Playing with fq_codel in 2.4
-
@uptownvagrant no change in behaviour with 1508 quantum. I'll test just the VDSL limiters enabled later this evening.
-
Limit could be lowered to help out:
https://www.bufferbloat.net/projects/codel/wiki/Best_practices_for_benchmarking_Codel_and_FQ_Codel/#tuning-fq-codelWhen running it at 1GigE and lower, today it helps to change a few parameters given limitations in today’s Linux implementation and underlying device drivers. The default packet limit of 10000 packets is crazy in any other scenario. It is sane to reduce this to a 1000, or less, on anything running at gigE or below. The over-large packet limit leads to bad results during slow start on some benchmarks. Note that, unlike txqueuelen, CoDel derived algorithms can and DO take advantage of larger queues, so reducing it to, say, 100, impacts new flow start, and a variety of other things. We tend to use ranges of 800-1200 in our testing, and at 10Mbit, currently 600. -
@uptownvagrant Sorry for the delay, just got a chance to test it without the dual wan. No change in the result.
-
@robnitro Thanks for the suggestion, It has seemingly improved my cable connection responsiveness slightly but doesn't make a difference to the upload problem on vdsl.
-
I wanted to give a brief update - I actually am here about the issues with traceroutes showing the default destination addresses for every hop, caused by the Floating Firewall rule.
I fixed this on my side, initially, by only having the rule shape TCP/UDP - but some other clients do traceroute via UDP so I had this same issue. Instead, there's a firewall option to limit/scope it down to particular TCP flags - you can set the ones you wish, but I ultimately ended up targeting it to "Any" protocol, and "Any flags" - this fixed it for me. :)
EDIT: My pfSense randomly crashed... and... it rebooted... and... somehow now it isn't working.
Sigh. Guess I'm back to applying this to a non-floating rule. :( -
Hi, what rule did you use for non floating?
When I do tracert from windows, it shows only 2 hops. Router and then the destination.From openwrt dumb access point, all hops show fine like From the router I get all of the hops. Floating rule instant match allow any IPV4 ICMP trace - and another rule icmp any at top of list. So that means it should skip using the codel limiters right? I just dont understand why my desktop client gets bad tracert info?
-
i actually just reverted to using a simple TCP/UDP floating rule, setting up the non-floating was a huge pain (I had it working before) but can't remember how.
I'm going to be creating exemptions / rules that exempt specific clients in the future - now that it's working fine (on my primary use case, Windows!)
Here is the exact rule I have (that is, somehow, letting pfSense UDP traceroute work - I am tired of messing with it / don't care). Anything that is missing means it's default.
Action: Pass
Interface: WAN
Direction: Out
Addr Family: IPv4
Protocol: TCP/UDP
Gateway: WAN_DHCP (my gateway selected)
In/Out Pipe: WANUpQ (my name) & WANDownQ (my name)Here are the rules I have:
Firewall Rules > Traffic Shaper > "Limiters""CODEL_QMDown"
Limiter: Enabled
Bandwidth: 320 Mbit
Queue Management Algorithm: CoDel
Scheduler: FQ_CODELSubqueue, "WANDownQ"
Queue algorithm: CoDel"CODEL_QMUp"
Limiter: Enabled
Bandwidth: 340Mbit (yes, I have higher upload than download)
Queue management algorithm: CoDel
Scheduler: FQ_CODELSubqueue, "WANUpQ"
Queue algorithm: CoDel
I know these are basically defaults - I'm not sure why these work? I simply re-created everything, and now everything works great... it's quite odd. I'm curious if there is an issue with pfSense and having the rules edited, or large changes made to the queues (I hit Save/Apply, particularly, after every single change / creation - no going back and editing for me!)
Quite odd. I've used FQ_CoDel in other devices/implementations and have never run into these nuances. It's working great, now, though - but the traceroute/etc was bothering me horribly. With these rules (no floating rule for 'any') it seems to be working great... for... whatever reason.

-
Hi all!
Configured limiters and now my traceroute always shows resolved IP address instead of actual hops.
I`ve read here this is common but just to be sure, is this supposed to be like this or is it a bug?Thanks!
-
Hi guys,
I’m also having an issue with my upload speed... So I have a 400Mbit down / 40 Mbit up connection, and I've followed the guide here to enable the limiters, filling in the 400 and 40 as my down and up speeds.
However when I do speedtests, while my bufferbloat is now gone... I no can no longer reach my maximum speeds.
Down I may get around 360Mbit max which I can live with butup is just pathetic, maybe between 2-8Mbit at most....Is this known? Anything I can do to improve this? I played with the Queue Length value which helped a bit, but in the end didn't really have too much of an impact....
Limiters: 00001: 400.000 Mbit/s 0 ms burst 0 q131073 10000 sl. 0 flows (1 buckets) sched 65537 weight 0 lmax 0 pri 0 AQM CoDel target 5ms interval 100ms ECN sched 65537 type FIFO flags 0x0 0 buckets 0 active 00002: 40.000 Mbit/s 0 ms burst 0 q131074 1000 sl. 0 flows (1 buckets) sched 65538 weight 0 lmax 0 pri 0 AQM CoDel target 5ms interval 100ms ECN sched 65538 type FIFO flags 0x0 0 buckets 0 active Schedulers: 00001: 400.000 Mbit/s 0 ms burst 0 q65537 50 sl. 0 flows (1 buckets) sched 1 weight 0 lmax 0 pri 0 droptail sched 1 type FQ_CODEL flags 0x0 0 buckets 0 active FQ_CODEL target 5ms interval 100ms quantum 1514 limit 10240 flows 1024 ECN Children flowsets: 1 00002: 40.000 Mbit/s 0 ms burst 0 q65538 50 sl. 0 flows (1 buckets) sched 2 weight 0 lmax 0 pri 0 droptail sched 2 type FQ_CODEL flags 0x0 0 buckets 0 active FQ_CODEL target 5ms interval 100ms quantum 1514 limit 10240 flows 1024 ECN Children flowsets: 2 Queues: q00001 50 sl. 0 flows (1 buckets) sched 1 weight 0 lmax 0 pri 0 AQM CoDel target 5ms interval 100ms ECN q00002 50 sl. 0 flows (1 buckets) sched 2 weight 0 lmax 0 pri 0 AQM CoDel target 5ms interval 100ms ECN -
You are supposed to set the limiters lower than your actual connection speed. I set mine to 95% of tested(not ISP advertised) speed.
Also please use the guide posted a little while earlier. The one from the hangouts session is outdated and does not cover a bug workaround.
https://forum.netgate.com/post/807490
P.S - I am also on Ziggo NL 240/24 connection.
-
@xciter327 Even at 95% of 400/40 which is 380/38, the upload speed is nowhere near that. The download at least comes in the vicinity.
-
@Veldkornet I don't suppose it's a PPPoE connection? I had a similar problem.
-
Hi how did you resolve pppoe problem?
Thanks! -
@maverick_slo I didn't. I am only able to use the Download shaper for my PPPoE WAN. It works perfectly on my other WAN which is DHCP.
-
@csutcliff Nope, mine is just a DHCPv4 connection
-
@Veldkornet said in Playing with fq_codel in 2.4:
@xciter327 Even at 95% of 400/40 which is 380/38, the upload speed is nowhere near that. The download at least comes in the vicinity.
Hm. That should not be. Did You follow the guide I linked? Also what hardware is the pfsense running on? Limiters add extra CPU usage. Take a look with "htop -d 1" (need to install it first "pkg install htop") and see if You are peaking the CPU while doing the test.
-
@xciter327 ah! I didn't see the guide. I've now re-created everything as per the guide... although it didn't change the results...
I have a PCEngines APU2. I just had a look in "top" while doing the tests. Didn't really see anything climb very high at all. Even then, if it can handle the download, it should be able to manage the upload which is 10% of the download.
If I watch the test, the upload starts strong and climbs to around 20Mbit quickly, for 2 seconds or so, but then drops down to around 4/5 for the remainder of the test where it eventually finishes.
-
Could You perhaps post some picture of your firewall rules and limiter config? I am shaping my Ziggo connection on a Zotac NUC, which theoretically should be less powerful than the APU2. Also make sure You clear the states/reset the firewall when applying the limiters. Keep an eye in the system log for any log messages when You apply the limiters as well.
-
I can post screenshots instead of the below.. but it will take lots of space. I just checked everything though, and except for the speed limits, to me it looks the same as in the post. Might as well just be a copy paste. Looking at the floating rule screenshot though, I see that the WAN-In FQ-CoDel queue is pretty small considering all the tests I was doing... normal?
Also, see how the upload just dies off:
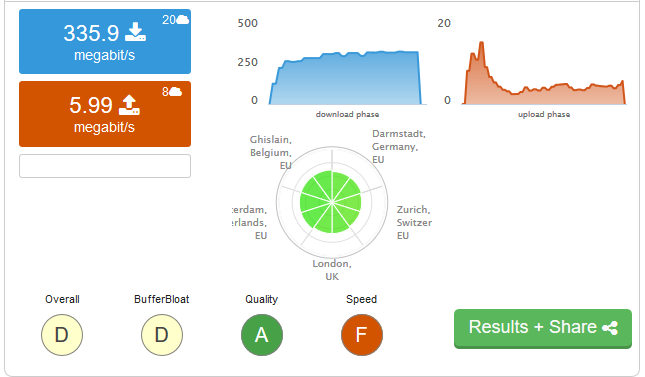
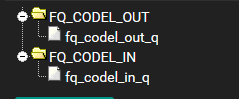
FQ_CODEL_OUT
Name: FQ_CODEL_OUT Bandwidth: 38 Mbit/s Mask: None Queue Management Algorithm: Tail Drop Scheduler: FQ_CODEL target: 5 interval: 100 quantum: 300 limit: 10240 flows: 20480fq_codel_out_q
Name: fq_codel_out_q Mask: None Queue Management Algorithm: Tail DropFQ_CODEL_IN
Name: FQ_CODEL_IN Bandwidth: 380 Mbit/s Mask: None Queue Management Algorithm: Tail Drop Scheduler: FQ_CODEL target: 5 interval: 100 quantum: 300 limit: 10240 flows: 20480fq_codel_in_q
Name: fq_codel_in_q Mask: None Queue Management Algorithm: Tail DropFirewall Rules - Floating:
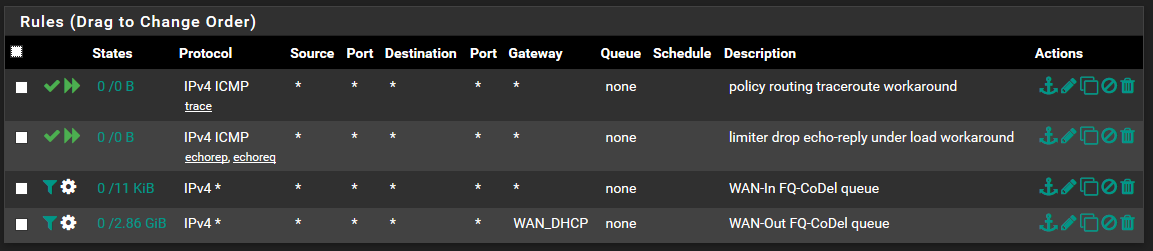
policy routing traceroute workaround
Action: Pass Quick: Tick Apply the action immediately on match. Interface: WAN Direction: out Address Family: IPv4 Protocol: ICMP ICMP subtypes: Traceroute Source: any Destination: any Description: policy routing traceroute workaroundlimiter drop echo-reply under load workaround
Action: Pass Quick: Tick Apply the action immediately on match. Interface: WAN Direction: any Address Family: IPv4 Protocol: ICMP ICMP subtypes: Echo reply, Echo Request Source: any Destination: any Description: limiter drop echo-reply under load workaroundWAN-In FQ-CoDel queue
Action: Match Interface: WAN Direction: in Address Family: IPv4 Protocol: Any Source: any Destination: any Description: WAN-In FQ-CoDel queue Gateway: Default In / Out pipe: fq_codel_in_q / fq_codel_out_qWAN-Out FQ-CoDel queue
Action: Match Interface: WAN Direction: out Address Family: IPv4 Protocol: Any Source: any Destination: any Description: WAN-Out FQ-CoDel queue Gateway: WAN_DHCP In / Out pipe: fq_codel_out_q / fq_codel_in_q -
Looks good to me. Mine at home is the same, with lower speeds tough. When You do the dslreports test, You can open up htop(prefer it because it's easier to deal with multiple cores) in one window and "ipfw sched show" in another to see if the limiters are actually matching traffic. Anything else on this box(like squid or snort)?



