SG-3100 Switch Configuration
-
Can someone please explain how to configure the switch in the 3100? I'm trying to have 2 VLANs/Subnets on this device. One is an internal network (VLAN10, 10.1.0.0/24) and the other is a guest network (VLAN 666, 192.168.255.0/24). I want to have LAN4 as a TRUNK to an access point. It should have both VLAN10 and VLAN 666 on it so it can present an INTERNAL SSID and a GUEST SSID.
I've got the following interfaces:
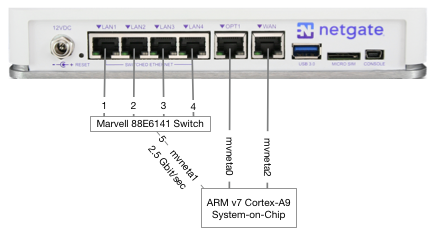
WAN: mvneta2
LAN: mvneta1
Guest: VLAN 666 on mvneta1Under INTERFACES / SWITCH / PORTS I've got:
LAN 1: PVID=1
LAN 2: PVID=10
LAN 3: PVID=10
LAN 4: PVID=1
LAN 5: PVID=1 HOSTUnder INTERFACES / SYSTEM / VLANs I've got:
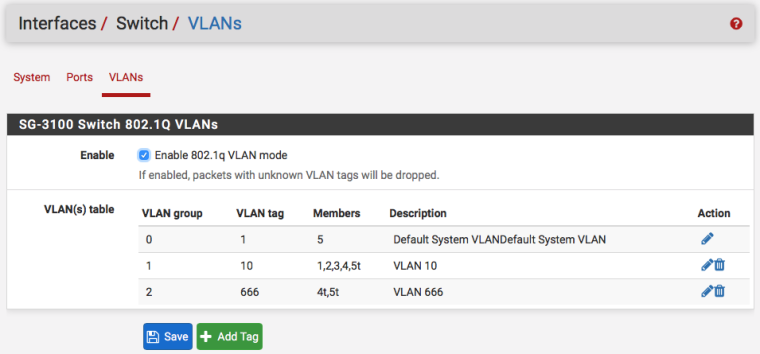
802.1q ENABLE CHECKED
VLAN Table
| VLAN Group | VLAN tag | Members | Description |
| 0 | 1 | 1,2,3,4,5 | Default |
| 1 | 10 | 2,3,4t,5t | INTERNAL |
| 2 | 666 | 4t,5t | GUEST |Whenever I assign my LAN interface to "VLAN 10 on mvneta1" I lose connectivity to the pfSense device from the laptop. However, from pfSense, I can still ping the laptop. It's super weird. Any help would be appreciated. thanks!
-
So I think I've got this mostly working, despite the lack of documentation (at least, that I could find online). I'm not sure why you have to create VLAN Groups that contain interfaces assigned to a certain VLAN, THEN go back to PORTS tab and assign a certain VLAN to a port. That makes no sense to me, but I've got a Cisco background.
I'm now concerned with how to trunk port 4 on the built in switch. I've got port 5 tagged and port 4 tagged in 2 VLAN Groups, one for VLAN 10 and one for VLAN 666. Is that all that's needed? Can anyone point me in the direction of actual documentation for how this switch module functions and configuration details?
-
Is that not working?
Be sure to be on 2.4.2 patch 1
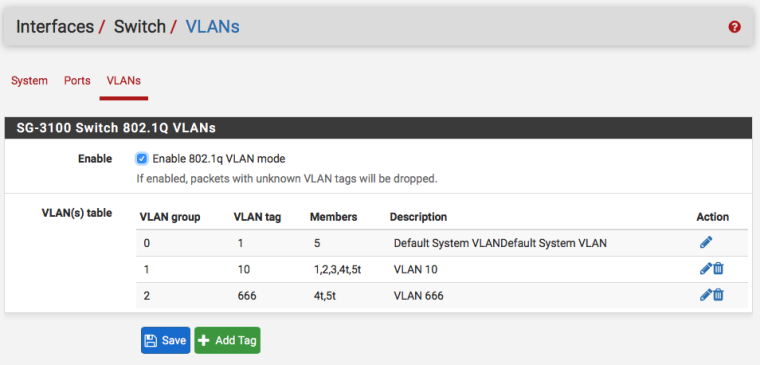
You should need something that looks like this:
Set 802.1Q mode in Interfaces > Switches, VLANs and Save
For clarity edit VLAN 1 and delete all but port 5. I am aware of the webgui glitch there and will be submitting a bug report on that.
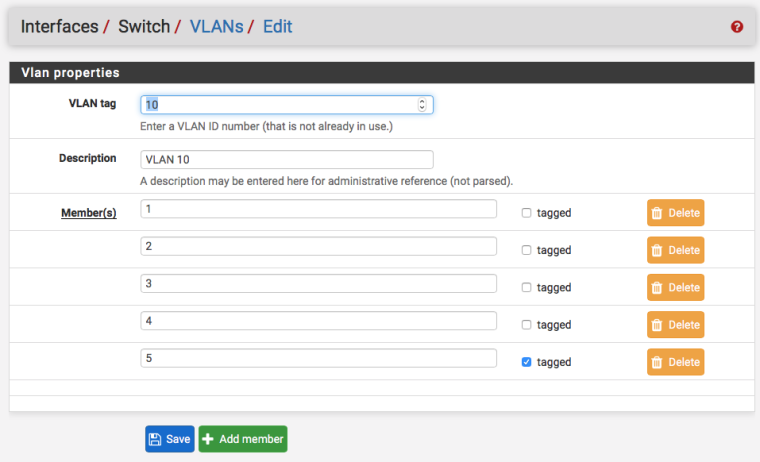
Add VLAN 10 creating 5 ports and setting them as 1, 2, 3, 4 tagged and 5 tagged
Add VLAN 666 creating two ports and setting them as 4 tagged and 5 tagged
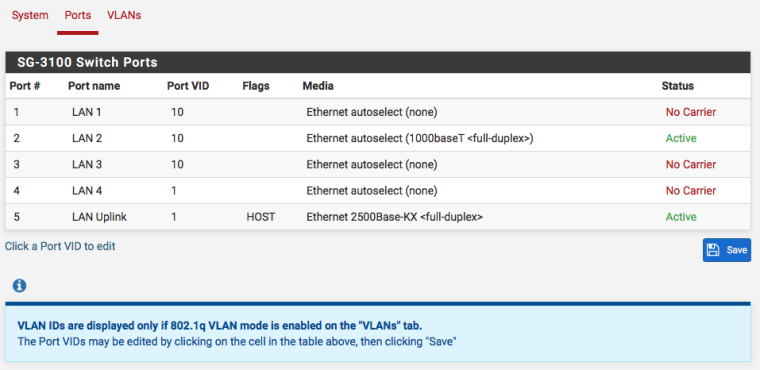
In Interfaces> Switches, Ports Set the PVID to 10. Click the PVID and be sure to backspace/clear everything out of it (another gui bug report coming for that) and set to 10. Do that on ports 1, 2, and 3 and Save.
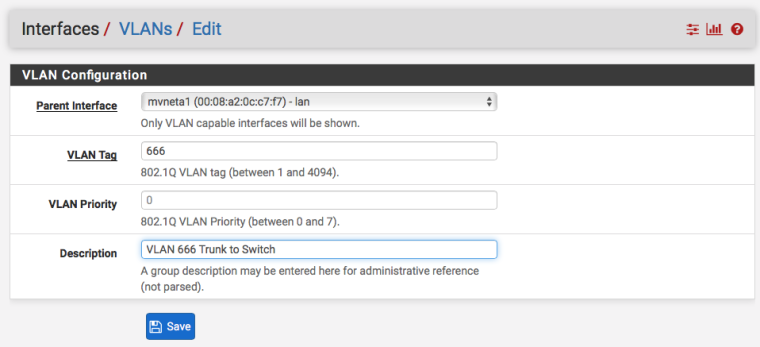
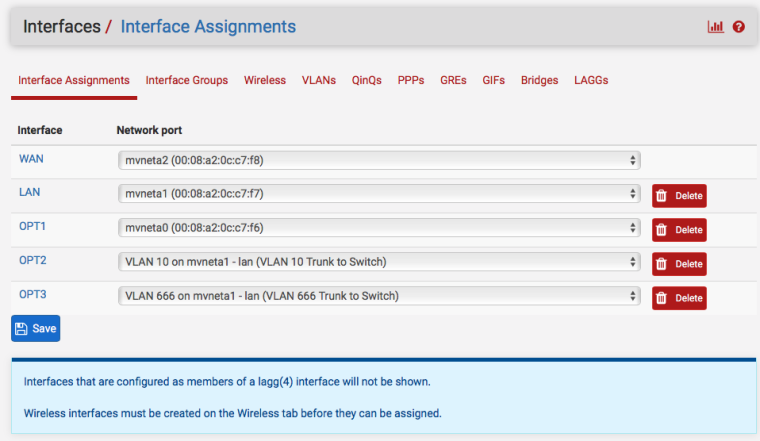
In Interfaces > Assignments, VLANs create VLAN tags 10 and 666 on mvneta1, which is actually the internal, 2.5Gbit "trunk" link from the SoC to the Switch.
In Interfaces > Assignments either set existing interfaces to the now-available VLAN interfaces or create new ones.
If you created new interfaces, edit them and enable, address, etc. Then create firewall rules and DHCP servers for them as you require.
-
Derelict,
Thank you for the response! I figured out most of what you said. However, when I changed the PVID on ports 1,2,3 I could no longer access the GUI. I had to go into the console and assign VLAN10 to mvneta1. Once I did that, the GUI was accessible again. It would be great if I could change those interfaces from the CLI/Console as well.
The other question I had is in regards to the AP that I want to hang off of LAN 4. As you know, I want VLANs 10 and 666 TAGGED to LAN 4, which I've setup. But, I want the AP to get a DHCP address for management from VLAN10. Do I go back to PORTS and assign 10 to port 4? The AP will pickup it's management IP based on the "NATIVE VLAN" of the interface it's on. In the Cisco world, I can change the NATIVE VLAN per interface:
interface Gig0/4 description Access Point switchport mode trunk switchport trunk encapsulation dot1q switchport nonegotiate switchport trunk native vlan 10 switchport trunk allowed vlan 10,666This Cisco switch config would allow the AP to grab it's management IP from VLAN10. Is this a possibility with the SG-3100? Can I change that VID to 10 and the AP will grab it's IP from VLAN 10? Thank you!
-
If you need port 4 to have VLAN 10 be the untagged/PVID (not tagged as you originally said) along with tagged traffic then do that.
Edit VLAN 10 and set port 4 to be untagged (uncheck tagged)
Edit the ports and set the PVID on port 4 to 10.
Yes, you can lock yourself out mucking about with layer 2 on the port you are connected to.
In your case I would have probably put a temporary layer 3 network on OPT1 and configured the switch from something connected there.
No, the CLI/Shell will not help in general. You need to make permanent changes via the GUI so they make it into config.xml. There is some basic capability there to add VLANs and number interfaces but it is generally intended to help get access to the node so the GUI can be used. Switch configuration is essentially brand new in the product and I do not believe the shell commands for the switch are caught up yet, if they ever will be.
-
Derelict,
That is what I ended up doing. If I come back and setup another VLAN for management, then I'll make that the UNTAGGED VLAN on that interface while tagging the other two. Thanks again for your help!
-
Added to Reply #2 for reference.
-
Ok I am having a bit of problem… This seems pretty straight forward... But doesn't seem to be be working with sg-3100 running 2.4.3
This should work with just the gui right??
So I set opt1 to be a 192.168.2.0/24 network so wouldn't lock myself out. I then setup the switch to be in q mode, and set port 1 with pvid 100. An set new vlan group and put port 1 in it untagged and 5 tagged
I setup dhcp server on this vlan interface. And move my connection over to lan1 and nothing... Maybe its late??
Connection is straight from my machine to the switch.. So can not be messing up any switch ports and same wire and interface grabs a 192.168.2 address when IP out in opt1 and access the gui that way. But when I move it over to port 1 nothing.
If just did it from the cmd line
[2.4.3-RELEASE][root@pfSense.localdomain]/root: etherswitchcfg etherswitch0: VLAN mode: DOT1Q port1: pvid: 100 state=1 <disabled>flags=0<> media: Ethernet autoselect (1000baseT <full-duplex>) status: active port2: pvid: 1 state=1 <disabled>flags=0<> media: Ethernet autoselect (none) status: no carrier port3: pvid: 1 state=1 <disabled>flags=0<> media: Ethernet autoselect (none) status: no carrier port4: pvid: 1 state=1 <disabled>flags=0<> media: Ethernet autoselect (none) status: no carrier port5: pvid: 1 state=1 <disabled>flags=1 <cpuport>media: Ethernet 2500Base-KX <full-duplex>status: active vlangroup0: vlan: 1 members 2 vlangroup1: vlan: 100 members 1,5t</full-duplex></cpuport></disabled></disabled></disabled></disabled></full-duplex></disabled> -
Yeah there's something not being done correctly when you switch to dot1q mode. All of those ports are disabled.
Edit/save the ports page and reboot. Those should say "FORWARDING" not "DISABLED"
I am pretty sure that has been fixed in 2.4.4, and is only necessary when you switch from port-based to dot1q mode. Subsequent config changes in dot1q mode should be fine.
If you don't want to reboot, run these:
etherswitchconfig port1 forwarding
run again for ports[2-5] -
Yeah I just woke up… Did a reboot and bam... Working WTF..
[2.4.3-RELEASE][root@pfSense.localdomain]/root: etherswitchcfg etherswitch0: VLAN mode: DOT1Q port1: pvid: 100 state=8 <forwarding>flags=0<> media: Ethernet autoselect (1000baseT <full-duplex,master>) status: active port2: pvid: 1 state=8 <forwarding>flags=0<> media: Ethernet autoselect (none) status: no carrier port3: pvid: 1 state=8 <forwarding>flags=0<> media: Ethernet autoselect (none) status: no carrier port4: pvid: 1 state=8 <forwarding>flags=0<> media: Ethernet autoselect (none) status: no carrier port5: pvid: 1 state=8 <forwarding>flags=1 <cpuport>media: Ethernet 2500Base-KX <full-duplex>status: active vlangroup0: vlan: 1 members 2 vlangroup1: vlan: 100 members 1,5t [2.4.3-RELEASE][root@pfSense.localdomain]/root:</full-duplex></cpuport></forwarding></forwarding></forwarding></forwarding></full-duplex,master></forwarding>Knew it was straight forward ;) Thought I had rebooted after putting in q mode though… Should of caught the disabled ;) DOH!!!
-
Yeah there's something not right there.
I did load 2.4.4-DEV and everything I saw that was wonky in the switch in 2.4.3 seems to be fixed, except the webgui field problem when you edit the Port VIDs. (Click then clear out the field completely if you need to change that.)
I'd stay at 2.4.3 for the time being though if you rely on that device.
-
Is possible I didn't reboot after… First time I did it was testing the other thread where he lost connectivity on the change.. Yeah for sure you can lock yourself out ;)
So then I fired up the opt interface and consoled in as well.. So no way to lock myself out - I knew the disabled was odd ;) But it was late last night and my brain wasn't working correctly or should of caught that it wasn't showing forwarding.
Thanks for kick to the ass ;) hehehe
Maybe I will reset it and play with actual set to forwarding mode. I plan on putting this box into production today and wanted to get some play time with the switch before I did that..
-
It's not a kick. You shouldn't have to reboot.
There is also a problem going from dot1q back to Port-based VLAN mode, which is also already fixed in 2.4.4, but I can't see a reason to do that. :)
Though there is a way to do port isolation in that mode which might have a niche somewhere.
-
Though there is a way to do port isolation in that mode which might have a niche somewhere.
Maybe if you want to isolate some devices, but still want them on the same network for easier traffic shaping.
-
I agree shouldn't have to reboot… But I was staring at those disabled and it wasn't clicking they should be showing forward. I was thinking they were showing disabled because I had nothing connected. And then when moved my client over since I couldn't get to the web interface couldn't tell.
But then when I looked at it via the console and saw disabled even on the interface I was connected too - it never clicked.. Lack of sleep and sure the beers didn't help ;) So the kick was pointing out that disabled.. Which thanks for that!
Before I even read your thread I had rebooted it when I woke up first thing as I was consoled in.. Wanted to see what it said about the switch while it booted.. And then when I looked at etherswitchcfg saw the forwarding mode... DOH ;)
We are up and running in it here at the office.. We really only needed 2 lan side interfaces. Have the opt as management and switch ports are all currently lan with just 1 connection.. But left it in q mode in case we need to break out some other networks at a future date, etc.
Nice to see speed you paying for finally. The old juniper we had on the connection was only 10/100 so max ever saw was like 90ish.. Now seeing 120mbps.. Few more to order for the other branch offices ;)
Its only the guest internet connection.. Love to get rid of beasts of cisco's they have here for the dual mpls connections - such a waste.. Pair of 4860s would be screaming overkill even.. Maybe at some point they will let me rotate those out.. But for now happy to get all the branch offices on netgate even if just for the guest internet connects..
-
Just to understand the switch/VLAN layout (before being able to put my hands on one of those units myself):
- A "VLAN Group" is just the row number in the VLAN table or can it do more than that?
- if mvneta1_port#5 is the uplink to the core then shouldn't it be port #0 rather than port #5? This seems counter-intuitive.
-
Doesn't much matter. It is what it is.
-
Thanks.
"VLAN Group" is or does what?
-
It depends on whether it is in port or dot1q mode.
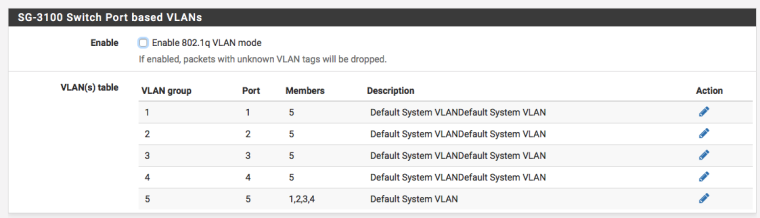
You can make what amount to "independent" switches with VLAN groups in port mode. But you probably don't want to put more than one group on port 5 if you intend them to be different broadcast domains.
You can also make a poor-man's port isolation in a single broadcast domain using something like the attached. In that config all four ports communicate with the "trunk" back to the layer 3 interface in the firewall but do not communicate with each other.
In dot1q mode each "group" is the collection of ports that have that VLAN tagged or untagged.