.
- Assign the interface (eg tun_wg0) and set a static IP, this is the tunnel network, set the MTU to 1420, see settings below, i use the subnet 192.168.77.0/24 in this exampel.
- Set a firewall rule (UDP) to allow traffic on the WAN interface to the Wireguard tunnel port. (eg UDP port 51820 to WAN address on the WAN interface) (And no it is not a NAT rule (Port forward))
- Set the needed firewall rules for WireGuard and the WireGuard interface WG
- Add the peers, on both sites, where the public key for the peer is the opposite sites public tunnel key. At least one of the peers shall have an endpoint, the opposite can be dynamic. So the site that have and public IP, can have its peers to be dynamic, we can call that site the server (the site with an public IP) and the other sites for clientes (those eg behind a CGNAT) if you like. Also add Allowed IPs here, you will need to add the LAN IP and the tunnel IP subnets
- Add the gateway, with the opposite sites tunnel IP.
- The gateway should come online at this point and the handshake should now be green-
- Now set the need static route on both sites
Tunnel - Site 1
Tunnel: tun_wg0 (Site 1)
Public key: PK1Peer - Site 1
Tunnel: tun_wg0 (Site 1)
Endpoint: Dynamic
Public Key: PK2
Allowed IPs: <LAN Subnet of Site 2>
Allowed IPs: 192.168.77.0/24Interface - Site 1
Description: WG
IPv4: Static IPv4
MTU: 1420
IPv4 Address: 192.168.77.1/24Gateway- Site 1
Interface: WG
Name: WG_Gateway
IPv4 Address: 192.168.77.2Tunnel - Site 2
Tunnel: tun_wg0 (Site 2)
Public key: PK2Peer - Site 2
Tunnel: tun_wg0 (Site 2)
Endpoint: <Public IP of Site 1>
Public Key: PK1
Allowed IPs: <LAN Subnet of Site 2>
Allowed IPs: 192.168.77.0/24Interface - Site 2
Description: WG
IPv4: Static IPv4
MTU: 1420
IPv4 Address: 192.168.77.2/24Gateway- Site 2
Interface: WG
Name: WG_Gateway
IPv4 Address: 192.168.77.1 -
@mikki-10 said in WireGuard site-to-site pfsense-to-pfsense no handshake?:
Peer - Site 2
Tunnel: tun_wg0 (Site 2)
Endpoint: <Public IP of Site 1>
Public Key: PK1
Allowed IPs: <LAN Subnet of Site 2>
Allowed IPs: 192.168.77.0/24I made a small mistanke, and can not edit my post?
Allowed IPs: <LAN Subnet of Site 2> should be <LAN Subnet of Site 1>Peer - Site 2
Tunnel: tun_wg0 (Site 2)
Endpoint: <Public IP of Site 1>
Public Key: PK1
Allowed IPs: <LAN Subnet of Site 1>
Allowed IPs: 192.168.77.0/24 -
wow your nice guys
every thing was already said in all the post for a pfsense user to do their jobs !
reposting all the procedure was kind of useless but friendly :)
have a nice one bro
-
Thank you for this summary!
I hope it helps other people too :)! -
That’s for the tutorial. I was following a German dude tutorial on YouTube and setting gateways for site 1 the site 1 ip and for site 2 the site 2 up. Result was losing handshake and pings after a few hours or randomly. Even with keep alive settings.
For now I reverted back to IPSec for site to site vpn as is more stable and easy to setup. Manual creation of static routes and gateways it’s as bit of pain if you’re on relatively big environment.
I know, I know… it’s experimental. Works great for mobile warriors though.