Playing with fq_codel in 2.4
-
@forbiddenlake Thanks for this info. I backed out of fq_codel a couple of months ago but may revisit it using the info you provided.
-
What I don't understand is that with no limiters and QOS disciplines not enabled, my traceroutes are still not working. Where else could there be an issue? I don't need qos now with gigabit fiber.
-
@forbiddenlake said in Playing with fq_codel in 2.4:
@JonH I have the same problem, and after reading 600 more posts in this topic, I believe I have the answer for you.
You're using a traceroute that uses UDP by default, and you're shaping TCP and UDP, and this is a bug in pfSense.
You can work around it by using ICMP for traceroutes, e.g. (disclaimer: I'm using Linux):
alias traceroute='traceroute -I'Some here have mentioned that you may also be able to work around it by applying the limits on LAN rules, not floating rules, however the alias is good enough for me for now, so I stopped reading at around 600 posts and can't show you what to do there :)
Hi, you have details of this bug? thanks.
-
@chrcoluk I believe this "bug" is being referenced. Certain configuration will cause pfSense to not decrease the TTL when forwarding. Policy routing is used with direction=out limiters, so it's a common cause of the behavior folks are seeing in this thread where traceroute doesn't work. If you're using configuration similar to this, there is a provision for ICMP traceroute but if you are using a traceroute program that is using UDP packets then those packets would use policy routing and the TTL would not decrease on those packets at pfSense.
-
This post is deleted! -
@robnitro said in Playing with fq_codel in 2.4:
What I don't understand is that with no limiters and QOS disciplines not enabled, my traceroutes are still not working. Where else could there be an issue? I don't need qos now with gigabit fiber.
The ISP could be the issue. I know Verizon has issues with traceroutes not showing properly in some areas, essentially showing your router then the destination host in a 2-hop traceroute (or more if you have multiple routers between you and Verizon).
This thread on DSLReports shows it starting back in late 2018, but still noted as happening in August this year in the thread. I'm still seeing the issue though. Has VZ disabled TTL propagation?
-
Hi guys an update from myself.
I did some more messing around with my limiters and changed my main pipe to this.
FQ_PIE target 5ms tupdate 15ms alpha 0.125 beta 1.25 max_burst 150ms max_ecnth 0.1 quantum 300 limit 1000 flows 1024 ECN CapDrop TS Derand
also
q131073 50 sl. 0 flows (1 buckets) sched 65537 weight 0 lmax 0 pri 0 AQM CoDel target 5ms interval 100ms NoECN
So I ditched droptail.
Now on downstream congestion it performs "way" better. I do still have to provide a sizely overhead for it to not affect latency, but on FQ_CODEL with droptail I needed to supply a massive 50-60% overhead, on this new configuration 2% isnt enough but it seems 12% is. I have yet to try anything between 2% and 12% to see how low I Can get it, but already 12% I consider a massive improvement. :)
Also the masking is set to on src /24 not dest.
-
@w0w said in Playing with fq_codel in 2.4:
both are on the same LAN
I have had the same issues with pf .
FQ_Codel in 2.4.4 doesnt work with floating rules.
Only works via gui as a lan limiter with children and weighted subqueues and even so tcp and udp traffic (udp voip) still experiences spikes under tcp load. ; Added that I have udp voip sub-queues (weighted) under the parent limiter,if not used like this fq_codel and fq_pie (with no interface shaping) its a mess.
On top of this traffic shapers on the interfaces always hinders the floating rule method so I have disabled traffic shping on the interfaces as per the linux method.
What is odd that fq_codel actually works with all ipv4 traffic on debian with all protocols very well,when applied to the wan i/f.
With freebsd for some reason fq_pie only seems to work with udp packets without shaping all ipv4???,whereas fq_codel with altq only works with tcp? as per the original codel implementation.
Hoping smart queuing works soon in the distribution as fq-codel does not perform the same as linux by far.
Anyone else had this issue ?.
-
@m8ee how does your rules look like? I have not had any problems getting fq-CoDel to work in either 2.4.4 or 2.4.5 with limiters and floating rules.
-
Hi all,
I'm a new PFsense user here.
I set up my FQ_Codel in my fresh install as per https://www.youtube.com/watch?v=o8nL81DzTlU
However I get a bunch of flowset errors in my syslog any ideas? I've been reading it's a bug but these messages are from 2017... and I'm unsure if they're still a thing in 2020? I'm currently at work on break and decided to chip in my concern.
Is the video guide maybe outdated? Does anyone have the 2020 version?
Thanks.
-
@Zeny001 try setting queue management algorithm under the queues to Tail drop and see if that helps.
-
Wow. That did it. From C bufferbloat on DSLreports to A+.
Thanks a bunch. For anyone having trouble remember to uncheck ECN since tail drop does not support it
I lost about 300mbps of bandwidth though.
I have a gigabit connection and I'm getting about 600mbps now, was getting 900ish before. I dont really care though, but if anyones got any tips let me know :)
-
@Zeny001 you could try lowering limit by a factor of ten and increase flows by the same and see if that makes a difference.
-
Just wanted to say thanks - I applied the technique in the video and my Bufferbloat and Quality on the DSL reports test went from C/C to A/A+. Hopefully this will resolve some weird network issues I've been having.
-
@uptownVagrant - wanted to thank you for posting these detailed steps on how to setup FQ-CoDel using floating rules.
https://forum.netgate.com/topic/112527/playing-with-fq_codel-in-2-4/815
Originally I had FQ-CoDel setup on my LAN interfaces, but using floating rules the approach is definitely simplified. Everything is working great and as expected. I use Linux so do run into the issue with traceroute (mentioned earlier in this thread) because UDP is used by default. Easily worked around though by using traceroute -I instead (which will use ICMP). Do you have any suggestions how to modify the floating rules so that traceroute using UDP might work properly?
Thanks in advance.
-
This post is deleted! -
Não tive mais problemas depois que fiz essa configuração :
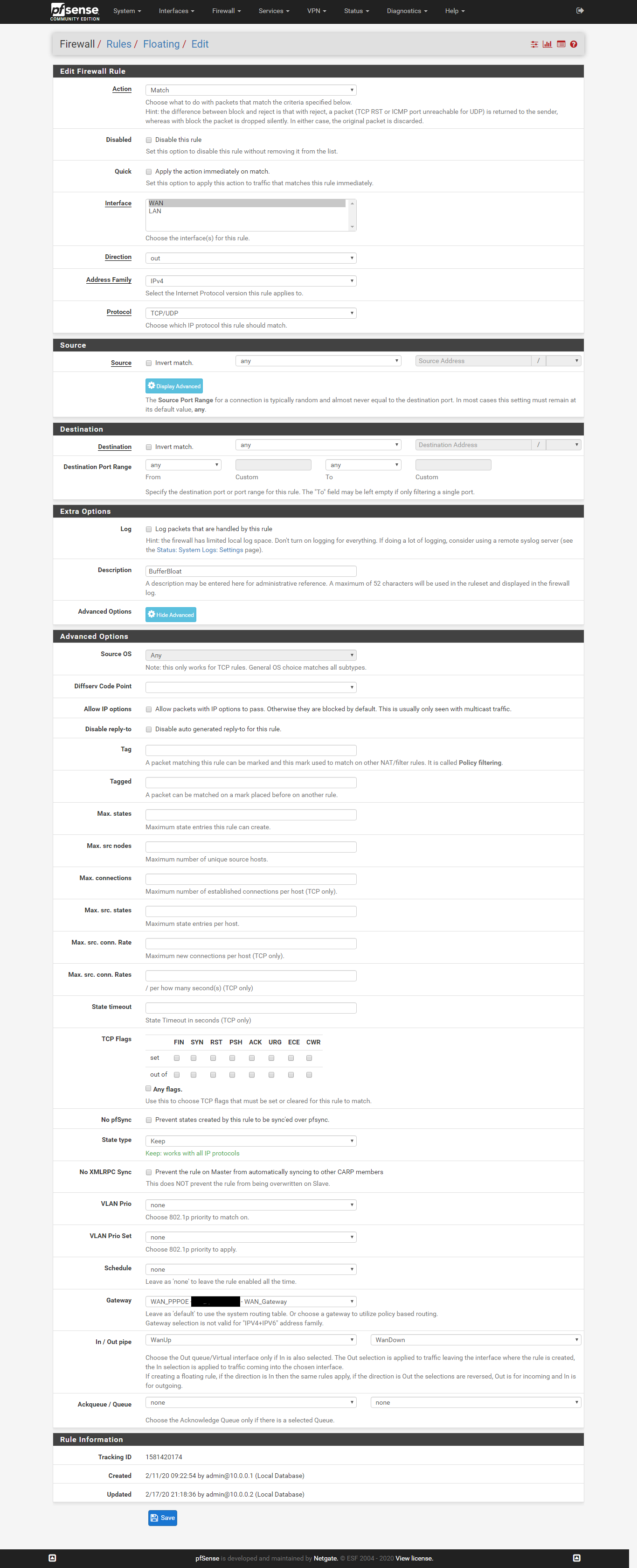
-
@tman222 using traceroute in windows gives the same problem, the only solution so far seems to be making a rule omitting ICMP traffic from FQ-CoDel.
Weird thing is that it works fine with IPfire which i briefly tried some months ago, so it might be something with the FreeBSD implementation of it. -
@tman222 said in Playing with fq_codel in 2.4:
Do you have any suggestions how to modify the floating rules so that traceroute using UDP might work properly?
For me the following works:
Create floating rule with limiters (with match action) not on "WAN out" but on "LAN/VLAN in" (in one floating rule you can select multiple interfaces/vlans) for traffic with source "any" and destination "not-your-local-networks-alias" - that works great for me, and for my easy setup I need only one floating rule for all my VLANS and with "in" traffic you don't need to set gateway.Unfortunately it won't work for traffic with source IP of your pfsense router
-
@uptownVagrant said in Playing with fq_codel in 2.4:
1.) Add quick pass floating rule to handle ICMP traceroute. This rule matches ICMP traceroute packets so that they are not matched by the WAN-Out limiter rule that utilizes policy routing. Policy routing breaks traceroute.
Are you guys actually sure it is this issue? The linked doc page and bug #932 is quite the opposite what we see here. It makes perfect sense that policy routing in certain cases does not decrease TTL making router (pfsense box) invisible in traceroute, but the rest of the hops looks ok.
Our issue is that it shows only one hop which is destination and nothing else. Which arguably doesn't make sense. Have anyone actually look into it or just found not quite similar traceroute issue and call it a day?
With Limiter:
1 <1 ms <1 ms <1 ms <...> [192.168.0.1] 2 * * * Request timed out. 3 11 ms 14 ms 8 ms one.one.one.one [1.1.1.1] 4 12 ms 11 ms 12 ms one.one.one.one [1.1.1.1] 5 12 ms 14 ms 18 ms one.one.one.one [1.1.1.1] 6 13 ms 13 ms 11 ms one.one.one.one [1.1.1.1] 7 13 ms 10 ms 11 ms one.one.one.one [1.1.1.1] 8 55 ms 54 ms 54 ms one.one.one.one [1.1.1.1] 9 49 ms 49 ms 51 ms one.one.one.one [1.1.1.1] 10 37 ms 37 ms 56 ms one.one.one.one [1.1.1.1] 11 55 ms 52 ms 50 ms one.one.one.one [1.1.1.1]Without Limiter:
1 <1 ms <1 ms <1 ms <...> [192.168.0.1] 2 * * * Request timed out. <removed some hops, but they are properly shown> 8 55 ms 53 ms 50 ms ae-12.r24.amstnl02.nl.bb.gin.ntt.net [129.250.3.81] 9 59 ms 54 ms 53 ms ae-7.r03.amstnl02.nl.bb.gin.ntt.net [129.250.2.103] 10 58 ms 59 ms 60 ms 81.20.65.150 11 56 ms 64 ms 56 ms one.one.one.one [1.1.1.1]