No Internet connection with non-default gateway
-
Hi, everyone!
There are 2 WANs (2 internet providers) and several VLANS in my configuration.
I have a problem with changing gateways in Firewall > Rules ( Advanced Options > Gateway). When I select "Default" (for example WAN1(default)) internet works good. When I select directly WAN1 (not "Default" option) internet does not work, but there is ping to 8:8:8:8 from client.
Perhaps someone had such a problem and knows the solution?
Could you please help?Thanks!
-
Do your clients use pfSense for DNS resolving? Forwarder or Resolver.
If yes, and you have only one firewall rule on the interface allowing anything, there is no access to pfSense when you state a gateway in that rule. So only traffic over that gw is possible.
If you want to state a gateway for upstream you have add an additional rule for the local traffic. -
No, pfSense is not used for DNS resolving. I am using separate DNS server for this.
Here are some configuration, which maybe can make situation more clear.
Last rule is only one rule in firewall for interface for which am trying to change GW.


 -
You can ping 8.8.8.8.
So try a ping to google-public-dns-a.google.com which is the same host to see if DNS works. -
Looks like DNS does not work when I have changed GW:
ping google-public-dns-a.google.com
ping: cannot resolve google-public-dns-a.google.com: Unknown hostHow to fix this with best practice?
-
So obviously your devices use a DNS service on pfSense to resolve host names, presumably the DNS resolver, cause that is activated by default in new versions.
So either allow the access to the DNS service or configure your clients to use external DNS servers.
To permit access to the pfSense DNS add firewall rules to your internal interfaces on top of the rule set which allow DNS to the interface address without specifying a gateway.
If you want to use external DNS servers on your clients, (I guess they get network settings from DHCP on pfSense) just deactivate the DNS Resolver or Forwarder, so pfSense will provide the DNS servers which you've set in general setup to DHCP clients.
-
@viragomann I tried to do what you propose. I added screenshot. It is not help for me =( Now you see how my general settings for DNS looks.
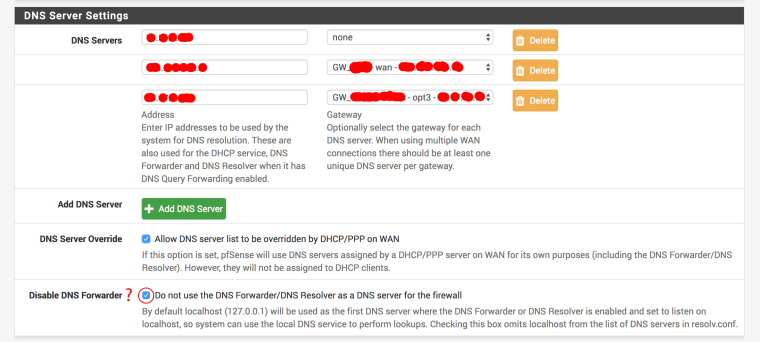
P.S. Sorry for long answer - it is because pfSense forum maintenance/update. -
@pilips_d said in No Internet connection with non-default gateway:
I tried to do what you propose.

Which suggestion? Allowing DNS access to pfSense or using external DNS? -
@viragomann said in No Internet connection with non-default gateway:
Which suggestion? Allowing DNS access to pfSense or using external DNS?
Last one, I using own DNS server for my network (first position on last screenshot) that is why i need external DNS
-
These settings don't matter the client DNS configuration.
The last option in the screenshot only prevents pfSense itself from accessing DNS Forwarder or Resolver.Again, if you have the DNS Resolver (Services > DNS Resolver) or the Forwarder (Services > DNS Forwarder ) enabled and your clients get IP configuration from pfSense DHCP server, the DHCP provides the pfsense DNS to the clients as long as you haven't stated other DNS servers in the DCHP settings.
Check the client DNS settings to assure which DNS is used.
-
What to do if I use a gateway and use pfSense as DNS resolver? What rule do I have to create to allow pfSense use its own DNS server?
-
@mrsunfire said in No Internet connection with non-default gateway:
What to do if I use a gateway and use pfSense as DNS resolver?
If its a VPN gateway you will catch DNS leaks by doing that when you also allow the resolver to go out to WAN for requests.
@mrsunfire said in No Internet connection with non-default gateway:
What rule do I have to create to allow pfSense use its own DNS server?
pfSense doesn't need a rule for that. pfSense use the resolver if activated as long as you haven't checked "Do not use the DNS Forwarder/DNS Resolver as a DNS server for the firewall" in the general settings.
For clients connected to an interface, however, you need a filter rule allowing TCP/UDP port 53 access to the interface address.
-
@viragomann clients have only local dns server for resolving.
I wonder how to configure pfSense for giving special DNS for different gateways?
As you seen in System > General Setup I have separate dns for each gateway. I think when I choosing different gateway for special VLAN clients get local dns and then clients cannot access to it via those gateways.
DNS Forwarder is disable and DNS Resolver is enable on pfSense.
-
So your clients use the DNS resolver on pfSense. I.e. you have to allow DNS access on the propriate interfaces to the pfSense interface address.
So add a pass rule to that interfaces:
protocol: TCP/UDP
destination: this firewall
dest. port: 53Put that rule to the top of the interface rule set and your clients should get DNS access.
-
After adding this rule nothing changed.
After it I disabled pfSense DNS Resolver and again nothin changed.So I do not use pfSense DNS Resolver.
Any ideas?
How to use specific DNS for each gateway? -
So let's go back to the beginning.
As you mentioned above, with the gateway stated in the firewall rule, a ping from a client to google-public-dns-a.google.com fails, but ping to 8.8.8.8 succeed.
google-public-dns-a.google.com is to be resolved to 8.8.8.8, so it is exactly the same IP, but for accessing the address by its name you need a DNS.
So if that is true, the client isn't able to access the DNS server. So please find out which DNS use used by the client to set a working rule for it.@pilips_d said in No Internet connection with non-default gateway:
After it I disabled pfSense DNS Resolver and again nothin changed.
Of course, if the client use the DNS resolver and you disable it, internet access fails, cause he cannot resolve host names.
-
@viragomann Thanks a lot!
I find the solution: for changing gateway there are have to be two rules for VLAN:- Access to local VLANS via Default gateway (x.x.x.254).
- Access outdoor where you can change gateway ( GW to internet )
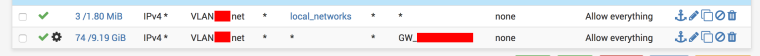
Problem was occurred because seting not default gateway not working as expecting.
When your set custom GW (not default) at some VLAN your VLAN can not access to other VLANs via it.
When set Default GW pfSense know which route to go to access other VLANS and even go outdoor for internet access.So first rule sase how to access VLANs indoor, and second sase how to go outdoor.
Thanks very much! Problem solved! Now I understand how to setup failover
