TP-Link Easy Smart Switch security question
-
so back with the budget project report ...
(at the moment ~ 20 - 28 EUR incl. VAT)
u can remove VLAN1 from all ports (not member of) ;)
but u have to use both (if not both is set its not gonna work)
works wit an uplink from coreswitch (Cisco / HP)
and direct filled from pfSbrNP
-
TL-SG108E v1.0/v2.0: You can edit .cfg with hex editor and remove ports from VLAN1, mark as tagged or even remove VLAN1 completely. v2.0 can be flashed with v3.0 firmware.
TL-SG108E v3.0/v4.0/v5.0: Allow remove ports from VLAN1, or mark as tagged.
TL-SG105E v1.0/v2.0: .cfg can be modified. I don't know if v2.0 can be flashed with v3.0 firmware.
TL-SG105E v3.0/v4.0/v5.0: Allow remove or tag ports from VLAN1.
TL-SG1016DE v1.0/v2.0: Verifies .cfg checksum, and if it does not match, it cannot be restored.
TL-SG1016DE v3.0/v4.0: Allow remove ports from VLAN1 or mark as tagged.
-
wow pretty cool info ... thanks a lot !
pricing in retail incl. VAT 28EUR for SG108E and 20EUR for SG105E
makes it pretty easy to go with the SG108E for low budget projectsbrNp
-
lets have a look how these little TPLinks perform out in the wild ....
never done a LAG group for a VLAN before ... i think i have to test it ...well ;)haha this will e so much fun ;)
any hints / ideas or inputs are welcome ;)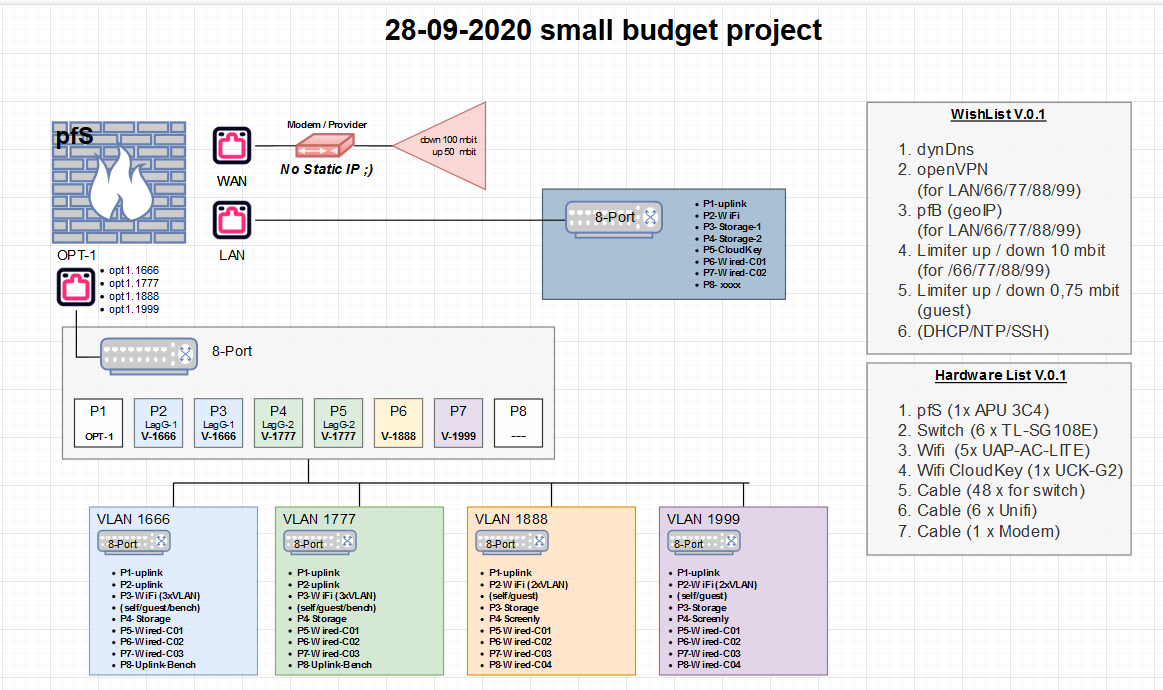
-
What is the point of the laggs in this setup exactly?
Your routing would happen at pfsense, those cheap switch don't do L3 routing. So for example any traffic between vlan1666 and 1777 would still be limited to the hairpin you have on opt1 connecting to pfsense. So other than than link redundancy the lagg would get you nothing.
If all your downstream switches you show there are going to only do 1 vlan, then there is no need for smart even on them.. You could save a few extra bucks each by just using dumb switches there.
Also your wasting a lot of ports in uplinks from all your switches. It would prob be more cost effective to just get a switch with more ports. Unless you have need for physical distance between the switches.. Prob better to just buy say a 48 port switch or 2 24 porters. Or maybe even just 1 would be enough ports if your not using so many up with lagg and uplinks.
edit: Looks like your AP connected to those downstream switches might be doing multiple vlans, if so then you would need to allow for the other vlans on your uplinks, etc. Not shown your drawing. Looks like those switches are only doing single vlans.
-
A)
yeah the lagGroup ... they just want it to have ... i dont see the use in it too
cuz the bottleNeck is the uplink to OPT-1B) those 4 downstream switches + the 1 for LAN need VLAN cuz i got a feeling that there will be some VLAN need in the Wifi setup (more than just a guest Wifi network)
C) those 4 + 1 downstream switches are needed as far is i m informed caused by the physical location (after callin the guys who think this is all fun and easy cheesee doable in no time ) it seems to be a super small coWorkin or so space
D) yes u r right seems like they are only doing single VLAN not the case iwth those APs
lets see what comes next arround the corner ....
the limiter vor each VLAN will be fun considering the up/down of WAN and openVPNEDIT:
oh now looks like we are Talkin global WiFi installation for
LAN an 4x VLAN and a global guest network with client isolation + 2 VLANs for Testbench should be all manageble by a cloud key -----> allright thats the easy part ;) -
I have the TL-SG105E v5 with a firmware from 2019 that came when I ordered it a few weeks ago. I have tested thoroughly and can confirm that the management interface is actually available on all VLANs, even if the port is unchecked from VLAN1 completely.
-
@vasko said in TP-Link Easy Smart Switch security question:
that the management interface is actually available on all VLANs, even if the port is unchecked from VLAN1 completely.
That is not very secure now is it ;)
-
I am trying to modify the TL-SG108E v1 to get the firmware from v3 or v4 working on v1. v1/2/3/4 they are identical except for the amount of memory, the v1 carries a 1 Megabyte GD25Q80 GigaDevice flash while the v2/3/4 carries a 2 Megabytes GD25Q16. Firmwares from v2 ownwards cannot be flashed to v1 just because of the amount of memory available (firmware from v2 occupies 0.98Megabyte, v3 or v4 occupies 1.05 Megabytes).I'm going to replace the flash memory from v1 with a GD25Q16. I will read the current flash memory, and introduce the firmware of v3 or v4.The memory layout is as follows:
0x0: Bootloader
0x1000: Firmware
0xFC000: MAC address
0xFF000: ConfigurationI intend to read the original flash, and modify from 0x1000 onwards by writing the firmware of v3/4 but it would exceed (due to its size) the 0xFC000 offset so the MAC address would be overwritten. In the v2/3/4 flash layout the MAC address must come in another offset, but I don't know which one. Nor do I know for sure if the MAC address is read from that offset by the bootloader or the firmware itself. In the first case, you should also modify or replace the bootloader.I am using a CH341a Mini Programmer with test clips (shorturl.at/abFI4) to read the flash without desoldering it.If someone has a TL-SG108E v2/3/4 and has a flash memory programmer, could you dump the memory and send it to me privately to investigate? Of course you must find your MAC address in the dump and modify it for example by 00:11:22:33:44:55 to be able to locate it.Thanks you very much for your collaboration.Not possible, v1 have a different Realtek chip than v2/v3. Instead, it can be crossflashed to Netgear GSS108E.
But it is possible to flash v3 firmware in v2. These are identical and v3 firmware allows to modify VLAN1.
-
I have managed to crossflash from TL-SG108E v1 to Netgear's GSS108E. Both have an RTL8370N chip.
The GSS108E is also a manageable 8-port switch with same chip and same flash memory as TP-Link v1 (1MB) and with a web interface. Also allow you to edit VLAN1. It also comes with two power-only USB ports for charging smartphones. But the Switch part is exactly the same and it doesn't affect anything.
You need the CH341a Mini Programmer and of course don't forget to make a backup of the flash. Read at least twice and check md5 of dumps to make sure it doesn't contain errors. Here are the steps to convert the TL-SG108E into a GSS108E.
1.- Create an empty 1MB file for v1 with hex editor and fill it completely with FF.
2.- Download the GSS108E bootloader from the Netgear website, it's included in the download of firmware version 1.0.0.10. Also download the latest firmware version (v1.6.0.4).
3-. Open the loader file with hex editor and select all content. Copy and paste it by writing (not inserting) from beginning (0x0) into the empty file you created before.
4-. Write the original MAC address at offset 0xFC000 and save the changes.
5.- Write the file in the flash with CH341A Mini Programmer (don't forget to check writed content).
6.- Turn on the Switch, connect your PC to any port and configure the network in 192.168.0.x/24.
7.- Open the browser and access the Switch (the default ip is 192.168.0.239). The bootloader recovery web will appear. Select the firmware v1.6.0.4 and flash. After a minute or two the Switch will reboot and you will be able to access its configuration.
Advantages over TP-Link firmware:
- Configuration web in TL-SG108E v1
- You can modify VLAN1, leave it without any port and even delete it.
- You can disable the configuration with the Netgear ProSAFE Plus Utility tool, which will prevent the Switch from being discovered by broadcast packets.
Problem (only cosmetic):
The port LEDs do not work as with original firmware. In Gigabit Ethernet mode, the LED that lights up is orange instead of green, and in Fast Ethernet mode is green instead of orange (leds are inverted).
All everything else works correctly as expected.
-
I have a TL-SG108E v2 on the way. I can upload a dump of the flash with the v3 firmware installed. In case anyone is interested.
-
Hi!
I’m new to this forum, so sorry to immediately open my first post with a request.
I would need a TL-SG108E V3 GD25Q16 flash chip for full content because I didn't save my own (: (: and the switch became a brick.
Thank you very much if anyone can help!
Hi: Fazon -
@fazon Here is the dump of the v3 flash with the latest version. You must edit the MAC address found at offset 0x1FC000 (filled in with "AA BB CC DD EE FF") for the one below on the Switch label.
https://www.mediafire.com/file/tpplnk69b6g5scw/TL-SG108E_v3_AABBCCDDEEFF_dump.bin/file
-
Hi friend!
You helped a lot, thank you very much!
Have good health and have a nice day!
wbr.
Fazon -
I have the TL-SG105E v5 with a firmware from 2019 that came when I ordered it a few weeks ago. I have tested thoroughly and can confirm that the management interface is actually available on all VLANs, even if the port is unchecked from VLAN1 completely.
Exact same issue on the TL-SG108E v5. Config:
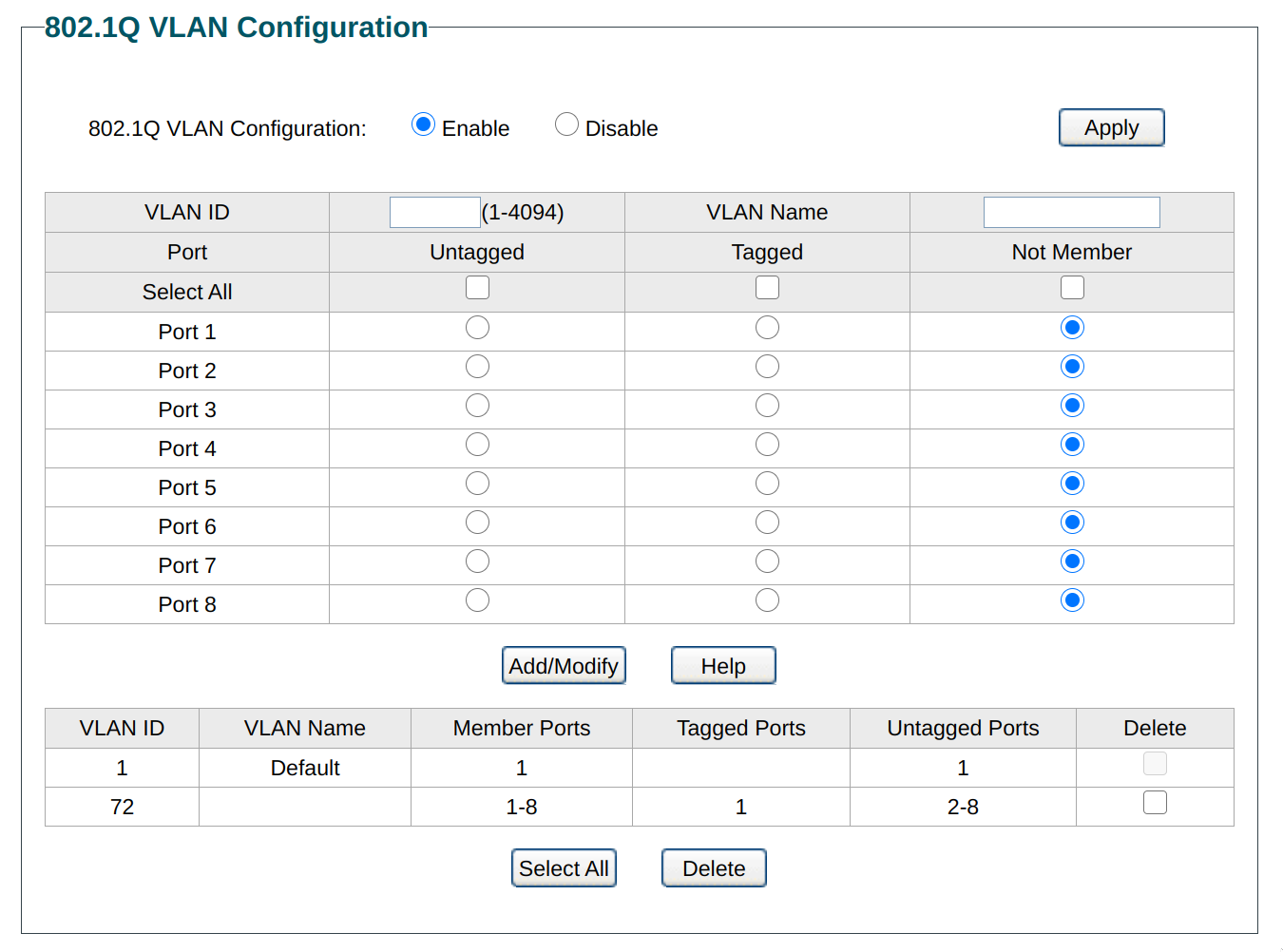
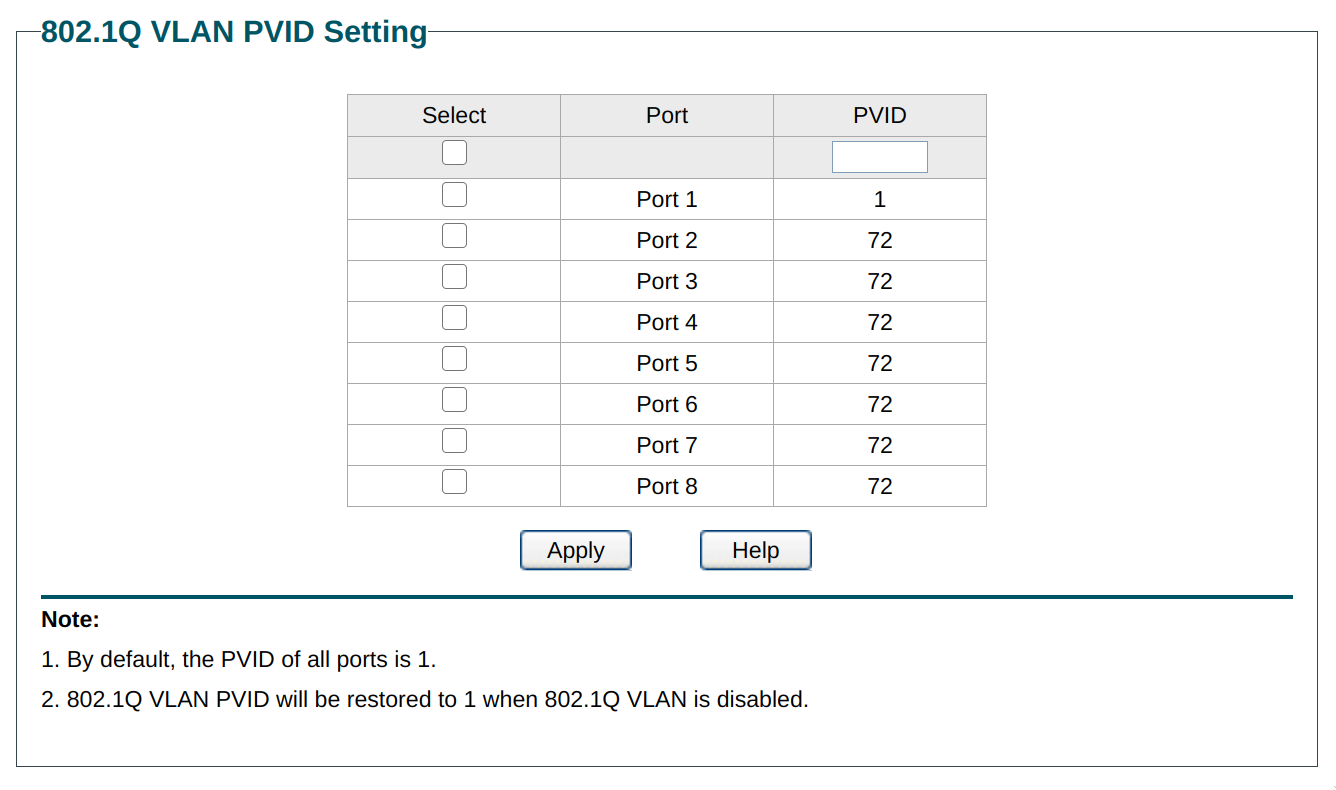
-> management Interface is still accessible on Ports 2-8. -
Yeah I really would just use those as dumb switches.. I put mine into use the other day.. just dumb.. The 2 devices I have plugged into same vlan.. That control upstream of that switch via cisco sg300..
I had a netgear I was going to use instead.. But ports wouldn't light up..
-
This post is deleted! -
@apocalypse I know that you created this over a year ago, but still, Have to say after finding and reading this just now, I am impressed and greatful that you have already gone through the work to do this. I have been doing my own research on this switch. has I have a few of them that I took home after replacing 3 of them at a Clients, and I want to repurpose them for a budget project I am working on for a friends Business, and I discovered the Major Flaw with the Security (All 3 of mine are TL-SG108E v1's, and all of them have that same flaw where you can access the management page, no matter what VLAN I isolate the port too. Of course I was just going to replace the switches outright with something new, but because I need 3 Small 8 Port Switches at different locations throughout the massive building, and he doesn't have the budget to get wiring done the way it should have been done in the first place, I would prefer to just make these essentially free switches work correctly.
So I was researching modifying the config file, when I just happened to come across your post. I already am familiar with the CH341a Mini Programmer, as this is what I use to flash "Bricked" Motherboards and GPU's for Clients. It will be a pretty simple matter to flash the Memory with your very detailed Instructions. I really thank you for that. Will be working on flashing all 3 this weekend and will try to remember to report back to show that I can now Make it so that the ports I don't want to have access to management, don't.
Thank You!
-
@mattthetechlv said in TP-Link Easy Smart Switch security question:
I can now Make it so that the ports I don't want to have access to management, don't.
Are you using them as dumb and all just in 1 vlan, and you just want to prevent access to the gui..
Because while it is a security issue - its a bit more than just access to the admin gui :)
That they thought they could just leave every port in vlan 1, and let other ports be in other vlans is just beyond crazy.. How this got through any sort of review is just beyond crazy. I really wouldn't trust that company with anything other than a dumb switch..
-
@johnpoz I agree, it is insane how this ever got past their Design team. Not the biggest TP-Link fan myself, just trying to make something happen with no budget as a favor to a friend. If this works as I hope it will, I intend to carry Multiple VLAN's to different ends of the property, going to these switches downstream in 3 different areas. 4 VLAN's Total. I have my management VLAN already sectioned off and am not sending that VLAN to any of these switches, I just didn't want anyone to be able to plugin to any empty ports on any of these switches to be able to reconfigure, as some of my friends employee's think they are smart, so I am just trying to avoid as much as possible. I am hoping with the Netgear firmware flashed onto these devices it will neutralize the security threat of VLAN's leaking over.
The Only Port that I will keep VLAN 1 Open on will be Boxes that I and my friend only have credentials too, so as long as no one switches ports out on me (And I intend Locking the switches behind a locked Cage to discourage this) it should be sufficient, as long as this firmware solves the VLAN Crosstalk issues. Not too impressed with Netgear either Mind you, but I have used the GSS108E as a cheap solution in the past and didn't have any VLAN related Security Issues, so I am hopeful this will work. Will find out soon enough though.
Is there some other Security Issue other than the VLAN Crosstalk/(Not being able to remove VLAN 1 Tags From Ports) that I should be aware of with this switch?