No access to internet from web browser anymore but can ping (LAN)
-
Hi,
I am new to pfsense, I have installed it just a few weeks ago. But since last week, I don't have internet on my VMs anymore. I can't receive HTTP/HTTPS packets.
From web browser (e.g., google.com):
- HTTPS : Secure connection failed, PR_CONNECT_RESET_ERROR
- HTTP : The connection was reset
From LAN :
- Ping, nslookup, netcat (8.8.8.8, google.com and other sites) OK
- Telnet : connected to host, connection closed by foreign host
- Can't install tracert or traceroute because I don't have internet
The exceptions are debian (e.g., deb.debian.org) and ubuntu mirrors : temporary failure in name resolution (error still here after numerous attempts).
From pfSense :
- Ping, nslookup, netcat (8.8.8.8, google.com, other sites, even deb.debian.org) OK
- Telnet : connected to host, connection closed by foreign host
- Traceroute OK
- In firewall logs, I have a "default deny rule IPv4" which seems to be blocking TCP traffic (but I did not create this rule and I don't know how to delete it. Some forums say it is not an issue)
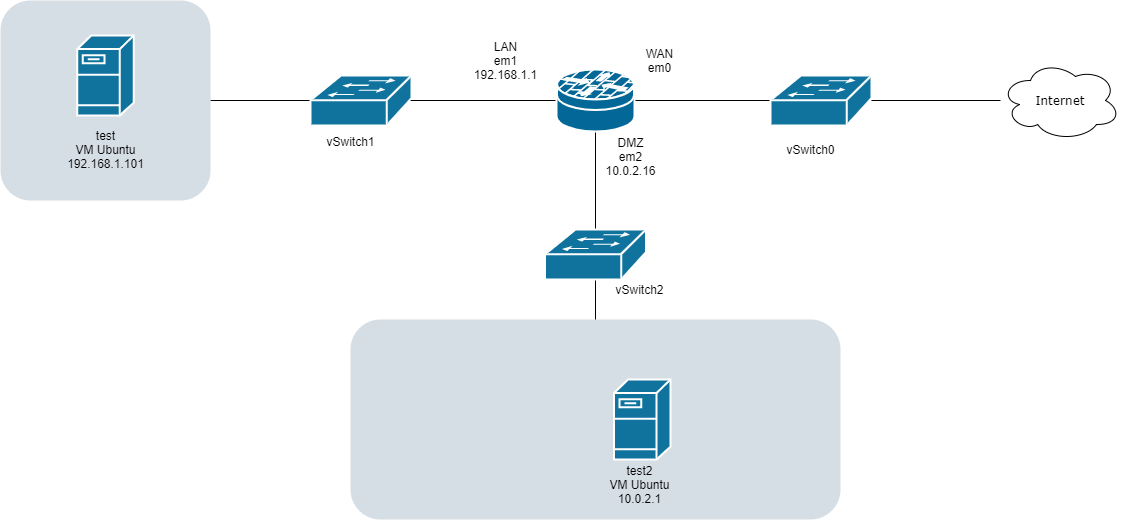
Here is my architecture:
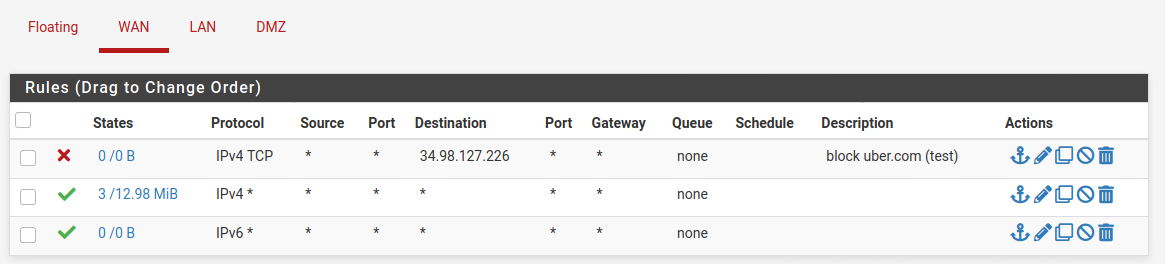
NAT Outbound is set to automatic, below are the rules for the WAN :
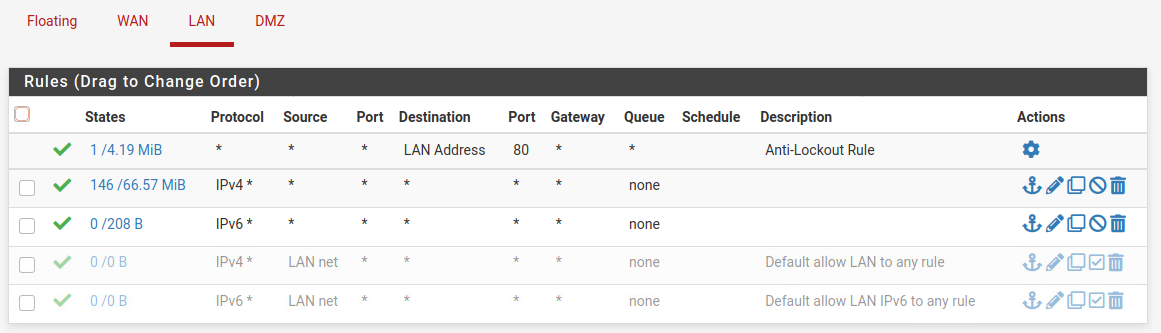
and for the LAN :
I don't have another firewall, no proxy and I don't use VPN.
Right now, the following options in pfSense are :- Unchecked - Disable hardware checksum offload
- Checked - Hardware TCP Segmentation Offloading
- Checked - Hardware Large Receive Offloading
- Unchecked - State Killing on Gateway Failure
- Unchecked - Skip rules when gateway is down
I only have one physical adapter in my server (vmnic0 connected to vSwitch0)
I have tried several things to solve this issue :
- Delete and reinstall everything (pfsense 2.5.2 + VMs)
- Reboot ESXi (v.6.7), checked the nic (up)
- Change DNS address, gateway, interfaces, rules (e.g., specific rules to allow TCP, any TCP flags, sloppy state type...)
- Enable DNS forwarder
- Check and Uncheck Disable hardware checksum offload, Hardware TCP Segmentation Offloading and Hardware Large Receive Offloading options
- Monitor states (checked every connections for malicious IP addresses)
Not everything is listed here, but I find my post quite long... I hope it will not drive you away. If you need any information, feel free to ask me. I have some tcpdumps as well.
Any idea is welcome ! Thanks
-
@yass01
What is your hypervisor?Rules have to be add to that interface where the traffic is coming into pfSense.
So a block rule on WAN with a specified destination might be useless. But the pass rule to any will allow access to the pfSense web configurator as well, which might not be that what you want.For accessing internet resources from inside your LAN there is no rule on WAN necessary.
In firewall logs, I have a "default deny rule IPv4" which seems to be blocking TCP traffic (but I did not create this rule and I don't know how to delete it. Some forums say it is not an issue)
The default deny rule is implicitly added to the bottom of each interface rule set. So any traffic which you don't pass explicitly by a rule will match this one and be blocked.
-
Hi @viragomann, thank you for your help. I will change the WAN rules, and won't put any block rule for now on the LAN.
The hypervisor is ESXi 6.7. With your reply, I thought that maybe the ESXi was blocking internet, so I did a quick check on the firewall :
- The firewall is enabled and the default action is DROP.
- I disabled it, rebooted pfSense and the VMs --> no internet
- Then I enabled it, set the default action to PASS --> no internet
Do you think that the problem comes from the esxi, and that I should rather dig on that side ?
-
@yass01
Not necessarily. In ESXi pfSense works out of the box, excepted its firewall.As I understand, it's not a DNS issue. You can ping google.com as well?
If ping works (ICMP), but HTTP(S) doesn't (TCP), it's often due to asymmetric routing. So recheck the firewall log. You mentioned the traffic is blocked by the default deny rule. Check its flag, please. If it's another than SYN that is an indication for asymmetric routing.
-
@viragomann
I can ping google.com, it works just fine.Indeed, in the logs there seem to be recurring patterns (and I totally missed the flags).
home_ip : my home public ip address server_ip : my server public ip address public_ip : multiple public ip addresses were captured by the filter port : multiple port numbers were captured by the filterHere is for the Default deny rule IPv4 :
block em0 TCP:PA home_ip:port server_ip:443 (*) block em0 ICMP public_ip server_ip block em0 TCP:S public_ip server_ip:port (mostly port 445) block em0 TCP:A/FA/PA 192.241.206.128:port server_ip:443(**) block em0 TCP:R public_ip:port server_ip:80(*) this line appears so often that it is difficult to see anything else.
(**) I don't know the 192.241.206.128 address, but it is the only one I have with the A, FA and PA flagsSome traffic is passing :
pass em0 TCP:S server_ip:port 99.86.113.21:443 pass em1 TCP:S 192.168.1.2:46178 99.86.113.21:443 (***) pass em1 TCP:S 192.168.1.101:port 34.122.121.32:80 (32.121.122.34.bc.googleusercontent.com)(***) 192.168.1.2 is another vm (debian) on the LAN --> no internet as well
In the end, the Default deny rule IPv4 seems to be blocking inbound traffic. I could see that it was mostly blocking ip addresses referenced as abusive.
And I think I have missed something, because I don't see all the LAN activities in the logs (e.g., ping). I am currently working on this issue.