Trunking VLANs on interfaces II
-
Hey I went to post in a thread I had started and there's no Reply button? What's up with that?
-
It was locked… My guess would the mods got tired of the stupidity... Seems to me your just trolling now... Nobody in networking for a year, let a lone the 40 you state could be that completely clueless to how vlans work.
I do not do vlans every day all day like I use to to do back a few years when supported DC lan infrastructure for global player with 100's different customers in the DCs, etc. But have been using vlans since really there was any such thing as "vlans" And your layer 2 had to be isolated physically... Early 2k's I think it was when you could actually isolate with vlans..
Yeah I remember running thicknet as well ;)
That other thread makes really no sense.. Sure and the F would not bridge interfaces on my router to extend a layer 2 when I can just do that with click click in my switching infrastructure way more efficiently.
Where I might create a bridge is when media changes, like I have a fiber sfp that connects to some remote switch.. And my local switch does not have way to connect the fiber too. But that would really be a jury rig until I could fix my layer 2 infrastructure to do what I need it to do..
Or if for some strange reason I needed to be able to firewall X from Y that need to reside in the same layer 2 where X is connected via interface A and Y is connected via interface B... But would be just easier to break them up into their own layer 2s and put each network on its own interface.
Pfsense is a ROUTER.. its interfaces are router interfaces and would be in different layer 2's... If you need a "router" that has switch ports on it so you can have multiple connections in the same layer 2 then I would really suggest the sg-3100 which has a 4 port switch that has a uplink into the routing function.. And if need be you can always isolate even though switch ports into their own layer 2 networks via vlans.
-
No not trolling. I would like to know who locked it and why it was locked.
I do not believe that bridging a VLAN on router ports violates any RFC's. In google'n for a HowTo last week I was directed to this forum to a number of threads where others were also asking how to do it. But they were never told how to do it, they were usually told not to do it.
How are VLANs presented on multiple interfaces? Bridging I do believe. But is seems router purists do not allow that to be done if the hardware is labeled a router. (No offense intended.)
For my 3 subnets coming off the router, 2 subnets are 2 switches deep, the remaining subnet is 3 switches deep. These all are 8 or 10 port switches. This is not a mega network.
It's not a stupid network configuration. It's a network that fits my needs performance and flexibility wise and will never be utilized to it's fullest potential by any means.
Is that against the forum's rules policies or charter?
Below is my current pfSense router utilization. Bridging a VLAN onto other two network interfaces is not going to degrade performance in any way shape or form that will be noticeable.
State table size 0% (435/1625000) Show states
MBUF Usage 1% (6076/1011574)
Temperature 27.9°C
Load average 0.04, 0.08, 0.08
CPU usage 1%
Memory usage 2% of 16257 MiB
SWAP usage 0% of 3979 MiB
Disk usage: / 0% of 222GiB - ufs
/var/run 4% of 3.4MiB - ufs in RAM -
So what happened to my post in this thread that provided a link to the "How To Add and Use Cisco Switch Like VLANs in pfSense Routers" instructions I wrote up?
Censorship?
-
It was reported as and considered to be spam.
-
How is a HowTo to configure VLANs considered to be SPAM?
-
Not a link farm to promote your blog.
-
This is NOT SPAM, this is NOT a BLOG, this is not promoting anything.
This is a stand alone document showing by example how to create Tagged and Untagged VLAN Trunks on pfSense interfaces.
This is done within the scope of what pfSense allows to be configured from within its GUI.
How To Add and Use Taggged and Untagged VLANs Trunks on pfSense Router Interfaces
-
It is a blog – Says so right there..
Called Curts Blog... Dude really... All things Curt... How is that not a blog? Its listed right next to tuna casserole - really really good ;) and Power Air Fryer Oven..
This is starting to get really funny ;) Is it a not a blog kind of how a router interface is not a switch port - yet you can bridge them?? ROFL
-
It is a blog – Says so right there..
Called Curts Blog... Dude really... All things Curt... How is that not a blog? Its listed right next to tuna casserole - really really good ;) and Power Air Fryer Oven..
This is starting to get really funny ;) Is it a not a blog kind of how a router interface is not a switch port - yet you can bridge them?? ROFL
You got the old link. This link which is the above link
http://www.curtronics.com/Networking/pfSense/pfSenseTrunkedVLANs.html
Is not a blog. Take a screenshot for that link and show me the blog Dude.
-
I am going to leave that up as an example of how not to solve that problem.
ETA: Attachment reflecting how someone might accomplish the same task.

 -
This is my network as cofigured and running just fine performance wise.
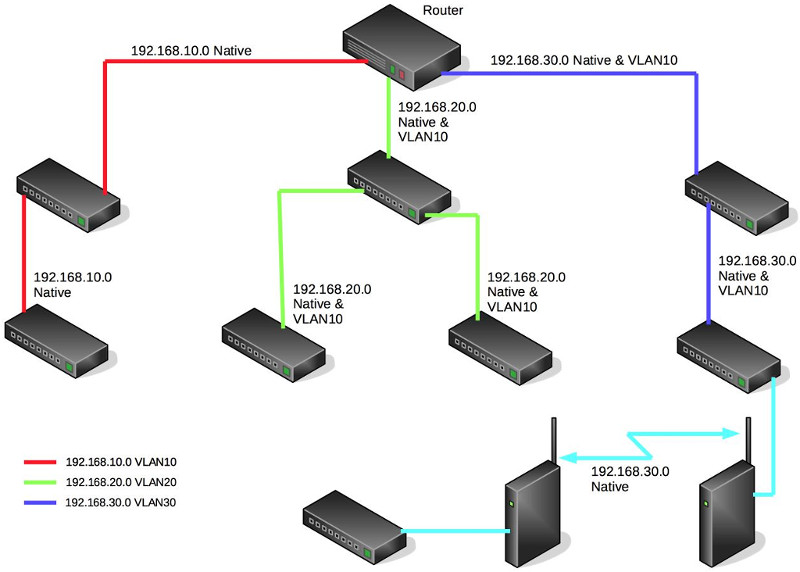
This is how you want me to configure it.
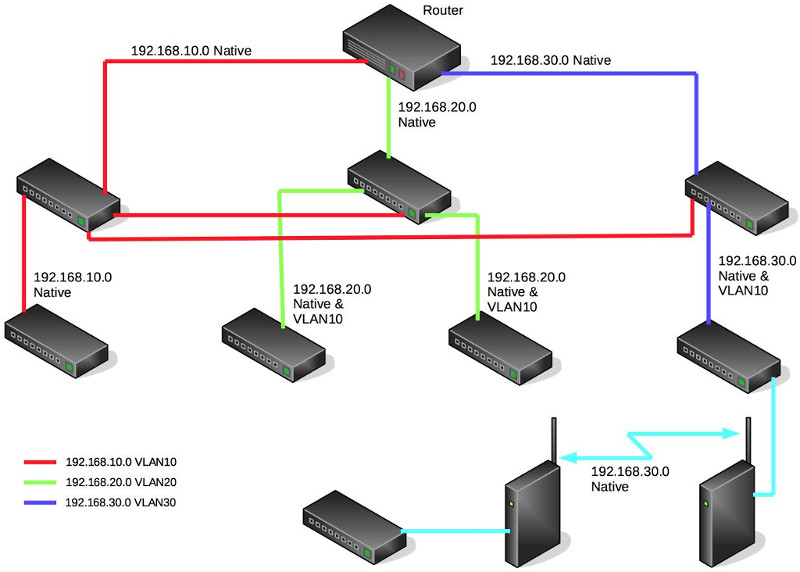
All because you don't like Bridging VLANs on a router.
-
Nope. Not even close.
You burned up two router ports instead of two switch ports and inserted a software/CPU bridge where one need not exist.
It is sad.
-
Where did I burn up two router ports? I'm using three router ports either way.
Your way I use an additional 4 switch ports.
I'm not putting 3 VLANs over 1 wire to the first switch and spreading out from there. That's what I had. That's what I don't want. That was the purpose of this whole exercise. To NOT do that. Let the router do it's job and keep the three subnets isolated.
And I have two unused router ports still with no current need for them. So I'm not burning up noth'n.
Here's current traffic graphs. I don't think that traffic peak of 1K on VLAN EM310 nor the peak of 50 bytes, yes bytes, on EM410 is going to degrade network performance.
Which is what I've been saying all along…

 -
With those traffic levels there is zero reason to even think about tagging all three VLANs to your layer 2. Just do it and remove the nonsense bridge that will in no way EVER perform as well as tagging everything on one trunk link if traffic levels ever increase in any meaningful way.
You have pigeonholed yourself into not being able to put any VLAN anywhere, too.
Adds/Moves/Changes happen. Requirements change.
But, for the third time, good luck. Glad you got it sorted and you think it works for you.
-
No I followed that link… Its still listed on your blog.. You think people not going to flow up to the parent domain?
See how simple and sleek the design Derelict posted... This way you can put any vlan anywhere in your switch environment.. Your limited to where vlan 20 and 30 can go.. So you could tie up 2 extra router ports on the same layer 2.
Because of why exactly? You don't know how to change the default vlan on your switch - you think its 10...You do understand the default vlan on a switch is ANY untagged traffic right.. Switch calls it vlan X - but just means untagged traffic outside of the switch environment.. That vlan 10 only means anything on that switch.. You can get to the management vlan be it tagged or untagged into the switch its up to you.
You can call that vlan anything you want as you connect switches together.. Or as you connect to them.. As to the layer 3 you put on it - can be anything you want.. Sure doesn't have to be the same layer 2 through out your network.
Why is it you think vlan 10 has to be same layer 2 through out your infrastructure? Its just a management IP why can it not be vlan 10, 11 and 12 on your different branches of switches on 192.168.10, 192.168.11 and 192.168.12
As I stated before if you wanted a "switch" on your router - should of gotten the sg-3100..
-
This is getting out of hand! :-\
Can we stick to constructive criticism please.
I think we can all agree that if you just need a single layer 2 available at all the switches and you don't need filtering between the segments then trunking the VLAN directly between the switches is preferable.
If however you don't have a direct connection between those switches already then bridging the VLANs in pfSense can work. It's ugly and if you find yourself doing it then you might want to think about adding a direct link instead. But it can work in a pinch. I've done it myself to avoid a major change for a 5min test.
Steve
-
stephenw10; Thank you.
johnpoz: If a person goes to the parent domain and sees that I have a blog that makes the article I linked to SPAM? Get real.
You're making assumptions again without facts in evidence. The default VLAN is not the same on all my switches.
I purposely limited where 20 and 30 can go, that is by design and is why they are isolated. 30 is high continuous traffic 24/7, 20 can be at times for hours at a time. The traffic on each is confined on each. I do not want either to adversely affect one another or 10 which has its own purpose besides being the default for the majority of the switches
Look, I came to this forum to ask how to configure pfSense to do exactly what I have done. Instead of getting help all I got was hostility and telling me how stupid this configuration is and how stupid I am and many other personal attacks. And I had to figure it out myself in the end.
In case you haven't realized it Mr. Hero Member, you were of no help in this case. Put aside your I know the best way and it's the only way and help people do what they want whether you like it or not. And if you don't like it and can't do that then for God's sake leave the peole alone!
I've told you more and showed you more then you need to know. Once again I came here for help configuring pfSense to do what I want that's all you needed to know.
IF YOU ARE NOT GOING TO HELP PLEASE JUST LEAVE ME AND THIS TOPIC ALONE!!!
This is what I want to do. This is what I did. This will work for my environment. It will have all the performance and flexibility I will ever need.