[SOLVED] How to access cable modem login [Rogers Hitron 192.168.100.1]
-
@guardian said in How can I access cable modem control on 192.168.0.1:
pub.lic.ipa.ddr.20075 > 192.168.0.1.80
In that situation the modem often has no way to responf to the public IP, it only has the private IP. So you need to add an IPAlias on the WAN in the 192.168.0.X subnet and NAT traffic to it to reach the modem. That way the modem can respond.
Steve
-
Thanks very much for the replies @stephenw10 @JKnott @steveits @kom
@jknott said in How can I access cable modem control on 192.168.0.1:
I no longer have a Hitron modem, but I seem to recall a different address. Also, IIRC, the address depends on whether you're in bridge or gateway mode
Thanks so much for this.... I happened to notice something going on with 192.168.100.1, and I just tried to access http://192.168.100.1 and got the log in page.
--
@steveits said in How can I access cable modem control on 192.168.0.1:
If 192.168.0.1 is not in your LAN subnet it should work. (if it is, then you need to change one of them).
In Interfaces/WAN see if "Block private networks and loopback addresses" is unchecked but IIRC it will work without that since the default LAN->any rule should allow the outbound request.
I'd make another thread for the web GUI question but the only issue I've ever seen re: no WAN is that the pfSense GUI can be slow if it's working its way through multiple DNS server timeouts (e.g. for the dashboard update lookup). What you're describing sounds like the PHP process crashing. Check the log?
Just checked the log, and I was getting one or two of these per second:
May 8 00:15:29 XXXXXXXX kernel: arpresolve: can't allocate llinfo for xxx.xxx.xx.1 on em0When I power cycled the modem I started getting:
May 8 00:16:08 XXXXXXXX kernel: arpresolve: can't allocate llinfo for 192.168.100.1 on em0I also have an OpenVPN Server that is pushing out quite a few messages as it is trying to get reconneced.
I also got a couple of these
May 8 00:11:34 XXXXXXXX php-fpm[80642]: /rc.linkup: The command '/usr/sbin/arp -s 'LANVPNIP.1' '00:28:1a:e0:10:05'' returned exit code '1', the output was 'arp: writing to routing socket: Operation not permitted'I'm assuming the CPU is so busy the GUI can't run (Am I correct that the GUI runs a lower priority as well). The shell was quite responsive, but other than killing PHP-FPM, I wasn't really sure what to do.
Given that the link has gone down, I can understand why these messages would be being generated, but I'm wondering if some sort of throttling/rate limiting should be added or if I need to make some sort of configuration change. Hopefully one of the devs will see this and can comment if this gives rise to an possible improvement. It's not great when something is going on with the ISP and the WebGUI is not responsive.
@kom said in How can I access cable modem control on 192.168.0.1:
Thanks for this.... It seems like I lucked out and I can access my login without the change. Thanks to @JKnott, I just figured out that the address printed on the modem is only valid for normal mode, and not bridge mode.
-
@guardian said in [SOLVED] How to access cable modem login [Rogers Hitron 192.168.100.1]:
Thanks for this.... It seems like I lucked out and I can access my login without the change. Thanks to @JKnott, I just figured out that the address printed on the modem is only valid for normal mode, and not bridge mode.
Now you can get IPv6 going. Rogers provides a /56 prefix.
-
@jknott said in [SOLVED] How to access cable modem login [Rogers Hitron 192.168.100.1]:
Now you can get IPv6 going. Rogers provides a /56 prefix.
So far I've been afraid to have anything to do with IPv6 because I haven't learned how do deal with the security. Any pointers (external references) would be much appreciated.
-
Block all incoming unsolicited connections. Allow out only the connections you need.
Same as IPv4.
Only NAT is significantly different there and relying in NAT for security is not security.
Steve
-
As @stephenw10 says, there's not a lot of difference. You just create the same rules and can even include both IPv4 and IPv6 in the same rule. As usual, you start by blocking everything and then adding exceptions to allow what you need. One difference is with consistent and privacy addresses. If you have a specific address for an incoming rule, you specify the consistent address. The privacy addresses are used for outgoing connections and you get a new one every day, up to 7 of them. The consistent address is often based on the MAC address, but can also use a random number. Either way, it doesn't change.
One really big difference is the huge address space. I mentioned Rogers provides a /56 prefix. That means you get 256 /64 prefixes, each of which contain 18.4 billion, billion addresses. You use a /64 for each local interface. For example, I have them for my main LAN, guest WiFi, test LAN, VPN and a Cisco router I have. You can filter on the entire /56, individual /64s or some combination. In my case, I have rules that apply to the /56, to control what's allowed in, but also rules on my guest WiFi that block guests from reaching my other networks.
Regardless, there are many here with IPv6 experience (I've been running it for over 11 years) and also with Rogers, again me.
BTW, Rogers also provides a /64 for devices tethered to a cell phone.
-
@stephenw10 said in [SOLVED] How to access cable modem login [Rogers Hitron 192.168.100.1]:
Block all incoming unsolicited connections. Allow out only the connections you need.
Same as IPv4.
Only NAT is significantly different there and relying in NAT for security is not security.
Steve
The problem for me is the address space is so damn big it's hard to deal with--and there is an education factor that I don't know what I don't know and I'm afraid that I don't know, so I'm holding on as long as I can.
-
@jknott said in [SOLVED] How to access cable modem login [Rogers Hitron 192.168.100.1]:
As @stephenw10 says, there's not a lot of difference. You just create the same rules and can even include both IPv4 and IPv6 in the same rule. As usual, you start by blocking everything and then adding exceptions to allow what you need. One difference is with consistent and privacy addresses. If you have a specific address for an incoming rule, you specify the consistent address. The privacy addresses are used for outgoing connections and you get a new one every day, up to 7 of them. The consistent address is often based on the MAC address, but can also use a random number. Either way, it doesn't change.
One really big difference is the huge address space. I mentioned Rogers provides a /56 prefix. That means you get 256 /64 prefixes, each of which contain 18.4 billion, billion addresses. You use a /64 for each local interface. For example, I have them for my main LAN, guest WiFi, test LAN, VPN and a Cisco router I have. You can filter on the entire /56, individual /64s or some combination. In my case, I have rules that apply to the /56, to control what's allowed in, but also rules on my guest WiFi that block guests from reaching my other networks.
Regardless, there are many here with IPv6 experience (I've been running it for over 11 years) and also with Rogers, again me.
BTW, Rogers also provides a /64 for devices tethered to a cell phone.
Wow! I'm impressed. I assume you do networking for a living? Where can someone who isn't a network engineer reasonably get up to speed with this?
There is much more setup tutorials on the net now, but I struggled setting up multiple VLANs with the appropriate routing/firewall rules with some routed to OpenVPN and an incoming OpenVPN server. To get to the nuggets of info I needed I had to wade though a ton of stuff about multiple levels of distribution over many floors/buildings and try and scale that back to my home network.
I'm familiar with IPv6 address, but I haven't heard about consistent address/privacy address before. Eventually we are all going to be forced this way, and it's good to be ready. Other than that are there any immediate benefits to IPv6 for you as a user?
-
The size has nothing to do with it. As I mentioned, you can block your entire prefix, an individual /64 or even a single address. This is no different than IPv4. However, as mentioned before, you start by blocking everything, as always. I suspect a large part of the problem is people have been using NAT for so long they think it's normal, when it's in fact a hack that causes it's own problems.
If you have questions, we're here to help.
BTW, here's my WAN rules.
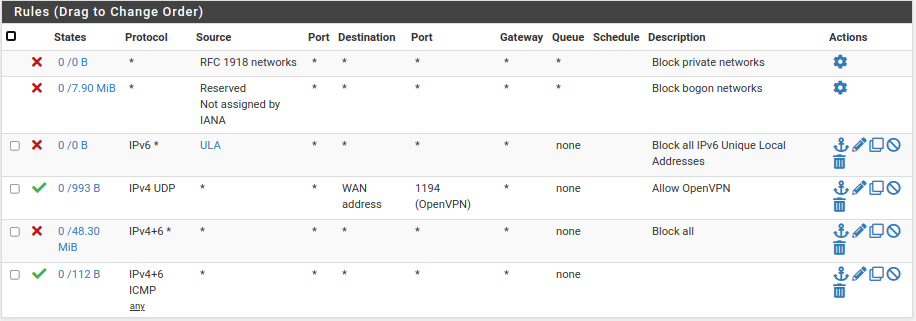
And my Guest WiFi rules, to keep guests off my local networks.
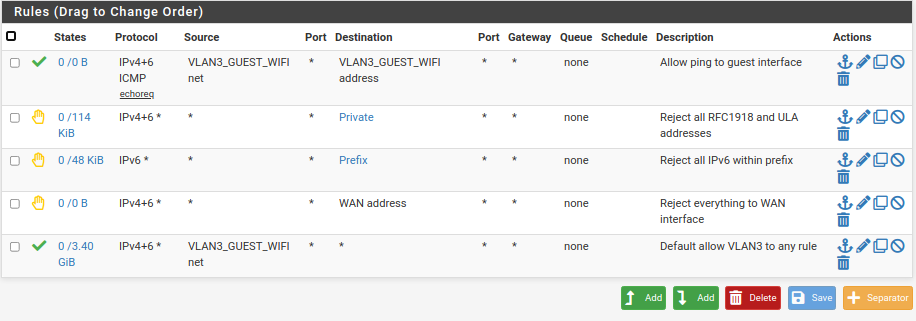
As you can see, they're not all that complex.
-
@jknott said in [SOLVED] How to access cable modem login [Rogers Hitron 192.168.100.1]:
The size has nothing to do with it. As I mentioned, you can block your entire prefix, an individual /64 or even a single address. This is no different than IPv4.
...
As you can see, they're not all that complex.Thanks very much for the reply... Guest WLAN is a pretty simple case, guest stays off your net, and can do almost anything else.
On my main VLAN, I can't do too much about http/https, but I keep a pretty tight reign on ssh, imap, ssmtp, etc. with explicit allow lists for destination. Sometimes it bites me in the butt, but I'm pretty much default deny.
What about for VLANs, and do you run pfBlocker or other adblocker/security tools?
-
The only VLAN I currently have is the Guest WiFi and I don't do anything other than the rules you see. I run adblocker addins in my browser, not pfsense.
-
@guardian said in [SOLVED] How to access cable modem login [Rogers Hitron 192.168.100.1]:
but I'm pretty much default deny.
Why? Do you think your going to infect yourself running any old code you come across? I get this in a company network - where you have "users"
But why would you do such a thing on your own network - do you have kids running crazy across the net running anything they can download? Visiting shoddy websites? etc..
ssh, imap
Your worried your some rouge device on your network is going to go about access this ?
-
@johnpoz said in [SOLVED] How to access cable modem login [Rogers Hitron 192.168.100.1]:
@guardian said in [SOLVED] How to access cable modem login [Rogers Hitron 192.168.100.1]:
but I'm pretty much default deny.
Why? Do you think your going to infect yourself running any old code you come across? I get this in a company network - where you have "users"
But why would you do such a thing on your own network - do you have kids running crazy across the net running anything they can download? Visiting shoddy websites? etc..
ssh, imap
Your worried your some rouge device on your network is going to go about access this ?
Hi @johnpoz my main concern is Visiting shoddy websites... but with some of the "adjacking" almost anysite could become "shoddy", and with the pandemic I am concerned that news sites (either mainstream and particularly new media may be hijacked). Even some attachment coming from a "supposedly trusted" source could be a problem.
The other thing is that by having a default deny that logs I can find out if there is something going on that I don't expect.
Unfortunately ports 80:443 and DNS over https are almost uncontrollable without making the network unuseable.
-
And how many hits do you get on ssh for example.. You understand that these shoddy websites are going to infect you over 80/443 right.. They don't tell your machine with some magic virus code come talk to me on ssh port 22 so I can infect you..
I just don't see any reason to cause yourself pain when it provides really no extra security.. Your spending cycles locking yourself in a box.. Which you agree bits you in the butt... Just don't see why..
Stopping something from going outbound is already too late.. Your infected already..
Vs blocking xyz ports that almost never come into play in any sort of infection.. Isn't cost effective.. You should filter where you might go with lists of these shoddy sites for example blocked sure.. But limiting the outbound traffic ports - I don't buy it as a means of securing you from infection.. Its keeping in what is bad already.. When its bad already its too late..
-
Blocking outbound connections to lists of know malware servers or ad servers is easy and unlikely to cause problems. It can only help IMO, though just how much help is debatable.

Steve
-
@johnpoz said in [SOLVED] How to access cable modem login [Rogers Hitron 192.168.100.1]:
And how many hits do you get on ssh for example.. You understand that these shoddy websites are going to infect you over 80/443 right.. They don't tell your machine with some magic virus code come talk to me on ssh port 22 so I can infect you..
I just don't see any reason to cause yourself pain when it provides really no extra security.. Your spending cycles locking yourself in a box.. Which you agree bits you in the butt... Just don't see why..
Stopping something from going outbound is already too late.. Your infected already..
Vs blocking xyz ports that almost never come into play in any sort of infection.. Isn't cost effective.. You should filter where you might go with lists of these shoddy sites for example blocked sure.. But limiting the outbound traffic ports - I don't buy it as a means of securing you from infection.. Its keeping in what is bad already.. When its bad already its too late..
@johnpoz I haven't had the time to reply before now, but IIUC there have been a number of ransomware infections that were quite successfully shut down by blocking their C&C ports. I do agree with you that 80/443 is the most likely and more or less impossible to close from a practical point of view.
-
@guardian said in [SOLVED] How to access cable modem login [Rogers Hitron 192.168.100.1]:
I do agree with you that 80/443 is the most likely and more or less impossible to close from a practical point of view.
Its impossible to really block those ports at firewall, if you want the internet to work ;)
Stopping C&C would be a list of bad IPs/Networks - there are many of these lists available. To those you can block all ports, not just 80/443