Matching traffic on TOS only
-
Hi all,
I'm looking at the feasibility of replacing physical Cisco routers (and CSR1000v) with pfsense. So far I can replicate most functionality, but I have a question regarding matching firewall rules using DSCP.
In Cisco land, I can do policy based routing where the match criteria is the TOS bit only (max reliability or max throughput). In other words, I only look at the TOS portion of the DSCP field. I do not need to match all bits, only the TOS ones. I can then set my net hop on this basis.
In pfsense, I can create a firewall rule that matches on the same TOS bits (max reliability or max throughput) and then sets my outbound gateway accordingly.
My question is will pfsense only look at the TOS bits for this match critera or will it evaluate the entire DSCP bits for a match? I will have multiple DSCP values, but path determination is on the basis of the TOS field only.
From the documentation:(https://www.netgate.com/docs/pfsense/trafficshaper/diffserv.html)
"pfSense only matches exact values. All six bit in the DSCP field must match."Will pfsense match DSCP 2, DSCP 26 and DSCP 34 as having max throughput set?
or
Will it only match DSCP 2 as it is an explicit match?Thanks in advance.
Kevin
<edit>
Thinking more about it, I could just create multiple rules for all DSCP values containing the TOS value I want, but this will not scale well across multiple devices/sites
</edit> -
Probably a tad offtopic, but you HAVE to remember that pfSense only classifies the traffic based on the FIRST packet of the flow it sees. So if you have a device sending to another device, but some traffic will be EF and some will be BE, but it's all the same sessions traffic, then whatever packet (a BE or an EF) packet creates the state will be the traffic priority that ALL Traffic uses.
There's a few tricks to work around this, but I post this cause it tripped me up for a long time (SSH was starting out using BE markings and only sending my markings later after the sessions was negotiated. I thought my rules weren't working, but they were...) -
Thanks for that, it is not off topic at all. I had forgotten about that, but I think I can disable state for these rules to get per packet matching instead of per flow:
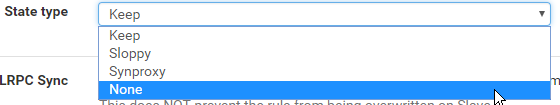
I appreciate this will increase the load on the device, but these are mostly low-bandwidth sites with over provisioned hardware. I'm using pfsense primarily as a router and not a firewall.
The markings will indeed change within a flow as there are WAN opt devices on the LAN side setting the TOS bits. They sometimes can only make a decision after they see a TCP three way handshake or in the case of some protocols, 7 or 8 packets. The WAN opt boxes then set the TOS bits accordingly so that the routers (Cisco, Juniper or pfsense) can correctly set the next hop with a routing policy looking for those bits.
-
You can disable state tracking to get that behavior, but you will need to craft rules in every direction with state disabled on every interface to make that work, for example:
- In LAN
- Out WAN (floating rule)
- Return traffic back in WAN -- opposite src/dst addresses and ports, no state so it doesn't automatically get let back in
- Return traffic back out LAN (floating rule)
-
@jimp
@mupppetThank you.
After more research, I don't think this will be viable to replace the routers I am currently using as I need to be able to set TOS bits on certain traffic also.
Thank you for the assistance in any case.