Multiple gateways on the same address space
-
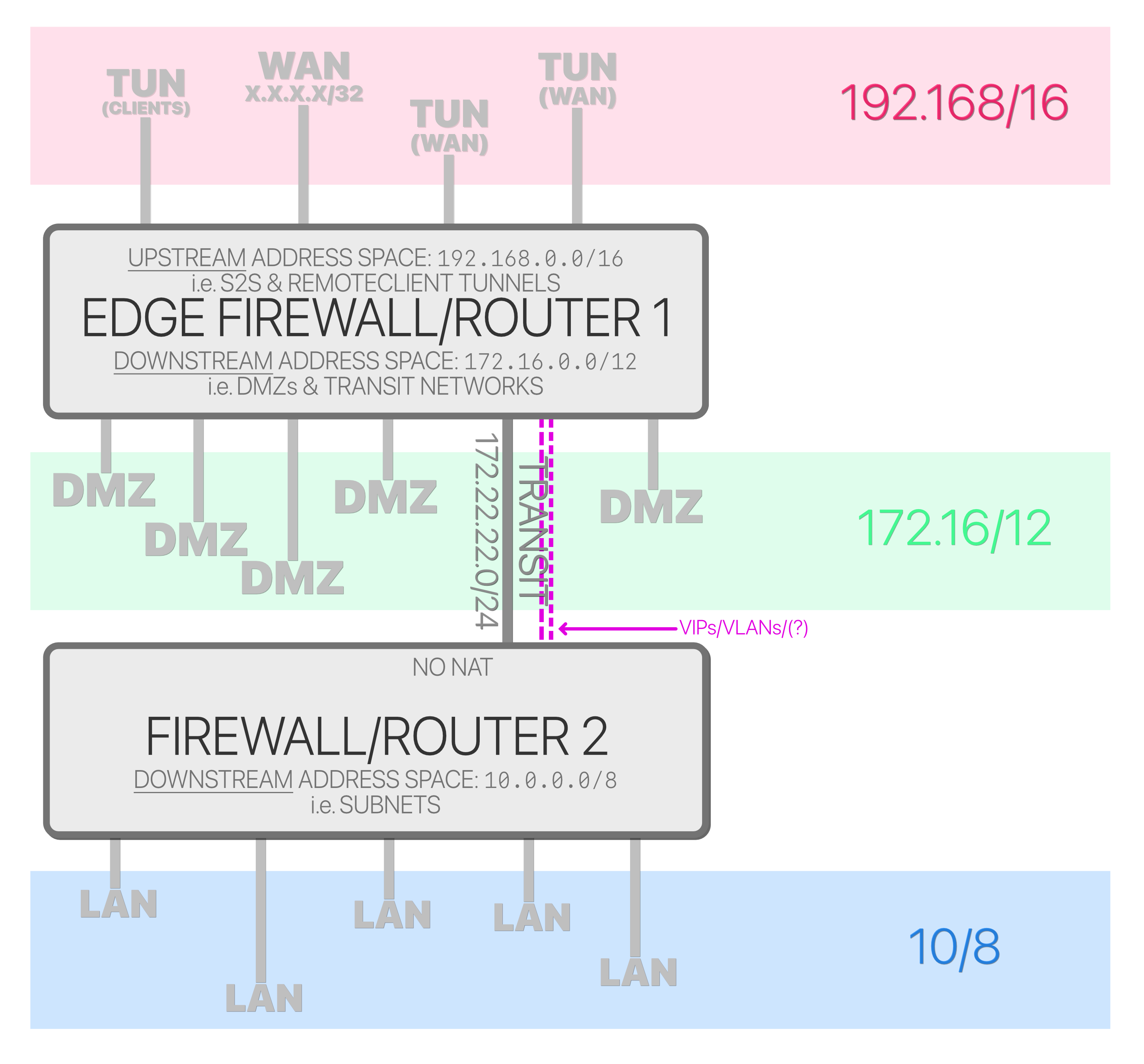
This is the topology:
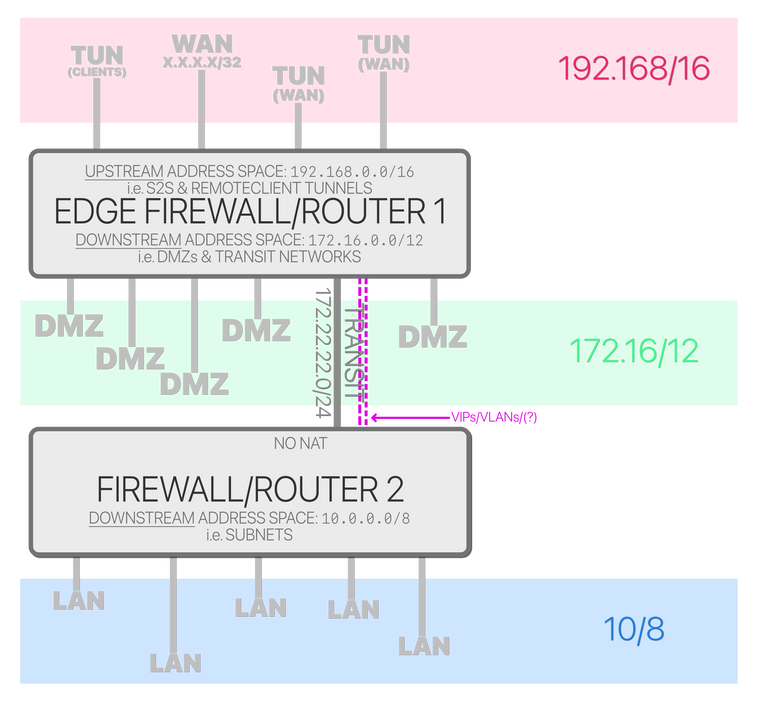
Each segment was put in the old IPv4 classes because it's super simpled and matched perfectly. The next step in this little setup is attempting to create more than one link between the firewall 1 & 2 so firewall 2 has multiple gateways available and the policy routing chores can be move downstream from the edge down.. In the edge a simple 1LAN:1WAN policy would be set.
But I can't think how to do it without removing very simple 10.0.0.0/8viaX static route in firewall one and breaking it into many smaller ones so it's not the same address space if I take the more-transit-VLANs-approach. On the other hand I could create VIPs in F1 and set the policy routes on them except, the traffic wouldn't be targeted at them but at
0.0.0.0/0--that and that I'm not sure how would I set them as downstream gateways anyway.I thought about some form of encapsulation; GIF, PPPoE, IKEv2, (…) to but they all would need NAT somewhere so I can set up policy routes in F2 and not in F1. It would essentially amount the same as using VLANs but with way more work.
There last thing I had in mind was OSPF, the first actually but I'm not good at it and I end up stopping traffic The old RIPv2 protocol probbly would work better in such small scale but it's now in the I-break-it-when-I-use-it- FRR

There are no other options, are they? (please say "yes, you forgot about X"), unrelated good/interesting ideas to try are welcome too!
Thanks ! -
I just remembered I can assign VIP on the WAN-side too (of F2)... I'm not sure what I'm doing because it will still be without NAT so F1 will have full visibility of the src address...
Is there a way to tag/mark packet/sessions/whatever across firewalls?? Like mos (decent) firewalls do, including pfSense, except a tag/mark that goes across firewalls. Is there one??
-
I slept on it and woke up with a workaround like if somebody had told me in sleep: URL Aliases.
Using transit networks means you have to make all the rules in a single interface, when you get near the hundreds editing anything on that page gets really tedious with how slow it becomes to load. You can still ⌘-click the edit link to speed things up a little editing in multiple tabs but to save each needs to wait or things get messed up.


In strict rulesets where each host has to be allowed out editing a text file in a web server--which can be accessed via SSH, WebDAVs, SMB, NFS even AFP!--is much faster and reduces the number or rules and therefore the load time of the page. Even if it didn't load faster, editing outside is way faster as long as it resolves faster (I set: System > Advanced > Firewall & NAT > Aliases Hostnames Resolve Interval >
60) and there's less chance of wandering off forgetting why you're there if you('ve/'re) OCPD/ADHD like I do. :)I don't want to say it's genius
 but I don't make the rules--oh wait…
but I don't make the rules--oh wait… 
-
UPDATE
I just hit a tiny snag, it turns out URL aliases can be update once a day at the soonest, unlike DNS based resolution. So, I can either (A) hack some cron job to force updates, although I think these would be resolved quicker because of pgBlockerNG that stores its rules there as well and has a timer to reload them or option B is to set a DNS record or delegation for it. Active Directory delegates DNS Service Discovery (
_dns-sd._udp.x.x.awesome way to ditch Avahi) to a macOS-based BIND9 server withdnsextdit's perfect for the job. :D