Pfsense plus hurricane electric breaks netflix IPV6 - proxy error
-
Yep - Fixed this ages ago also basically by not allowing ipv6 netflix anything.
Still - I think it is crazy stupid of netflix to so zealously block anything remotely related to a tunnel.It is stupidity with a capital S.
-
Yep - Fixed this ages ago also basically by not allowing ipv6 netflix anything.
Still - I think it is crazy stupid of netflix to so zealously block anything remotely related to a tunnel.It is stupidity with a capital S.
Agreed. It's too bad they didn't at least talk with the HE team to come up with a better plan. Surely Netflix realizes tons of ISPs have not yet implemented ipv6, and that tunnels will be used for legit purposes.
Oh well.
Anyway, I wanted to provide that write-up for others who are struggling, and for myself for future reference.
-
This seems to be working for me. Thanks so much!
-
I use HE.net as well, and just noticed this ATV issue today. I actually have a handful of streaming devices and I'd really prefer all of them to use IPv4 - mainly because I'm OTT-only with all my viewing and don't want to screw around with things by possibly pushing traffic over a tunnel, it's just another possible point of failure I don't want to think about.
Given that I know all the MACs of these devices (a few rokus, an ATV and a fire TV), is there some way on the pfsense side to just prevent them from even picking up IPv6 addresses? I know I could VLAN but I really don't want to invest in more gear or cable runs to accomplish this.
-
Put them on a VLAN that doesn't have IPv6 enabled.
-
This is also a good solution that works fine here: https://forum.pfsense.org/index.php?topic=134352.msg737158#msg737158
-
Late to the party, but posting anyway, as I just encountered the Netflix tunnel issue today.
In pfSense 2.4.3-RELEASE-p1, I went to System->Routing, then clicked on the Static Routes tab.
Under Destination Network, I added 2406:da00:ff00::, and selected 48 as the netmask. For Gateway, I selected Null6 ::1
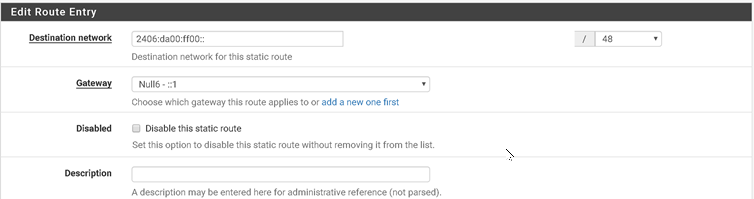
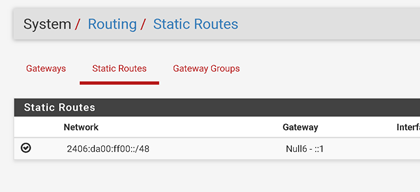
This forced Netflix to go through IPv4 instead of my HE tunnel. It was quite easy, and seems to do the trick for me.
-
@kejianshi Thanks. This quick fix works fine for me.
-
I'm running into a situation where the Netflix app is not failing over to IPv4 with the reject rule in place for IPv6 addresses. Only solution is to disable IPv6 on the client.
Has anyone had trouble with their setup since implementing the reject rules described (above)?
-
If the client thinks it has IPv6 and gets a response - even though it is a connection refused - why should it try IPv4? In general, if you have a dual stack client you don't want to selectively break IPv6. You want to turn it off. Behavior there will be application and operating system dependent.
-
Another solution is : inform the local resolver ( unbound) that it should remove any IPv6 when the URL is "netflix" like.
https://forum.netgate.com/topic/118566/netflix-and-he-net-tunnel-fixed-using-unbound-python-module
As soon as I view a film from netflix with my IPv6 enabled PC via pfSense (using he.net for IPv6 addresses) I see this in the DNS log :
Aug 6 17:35:51 unbound 52268:1 info: no-aaaa: blocking AAAA request for anycast.ftl.netflix.com. Aug 6 17:35:51 unbound 52268:1 info: no-aaaa: blocking AAAA request for anycast.ftl.netflix.com. Aug 6 17:35:51 unbound 52268:1 info: no-aaaa: blocking AAAA request for oca-api.us-west-2.prodaa.netflix.com. Aug 6 17:35:51 unbound 52268:1 info: no-aaaa: blocking AAAA request for oca-api.us-west-2.prodaa.netflix.com. Aug 6 17:35:51 unbound 52268:1 info: no-aaaa: blocking AAAA request for ifo5usjqtzhvl6xjlsanq-euw1.r.nflxso.net. Aug 6 17:35:51 unbound 52268:1 info: no-aaaa: blocking AAAA request for oca-api.netflix.com. Aug 6 17:35:48 unbound 52268:1 info: no-aaaa: blocking AAAA request for push.prod.us-west-2.prodaa.netflix.com. Aug 6 17:35:48 unbound 52268:1 info: no-aaaa: blocking AAAA request for push.prod.netflix.com. Aug 6 17:35:47 unbound 52268:1 info: no-aaaa: blocking AAAA request for occ-0-56-55.1.nflxso.net. Aug 6 17:35:47 unbound 52268:1 info: no-aaaa: blocking AAAA request for occ-0-56-55.1.nflxso.net. Aug 6 17:35:41 unbound 52268:1 info: no-aaaa: blocking AAAA request for ichnaea-web.us-west-2.prodaa.netflix.com. Aug 6 17:35:41 unbound 52268:1 info: no-aaaa: blocking AAAA request for ichnaea-web.netflix.com. Aug 6 17:35:39 unbound 52268:1 info: no-aaaa: blocking AAAA request for assets.nflxext.com. Aug 6 17:35:39 unbound 52268:1 info: no-aaaa: blocking AAAA request for assets.nflxext.com. Aug 6 17:35:39 unbound 52268:1 info: no-aaaa: blocking AAAA request for codex.nflxext.com. Aug 6 17:35:39 unbound 52268:1 info: no-aaaa: blocking AAAA request for codex.nflxext.com. Aug 6 17:35:38 unbound 52268:1 info: no-aaaa: blocking AAAA request for www.eu-west-1.prodaa.netflix.com. Aug 6 17:35:38 unbound 52268:1 info: no-aaaa: blocking AAAA request for www.netflix.com.Thus : any Netflix related URL that has an Pv6 is removed from the DNS request reply - only IPv4 persists. So the application use pure IPv4 to contact Netflix. This means : not using IPv6 so not using he.net.
Works ! -
@msf2000 said in Pfsense plus hurricane electric breaks netflix IPV6 - proxy error:
I'm running into a situation where the Netflix app is not failing over to IPv4 with the reject rule in place for IPv6 addresses. Only solution is to disable IPv6 on the client.
Has anyone had trouble with their setup since implementing the reject rules described (above)?
Switch Reject for Block and see if Happy Eyeballs kicks in?
-
So its years later. Jan 2022 and I set this up again on a new pfsense and this time it seems so far that Netflix, Amazon and others are not blocking Hurricane Electric IPV6 anymore. So thats nice! (So far).
-
@kejianshi You will notice ALOT of stuff is missing. They no longer outright block you, but they only show you a "Global" view, i.e. stuff available everywhere. Stuff allowed in your location but not allowed everywhere is not shown.
This is my currently block list that seems to catch everything netflix.
2406:da00:ff00::/48
2607:f8b0:4001::/48
2620:108:700f::/48
2a01:578:3::/48
2600:1407:19::/48
2a05:d018:76c::/48
2600:1f18:631e::/48
2607:fb10::/32 -
@napsterbater said in Pfsense plus hurricane electric breaks netflix IPV6 - proxy error:
but they only show you a "Global" view
You have to login first, right ?
What you can view is probably based upon your IP (4 or 6).
And probably the country from which you subscribed. -
@napsterbater Thanks! I tested your "Theory" and turns out it was a fact. I have loaded my alias with those IPs and made the firewall block rule. Now the omitted content is present again. I tested it with "Stargate SG1" which is apparently US-Only content and your are correct. Thanks for the heads up.
-
@gertjan said in Pfsense plus hurricane electric breaks netflix IPV6 - proxy error:
@napsterbater said in Pfsense plus hurricane electric breaks netflix IPV6 - proxy error:
but they only show you a "Global" view
You have to login first, right ?
What you can view is probably based upon your IP (4 or 6).
And probably the country from which you subscribed.Yes.
An HE IPv6 = VPN as far as Netflix is concerned.
No, only Globally available items, your login or "country subscribed in" has no bearing.. -
For the record : these (are placed in an alias) and then placed on the LAN interface, right ? ::
@napsterbater said in Pfsense plus hurricane electric breaks netflix IPV6 - proxy error:
2406:da00:ff00::/48
2607:f8b0:4001::/48
2620:108:700f::/48
2a01:578:3::/48
2600:1407:19::/48
2a05:d018:76c::/48
2600:1f18:631e::/48
2607:fb10::/32 -
@gertjan I applied it to all interfaces in a floating rule. Why Not right? Yeah. Its an alias. Netflix was sort of sneaky by not blocking everything. Had me fooled for a minute there. I also handed out static IPV6 addresses to everything connected to the pfsense including my XMPP chat server and phone server. Interestingly, that totally fixed NAT issues like broken video and broken voice even when only one side of the conversation was on IPV6 and the other side was on IPV4. Thats the main reason I want everyone to transition to IPV6. No more NAT. No more buying a public IP for every server. No more need for STUN, ICE, Jingle, WebRTC, TURN servers or crap like that.