Having issues with Azure IPSec Connection
-
I managed to get my tunnel setup and a wopping 412bits of data sent over the connection but I realized that my local range was offset. My LAN is 192.168.71.0/24, and Azure was set to 192.168.70.0/24.
I jumped into the config and changed the local range from Network(192.168.70.0/24) to Lan subnet, saved and disabled / enabled the connection. I also updated the config on the Local Connection in Azure to point to my local LAN range of 192.168.71.0/24. Its now been stuck on 'Connecting' for an hour with no data.
Any ideas as to what I am doing wrong.
Jun 1 05:08:04 charon 14[CFG] vici client 16 connected
Jun 1 05:08:04 charon 14[CFG] vici client 16 registered for: list-sa
Jun 1 05:08:04 charon 05[CFG] vici client 16 requests: list-sas
Jun 1 05:08:04 charon 14[CFG] vici client 16 disconnected
Jun 1 05:08:08 charon 14[NET] <7> received packet: from 13.78.137.8[500] to 67.175.69.172[500] (620 bytes)
Jun 1 05:08:08 charon 14[ENC] <7> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) V V V V ]
Jun 1 05:08:08 charon 14[CFG] <7> looking for an ike config for 67.175.69.172...13.78.137.8
Jun 1 05:08:08 charon 14[CFG] <7> candidate: %any...%any, prio 24
Jun 1 05:08:08 charon 14[CFG] <7> candidate: 67.175.69.172...13.78.137.8, prio 3100
Jun 1 05:08:08 charon 14[CFG] <7> found matching ike config: 67.175.69.172...13.78.137.8 with prio 3100
Jun 1 05:08:08 charon 14[IKE] <7> received MS NT5 ISAKMPOAKLEY v9 vendor ID
Jun 1 05:08:08 charon 14[IKE] <7> received MS-Negotiation Discovery Capable vendor ID
Jun 1 05:08:08 charon 14[IKE] <7> received Vid-Initial-Contact vendor ID
Jun 1 05:08:08 charon 14[ENC] <7> received unknown vendor ID: 01:52:8b:bb:c0:06:96:12:18:49:ab:9a:1c:5b:2a:51:00:00:00:02
Jun 1 05:08:08 charon 14[IKE] <7> 13.78.137.8 is initiating an IKE_SA
Jun 1 05:08:08 charon 14[IKE] <7> IKE_SA (unnamed)[7] state change: CREATED => CONNECTING
Jun 1 05:08:08 charon 14[CFG] <7> selecting proposal:
Jun 1 05:08:08 charon 14[CFG] <7> no acceptable ENCRYPTION_ALGORITHM found
Jun 1 05:08:08 charon 14[CFG] <7> selecting proposal:
Jun 1 05:08:08 charon 14[CFG] <7> no acceptable ENCRYPTION_ALGORITHM found
Jun 1 05:08:08 charon 14[CFG] <7> selecting proposal:
Jun 1 05:08:08 charon 14[CFG] <7> no acceptable ENCRYPTION_ALGORITHM found
Jun 1 05:08:08 charon 14[CFG] <7> selecting proposal:
Jun 1 05:08:08 charon 14[CFG] <7> no acceptable ENCRYPTION_ALGORITHM found
Jun 1 05:08:08 charon 14[CFG] <7> selecting proposal:
Jun 1 05:08:08 charon 14[CFG] <7> no acceptable ENCRYPTION_ALGORITHM found
Jun 1 05:08:08 charon 14[CFG] <7> selecting proposal:
Jun 1 05:08:08 charon 14[CFG] <7> no acceptable ENCRYPTION_ALGORITHM found
Jun 1 05:08:08 charon 14[CFG] <7> received proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:3DES_CBC/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024
Jun 1 05:08:08 charon 14[CFG] <7> configured proposals: IKE:AES_GCM_16_256/PRF_HMAC_SHA1/MODP_1024
Jun 1 05:08:08 charon 14[IKE] <7> received proposals inacceptable
Jun 1 05:08:08 charon 14[ENC] <7> generating IKE_SA_INIT response 0 [ N(NO_PROP) ]
Jun 1 05:08:08 charon 14[NET] <7> sending packet: from 67.175.69.172[500] to 13.78.137.8[500] (36 bytes)
Jun 1 05:08:08 charon 14[IKE] <7> IKE_SA (unnamed)[7] state change: CONNECTING => DESTROYING -
I just posed about an issue with ipsec not updating... ssh to your pfsense box and see if /var/etc/ipsec/ipsec.conf is updating. I saw the same messages in our logs when the end point was trying to connect to our pfsense box.
You may be having the same issue.
-
@livestrong2109 said in Having issues with Azure IPSec Connection:
Jun 1 05:08:08 charon 14[CFG] <7> received proposals:
 The other side
The other side
IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024,
IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024,
IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024,
IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024,
IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024,
IKE:3DES_CBC/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024
Jun 1 05:08:08 charon 14[CFG] <7> configured proposals: Your side
Your side
IKE:AES_GCM_16_256/PRF_HMAC_SHA1/MODP_1024
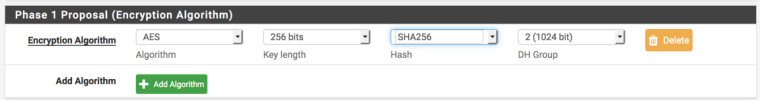
Jun 1 05:08:08 charon 14[IKE] <7> received proposals inacceptableYou are forcing AES GCM in the Phase 1 and the other side wants AES CBC (or 3DES).
Based on what the other side is presenting I would probably select AES 256 and SHA256.
Jun 1 05:08:08 charon 14[CFG] <7> no acceptable ENCRYPTION_ALGORITHM found
Jun 1 05:08:08 charon 14[CFG] <7> selecting proposal:
Jun 1 05:08:08 charon 14[CFG] <7> no acceptable ENCRYPTION_ALGORITHM found
Jun 1 05:08:08 charon 14[CFG] <7> selecting proposal:
Jun 1 05:08:08 charon 14[CFG] <7> no acceptable ENCRYPTION_ALGORITHM found
Jun 1 05:08:08 charon 14[CFG] <7> selecting proposal:
Jun 1 05:08:08 charon 14[CFG] <7> no acceptable ENCRYPTION_ALGORITHM found
Jun 1 05:08:08 charon 14[CFG] <7> selecting proposal:
Jun 1 05:08:08 charon 14[CFG] <7> no acceptable ENCRYPTION_ALGORITHM found
Jun 1 05:08:08 charon 14[CFG] <7> selecting proposal:
Jun 1 05:08:08 charon 14[CFG] <7> no acceptable ENCRYPTION_ALGORITHM foundAll of that is probably Azure attempting PFS groups you don't have defined. Probably more secure than PFS group 2.