Installation with Whole Disk Encryption
-
@harika1258 said in Installation with Whole Disk Encryption:
I want to encrypt partitions with ZFS without entering passphrase every time when os is booting
Then there is ZERO point to the encryption in the first place... What is it protecting??? The whole problem of FDE on something like a router is that it needs intervention for boot..
If there is no passphrase, then when it boots the encryption is just unlocked. Like a zipfile without a password on it - anyone can open it. You put a password on the zip file and you have to know the password to unlock it.
-
@johnpoz
if someone has physical access to appliance who can move the appliance 's hard drive to another system (computer with Windows os) to view and does everything.
I want to protect it in this case.
although I want, when pfsense is booting, we don't need any passphrase.
just want to protect files in attaching to machine who running windows OS ;-) -
@harika1258 said in Installation with Whole Disk Encryption:
just want to protect files in attaching to machine who running windows OS
So your wanting to protect it from idiot users? Why would I move the HDD to another system when I would just get the info off the thing while I have physical access to it??
I really think you need to do some research on what FDE actually protects you from..
So your scenario your wanting to protect against.. Windows not going to read a zfs anyway ;) Be it encrypted or not. And what appliance are you using exactly... Mine doesn't even have a HDD they could take out...
-
This post is deleted! -
@johnpoz
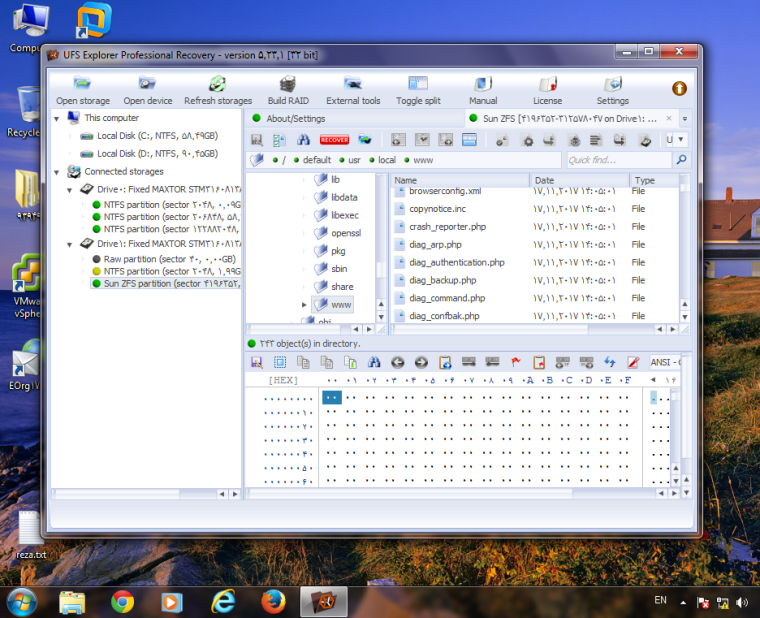
As you know, in windows OS, by UFS Explorer you can see partition that is set up with ZFS.
I use Nexcom Appliance .... -
Your adding normally non-existing issues : a system that runs virtual appliances shouldn't be made accessible by ordinary users, except for the services they offer remotely.
Only an 'admin' should access such a systems directly. -
I'm not quite sure I understand arguing against FDE with the justification "it's just a firewall" when this simple firewall has a robust package management system which features an impressive catalog of packages.
I personally use pfSense as a firewall, a dynamic DNS client to NoIP (which requires credentials), and a tinc (keys!) server to tie other pfSense boxes together. I see people leveraging pfSense for much heavier workloads so I definitely see the argument for FDE.
I also see that FDE is a PITA because, at boot, you have to either be physically present to enter credentials, share said credentials with somebody who's present, or expose IPMI (if you have it) to gain virtual KVM access to it.
Would it be possible to see something like dracut-crypt-ssh make its way into the feature list? I use it on everything as a backup for when tang/clevis isn't working in a predominantly CentOS-based environment. It would be quite handy to have pfSense have a similar functionality whereby it boots dropbear on a specific port, protected with a preconfigured keypair, that goes away once pfSense is fully booted. Just my $.02.
-
FDE is a PITA that is only useful if you're in an environment where there is a significant risk that someone will steal your disk so they can mount it elsewhere and look for prizes. Most people are not in that environment, and even if they were, there is usually nothing on the firewall that would be of any use to an attacker. Your mileage may vary, of course. Nobody else should have physical access to the box except you or other IT admins. Certainly not users.
-
This post is deleted! -
sorry to revive old post but I would like to reply for a specific use case no one brought up. As a journalist I need a higher level of security when accessing specific content. I use pfSense as a VPN gateway configure with FDE and zero-logging. It's a lot easier than having to setup vpn after every reboot on my boot-only USB OS.