Routing between interfaces..
-
Hello,
Hoping someone can point me in the right direction.Have 2x pfSense boxes - and OpenVPN tunnel between them. On the server side I define what subnets to bring over the tunnel, and then on the remote side I define the same subnets. On the remote side, no matter what VLAN / Interface / subnet I am on, I am able to (firewall rules permitting) access resources from that tunnel. pfSense "Routes" that traffic as needed.
I also have an IPSec tunnel connected. On the server side I define what subnets to bring over the tunnel, and then on the remote side I define the same subnets. When a PC on the remote side is on one of those subnets - traffic flows no issue. But if they are on a different subnet, traffic does not flow.
How can I get pfSense to "route" that traffic over the tunnel?
-
Please be more specific. I cannot picture what you are talking about.
A diagram would be great. Complete with subnets, addresses, gateway addresses, etc.
-
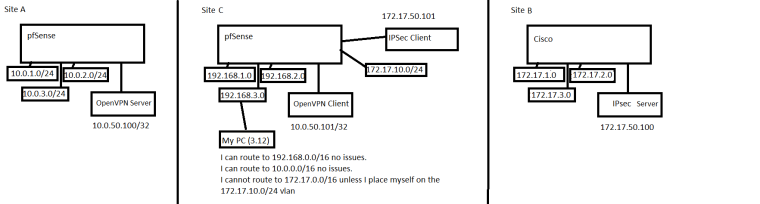
See attached. Let me know if that helps or more info is needed.
-
Great. Please give a complete example of something that is not working.
When host address X tries to connect to host address Y on port X this happens.
-
Hi,
Sorry - I missed the notification this was responded to - didn't mean to ignore you for 5 days.
Thank you again for your help so far.When I try to access 172.17.1.1 from 172.17.10.1 it works.
When I try to access 172.17.1.1 from 192.168.3.12 it does not work.
When I try to access 10.0.1.1 from 192.168.3.12 it work.Let me know if you need further information.
Thanks -
Sounds like you need a phase 2 on the IPsec tunnel for traffic between 172.17.1.0/24 and 192.168.3.0/24
-
In a normal site to site VPN tunnel you have to specify what traffic you want to encrypt over that tunnel. Both VPN endpoints have to agree on that "interesting" traffic before packets will be accepted. The VPN endpoints also need to know (via routing normally) that that traffic needs to be routed via the tunnels. That how it would work in a typical Cisco environment - I would assume pfsense would be similar. Phase 2 is the part where the actual traffic gets encrypted....
-
I forgot to follow up on this.
I can't make changes on the Cisco side, so I couldn't make a separate P2 from 172.17.1.0/24 to 192.168.3.0/24. I needed to nat traffic so that 192.168.3.0/24 routes through 172.17.10.0/24 (since the P2 already exists from that subnet)
I found this that seemed be what I was wanting to do.
https://serverfault.com/questions/703112/routing-between-pfsense-subnets-and-ipsec-vpnI ended up making a second P2 only on the pfSense side with the local network being 192.168.3.0/24 and the NAT network being 172.17.10.0/24 and the remote network being 72.17.1.0/24.
Before:
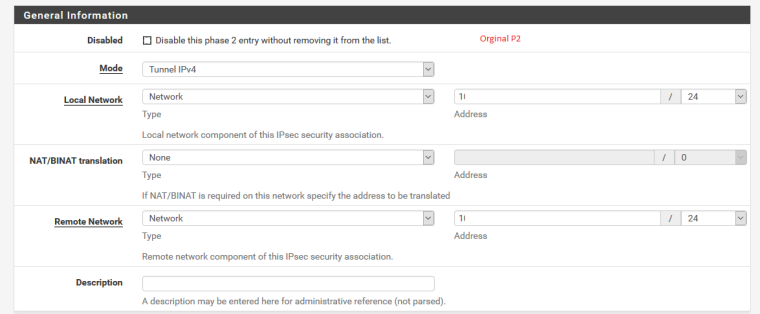
After:
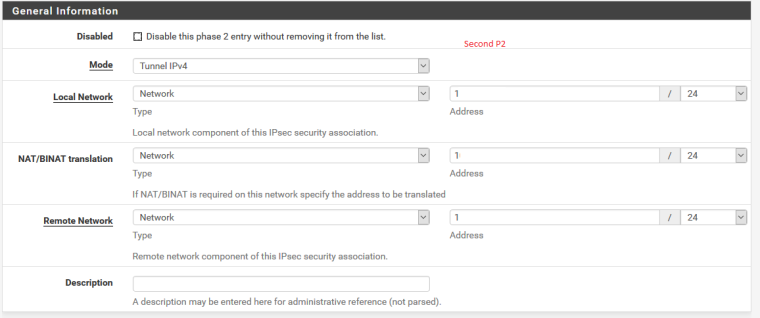
It seems to be working correctly now, I can route as desired, but I am experiencing a couple of visual bugs in the UI of pfSense after doing so. I''ll make a new thread for that.
-
That looks correct. You can't route over policy based IPSec. But if you NAT the subnets you can make the traffic match an existing policy.
Steve