pfSense 2.5.2 in HA/CARP is processing promiscuous traffic
-
When you add a CARP VIP to the interface it enables promiscuous mode but you should only see traffic that is sent to it. Traffic between other hosts in the WAN side subnet would not normally arrive at your WAN interface whatever mode the NIC is in.
There's not much you can do about that in pfSense. It's up to the upstream not to send it.
You can add block rules without logging if you just want to see it in the logs.Steve
-
@stephenw10 thank you very much for your answer. I really appreciated it.
I will try to add block rules with "no logging" as you suggested.
Could you please help me with an example rule?Sorry, I'm a newbie and I'm still at the beginnig.
Regards,
Mauro -
Well you might use a rule that looks like:
Source: WAN subnet
Destination: NOT WAN addressThat traffic has no business being on your WAN in most situations so you can add that as a block rule on WAN and simply don't enable logging.
Can we see the traffic that you are actually seeing logged currently?
Steve
-
@stephenw10 many thanks for your support.
Sure, I think I can do it :) but...how can I show you the traffic currently logged?
With a screenshot? Should I hide the IP addresses? Or I can send it via email?
Sorry, but it is my first timeAnyway I just noticed that the processed "external traffic" is essentially UDP
I don't know if it can help to help me :)thanks again
-
I would copy and paste the firewall logs here. Fudge the IPs if you need to.
What I expect to see there is UDP multicast/broadcast traffic. If that is the case it's legitimate to see it there.
Steve
-
@stephenw10 yes, you are right! the traffic is essentially UDP traffic.
I just copied the firewall logs and I removed the CARP IPs traffic.
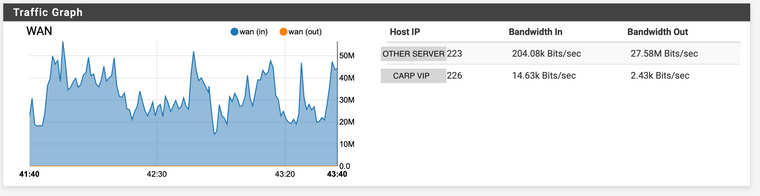
The traffic you will see below is the traffic that I don't want to process :)Anyway, I would add that, in PFSENSE GUI->Status Graph-> WAN (local), I can see:
- the traffic generated by CARP IP (is very low because behind the pfsense instance there are no hosts at this moment)
- tthee traffice generated by a different server on the same network (please see the attached image).
Jul 29 19:24:54 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:24:50 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:24:47 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:24:45 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:24:41 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:24:40 WAN 10.0.32.42:5353 224.0.0.251:5353 UDP
Jul 29 19:24:40 WAN 10.0.32.34:5353 224.0.0.251:5353 UDP
Jul 29 19:24:40 WAN 10.0.32.233:5353 224.0.0.251:5353 UDP
Jul 29 19:24:38 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:24:35 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:24:30 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:24:27 WAN 10.0.32.233:5353 224.0.0.251:5353 UDP
Jul 29 19:24:27 WAN 10.0.32.34:5353 224.0.0.251:5353 UDP
Jul 29 19:24:27 WAN 10.0.32.34:5353 224.0.0.251:5353 UDP
Jul 29 19:24:27 WAN 10.0.32.199:5353 224.0.0.251:5353 UDP
Jul 29 19:24:27 WAN 10.0.32.254:5353 224.0.0.251:5353 UDP
Jul 29 19:24:27 WAN 10.0.32.233:5353 224.0.0.251:5353 UDP
Jul 29 19:24:27 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:24:24 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:24:20 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:24:17 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:24:14 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:24:10 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:24:07 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:20:47 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:20:44 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:20:39 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:20:36 WAN 10.0.32.42:62784 239.255.255.250:1900 UDP
Jul 29 19:20:33 WAN 10.0.32.42:62784 239.255.255.250:1900 UDPThank you,
Mauro -
And more importantly they are all using multicast destination addresses so they are correctly ending up at your WAN locally. That traffic is just dropped until you have the NIC in promiscuous mode. Those logs are expected on an HA pair but you can still drop and not the traffic with a rule.
It's all UPnP and mDNS.https://en.wikipedia.org/wiki/Multicast_address
Steve
-
Yes, the NICs are in promiscuous mode ( I missed to say that pfsense instance is a virtual instance in HA on VMware ESXi v.7 ).
The promiscuous mode has been enabled following this:
https://docs.netgate.com/pfsense/en/latest/troubleshooting/high-availability-virtual.html
Thank you, Steve, for the time you spent helping me. much appreciated!
Mauro
-
Good morning, Steve.
I'm sorry to disturb you again, but, if it is possible, I would like to ask you a question. Please, let me know if I have to open a new case/thread on this forum.This is the question:
I successfully activated (on pfSense) HAproxy for web sites management.
So, users from the WAN are redirected to the right web server behind the firewall depending on the DNS name request.
Is there a way to do the same thing with FTP servers? I didn't find an "FTPproxy" in the pfSense packages list...Could you please help me?
Thank you in advance.
Mauro -
HAProxy can pass FTP using TCP mode but not with host-header matching like that. You can only do that with http, ftp doesn't send that information.
Steve