2 subnets on 1 lan interface
-
Hi
Fairly new to psSense and my netgate SG-4860 and can't figure out how to setup following:
We get 2 /24 from our ISP x.x.233.0/24 and x.x.234.0/24 (which can't be setup as a /23 in pfSense) which I want to setup on the LAN side, WAN is a routed public /28 (between our wan port and ISP router). I can get it working when setting up the WAN with the /28 and the LAN with either of the /24 but not with both (and I can't get a /23 at the moment so am stick with 2 x /24)
LAN1: x.x.233.0/24 GW x.x.233.1
LAN2: x.x.234.0/24 GW x.x.234.1
How do it set this up so both /24 are on my LAN port and route to the WAN?
many thanks
Jan -
@jwr17 said in 2 subnets on 1 lan interface:
How do it set this up so both /24 are on my LAN port and route to the WAN?

Using VIP perhaps
https://www.netgate.com/docs/pfsense/interfaces/mixing-public-and-private-ip-addresses-on-an-interface.html
Instead of "mixing" (Private/ Public) you will have "all Public IP addresses"
-
How do it set this up so both /24 are on my LAN port and route to the WAN?
Short answer is, you probably don't - or at least shouldn't.
WAN is a routed public /28
The WAN interface is probably not routed it is probably the interface subnet. You need to get with your ISP and determine what, exactly is the interface subnet and what, exactly the two /24 networks are routed to.
You would likely then create an inside interface for each /24 and disable outbound NAT for them.
-
@derelict you are right, the /28 is the interface subnet. I added in my test environment the secondary /24 to OPT1 and disabled all NAT and created some allow all from all rules between LAN and OPT1 it seems to work (I don’t want to block any ports between my inside interfaces).
Now the second challenge came up: my ISP gives me 2 VRRP uplinks for redundancy, before we just had them connected to our core switch and from there our servers were connected. Now, I have only 1 WAN interface setup and it seems I can’t setup a second WAN for uplink 2 as it has the same gateway ons ISP side. What would be the best option? Terminate the 2 uplinks in a switch and then 1 cable to WAN port (adding another point of failure, the switch) or using OPT2 but how to setup the gayeway then?
Sorry for so many questions and thanks for any help!
Jan -
Yeah.
That's pretty much a bone-headed way for your ISP to do it. Maybe you are misunderstanding.
You are likely going to have to provide more details as to exactly what the ISP says they are giving you. You know things like addresses, netmasks, and gateways.
-
This is what they wrote
We configured x.x.250.0/29 as the subnet between your side and our router and we will route both /24 over this subnet.
Our virtual addres (your gateway is) x.x.250.1 and we will use x.x.250.5 and x.x.250.6 for VRRP. -The .2 .3 and .4 are free for you to use.I assigned .2 as the WAN IP and the .1 as default GW on the WAN.
Thanks!
Jan -
@jwr17 said in 2 subnets on 1 lan interface:
(which can’t be setup as a /23 in pfSense)
You wouldn't be able to set them up anywhere as a /23 because they are not at the /23 break... .232/23 and 234/23 is where you could have /23's
If you put in x.x.233/23 then you rrange would be 232.0 - 233.255
If you want them in the same L2 then you could use 232/22 and not use the first and 2nd /24, knowing that you would never be able to get to a host out using those IPs.
-
Our virtual address (your gateway is) x.x.250.1 and we will use x.x.250.5 and x.x.250.6 for VRRP.
That just means you use x.x.250.1 as your default gateway but you cannot use .5 or .6 because they are using those for the physical interface addresses of their VRRP nodes. The VRRP address (x.x.250.1) will swing over to the other router if they experience a failure, perform maintenance, etc. You don't have to do anything like two connections.
The .2 .3 and .4 are free for you to use
Set your WAN address to one of those with .1 as the gateway. Nothing special there. You, too have enough addresses to do High-Availability if you like.
They should have specified which of the addresses (.2 .3 and .4) they are routing the /24s to. That would be the address you would want to use as your CARP VIP if you did HA. Based on what you have seen they are probably routing the addresses to .2.
-
This sounds a lot like what Switch in Vegas provisions.
-
@derelict yes they route to .2 but give me two cables in my rack... so bit confusing how to connect them as i have only 1 WAN port setup.
Guess easiest will be just throwing a switch in between? -
The two cables are probably for two WAN interfaces to their switch stack if you were to set up an HA pair. If you are not doing that you can connect one or the other and ignore the second I would think.
They might also be able to set up something like LACP to your outside switch(es) over those if you wanted them to. Not sure.
None of this is really pfSense-specific.
-
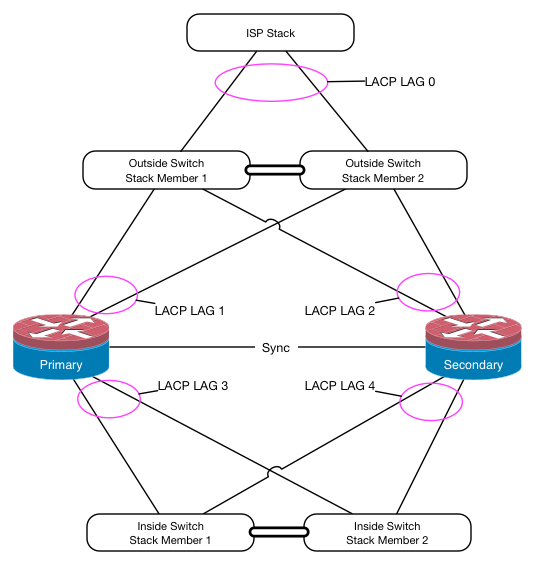
The two connections are probably those depicted there as LACP LAG 0.
Depending on how they have it provisioned you could probably just eliminate the outside switch stack and LACP LAGs 1 and 2 and run one connection to Primary WAN and one to Secondary WAN. You would be putting more responsibility for layer 2 redundancy in their hands in that case.
-
That makes it much clearer and is indeed how they have set this ip.
Eliminating the outside switches (and currently having 1 Netgate/pFSense box, what would be the secondary WAN port config? Can I just give it .3 as WAN2 address and point to the same .1 gateway as on WAN1 (which is at .2)
The ISP is not really informative and the rack is 800km away.. plan to go onsite to install in July but want to be well prepared config-wise.
Again, your help is much appreciated! -
It would be your standard HA setup using .2 as CARP and .3 and .4 as the node interface addresses.
https://www.netgate.com/docs/pfsense/highavailability/
-
With above info from you I contacted again the ISP and it's finally clear... Had indeed to install LACP ( LAGG ) on OPT3 and OPT4 and all is working now in my test environment.
They do the VRRP on their side and just bring 2 cables to our rack (aggegration and redundancy in case of cable problem). So problem solved thanks to your help!
Highly appreciated @Derelict !
Thanks!
Jan