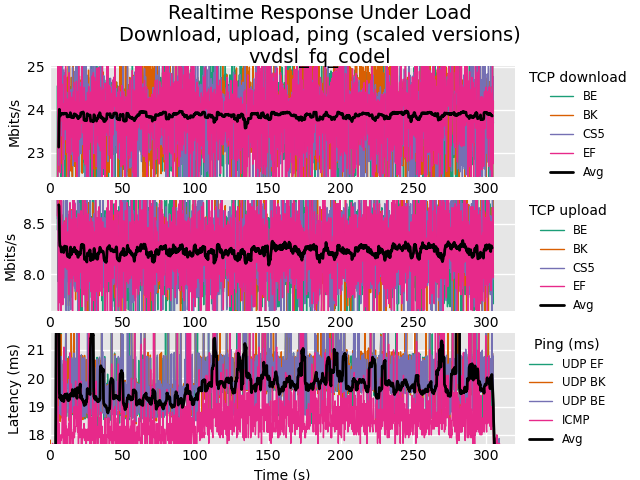
Playing with fq_codel in 2.4
-
@thiasaef I have mine on the Floating (with Quick checked) applied to WAN. May that can work for you?
-
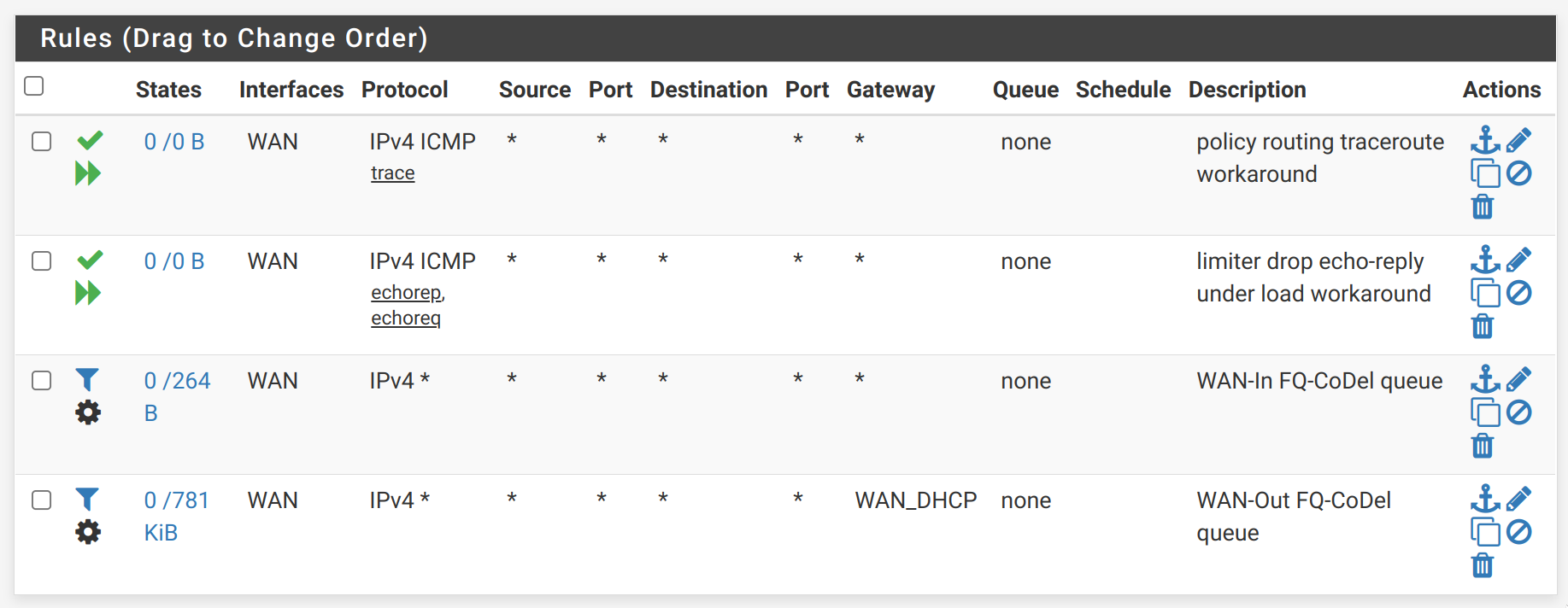
@bartkowski, my floating rules look like this:
Traceroute output:traceroute netgate.com traceroute to netgate.com (208.123.73.73), 30 hops max, 60 byte packets 1 _gateway (192.168.20.1) 0.098 ms 0.138 ms 0.080 ms 2 208.123.73.73 (208.123.73.73) 2.615 ms 2.822 ms 4.052 ms 3 * * * 4 208.123.73.73 (208.123.73.73) 22.185 ms 17.234 ms 17.226 ms ... 8 208.123.73.73 (208.123.73.73) 18.800 ms 18.792 ms 21.285 ms 9 * * * 10 * * * 11 208.123.73.73 (208.123.73.73) 167.760 ms 169.189 ms 169.182 ms ... 15 208.123.73.73 (208.123.73.73) 167.513 ms * 164.364 ms -
I'm stupid
 ... all I had to do to make it work was to enable the
... all I had to do to make it work was to enable the --icmpoption in traceroute, since traceroute uses udp by default on linux.PS: Could someone explain me why fq_codel still works in both directions when I disable the 3rd floating rule (WAN-In FQ-CoDel queue).
-
@thiasaef Are you really sure that it works?
I made the same mistake before that the states were not cleared to the test IPs and resulted the same as before. Make sure to kill all states to the testing server before testing again. -
@mind12 it definitely works if I add the
-Iflag to the traceroute command, but the 1st floating rule (policy routing traceroute workaround) seems to have nothing to do with it.I logged the outgoing traceroute traffic both with and without the
-Iflag using Wireshark, but I could not find any packets of theICMP subtype: Traceroute.I would be glad if someone with more expertise than us would chime in on this.
-
@thiasaef I replied to this I'm sorry, not the traceroute part
"PS: Could someone explain me why fq_codel still works in both directions when I disable the 3rd floating rule (WAN-In FQ-CoDel queue)."
-
@mind12 if I disable the 3rd floating rule, reset the firewall state table and then run the waveform bufferbloat test, I get the following result: https://www.waveform.com/tools/bufferbloat?test-id=9cced6ab-e6a9-48b9-a7a5-c562dc7df528, my limiter is set to (96, 36).
-
I believe you need third rule (WAN in) only if somebody initialize connection from "internet" and connects to your WAN (so you also need some other rule to allow connection from "internet" to your WAN)
Your WAN out rule makes almost all work because it is working with traffic from your LAN going to internet and all responses (matching response is like the same traffic as your WAN out).
Because of that for fq_codel I have only one rule (but I also use different approach - when you have rule on "LAN in" there is no problem with ping and traceroute)
I hope it makes sense and I'm not wrong :)
-
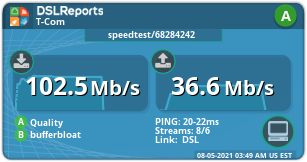
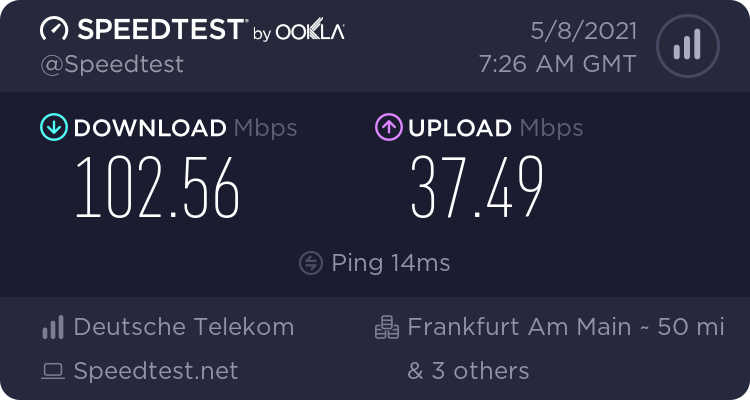
Flent is amazing - simple yet incredibly powerful! The result after optimizing my VVDSL line:
Before:
https://www.waveform.com/tools/bufferbloat?test-id=9bee8331-5e7f-4503-a74d-d146ab511ab9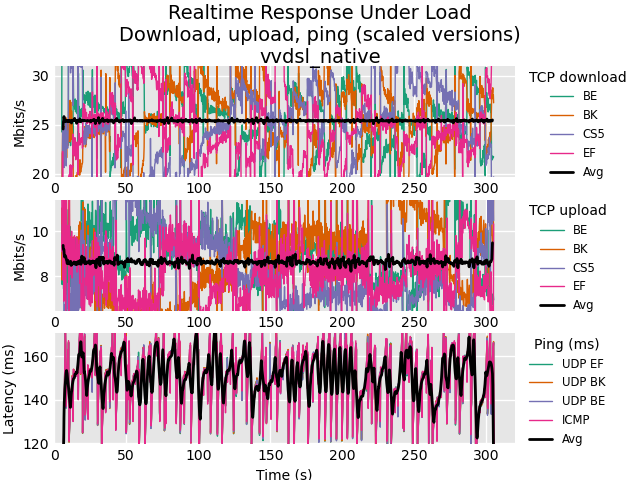
rrul-2021-05-07T200244.228034.vvdsl_native.flent.gzAfter:
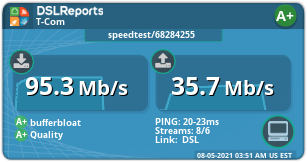
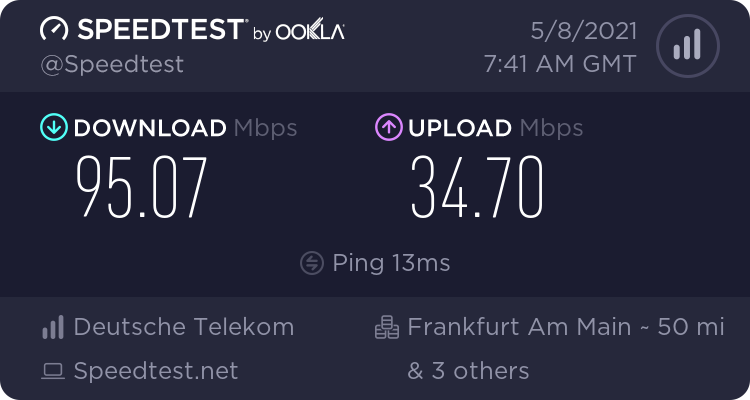
https://www.waveform.com/tools/bufferbloat?test-id=1ccd779a-c3f3-4b0f-be46-22638b446d96 -
Hi, what about "hn ALTQ support" setting? Is it recommended enabled or disabled in 2.5.1?
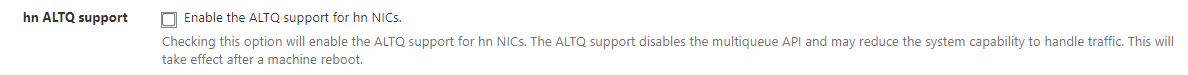
-
Is there a recommended strategy for when the WAN speed fluctuates significantly, such as with a cellular connection (e.g., LTE)?
-
@thiasaef
Not that I know of. If you can change the settings via a script, perhaps you can run a loop that runs a ping and when its high, drops the speed and checks againGargoyle router which is a version of openwrt does it well though, auto speed adjust.
-
Hi guys,
just want to ask how to add a 1mbit guarantee to a voice vlan on the limiter? I am a bit scared that voip does not work if someone in the network max out upload/download ... i already use QoS as best i can, but i think reserved bandwith for the vlan is maybe safer?
-
@robnitro That sounds really good.
-
B bartkowski referenced this topic on
-
B bartkowski referenced this topic on
-
B bartkowski referenced this topic on
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
T thiasaef referenced this topic on
-
T thiasaef referenced this topic on
-
T thiasaef referenced this topic on
-
T tman222 referenced this topic on
-
T tman222 referenced this topic on
-
T tman222 referenced this topic on
-
T thiasaef referenced this topic on
-
T thiasaef referenced this topic on
-
T thiasaef referenced this topic on
-
 M m0nji referenced this topic on
M m0nji referenced this topic on
-
T thiasaef referenced this topic on
-
T thiasaef referenced this topic on
-
T tman222 referenced this topic on
-
T tman222 referenced this topic on
-
M Mixka referenced this topic on
-
M Mixka referenced this topic on
-
M Mixka referenced this topic on
-
M Mixka referenced this topic on
-
M Mixka referenced this topic on
-
M Mixka referenced this topic on
-
M Mixka referenced this topic on
-
M mkcharlie referenced this topic on
-
M mkcharlie referenced this topic on
-
M mkcharlie referenced this topic on
-
M mkcharlie referenced this topic on
-
M mkcharlie referenced this topic on
-
 H HLPPC referenced this topic on
H HLPPC referenced this topic on