pfSense behind ISP Router
-
@kom Thanks for the reply, I will give them a call and see if I can switch the modem to bridged mode. As for the LAN clients, they can ping 8.8.8.8 and resolve www.netgate.com.
Is there no workaround for the double-NAT config? Say I can't switch the modem to bridged mode, that means im screwed?
-
@networkingpeasant OK so LAN clients seem to be working. I'm confused by what you meant when you said LAN clients had Internet but couldn't communicate with devices outside the firewall. What devices? The machine at .2.68? How is .2.68 connected here, direct from an ethernet port on the modem?
Unless you are able to configure port forwards on the modem (very unlikely) then unsolicited inbound traffic from the Internet won't be forwarded to your LAN. Not much you can do without bridge mode.
-
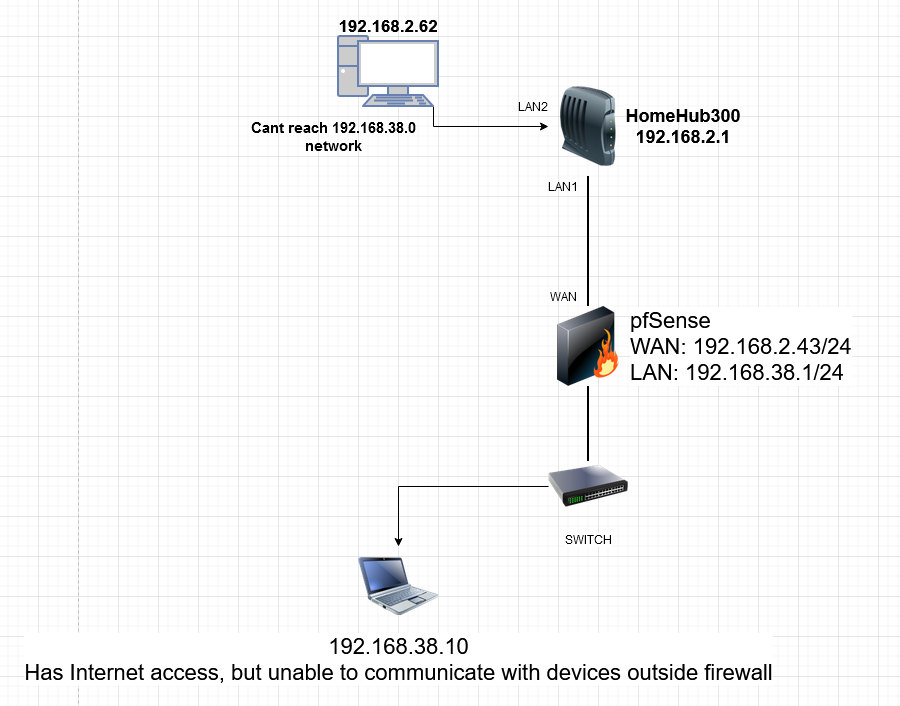
@kom So I have my laptop behind the firewall. It can access the internet with no problem. When I ping my PC (192.168.2.62) from my laptop (192.168.38.10) or vice versa, there is no reply. The PC (192.168.2.62) is connected to a LAN port on the modem. I am able to configure port forwarding, if I were to port forward, what would I do?
I want to be able to access the pfSense web gui from my .2.62 PC
-
@networkingpeasant You don't need a port forward. You need to go to Interfaces - WAN and uncheck the Block private networks and loopback addresses box.
Next, go your Firewall - Rules. Select the WAN tab. Add a Pass rule for Source 192.168.2.68, Destination This Firewall, Dest Port 80 or 443 depending on what you configured WebGUI to use.
-
This post is deleted! -
Go, Interfaces, WAN, right at the bottom,
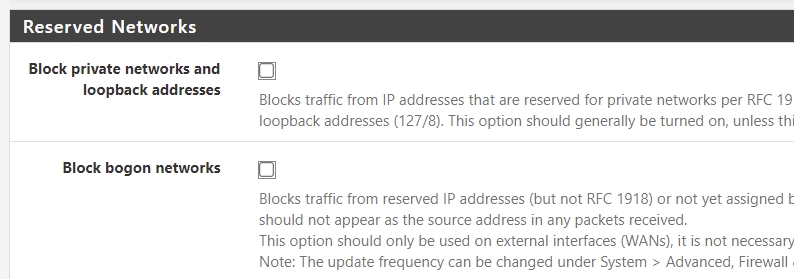
untick those two options.
save and apply
then in Firewall | Rules, LAN Tab, create rules where source is your LAN network and destination is ur wan ip addresses, and allow ports/protocol as required.
save | apply and test
-
@mr-rosh No luck
-
@kom No luck either
-
@networkingpeasant Don't connect anything other then the pfsense to the isp-router.
-
@bob-dig I will unplug the PC from the modem and into my switch (which is behind the firewall)
There are still 2 clients connected to the modem but i do not need access to them, will it affect them is anyway? -
@networkingpeasant technically to avoid further issues, move all devices off modem [except pfsense], and plug them into switch and ensure they are on 192.168.31.x ip range. reset should painless.
-
pfSense behind ISP Router
That kind of setup is not rare, I guess it's even the most common.
My ISP router uses 192.168.10.1/24 - pfSense obtains on it's WAN interface 192.168.10.3, because it's using the default DHCP client on WAN.
I can visit the GUI of my ISP router just fine : 192.168.10.1 :
If I was connecting some other device like a PC to my ISP router (it has a 4 port LAN switch), it would obtain an IP like 192.168.10.x/24 and I would be able to ping this device from behind pfSense.
My pfSense WAN firewall rules :
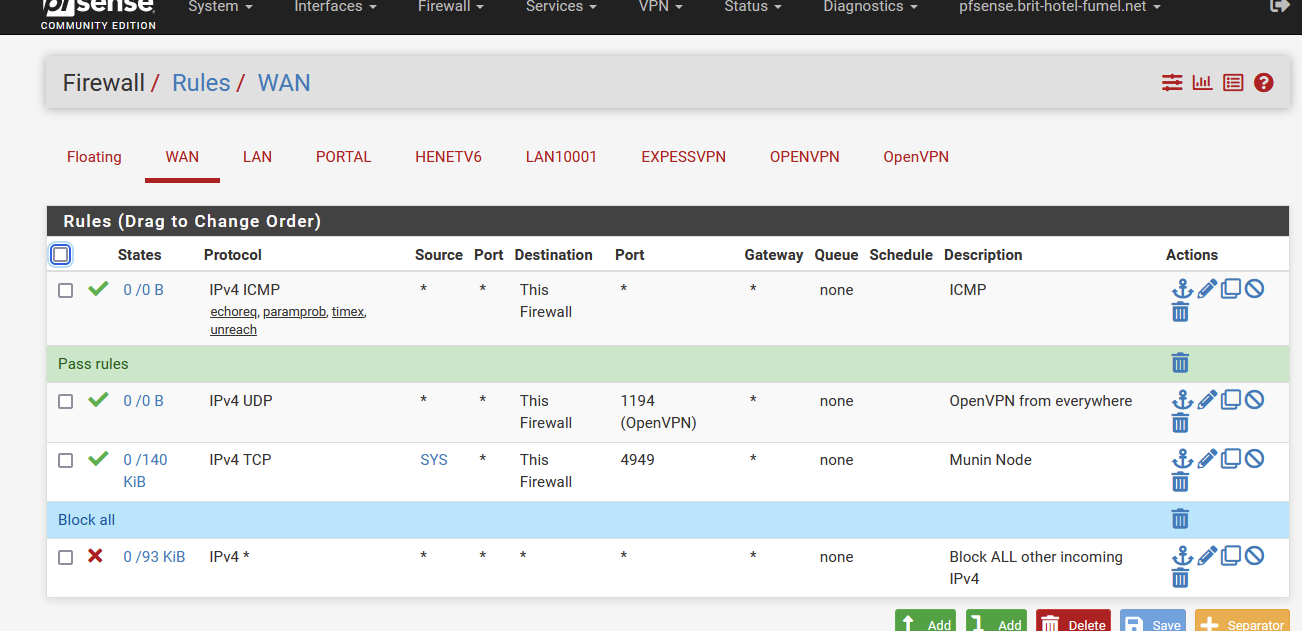
The first rule : my pfSense WAN IP (192.168.10.3) replies to ping. This is purely optional.
The second rule is my OpenVPN access from the outside world. My ISP router has the same NAT rule (entering UDP port 1194 to the IP of pfSense).
The third rule is sued for my "Munin" setup. Pure optionnal.
The last (4) rule is an explicit "block everything"As said above : you should plac all your local devices behind pfSense.
You shouldn't even use the Wifi capabilities of your ISP router, place an AP behind pfSense and use that one.There are exceptions : I have a TV box that has to be connected directly to the ISP box.
Some of us have a VOIP phone box, this should also be connected to the ISP router directly. -
@gertjan said in pfSense behind ISP Router:
If I was connecting some other device like a PC to my ISP router (it has a 4 port LAN switch), it would obtain an IP like 192.168.10.x/24 and I would be able to ping this device from behind pfSense.
In this scenario, your pfSense is behind the ISP router which a PC is connected to, and you would be able to ping that PC from the pfSense LAN devices? For me my LAN is 192.168.38.x, and i cant ping any devices outside the firewall, which use 192.168.2.x
-
@gertjan said in pfSense behind ISP Router:
The last (4) rule is an explicit "block everything"
Since when is this needed?