Keeping Source IPs
-
Maybe I missed a prior topic so bear with me. I have NATs and Rules setup.
I can see my pfsense server in destination server IIS Logs. Is there a setting retains the source IPs instead of replacing them with the NAT'd IP? so 8.8.8.8 (Example) is always 8.8.8.8 in my logs after being NAT'd and routed to my server ? -
@kbarrett
That is not the default behavior.Did you set a gateway on the internal interface facing to the web server in the interface settings?
Or are you running a reverse proxy on pfSense? -
@viragomann Not running the reverse proxy. and yes the webserver default gateway points to pfsense. Should I possibly consider running the firewall without NAT? Similiar to using Windows firewall only ?
-
@kbarrett said in Keeping Source IPs:
and yes the webserver default gateway points to pfsense.
The question was if you have stated a gateway in the interface setting on pfSense.
-
@kbarrett said in Keeping Source IPs:
d yes the webserver default gateway points to pfsense
and i said
Yes the webserver default gateway points to pfsense IPAddress. -
@kbarrett
Yes, I know. This is needed as well, but was not the question here. -
@kbarrett said in Keeping Source IPs:
Yes the webserver default gateway points to pfsense IPAddress.
That's not what was asked. He asked if you set up a GW in your interface that points to your web server. E.g. your webserver is on the LAN segment so do you have a gateway configured in your pfsense LAN interface settings NOT the webserver network configuration.
-
In the pfSense Interface, I do not believe we made any changes.
We accepted defaults for the values except time zone I believe. -
@kbarrett
During the installation process pfSense asks you for the interface settings like DHCP or IP address and gateway. Possibly you entered a gateway erroneously.
pfSense will consequently do masqerading on this interface.
So simply go to the LAN interface settings and verify that the gateway value is showing "none". -
Sorry for the extreme delays...other items got in the way.
No, we accepted the defaults for the installation/configuration opening screens. We were able to get NAT running and the Firewall rules working.
I have to imagine it is setup correctly with the proper options. Just wondering if there is an option that passes the source IP all the way, instead of replacing it with the NAT (Firewall) address. -
@kbarrett said in Keeping Source IPs:
wondering if there is an option that passes the source IP all the way, instead of replacing it with the NAT (Firewall) address
What you're asking for is the default behavior of all routers including pfSense. The web server on your LAN should not see the pfSense LAN IP address. If your config isn't complicated you might consider resetting it to factory defaults (diag menu) and starting over. Having been in IT for 30 years I'm not sure how I would even try to accomplish this except some sort of reverse proxy. :)
Rereading your post, where is the web server? On your LAN or outside the network? If outside, NAT will always use the WAN address for outbound connections, that's the point of NAT (public IPv4 address sharing). And one of the points of IPv6 (a quintillion addresses to everyone so everything has its own IP).
-
@steveits said in Keeping Source IPs:
All my replies are after the "-->"What you're asking for is the default behavior of all routers including pfSense.
--> Alright. Guess I am asking if it can allow the packets without changing the IP (Nat). If it is not possible ok.The web server on your LAN should not see the pfSense LAN IP address.
--> It is seeing it.If your config isn't complicated you might consider resetting it to factory defaults (diag menu) and starting over.
--> Yes did that.Having been in IT for 30 years I'm not sure how I would even try to accomplish this except some sort of reverse proxy. :)
--> Understood. That isn't what we are trying to do. We just want to use the firewall functions it seems not the NAT functions.Rereading your post, where is the web server? On your LAN or outside the network?
--> LAN SideIf outside, NAT will always use the WAN address for outbound connections, that's the point of NAT (public IPv4 address sharing). And one of the points of IPv6 (a quintillion addresses to everyone so everything has its own IP).
--> IIS Server on the inside of the network -
@kbarrett said in Keeping Source IPs:
is always 8.8.8.8 in my logs after being NAT'd and routed to my server ?
Where is the client talking to your webserver? If you were doing nat reflection and your client was on your network trying to access webserver via your public IP?
For this to happen from an external client out on the internet, you would have to be doing source nat via outbound nat rules. Post up your outbound nat rules..
example here are mine..
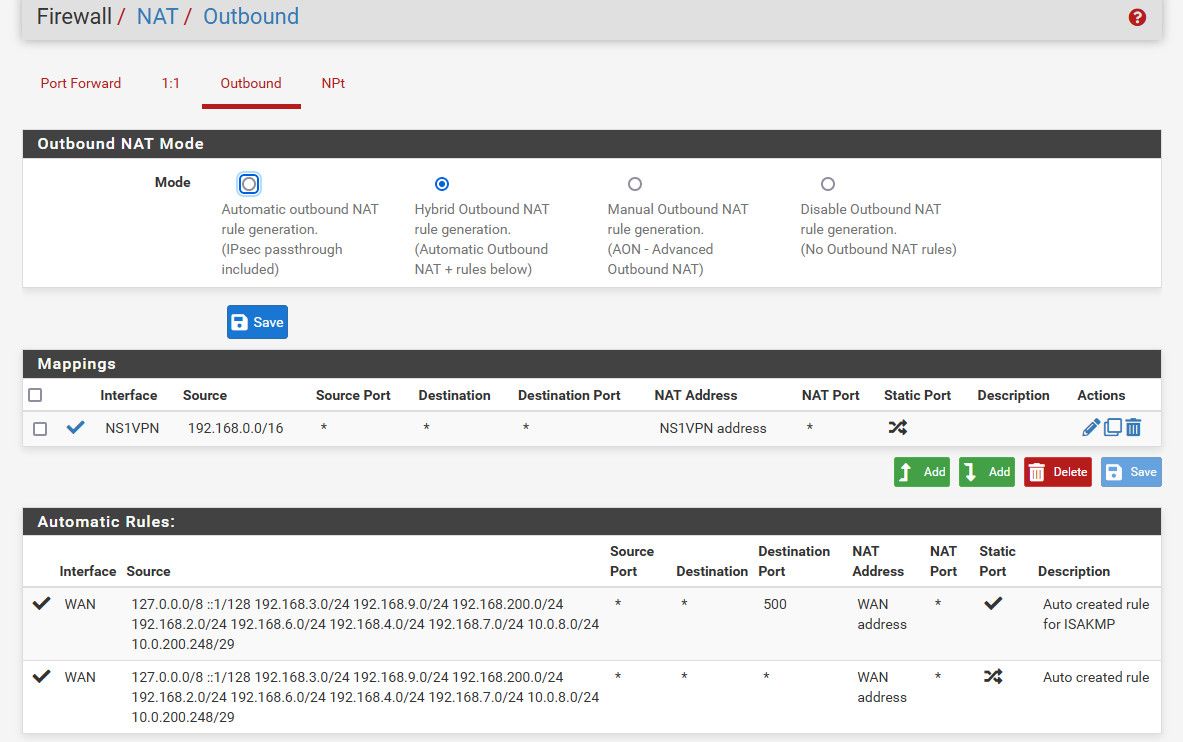
-
@johnpoz said in Keeping Source IPs:
Where is the client talking to your webserver? If you were doing nat reflection and your client was on your network trying to access webserver via your public IP?
For this to happen from an external client out on the internet, you would have to be doing source nat via outbound nat rules. Post up your outbound nat rules..
example here are mine..
My Comments are after the >>
Where is the client talking to your webserver?
External to the segment. Incoming from the internet.
If you were doing nat reflection and your client was on your network trying to access webserver via your public IP?
No internal traffic should use internal network.For this to happen from an external client out on the internet, you would have to be doing source nat via outbound nat rules.
Yes, I am NATing the incoming traffic.
Post up your outbound nat rules..
Company unfortunately wont allow it, but from your information it seems as long as I NAT I will not see the Internet IP in the logs on the webserver. i will only see the NAT device IP address. Is that a correct understanding ? -
@kbarrett said in Keeping Source IPs:
Company unfortunately wont allow it
Will not allow you to post up what? What your internal rfc1918 address are? WTF?? Someones tinfoil hat is so freaking tight its cutting off the blood flow..
Like giving away you live on main street. Without even knowing what country your in, let alone state, etc. Pretty worried about telling someone you live on the planet earth ;) There is zero issue with post up some arbitrary IP space, and interface be it wan or lan. Hide your rfc1918 space if you want. I just need to see if your using lan as an outbound nat..
Are you using public IP space internally?
Not sure how you expect help - when you come back 23 days later and don't even post up an answer to the question.
Yes, I am NATing the incoming traffic.
If you are source natting external traffic to your webserver - than yeah it is always going to see the IP you natted it too.. Why would you be doing that? Other than circumvention of some firewall running on where your forwarding too..
If you want to see the actual public IP of a client out on the internet talking to something you port forward traffic too, then don't source nat.. Do you understand the difference between a port forward and what I am saying with a source nat?
Do you have something in your outbound nat using the LAN interface? vs the WAN - if so that would be a source nat for traffic coming from the internet going to something on your Lan net..
Here - do you have something like this in your outbound nat rules?
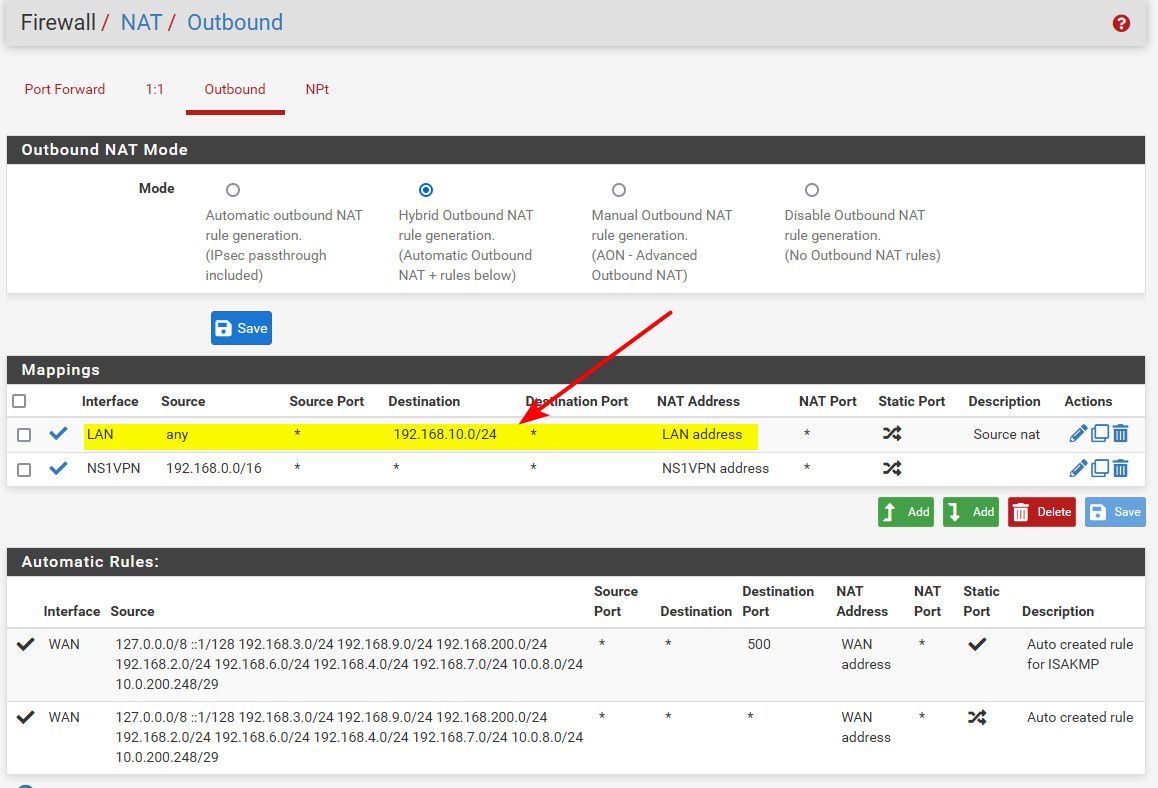
if I forwarded traffic to something on my 192.168.10/24 network - to that device on 192.168.10.X it would look like I am coming from the IP address of my Lan Address.. That is a source nat.
edit: BTW to any would be hackers - please don't hack me now that I have given away that my internal networks use rfc1918.. Like every other internal network on the planet ;)