Simple Firewall setup not working
-
@e4ch Your a member of this forum since three years and still don't know how this works?
Ok! Get a switch with vlan-support for around 40 bugs if your firewall has not enough interfaces.
-
Hi @bob-dig! Thanks for taking the time to respond.
Even if your answer was very insulting, I'll try to ignore that and just assume best intentions. It's a new setup, so ignore anything I might have asked years ago. I translate your answer as: "use VLAN with a new switch". That's quite short and not very helpful, but I'll try to read something useful from it anyway.First, VLAN. I have enough ports and physical cables, so I don't see why VLAN would help here in any way. Also, the three high-risk devices do not support VLAN, so I would need a translator device (like a managed layer-3 switch) just for that if I would be using VLAN. So let's ignore the VLAN suggestion for now and assume physical cables/ports.
I have thought a lot about your answer and I think your idea was to handle the firewalling on the main Intranet gateway (a non-pfSense router) instead and from there connect a port to the three devices. Is it that what you meant?
I understand that this would work (and even eliminate the need for the pfSense device), but I want the firewalling functionality segregated to the pfSense device. So pfSense would still physically be connected to the main gateway on one side and on the other side to the three devices. How can I set up the firewall to make this work? The Netgate/pfSense device is not powerful enough to handle the entire Intranet by replacing the gateway, but it's ideal to handle the traffic to these three devices as a standalone firewall.
My question on how to configure the pfSense device is similar to this one: Imagine I have three devices with public IP addresses that I want to connect with a firewall to the Internet. So the firewall needs no NAT, but needs to publish their presence somehow and still be able to filter traffic. How could that be done?
-
@e4ch said in Simple Firewall setup not working:
(I believe this doesn't belong into the firewall category.)
Requirement: I have three high-risk computers (IoT, Intranet Webservers, whatever) that I want to segregate. They should be reachable from the Intranet, but not be able to send anything outside of their subnet. They don't need Internet incoming or outgoing.
By intranet , do you mean that specific "L2-net" ?
Hardware/Cabling: The three computers are connected to an unmanaged switch which is connected through a Netgate pfSense firewall to the Intranet. The three computers are connected on the WAN side, while the LAN port is connected to the Intranet. I could change that, but I think this is the best way to connect them.
Drawing
IP Setup: Let's assume that the three computers have the IPs 192.168.2.x, the WAN port of the firewall 192.168.2.1, which is also the configured gateway on the three computers. The LAN port of the firewall is configured as 192.168.1.20 and the other computers on the LAN are also on that subnet 192.168.1.x. The computers on the LAN and the three to isolate have a subnet mask of /16 configured, so they should see each other if there wouldn't be a firewall between.
The /16 mask is clearly an error if the network is defined as a /24 in pfSense or other devices.
Firewall Configuration: currently any-any rule configured, the Interfaces have /24 subnet configured, because overlapping subnets on Interfaces are not allowed. Bogus networks on the Interfaces are not blocked. NAT is disabled, as all IPs are internal.
Then /16 is an error
Testing: On a PC on the Intranet, with gateway configured as 192.168.1.20 (firewall), I can reach the firewall including the UI. From the UI of the firewall, I can ping the three computers on the other side. But I cannot ping or reach the three computers directly, although this is not blocked by any firewall rule.
Prob. the /16 mask
Data would never be sent to the pfsense (default gateway) for any 192.168.x.x range.Questions: What am I missing? I would expect that the Netgate device just routes the traffic to the computers, but obviously this is not the case. Do I need to configure routing somehow? I mean I could implement some kind of NAT, but I don't want to use NAT at all. And the testing computer was configured with gateway=firewall, but normally intranet devices would have a different gateway configured, probably the router to the internet - so can this work at all? Would it find these machines somehow by sending broadcast packets? If this cannot work, what is the suggested setup (without using NAT)? In all big company networks I can just ping the destination IP and there are many firewalls on the way. How should I set this up?
Begin with correcting all device subnet masks to correspond to the pfSense or router interface mask.
/Bingo
-
@e4ch said in Simple Firewall setup not working:
the WAN port of the firewall 192.168.2.1, which is also the configured gateway on the three computers
Huh?? I am just at a lost to how that would work?
So you have a double nat setup..
Your setup is like this?
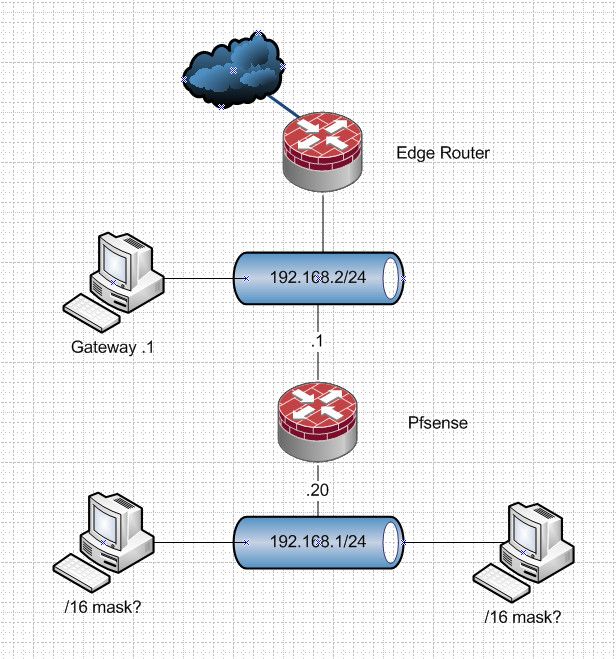
This would be a normal setup.. Where you want to isolate a network..
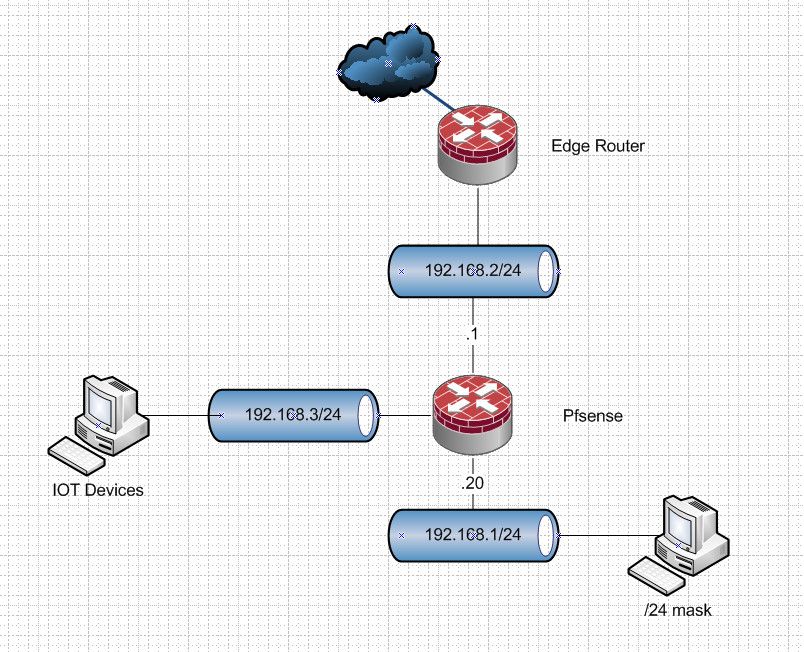
The use of /16 mask on devices while your using /24 on pfsense is going to problematic at best..
-
@bingo600 said in Simple Firewall setup not working:
By intranet , do you mean that specific "L2-net" ?
Yes, the main LAN network.
You were right. The subnet mask was indeed the problem. The test computer doesn't send the traffic to the gateway (firewall) if it thinks the device is on the local subnet. I should've known this. So I made it two completely separate subnets with correct subnet mask and now the firewall is forwarding the traffic as it should. First step solved.
Now it should also work when the gateway on the test computer (on the LAN) is the edge router instead of that firewall. I haven't tried anything yet, because I don't want to mix old and new IP addresses on the same physical network, but want to plan this theoretically first.
So if I have traffic to those three devices, it must be routed to the firewall somehow. As they are not on the subnet, it would get forwarded to the main gateway. That gateway thinks it's not on the LAN subnet and would forward it to the internet (or drop it as it's non-routable). Of course I could add the LAN subnet to be /16 on the main gateway, then it would think it is on its LAN subnet (as it is), but it still wouldn't know that the traffic should be sent to the firewall's IP.
So either I have to configure some specific routing for that network on the main gateway or I would have to implement 1:1 NAT on the firewall or something like that.
Thanks!
-
@johnpoz said in Simple Firewall setup not working:
@e4ch said in Simple Firewall setup not working:
So you have a double nat setup..No. The pfSense has NAT disabled.
Your setup is like this?
No. It would look something like this:
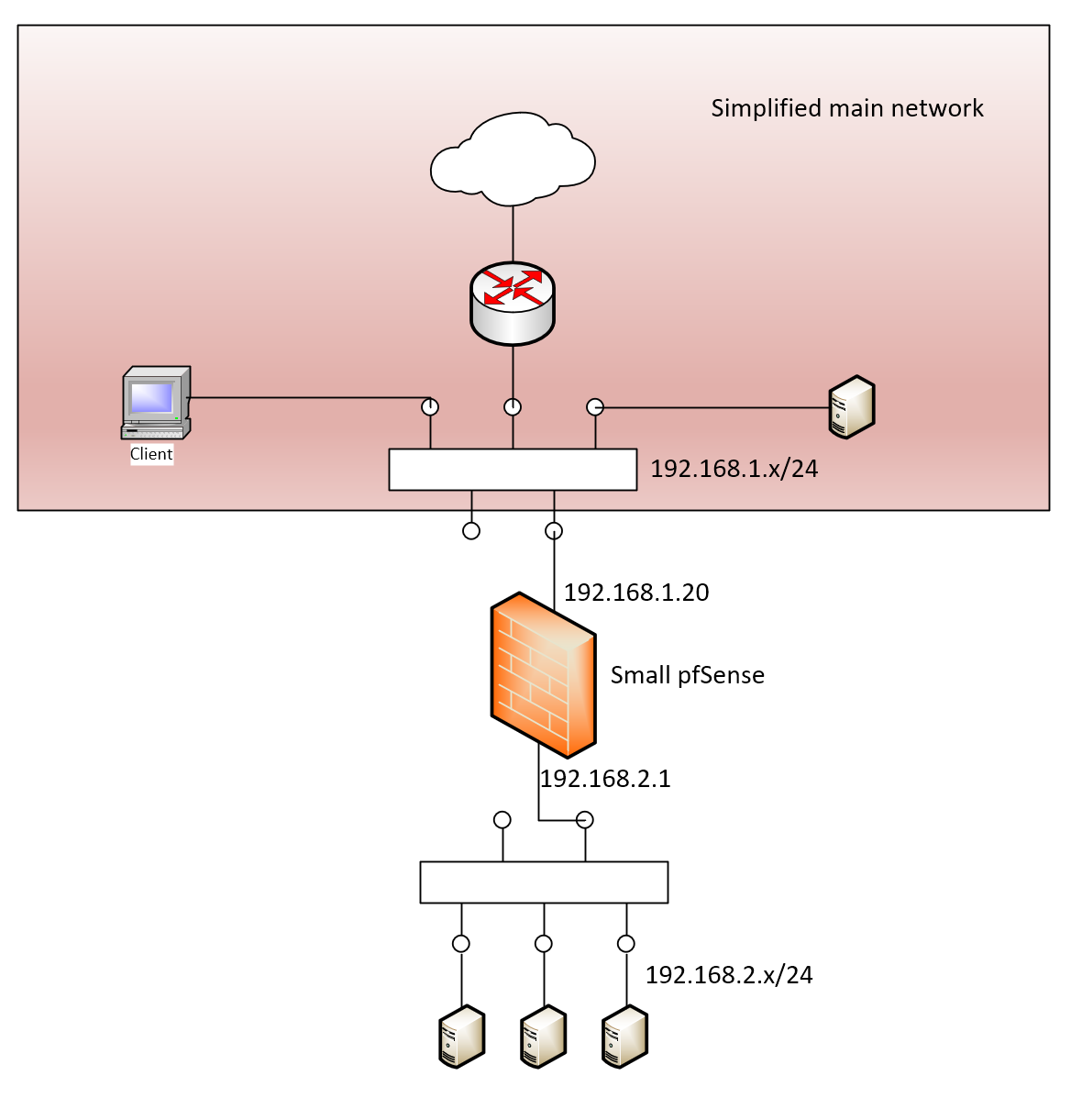
Please note the corrections from my post above to @bingo600 where we noted that the subnet mask must be /24.
-
How many interfaces do you have on that pfSense ?
If you have 3 , you could put the 192.168.1.x/24 Lan behind the pfSense also.
That would solve the routing issue, as pfSense would know both networks.Else ... Yes , you either have to set static routing on all your "Lan devices" , so they would also know that 192.168.2.x/24 is behind the pfSense , or if possible "do that routing in your internet router".
It might not be every device you have that need to talk to the IoT units.You could "cheat" a bit , and set your pfSense (.20) as default gateway for the 192.168.1.x/24 lan , and then have the pfSense have default gateway via the router. That would also make the 192.168.2.x/24 lan kown to everyone using pfSense as default gw , at the cost of every package going to the internet had to pass the pfSense interface. Unless the pfSense sends ICMP redirect , but most firewalls don't.
/Bingo
-
@e4ch said in Simple Firewall setup not working:
No. The pfSense has NAT disabled.
Then does your edge router have route to your 192.168.2 network?
-
Thanks @bingo600 and @johnpoz for your helpful ideas.
Some comments:
"If you have 3 interfaces, you could put the 192.168.1.x/24 LAN behind the pfSense also.
It has only two ports (LAN and WAN), but with VLANs we could extend this, I assume. That would be a bad idea though: the pfSense is a low-powered device (SG-1000), I think it can't even do 1Gbit/s. For these three devices, I think it is barely sufficient.
So also the "cheat a bit" solution wouldn't be good then.
I think this leaves me with three options:
-
Configure static routing on the devices in the Intranet that need to reach the three devices. There are only very few computers that need to reach them, so that might be an option. I currently don't know how to configure this in Windows though, but can find out of course. UPDATE: I found out how this works.
-
Configure some routing on the edge router so that the traffic to the 192.168.2.x network gets sent to the pfSense via its LAN port. (That's what @johnpoz suggested.) It's a common Ubiquiti router, but I don't know how to configure this. It should be possible though. I can find that out. I think this is the best solution, as this would make it work for all machines then.
-
Configure some 1:1 NAT on the pfSense. I don't know how to configure that exactly, but this should also work. Then the three machines would have a 192.168.2.x address within their network and 192.168.1.x address on the LAN side. I don't like to have two different IP addresses for these machines, but this might not be that a bad idea.
This is not the right forum to ask further on how to configure this, as this is not Netgate/pfSense specific, but at least I have some ideas now. Currently I'm using different IP ranges, so as first solution I might use solution (1) from above if I find out how to have a second subnet in Windows, as that wouldn't interfere with my current setup. For the final solution I'll probably go with (2) or (3).
UPDATE: (1) won't work with completely different IP ranges currently in use, as the static route forwarding doesn't work, because the pfSense IP is not in the current subnet range. But that's fine; it would work after the correct subnet configuration - just not usable as intermediary solution.
UPDATE: "1:1 NAT" (3) I couldn't get to work. How would that be configured on pfSense for the cases above? For example if the high-risk device 192.168.2.11 should get 1:1 NATed to 192.168.1.21. I tried, but couldn't get the 192.168.1.21 IP reachable, not even if configured as gateway.Thanks again.
-
-
I also figured out why the 1:1 NAT (the (3) from above) wasn't working. It looks like you not only have to setup the 1:1 NAT and firewall rules, but you also have to define the outside IP under Firewall / Virtual IPs, otherwise the firewall will not respond. (Found this here: PFSense: 1:1 NAT Configuration)
With that, all problems are resolved. Thanks everyone.