HA Site to Site IPSEC VPN Issues
-
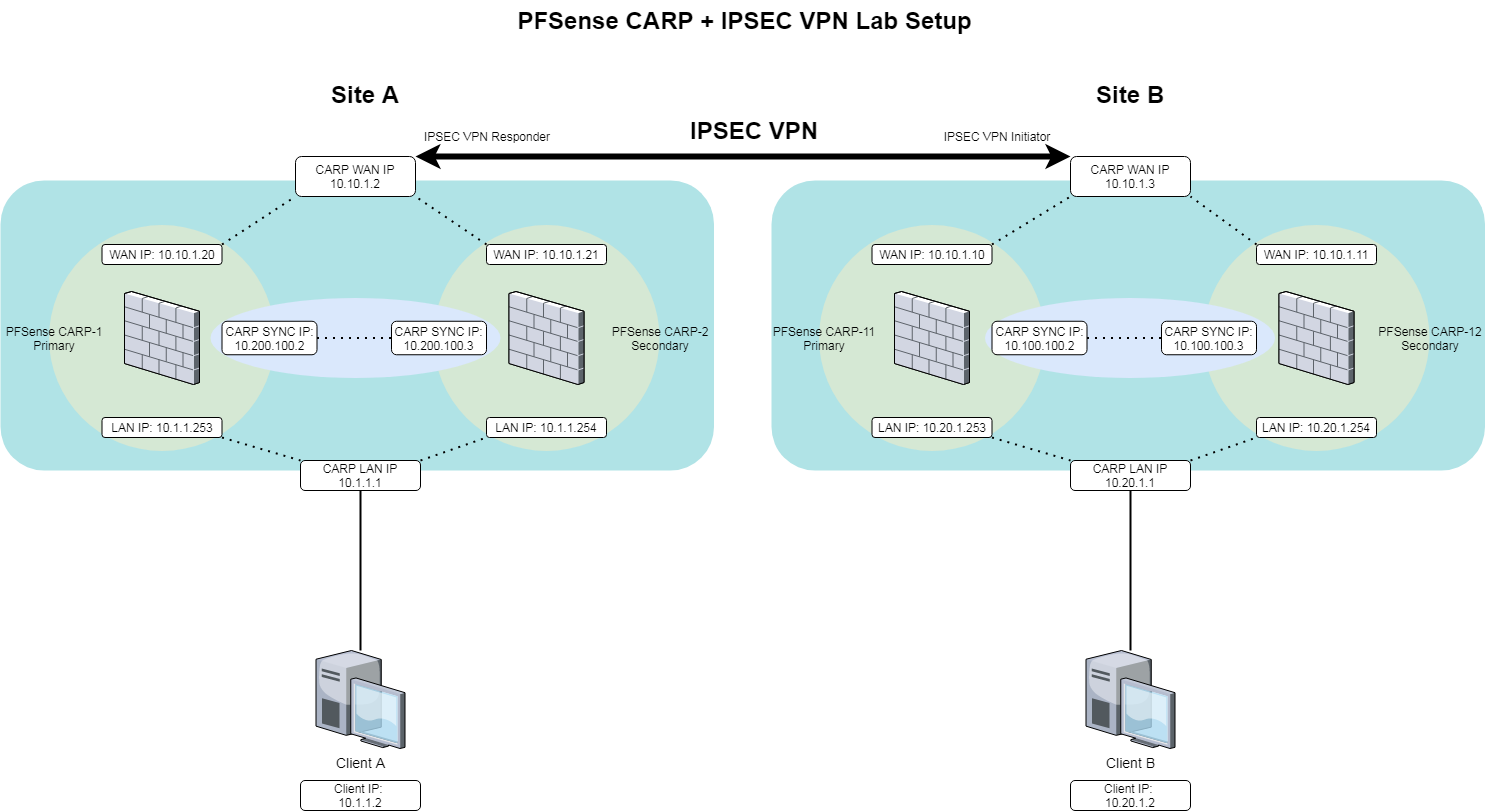
I'm labbing an HA Site to Site VPN configuration and have run into an issue when testing CARP fail-over where the VPN tunnel will not re-establish quickly when the Master PFSense in the IPSEC responder role goes down. I've tried OpenVPN instead of IPSEC but I don't get the throughput I need so I'm trying to find a way to make this work. I'm running the latest 2.5.2 on all systems in VM's on 2 Proxmox hosts.
Here's my test setup:
SITE A:
CARP WAN IP: 10.10.1.2
PFSense-CARP-1 WAN IP: 10.10.1.20
PFSense-CARP-1 SYNC IP: 10.200.100.2
PFSense-CARP-1 LAN IP: 10.1.1.253
PFSense-CARP-2 WAN IP: 10.10.1.21
PFSense-CARP-2 SYNC IP: 10.200.100.3
PFSense-CARP-2 LAN IP: 10.1.1.254
CARP LAN IP: 10.1.1.1
Client A IP: 10.1.1.2
SITE B:
CARP WAN IP: 10.10.1.3
PFSense-CARP-11 WAN IP: 10.10.1.10
PFSense-CARP-11 SYNC IP: 10.100.100.2
PFSense-CARP-11 LAN IP: 10.20.1.253
PFSense-CARP-12 WAN IP: 10.10.1.11
PFSense-CARP-12 SYNC IP: 10.100.100.3
PFSense-CARP-12 LAN IP: 10.20.1.254
CARP LAN IP: 10.20.1.1
Client B IP: 10.20.1.2
All settings match the netgate documentation regarding CARP setup and IPSEC VPN configuration and the CARP WAN IP's are being used as Interface and Remote Gateway in the IPSEC configuration. CARP configuration sync is functional on each pair and the Virtual IP takeover for LAN and WAN also functions for both. Traffic can pass from client A to B when the VPN is establish with no problem. Overall the setup works as expected.
The problem is that the VPN tunnel will not reestablish if the Master at Site A (set as the IPSEC Responder) goes down and the Secondary takes over as master. If the Master at Site B goes down, the tunnel drops for about 3.5 seconds then reestablishes and pings start passing again, the issue only happens if the Responder goes down.
Are there any tweaks are adjustments that I can apply to trigger tunnel reestablishment if the responder goes down?
-
Did you try
Child SA Close Action: Restart/Reconnectfor the Tunnel Configuration at Site B?