MFA for pfSense GUI
-
This post is deleted! -
TOTP has become commonplace. sad this is still a reality in 2022...
RIP cybersecurity attestation forms as pfsense is natively uninsurable
-
You know you can do this via Freeradius using Google Auth or mOTP?
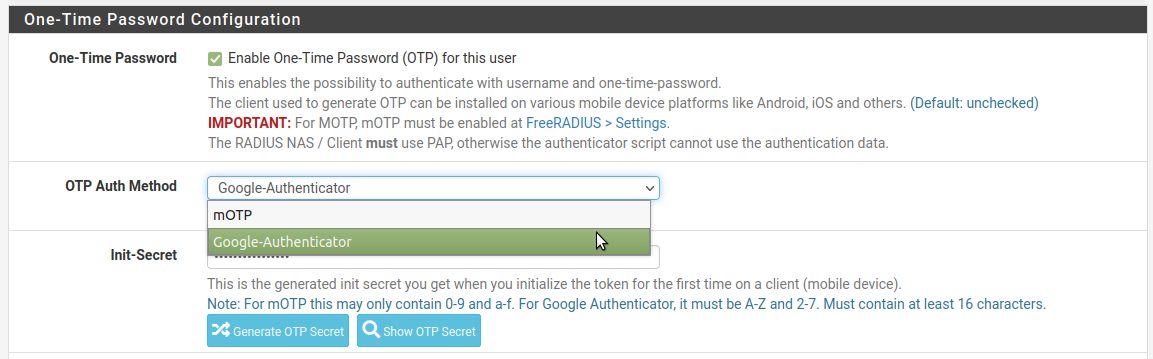
-
@stephenw10 I get that it's possible. It just feels unnecessary to have a dependency on the freerad package for this functionality.
-
@condescending_dev said in MFA for pfSense GUI:
@stephenw10 I get that it's possible. It just feels unnecessary to have a dependency on the freerad package for this functionality.
I don’t mean to stir up the discussion again, but it is a fact that cybersecurity insurance and company policies can become a pfSense showstopper because of MFA.
Yes, I know, install freeradius and do it that way, but you - like me - also know that there are several cases where that package stops running, doesn’t reinstall on upgrades and so on, and that just becomes a major problem if you are in uptime trouble as it is.
It would be nice if it was a backed in feature you could depend on in a standalone/isolated/no running packages situation as well.
-
@keyser said in MFA for pfSense GUI:
It would be nice if it was a backed in feature
I agree. I'll poke it further up the list if I can.
Steve
-
and just last week, we were stopped from using
pfSensebecause we failed to demonstrate a meaningful MFA to login to the webConfigurator.
We also failed to get Cyber Essential certificate (in UK) because of lack of MFA on the GUI.
We really need something sooner than later.
-San
-
If it were to be something considered in the future. Then please consider adding support for such things as FIDO/2. So that we could use hardware keys e.g. Yubikeys as well.
Please and thank you.

-
@macusers but why didnt you implement the suggestion asd outlined by @jimp
Use FreeRadius and Google Auth?I get where everyone is coming from - basically a standlone feature to do this but again....the feature technically exists now with the freeradius package. Im really not understanding the issue here. Use it or dont.
-
@michmoor said in MFA for pfSense GUI:
@macusers but why didnt you implement the suggestion asd outlined by @jimp
Use FreeRadius and Google Auth?I get where everyone is coming from - basically a standlone feature to do this but again....the feature technically exists now with the freeradius package. Im really not understanding the issue here. Use it or dont.
Because we have all tried doing upgrades :-)
Packages are supposed to install in the background, but that can occasionally fail - or cause issues, and then you are in big trouble if your physical console is a 1000 miles away.
Relying on a local installed 3rd party freeradius package for the second factor is a hen and the egg problem waiting to happen if you have any issues. -
@keyser if Radius fails isnt there a fallback to local auth then?
-
@michmoor said in MFA for pfSense GUI:
@keyser if Radius fails isnt there a fallback to local auth then?
and you back with no MFA again.
The thing, which is very hard for me understand: why it's so hard to acknwledge the issue and work towards a proper solution, rather than spending time convincinging people for a not-so-convenient work around.-San
-
@macusers ??? Im really not following here.
This is a problem enterprises have. I have TACACS and RADIUS deployed on my network gear. If my ClearPass servers fail, the fallback authentication method is local auth.
How is this any different here? Radius fails, local auth should be used. Is the assumption that no authentication should be used to manage a device if your central management platform fails? thats insane.. -
@michmoor said in MFA for pfSense GUI:
@keyser if Radius fails isnt there a fallback to local auth then?
If implemented correctly then yes, you should be able to configure that option. But as far as I remember, pfSense does not have this option - so the built-in admin either always works without MFA, or you do not have a fallback in case radius is down (because admin is disabled). I may be wrong here, but a couple of years ago I could not get it to work in a proper MFA certifiable way.
-
@keyser if pfsense does not have that ability then i agree in that MFA as implemented for the GUI portion is useless.
edit: i would argue that if i already have access to your firewall via https than the firewall having 2FA or not is moot. Im already in your environment and doing mysql dumps. -
@michmoor said in MFA for pfSense GUI:
edit: i would argue that if i already have access to your firewall via https than the firewall having 2FA or not is moot. Im already in your environment and doing mysql dumps.
I agree with that part, but again - it’s besides the point.
If you want cyber insurance, or it’s company policy, you need to demonstrate your Firewall is MFA auth only unless you have physical access. -
@keyser I will say this......
Palo Alto at my site and at most sites are set up the EXACT same way.
There is a radius account that your NetOps or Sysadmisn uses to log in. There is also a local account that you can use to log in that has nothing to do with radius. Both methods are permissible. I use local account sometimes because the way Panorama (Palo Alto) works is that some features are only available if you log into the device directly rather than using switching contexts
That being said what pfsense does is in no way different from how Palo Alto operates their software. Radius and Local auth are used at the same time. Nothing wrong with this.
edit: If the cyber insurance company doesnt understand the difference between 2FA and Local Account and how the software works then you are probably best not using that company anyway....
-
@michmoor said in MFA for pfSense GUI:
edit: If the cyber insurance company doesnt understand the difference between 2FA and Local Account and how the software works then you are probably best not using that company anyway....
That's not always an option.
What's the benefit of dictating the design?
-
@condescending_dev said in MFA for pfSense GUI:
That's not always an option.
What's the benefit of dictating the design?i dont understand your question?
Whats not an option? -
@michmoor going with another another company or forgoing compliance