Can't access second AP from clients connected to my main AP
-
I attached my diagram here.
I've been running my pfSense for a few years. Current version 2.4.5.
I usually use my dd-wrt AP as my only AP with multi-ssid associated with VLANs. Now I'm setting my 2nd AP; and wish both APs to be able to communicate to each other.All clients connected to my dd-wrt AP (main AP) and my TPLink AP (2nd AP) can obtain IPs from my pfSense and can access internet without problem.
What I can't do is to access my 2nd AP from clients connected to my main AP.
My main AP LAN allows to access all destinations. I'm not sure what else I have to set on my pfSense.My intention is to replace my DDWRT AP with a more powerful/stable Wifi6 consumer wifi router (only use it as my main AP) which do not support VLAN and multi-ssd; and intend to use my 2nd AP for mult-issd (VLAN supported) for iot devices, testing, guest, etc...

-
What addresses are on the DD-WRT? What are your rules?
-
@jknott dd-wrt itself ip is 192.168.2.254
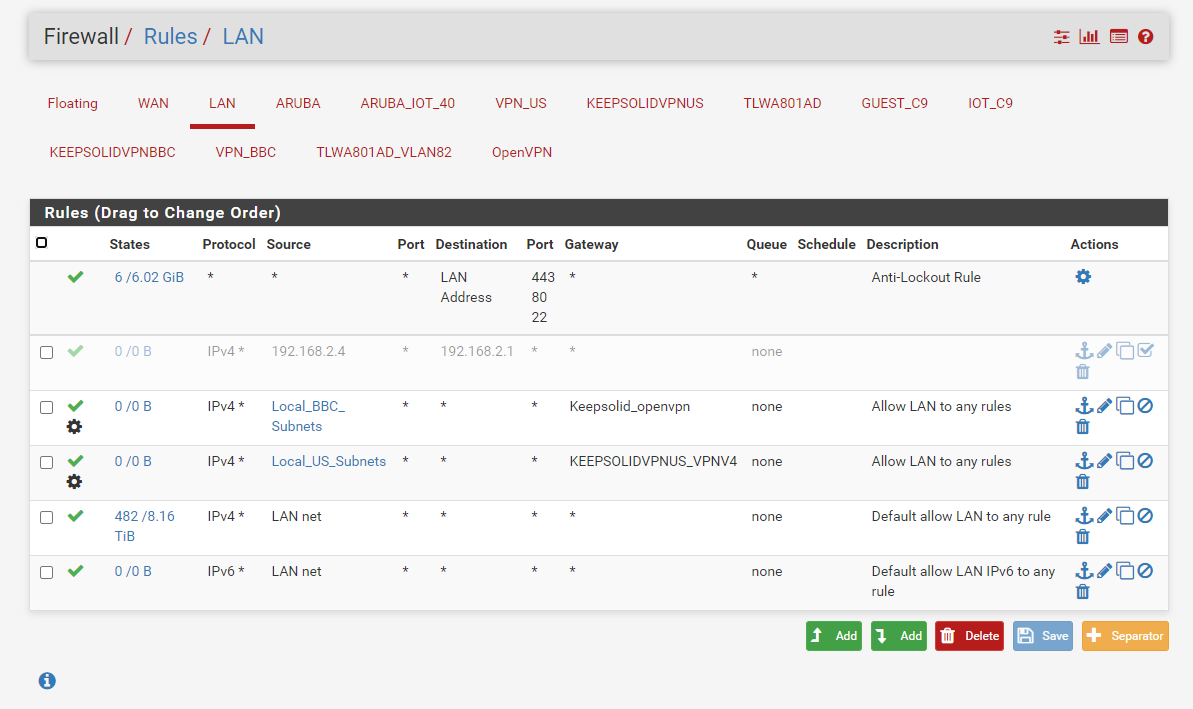
pfSense main AP Lan rules
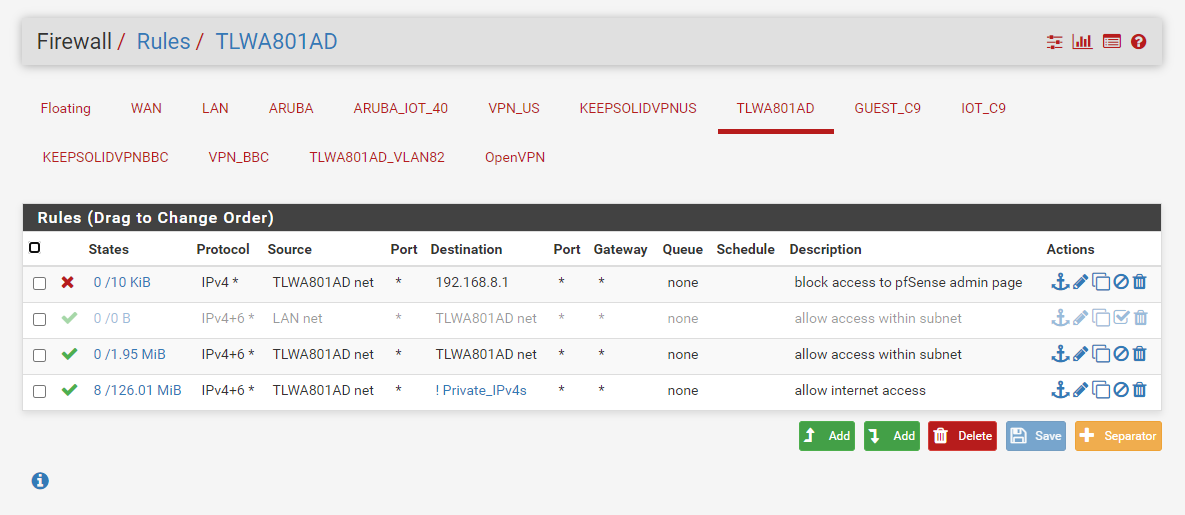
pfSense 2nd AP Lan rules
-
A question - and I hope it hides the answer ;)
Your DD-WRT is using VLANs.
So your pfSense should have as as many VLAN interfaces as the DD-WRT has - not only just one "LAN". Each VLAN interface should contain it's own pass rules.
Right ,And just to be sure : This one shouldn't be checked :

-
@gertjan All the vlans defined on my dd-wrt have corresponding VLAN interfaces on my pfSense; thus having their own firewall rules and dhcp servers.
ps: you can access my dd-wrt admin page?
-
@bthoven said in Can't access second AP from clients connected to my main AP:
ps: you can access my dd-wrt admin page?
Oops.
Ok, this is normally ruled by a very strict "Need to know" basis but I can guess I can inform you that :I have 3 DD-WRT devices running on my own Wifi network.

-
@bthoven said in Can't access second AP from clients connected to my main AP:
thus having their own firewall rules
Well, inspect them all.
Can you see traffic coming in ? check the counter, make the rules log - or even "sniff" (packet capture) if you have to. -
Just to clarify something, “AP isolation” in consumer grade routers doesn’t do everything you think it does. AP isolation only prevents wireless clients connected wirelessly to the same AP from talking to each other. It does not prevent Wireless Clients from talking to Wired Clients. Since @bthoven has two separate DD-WRT APs connected via hard wire, AP Isolation isn’t applicable when Client A is connected to AP1 and wants to communicate with Client B on AP2. DD-WRT doesn’t work like a true Mesh network, hence there is no “controller” that rules them all.
It’s easy to test by connecting a Wireless Client with AP Isolation turned on in DD-WRT and connecting a wired client to the switch or a free AP port. (I’m betting @bthoven has got 3 open ports on the APs as they are probably routers that have been turned into APs.) Disable the software firewalls on both wireless and wired clients. Try to ping each other and watch the replies flow. Yes, they can talk to each other even with AP isolation on. Only wireless clients attached to the same AP could not talk to each other.
Now products from Ubiquiti with “Controllers” have “Guest Policies” that can prevent wireless clients from talking to wireless and wired clients on the network. It’s probably because their APs have some managed switch/magic sauce in them.
-
@thatguy Thank you.
Only my main AP (Archer C9 wifi router turned to DD-WRT AP) is running DD-WRT.
My 2nd wifi AP is a one-ethernet-port AP (Tplink TL-WA801ND with its stock firmware) which supports 4 multi-ssids with associating VLAN ids. -
What IPs are you actually trying to connect between?
I assume you have those NICs bridged in pfSense? Or at least the VLANs bridged?
You have something there that seems to be labelled 'VLAN1 tagged'.
Is that actually a VLAN tagged 1? You should avoid using VLAN1 if at all possible.Steve
-
@stephenw10
What IPs are you actually trying to connect between?
e.g. 192.168.2.90 (main AP LAN)---> 192.168.8.254 (my 2nd AP network IP for admin)I assume you have those NICs bridged in pfSense? Or at least the VLANs bridged?
no. Do I have to, why?You have something there that seems to be labelled 'VLAN1 tagged'.
Is that actually a VLAN tagged 1?
I don't know because my 2nd AP VLAN ID settings do not have tagged optionYou should avoid using VLAN1 if at all possible.
As mentioned in my previous reply, I did try replacing VLAN id 1 with other id number, I can no longer access internet from any clients connected to all ssids. -
Update: The only IP address on my 2nd AP that I can't access from hosts on my main IP is 192.168.8.254 which I assign as my 2nd AP network IP (to manage my 2nd AP via 192.168.8.254).
I can ping from hosts connected to my main AP to other hosts connected my 2nd AP. -
@bthoven said in Can't access second AP from clients connected to my main AP:
Update: The only IP address on my 2nd AP that I can't access from hosts on my main IP is 192.168.8.254 which I assign as my 2nd AP network IP (to manage my 2nd AP via 192.168.8.254).
You set the gateway on this AP2 ?
It should be the IP of the pfsense LAN where it is connected to . -
If you're just routing between subnets there is no need to bridge anything. That should work fine as long as there are rules to pass the traffic in pfSense.
The most likely cause here is that AP2 does not allow connections to it's management interface from outside it's own subnet. At least by default, you may be able to enable it.
You could work past that with an outbound NAT rule in pfSense if you have to.
Steve
-
@stephenw10 Thanks. I start to believe what you said that my AP2 does not alow connections to its management interface from outside its own subnet. My Aruba AP connection with similar manner doesn't have such problem.
I'm not sure how to set outbound NAT rule in pfSense. Could you elaborate more? I intend to allow my main AP LAN 192.168.2.0/24 to access 192.168.8.254 (my 2nd AP).
Update: I create this outbound NAT, and now I can access the 2nd AP admin page from my main LAN client...Do you think the setting needs to be tweak? Will it have any side effect to any other access?

-
That looks good if you need to be able to access it from any IP in the main LAN subnet.
You can set the address family to IPv4 only.
Of course it would still be better to just set that subnet as allowed in the AP if possible.
Steve
-
@stephenw10 Thanks. I changed it to ip4 only as you suggested. I may be limiting only one main LAN ip to access it.
I can't do anything else on my 2nd AP because it has limited setting options.
Thanks again.