Static route via VPN interface binds to lo0 when created from web page, but binds to tun1 when created from command line.
-
I have an OpenVPN client on pfSense server up and running. I have assigned a custom interface OPT1 and have created a gateway via that interface. When I am trying to create static route using pfSense web interface via this gateway I am getting a route binded to wrong IP address and wrong interface lo0 and of course it doesn't work.
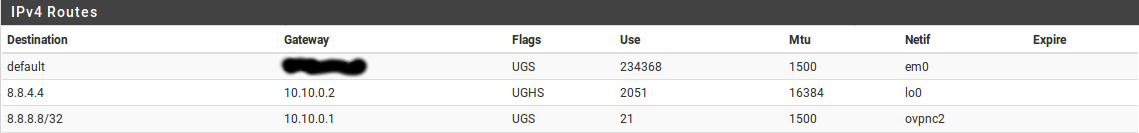
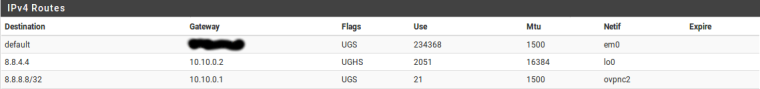
but then I remove this static route from web interface and create right route but via command linesudo route add -net 8.8.8.8/32 10.10.0.1it works fine
What I am doing wrong ? -
Don't add static routes for OpenVPN connections on the routing page, use OpenVPN's own push route method to tell the client to add a route when the connection is initialized. Put this in the Advanced Configuration/Custom options box of your OpenVPN server.
push "route 8.8.8.8 255.255.255.255"If the server is not under your control you can add the custom option to the OpenVPN client configuration on your pfSense, in that case you'd use just (again Advanced Configuration/Custom options):
route 8.8.8.8 255.255.255.255 -
@kpa thanks for replying
When I addroute 8.8.8.8 255.255.255.255on client Custom config there is nothing happens at all.
When I addpush "route 8.8.8.8 255.255.255.255"to server config there is an error in client log
Options error: option 'route' cannot be used in this context ([PUSH-OPTIONS]) -
You need to disconnect/reconnect on the client for the options to take effect. After doing so take a look at the routing table to verify that the route is there.
The error on the server side suggests that this is a peer-to-peer setup with a static key, is that right? If so the push options can't be used, you'll have to use route statements in custom options on both sides.
-
@kpa Of course I made reconnect every time when config on server or client was changed.
Yes it's peer to peer setup with static key.
I have added same stringroute 8.8.8.8 255.255.255.255to server.conf and client Custom options - no effect.
-
Do you have 8.8.8.8 defined anywhere else such as in System > General?
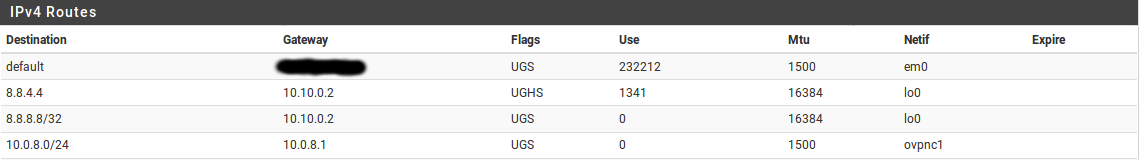
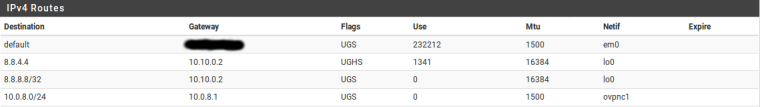
What routes exist for 8.8.8.8 in Diagnostics > Routes?
Are there any ifconfig errors logged in the OpenVPN logs?
-
It would help if you posted the connection log from the client here.
-
@derelict Generally I am trying to add route to different (not 8.8.8.8) IP address and it is NOT defined in System>General for sure and there is no routes for it for sure. There is no errors in both server and client logs.
-
@kpa Here is parts of my configs:
Client
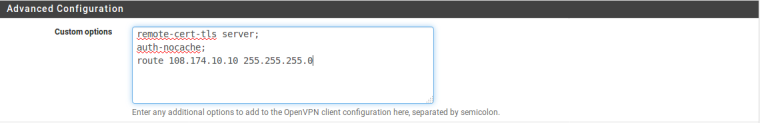
Server ccd
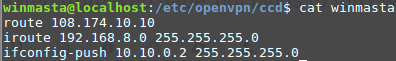
Server server.conf
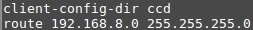
Server log before client connected
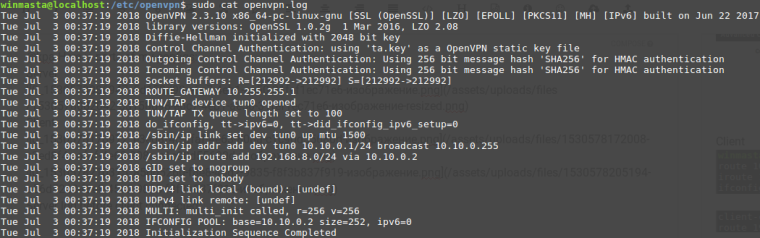
Server log after client connected

Client logJul 3 07:45:33 openvpn 60153 Initialization Sequence Completed Jul 3 07:45:33 openvpn 60153 /usr/local/sbin/ovpn-linkup ovpnc2 1500 1570 10.10.0.2 255.255.255.0 init Jul 3 07:45:33 openvpn 60153 /sbin/route add -net 10.10.0.0 10.10.0.1 255.255.255.0 Jul 3 07:45:33 openvpn 60153 /sbin/ifconfig ovpnc2 10.10.0.2 10.10.0.1 mtu 1500 netmask 255.255.255.0 up Jul 3 07:45:33 openvpn 60153 do_ifconfig, tt->did_ifconfig_ipv6_setup=0 Jul 3 07:45:33 openvpn 60153 TUN/TAP device /dev/tun2 opened Jul 3 07:45:33 openvpn 60153 TUN/TAP device ovpnc2 exists previously, keep at program end Jul 3 07:45:33 openvpn 60153 ROUTE_GATEWAY CLIENT_EX_IP/255.255.255.192 IFACE=em0 HWADDR=00:0c:29:6c:7e:79 Jul 3 07:45:33 openvpn 60153 Incoming Data Channel: Using 256 bit message hash 'SHA256' for HMAC authentication Jul 3 07:45:33 openvpn 60153 Incoming Data Channel: Cipher 'AES-128-CBC' initialized with 128 bit key Jul 3 07:45:33 openvpn 60153 Outgoing Data Channel: Using 256 bit message hash 'SHA256' for HMAC authentication Jul 3 07:45:33 openvpn 60153 Outgoing Data Channel: Cipher 'AES-128-CBC' initialized with 128 bit key Jul 3 07:45:33 openvpn 60153 OPTIONS IMPORT: route-related options modified Jul 3 07:45:33 openvpn 60153 OPTIONS IMPORT: --ifconfig/up options modified Jul 3 07:45:33 openvpn 60153 OPTIONS IMPORT: timers and/or timeouts modified Jul 3 07:45:33 openvpn 60153 PUSH: Received control message: 'PUSH_REPLY,route-gateway 10.10.0.1,topology subnet,ping 10,ping-restart 120,ifconfig 10.10.0.2 255.255.255.0' Jul 3 07:45:33 openvpn 60153 SENT CONTROL [server]: 'PUSH_REQUEST' (status=1) Jul 3 07:45:32 openvpn 60153 [server] Peer Connection Initiated with [AF_INET]VPN_SERVER_EXT_IP:PORT Jul 3 07:45:32 openvpn 60153 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 DHE-RSA-AES256-GCM-SHA384, 2048 bit RSA Jul 3 07:45:32 openvpn 60153 VERIFY OK: depth=0, C=RU, ST=TO, L=Tomsk, O=Kireva, OU=IT_dept, CN=server, name=oneandoneserver, emailAddress=winmasta@kireva.com Jul 3 07:45:32 openvpn 60153 VERIFY EKU OK Jul 3 07:45:32 openvpn 60153 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication Jul 3 07:45:32 openvpn 60153 Validating certificate extended key usage Jul 3 07:45:32 openvpn 60153 VERIFY KU OK Jul 3 07:45:32 openvpn 60153 VERIFY OK: depth=1, C=RU, ST=TO, L=Tomsk, O=Kireva, OU=IT_dept, CN=Kireva CA, name=oneandoneserver, emailAddress=winmasta@kireva.com Jul 3 07:45:31 openvpn 60153 TLS: Initial packet from [AF_INET]VPN_SERVER_EXT_IP:PORT, sid=446f96a7 9c4b7ab0 Jul 3 07:45:31 openvpn 60153 UDPv4 link remote: [AF_INET]VPN_SERVER_EXT_IP:PORT Jul 3 07:45:31 openvpn 60153 UDPv4 link local (bound): [AF_INET]CLIENT_EXT_IP:0 Jul 3 07:45:31 openvpn 60153 Socket Buffers: R=[42080->42080] S=[57344->57344] Jul 3 07:45:31 openvpn 60153 TCP/UDP: Preserving recently used remote address: [AF_INET]VPN_SERVER_EXT_IP:PORT Jul 3 07:45:31 openvpn 60153 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication Jul 3 07:45:31 openvpn 60153 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication Jul 3 07:45:31 openvpn 60153 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Jul 3 07:45:31 openvpn 60153 MANAGEMENT: unix domain socket listening on /var/etc/openvpn/client2.sock Jul 3 07:45:31 openvpn 60082 library versions: OpenSSL 1.0.2m-freebsd 2 Nov 2017, LZO 2.10 Jul 3 07:45:31 openvpn 60082 OpenVPN 2.4.4 amd64-portbld-freebsd11.1 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Oct 8 2017 Jul 3 07:45:31 openvpn 60825 SIGTERM[hard,] received, process exiting Jul 3 07:45:31 openvpn 60825 /usr/local/sbin/ovpn-linkdown ovpnc2 1500 1570 10.10.0.2 255.255.255.0 init Jul 3 07:45:31 openvpn 60825 Closing TUN/TAP interface Jul 3 07:45:31 openvpn 60825 event_wait : Interrupted system call (code=4) Jul 3 07:45:29 openvpn 60825 MANAGEMENT: Client disconnected Jul 3 07:45:29 openvpn 60825 MANAGEMENT: CMD 'status 2' Jul 3 07:45:29 openvpn 60825 MANAGEMENT: CMD 'state 1' Jul 3 07:45:29 openvpn 7621 MANAGEMENT: Client disconnected Jul 3 07:45:29 openvpn 60825 MANAGEMENT: Client connected from /var/etc/openvpn/client2.sock Jul 3 07:45:29 openvpn 7621 MANAGEMENT: CMD 'status 2' Jul 3 07:45:29 openvpn 7621 MANAGEMENT: CMD 'state 1' Jul 3 07:45:29 openvpn 7621 MANAGEMENT: Client connected from /var/etc/openvpn/client1.sock 111