pfBlockerNG Content Filtering and FIREFOX DoH
-
I was working to ensure I could protect clients from going to 'wrong' sites like porn, etc. I noticed that MS Edge and Chrome resolved correctly using the unbound pfsense/pfblockerng tool for blocking unwanted sites that I picked out using:
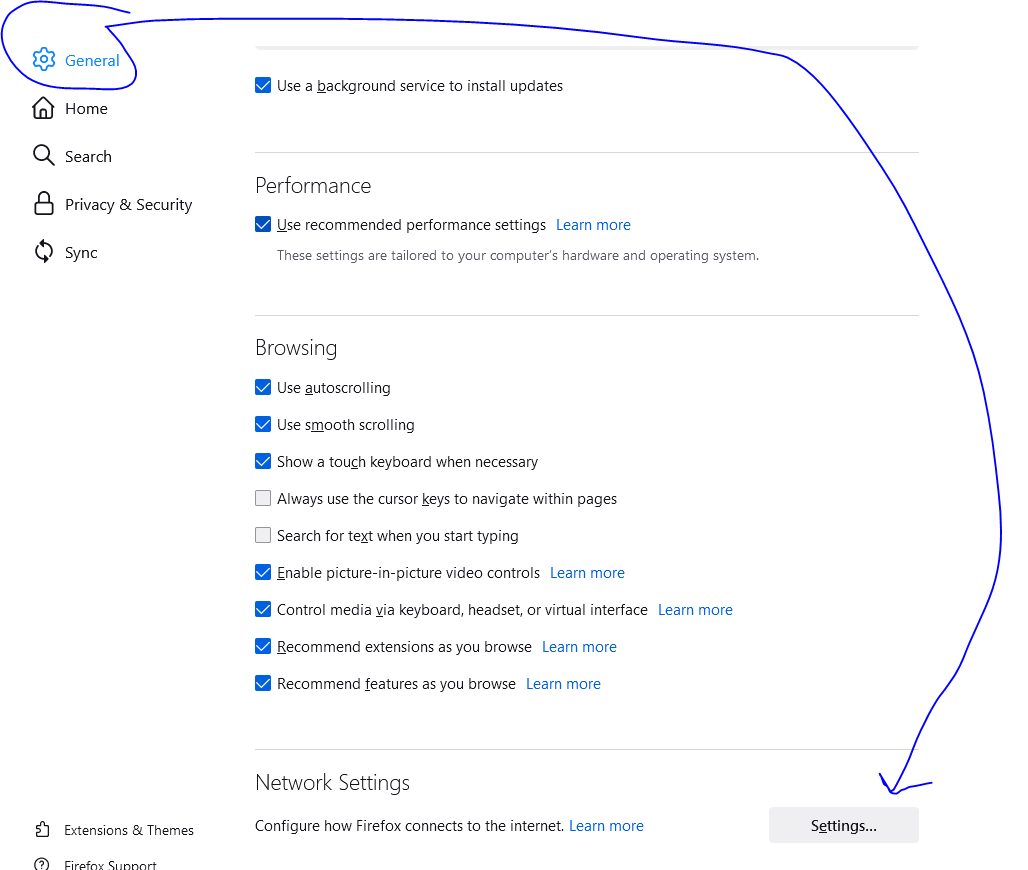
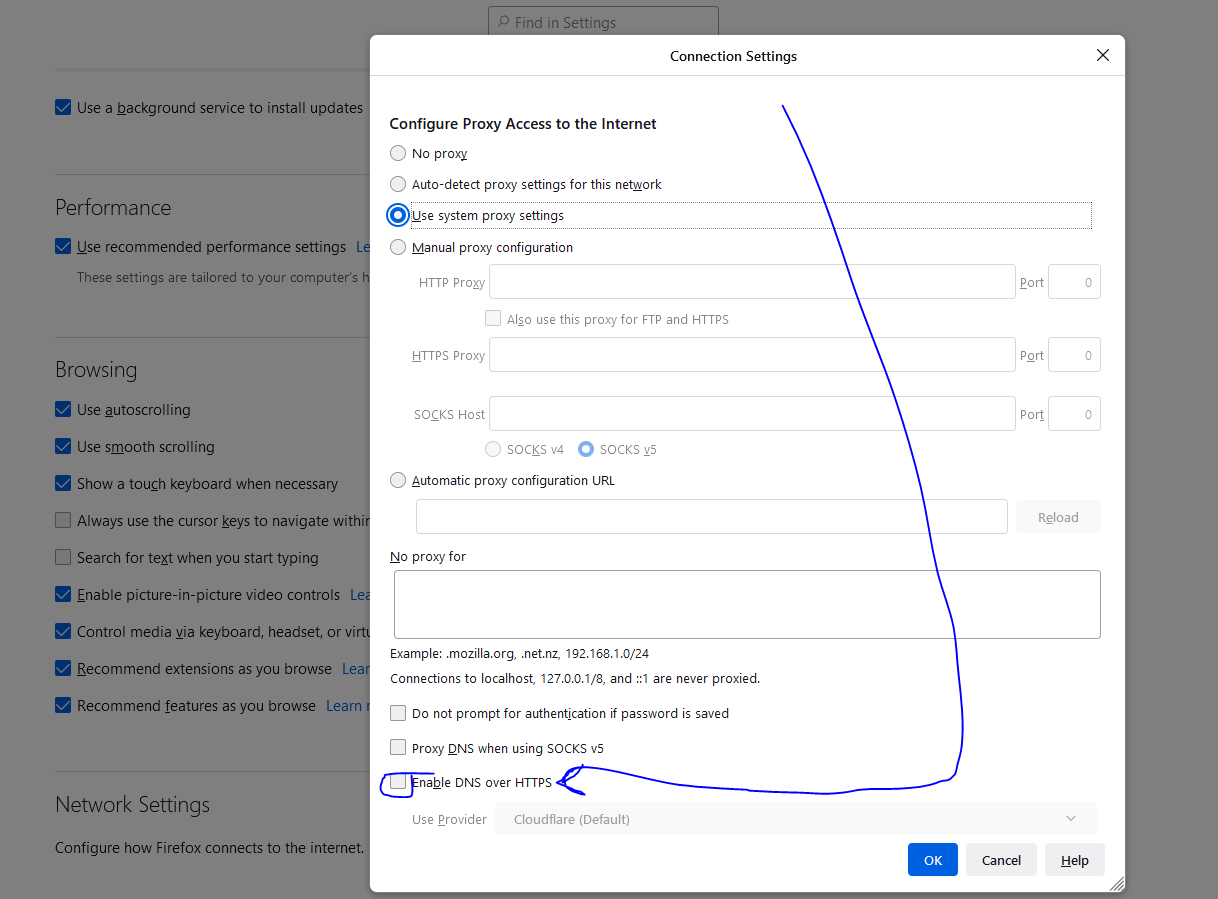
So, why wasn't FIREFOX working? Well, by default to day, it enables DNS over HTTPS. You will need to turn that off, each client browser so the browser will use pfsense. Directions are found here:
https://support.mozilla.org/en-US/kb/firefox-dns-over-https
I've read that eventually Edge and Chrome may follow the Firefox model. I hear of benefits of this technique. I don't know what to make of it. Comments welcomed....
Seems like an administrative nightmare for businesses ? and their end users. I suppose a script would or can or is being run to uncheck Firefox's default setting..
I UNCHECKED it in Firefox and now my browser uses the localhost catch all for unwanted browsing and it works now. I was banging my head for a bit. I had to read around to get familiar with DoH and then googled Firefox and DoH to find the culprit. I hope this helps someone. If you have any comments, I'm all ears. I want to be on top of my DNS game, even as novice as I feel I am at times.
-
-
What drives me nuts is, that the pfBlockerNG Settings to block DoH is not working all the Time
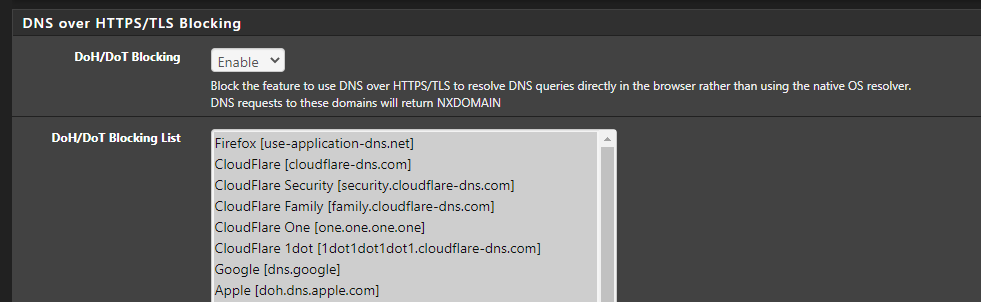
It blocks maybe every 4. to 10. attempt.
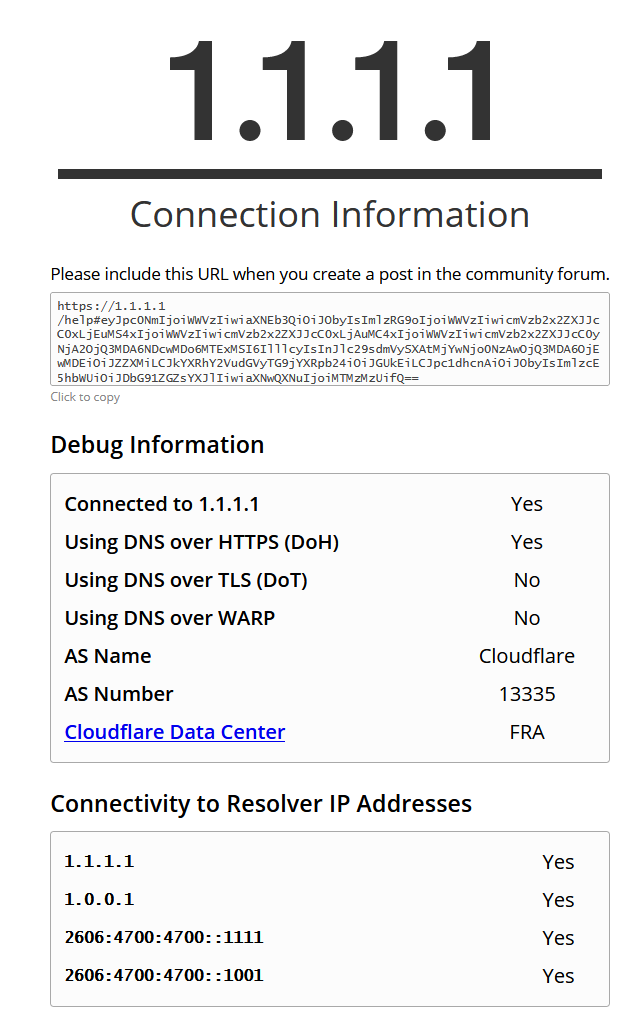
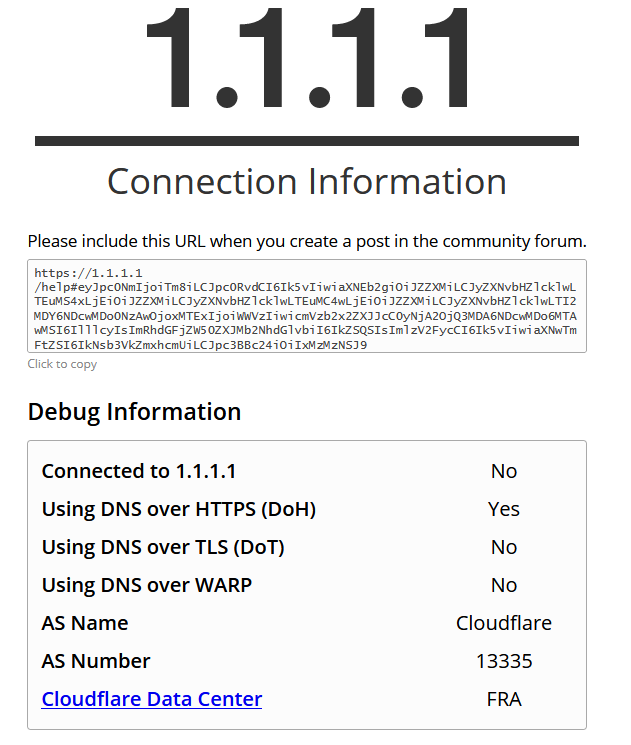
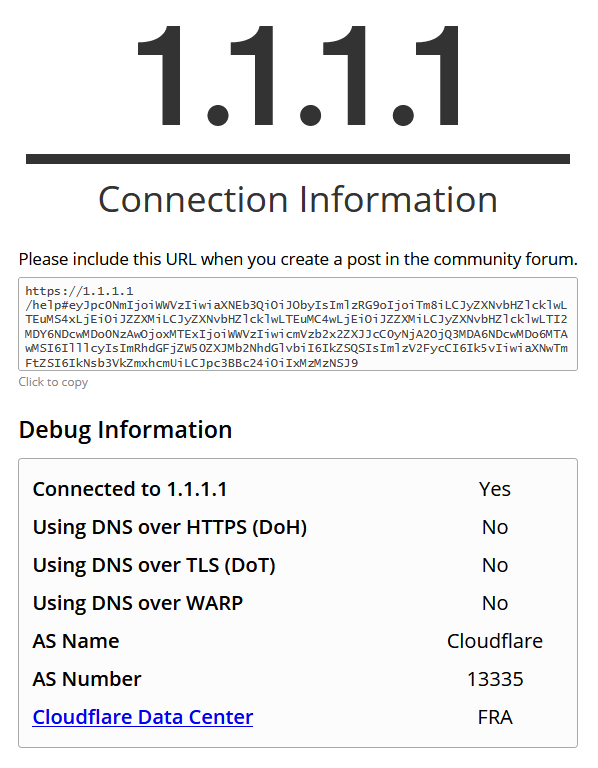
I don't even know where to look for the Logs which should give me more Information about this DNSBL DoH Blocks. Could not find anything at DNSBL Reports.
If i try to nslookup for example "cloudflare-dns.com" it always give me the NXDOMAIN result as expected.EDIT: Ok i guess Firefox is using in the meanwhile a new dns record "mozilla.cloudflare-dns.com" which will be not blocked through the predefined DNSBL DoH list. After i made a custome DNSBL Blocklist Entry. The Firefox 1.1.1.1 DoH test is giving me the results i expect.
-
Are these browsers outside of your control? Prob doesn't hurt if you don't want firefox using doh is disable it in the browser, also setting the canary in your dns.
https://support.mozilla.org/en-US/kb/canary-domain-use-application-dnsnet
As well as set network.trr.mode to 5 which is
5 - Off by choice. This is the same as 0 but marks it as done by choice and not done by default.
-
@johnpoz
i manually activated DoH in the firefox settings for testing the pfBlockerNG DoH Block feature. So yes, they are under my control and yes canary domain is activated as i have shown in my screenshot.i just wan't to verify, that the pfBlocker DoH Block feature is really working.
-
@m0nji did you just ctrl A the entire list and enable and save? I wan't aware of this blocking capability (learning with every inquiry)!!! I appreciate this too....Detfree23
-
@detfree23 you also need to do a force reload/update
-
FYI
if you block cloudflare-dns.com through DNSBL DoH Block, then ACME cert renewal is not working anymore! Tested this with a certificate located on cloudflare AND godaddy. -
@m0nji what? Those have nothing to do with each other..
Stopping a client from using doh, would have zero to do with pfsense resolving some domain to renew the cert.. What settings do you have in acme exactly? What type of renewal are you doing - dns based? Acme sure isn't going to be using doh, and the ips for cloudflare doh are not the same IPs as cloundflare normal dns, etc.
I show the cloudflare-dns.com resolving as these IPs
cloudflare-dns.com. 214 IN A 104.16.249.249 cloudflare-dns.com. 214 IN A 104.16.248.249Those are not the same IPs that would be used if hosting your domain on cloudflare for the NS.
-
i don't believe this is a coincidence. when i block cloudflare-dns.com through the dnsbl safesearch feature, then i see many dns-querys for cloudflare-dns.com while renewing a certificate
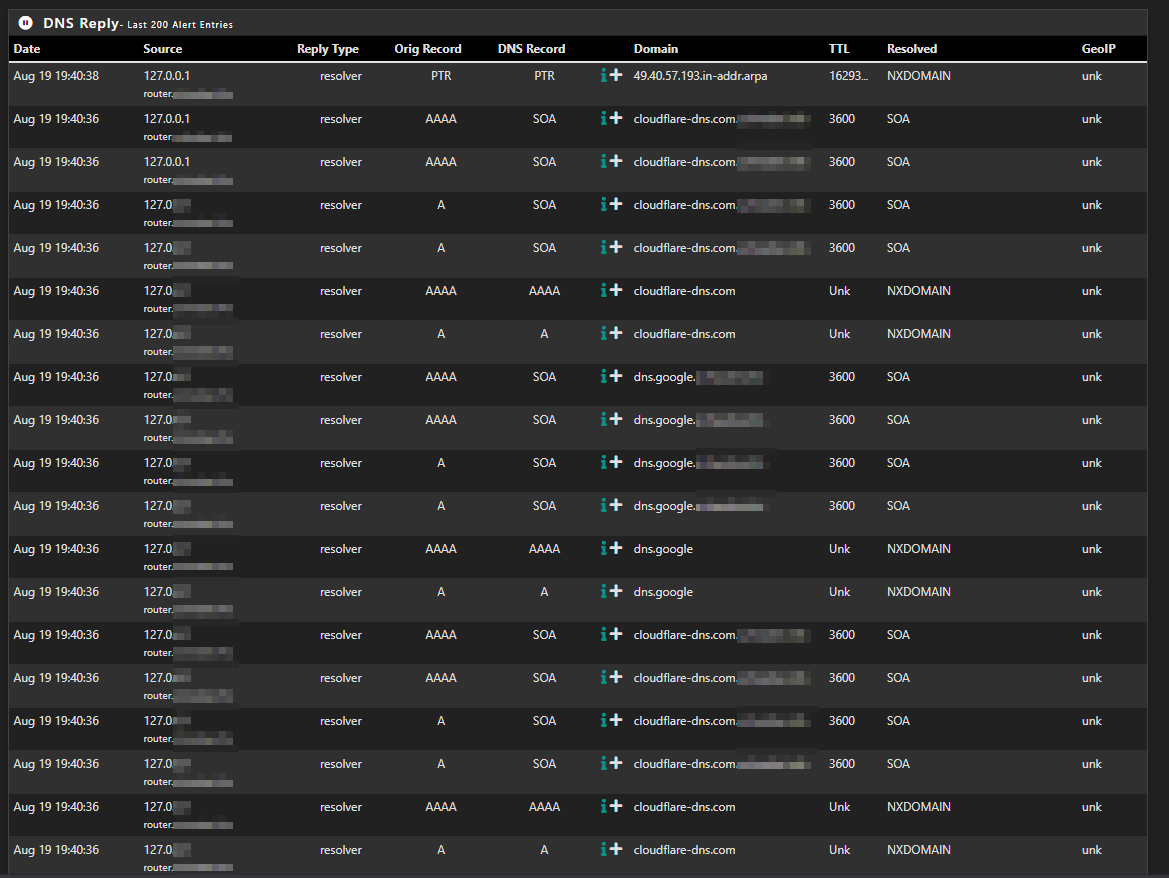
i use the cloudflare and godaddy api to renew the certificates.
this is the error i get while renewing..
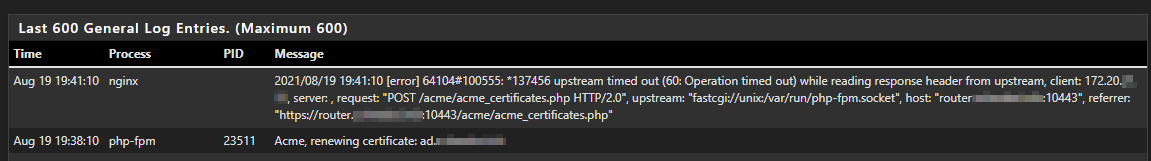
if i disable blocking the cloudflare-dns.com it will work...
what type of coincidence should this be?
-
I have no idea why your seeing those - but has nothing to do with acme updating a dns record.. SOA of whatever domain your doing isn't going to be cloudflare-dns.com nor is it going to dns.google, etc..
Many of those queries your blocking out what the actual fqdn was.. and you local domain... And why and hell would you hide your rfc1918 address 172.20.x.x ?
anything using the api for cloudflare would be talking to api.cloudflare.com, godaddy would be either api.ote-godaddy.com or api.godaddy.com
Its quite possible whatever your doing with trying to filter is just breaking dns in general.. But if your updating anything with the apis of cloudflare or godaddy it sure would be trying to resolve the doh fqdn..
edit: btw I have domains with cloudflare, and use acme certs for those domains.. I have no issues renewing them.. And I specifically block doh domains by resolving them to a specific rfc1918 address, so I can see if any clients try and resolve them and access them..
;; QUESTION SECTION: ;cloudflare-dns.com. IN A ;; ANSWER SECTION: cloudflare-dns.com. 120 IN A 172.19.19.19So if acme needed to talk to cloudflare-dns.com for some reason it wouldn't be able to.. I also have their real IPs blocked..
the fqdn or IP of cloudflare-dns.com would not be used in renewing a cert via clouldflare and acme.. It just wouldn't - they are not related to the api, and or anything to do with actually resolving whatever you domain is.