DNS Lookup Help
-
Hello
I needed some help building my home network and posted in general section here, https://forum.netgate.com/user/rakibNow I have configured everything from below links more or less all copy paste basis
https://nguvu.org/pfsense/pfsense-baseline-setup/
https://nguvu.org/pfsense/pfsense-multi-vpn-wan/
https://nguvu.org/pfsense/pfsense-inbound_vpn/
https://nguvu.org/pfsense/pfsense-router-on-a-stick-with-netgear-gs108/Got all working as expected except the DNS lookup issues in all interfaces. I have gone through the guides multiple times but did not find any deviation from the guide. Yet can't get the result as displayed at the end of the guide: what I get is as follow:
Verify local lookups
We use nslookup to resolve an address:Shell Output - nslookup pfsense.org
Server: 208.67.222.222
Address: 208.67.222.222#53Non-authoritative answer:
Name: pfsense.org
Address: 208.123.73.69
Name: pfsense.org
Address: 2610:160:11:11:69Verify DNS lookups to non local DNS servers are blocked.
Here I use the dig command and force the DNS query to use Googles DNS server (8.8.8.8). This should and does fail but it does notShell Output - dig @8.8.8.8 pfsense.prg
; <<>> DiG 9.11.2-P1 <<>> @8.8.8.8 pfsense.prg
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 27948
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;pfsense.prg. IN A;; AUTHORITY SECTION:
. 86396 IN SOA a.root-servers.net. nstld.verisign-grs.com. 2018050200 1800 900 604800 86400;; Query time: 196 msec
;; SERVER: 8.8.8.8#53(8.8.8.8)
;; WHEN: Wed May 02 11:28:55 +03 2018
;; MSG SIZE rcvd: 115Verify local name resolution is working correctly.
I use nslookup to lookup my pfsense gateway by its hostname and verify the address is returned correctly.Shell Output - nslookup pfsense
Server: 208.67.222.222
Address: 208.67.222.222#53** server can't find pfsense: NXDOMAIN
Verify reverse lookups
Verify you can resolve a hostname from an IP addressShell Output - nslookup 192.168.1.1
** server can't find 1.1.168.192.in-addr.arpaAny remarks anyone?
-
Why would you think google dns would resolve pfsense.prg?
Why would you think unbound or dnsmasq running on pfsense would resolve pfsense - that is not fqdn.
why would you think that opendns would be able to resolve a PTR for 192.168.1.1 ?
-
@johnpoz
I have read you a lot in this forum and extremely happy to read you here. Actually I know nothing on DNS. All what I am trying to get is the same result of the blog as I copied everything from there. Blog DNS results are as follow:$ nslookup pfsense.org
Server: 192.168.20.1
Address: 192.168.20.1#53Non-authoritative answer:
Name: pfsense.org
Address: 208.123.73.69$ dig @8.8.8.8 pfsense.org
; <<>> DiG 9.8.3-P1 <<>> @8.8.8.8 pfsense.org
; (1 server found)
;; global options: +cmd
;; connection timed out; no servers could be reached$ nslookup pfsense
Server: 192.168.20.1
Address: 192.168.20.1#53Name: pfsense.local.lan
Address: 192.168.1.1$ nslookup 192.168.1.1
Server: 192.168.20.1
Address: 192.168.20.1#531.1.168.192.in-addr.arpa name = pfsense.local.lan.
$ dig nothere.local.lan
; <<>> DiG 9.8.3-P1 <<>> nothere.local.lan
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 18955
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 0;; QUESTION SECTION:
;nothere.local.lan. IN A;; AUTHORITY SECTION:
local.lan. 10800 IN SOA pfsense.local.lan. root.local.lan. 1 3600 1200 604800 10800;; Query time: 4 msec
;; SERVER: 192.168.20.1#53(192.168.20.1)
;; WHEN: Sun Aug 27 10:22:30 2017
;; MSG SIZE rcvd: 84 -
@rakib said in DNS Lookup Help:
I know nothing on DNS
Then I would suggest you do some reading/research on what it is, how it works the difference between a resolver and a forwarder before you attempt any sort of anything with it.
Your clients will point to pfsense out of the box with pfsense running as dhcp. Pfsense will then resolve what you ask for and return it to your clients. Anything more than that you need to understand the basics of what it is and how it works before you go mucking around with it..
Back to your specific problems.. You asked googldns 8.8.8.8 for pfsense.prg not .org - there is no such tld as .prg in the public dns so no pfsense.prg would not get an answer.
asking for just pfsense is not a fully qualified domain name... you would need to ask for pfsense.something.tld where something.tld is what you setup pfsense domain as. etc..
And again asking opendns 208.67.222.222 is not going to be able to return a reverse record PTR for some rfc1918 address 192.168.x.x those are only used on local network. Ask pfsense for the PTR..
-
@johnpoz
Hi,
Sorry for the delay. I have gone through some reading to understand both. Seems it would be much easier to take issues one-by-one as I believe rest of the issues are linked to this at large. I have attached few relevant screenshot for your review.From diagnostic > command prompt > execute shell command (is it the right place?)
I execute: nslookup pfsense.org.
Although I did not check "DNS query forward" in the unbound, and no DNS mentioned in the interface DHCP server, I get :
Server: Whatever DNS address of the general setup
Address: Whatever DNS address of the general setup#53
Here, I want to see my interface IP as server and address, NOT the DNS address of the general setup. How can I achieve itIPV6 is disabled everywhere, yet I get IPV6 resolution. How can I make it disappear?
Non-authoritative answer:
Name: pfsense.org
Address: 208.123.73.69
Name: pfsense.org
Address: 2610:160:11:11::69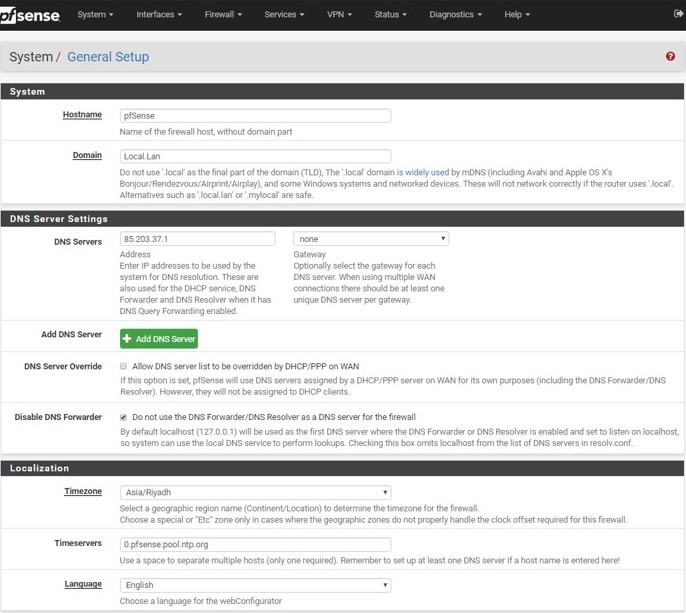
-
@rakib said in DNS Lookup Help:
Name: pfsense.org
Address: 2610:160:11:11::69That is just the AAAA record for pfsense.org.. That has nothing to do with your client or your network supporting or using IPv6..
Don't ask for AAAA if you don't want to see it when doing the query, just ask for the A record.. But most OS dns client will ask for both all the time... For example if you put www.domain.tld in your browser the dns query that your OS generates will ask for the AAAA record as well as the A record.. This is not an issue that you should be concerned with.
As to not putting in anything in pfsense - yeah out of the box it resolves... Did you look up what the difference is between a resolver and a forwarder.. If so you will know that a resolver doesn't need anything.. It has the roots and will walk down the tree from there to find the authoritative ns for whatever it is your asking for.
Here, I want to see my interface IP as server and address, NOT the DNS address of the general setup.
Why are you putting anything in general setup, if your going to use pfsense as resolver then again it doesn't need anything in general setup, nor does it need anything from dhcp.. Make sure your set to not override from dhcp if your dhcp of pfsense wan is dhcp..
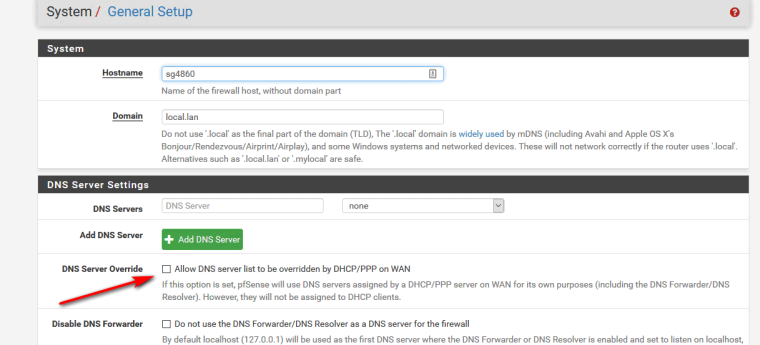
Make sure that is unchecked..
-
@johnpoz
Hi,
I understood about AAAA thing.
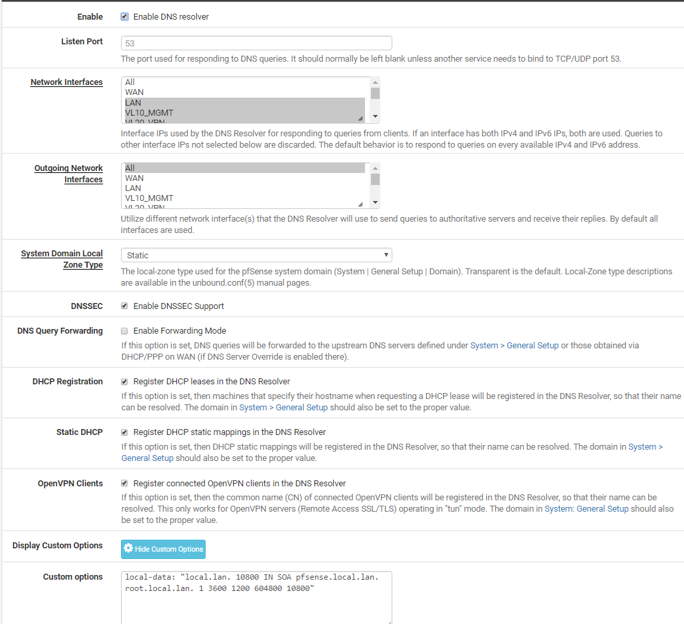
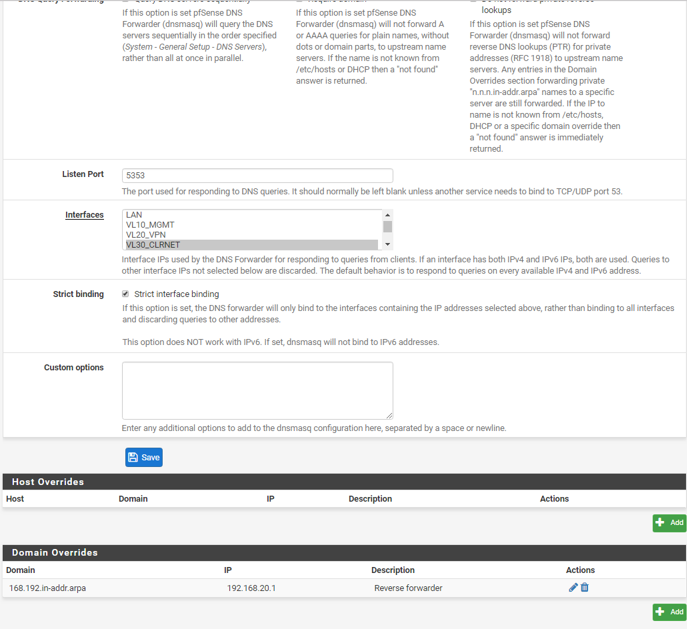
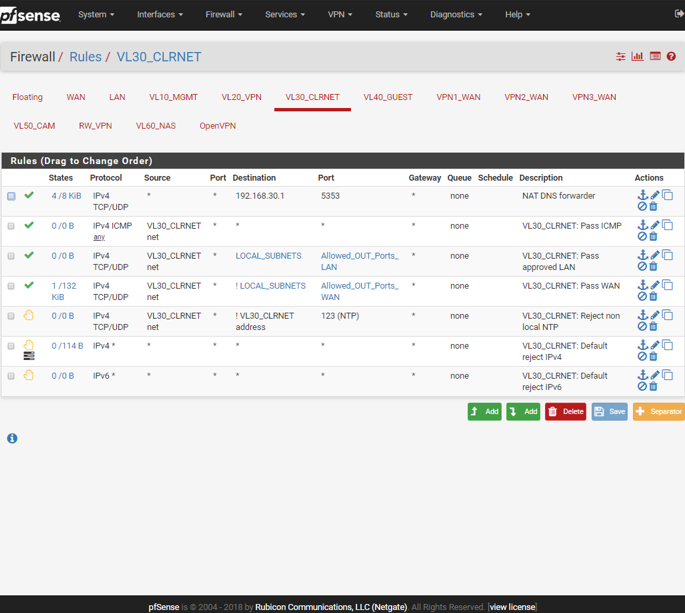
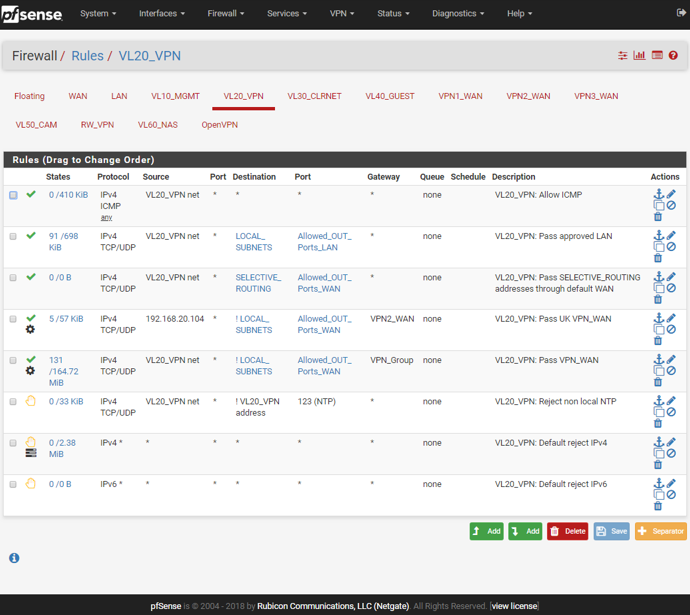
I'm using general setup DNS only for VLAN 30 interface; I need that. This is served by DNS forwarder as you can see from 3rd screen shot.
VLAN 20 interface is only for VPN users and supposed to use resolver and VPN DNS only.
I did not check "DNS server override". I checked the "Disable DNS forwarder" in general setup. -
That disables pfsense from using itself.. Did you not read what it says?
If you want your clients to use some other dns, then hand it out to them in dhcp.. Don't expect pfsense to redirect and capture traffic and then forward it..
To be honest I have no idea what sort of nonsense your trying to do without basic understanding of dns. Why don't you start simple and get more complex..
-
@johnpoz said in DNS Lookup Help:
To be honest I have no idea what sort of nonsense your trying to do without basic understanding of dns. Why don’t you start simple and get more complex…
Nonsense I am trying to achieve is as follow:
VL20_VPN: will use Resolver for local and non-local lookups. External DNS servers should be blocked.
VL30_CLRNET: will use Forwarder for non-local and DNS Resolver for local. External DNS servers should be blocked.
VL40_GUEST: will uses ISP DNS resolver for non-local. No local lookups should be possible.Help me achieve it.
-
@rakib said in DNS Lookup Help:
VL20_VPN: will use Resolver for local and non-local lookups. External DNS servers should be blocked.
That is how pfsense is out of the box.. Nothing to do but a rule on vl20 that blocks udp/tcp 53. So is your resolver only going to use vpn connect? Why is the this network _vpn? Is going out some vpn service. I would think your going to be all tinfoil hatty about dns leaks if using the resolver. Why should external be blocked? If they are going through the vpn?
VL30_CLRNET: will use Forwarder (to where) for non-local and DNS Resolver for local. External DNS servers should be blocked.
Why if your just going to forward them to somewhere what does it matter if client asks on its own for dns to some public dns?
What do you think that accomplishes?? Why do you think you need to use the forwarder and resolver in pfsense? You do understand with a simple unbound view you can have client X forward to somewhere, while Client Y lets pfsense resolve for it, etc.VL40_GUEST: will uses ISP DNS resolver for non-local. No local lookups should be possible.
You mean just ask your ISP dns? You can not know if its a resolver, it might just forward to somewhere else.Simple firewall rule block dns to pfsense IP blocks them from asking pfsense for anything local
Why don't you explain what you think all of this nonsense gets you - then be happy to walk you through how to set it up.
-
@johnpoz
All local devices is set to use the pfSense router as their sole DNS server. Cached or local names found in the DNS Resolver will be returned to the client and unknown lookups will be forwarded to either Specific DNS or the root nodes via the VPN tunnel. Results returned will be cached for future reference.To reduce any leaks, I lock down the Resolver to the VPN_WAN interface only. If the VPN connection goes down, DNS lookups wont be possible and this is why I provide the guest and clrnet networks as a backup on the rare occasions VPN goes down. Nevertheless, I have setup multiple simultaneous connections to VPN provider which provides further redundancy.
I believe this is a good compromise between providing the required functionality and security. I’ve spent time verifying there are no leaks and found no leak so far.
VL40_GUEST is not added to the interfaces selection as devices on that subnet do not utilise the DNS Resolver or Forwarder to resolve names but instead directly access the DNS servers as awarded from the DHCP server.
If I have passed the exam and you think now qualify to get some help, please be kind enough to do so.
-
Your vl30 setup is not going to work... So you want to use the resolver for your local, but since your vpn is down it can not resolve so you want it to forward.
Just have this network use the forwarder, the forwarder can serve up local as well.
All of it buys you what exactly.. Hiding your dns from your isp? Why don't you just forward anything that is not local via dnscrypt to say quad 9?
And no you have not passed any sort of test because you have not explained what all this nonsense gets you.. Hiding your dns queries from your ISP? If you resolve they would have to sniff all your traffic to find out what your looking for. But your ok with leaking your queries to somewhere if the VPN Is down..
If your so worried about privacy and your vpn is down - then you shouldn't be be looking up anything or going anywhere.. So your tinfoil hat is tight enough to say hide my dns from my isp... Unless vpn is not working - then screw all privacy just let look up where I want to go and I will go there without the vpn..
-
@johnpoz said in DNS Lookup Help:
Your vl30 setup is not going to work… So you want to use the resolver for your local, but since your vpn is down it can not resolve so you want it to forward
When my all the VPNs are down VL20 network is down but VL30 network is working actually.
@johnpoz said in DNS Lookup Help:
Hiding your dns from your isp? Why don’t you just forward anything that is not local via dnscrypt to say quad 9?
Hiding your dns queries from your ISP? If you resolve they would have to sniff all your traffic to find out what your looking for. But your ok with leaking your queries to somewhere if the VPN Is down…I would love to use quad 9 but this option for VL30 is not for me as I need to use specific DNS for streaming eliminating georestriction. Yes, privacy is compromised here for the benefit of enough internet speed for streaming services.
So now can we get to the point which take us to square 1?
@rakib said in DNS Lookup Help:
Although I did not check “DNS query forward” in the unbound, and no DNS mentioned in the interface DHCP server, I get :
Server: Whatever DNS address of the general setup
Address: Whatever DNS address of the general setup#53
Here, I want to see my interface IP as server and address, NOT the DNS address of the general setup. How can I achieve it?