Disable Auto-added VPN rules???
-
Hello,
I have checked "Disable Auto-added VPN rules" on System / Advanced / Firewall & NAT. I create rules manually on WAN.
I want to know disabling this option also prevents adding rules to NAT / Outbound rules or it just disables adding rules to Rules / WAN?
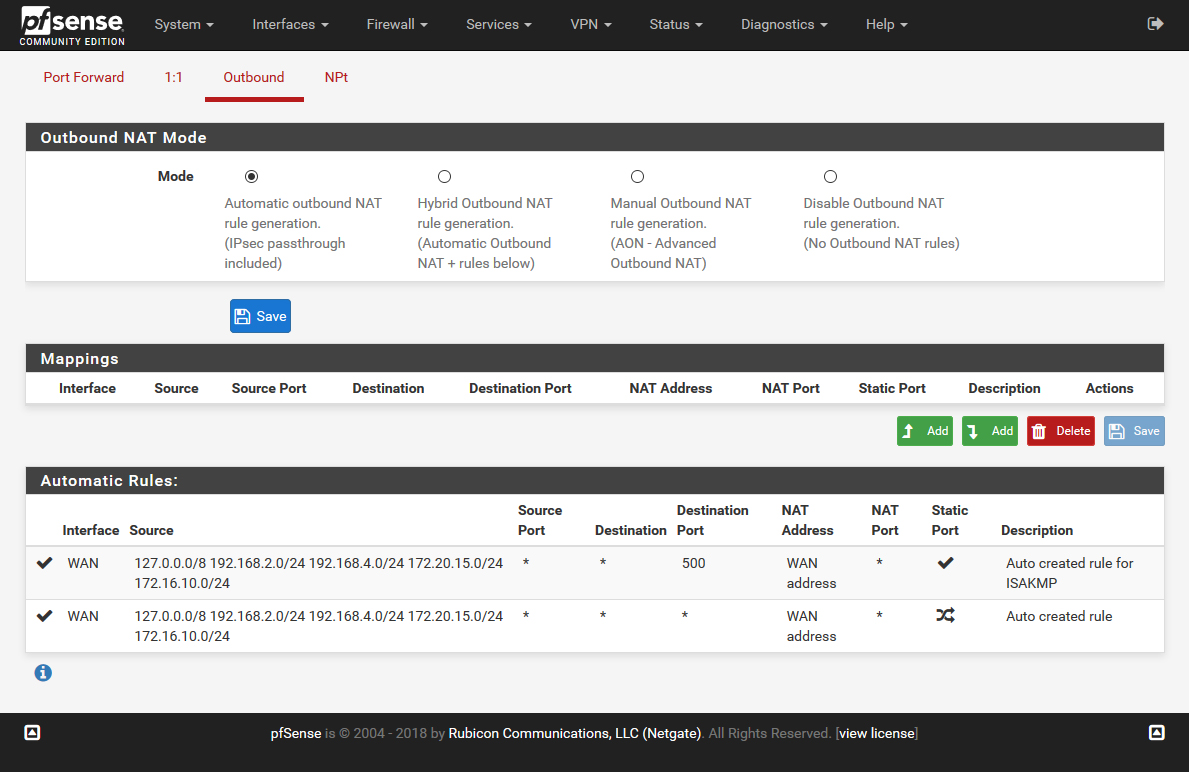
Outbound rules in NAT is automatic.Firewall / Rules / WAN
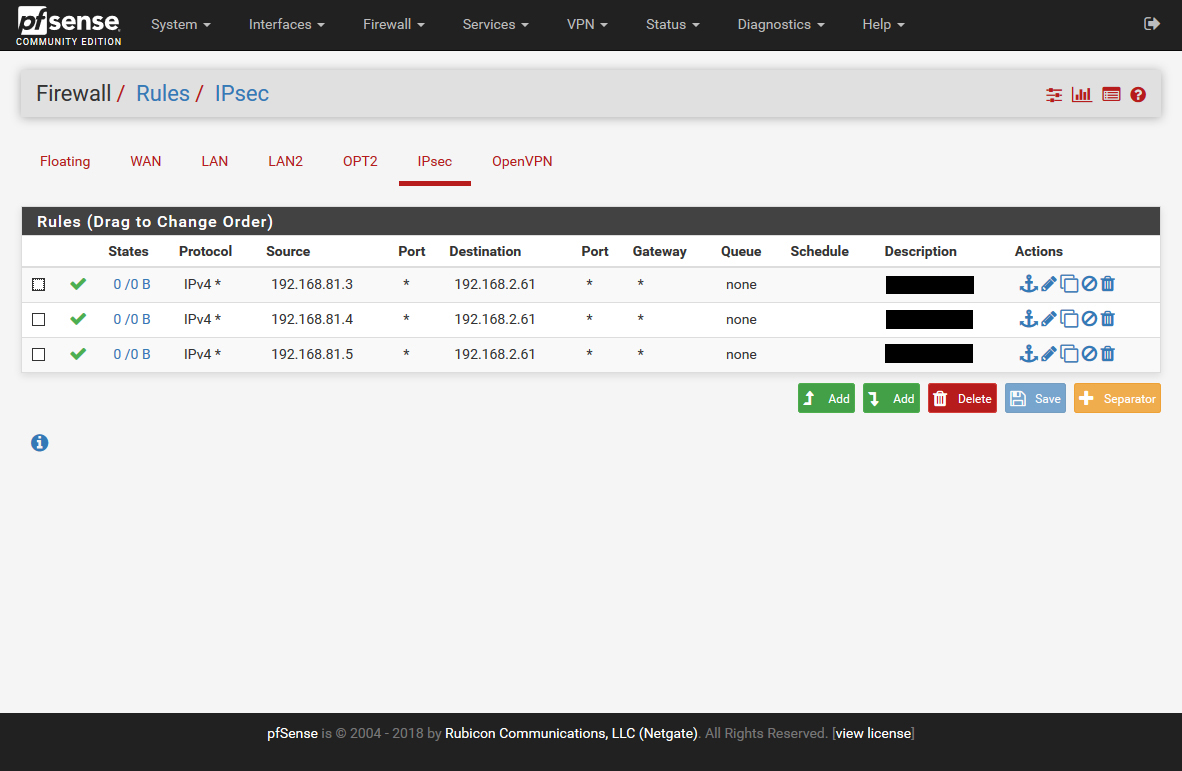
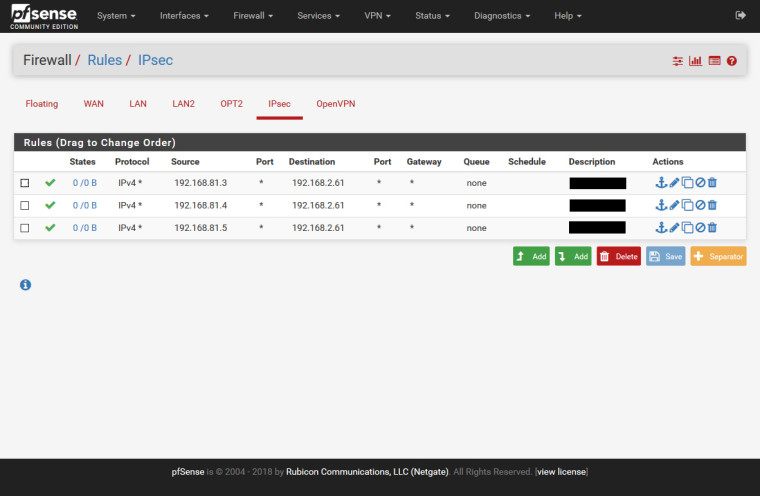
Firewall / Rules / IPSec
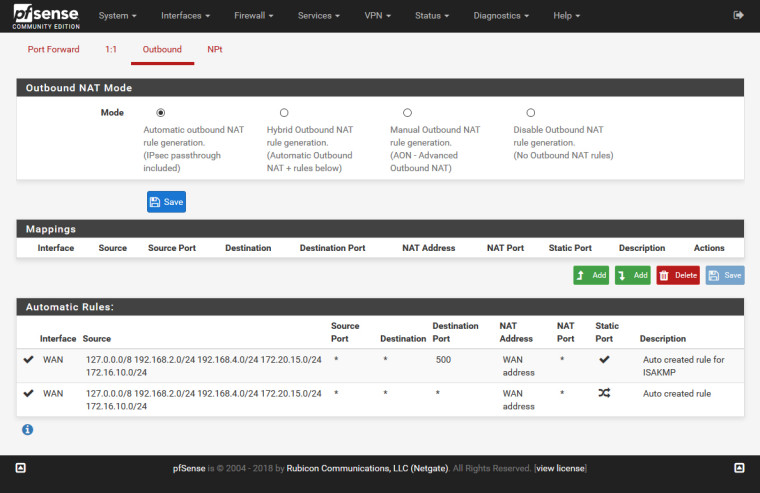
Firewall / NAT / Outbound
 %(#000000)[colored text]
%(#000000)[colored text] -
You can see the outbound NAT rules that have been added when the mode is set to Automatic there.
I would only expect to see rules added for mobile client subnets.The automatic firewall rules option you disabled is only to allow IPSec traffic into the firewall. Not traffic within the tunnel.
Steve
-
In this situation, do I need add rules for ipsec to outbound nat (outbound nat is automatic now)?
-
You would do if traffic sourced from the other side of the VPN needs to access something via the WAN interface locally.
However your IPSec firewall rules show only traffic for one single local host so that should never happen. Unless you add new tunnels or rules.
Steve
-
Here, xx.xx.129.13 is remote office wan address and 192.168.81.3, 192.168.81.4, 192.168.81.5 are remote office internal ip address, and 192.168.2.61 is our internal server's ip address. These hosts must see each other via ipsec. Actually I didn't understand clearly if need to add rules to outbound nat or not, however outbound nat is automatic.
-
No. If you needed to NAT on IPsec you would use the NAT in IPsec Phase 2 not Outbound NAT.
Once the Phase 1 (IKE) tunnel is up you can forget all about the WAN interface.
In your case, if you wanted to only pass traffic between those hosts you would probably want to make these Phase 2 Networks:
Local Network Remote network Host 192.168.2.61 Host 192.168.81.3 Host 192.168.2.61 Host 192.168.81.4 Host 192.168.2.61 Host 192.168.81.5 You can further enforce inbound connections with proper rules on the IPsec tab.