pfsense 2.4.3 ssh password authentication
-
Hello All,
Im testing out pfsense for the first time. I have been a openwrt user for years.
I have installed the latest, 2.4.3 pfsense, in a VM. I cant seem to get ssh to work with password authentication. On the gui i've made sure that "Disable password login for Secure Shell" is UNCHECKED.
yet when i try to ssh using putty or secureCRT, the connection is closed right away. i get a popup saying "connection to pfsense failed. key exchange failed etc................."I have not setup any shared keys yet and just want a password based login. Is that not available in this version of pfsense?
thanks
-
Oh you get key exchange failed.. What version of securecrt are you using? pfsense uses current ciphers and algo's
debug1: kex: algorithm: curve25519-sha256@libssh.org
debug1: kex: host key algorithm: ssh-ed25519
debug1: kex: server->client cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: noneOlder versions of securecrt do not support current ciphers and algo's
I am using 8.5 beta.. But the current stable works as well.
-
i have even tried putty. similar issue. im not even prompted for a username/password.
-
What version of putty?
Again you will not get prompted if your not able to use the right cipher.
Current version is .70 and works just fine with pfsense 2.4.3p1
-
i see. Got it thanks.
-
Here
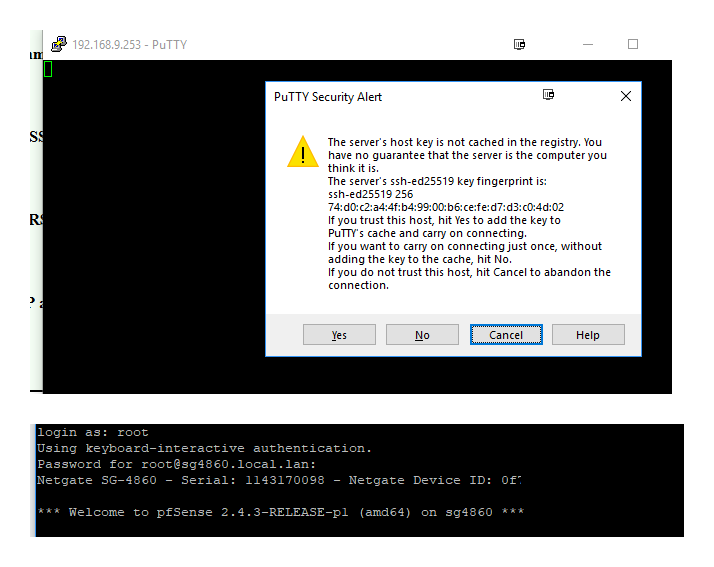
If you have some OLD version of putty you could have problems.
BTW to be complete in my answer - here is simple nmap command you can run against sshd to see what is supported
root@uc:/tmp# nmap --script ssh2-enum-algos -sV -p 22 192.168.9.253
Starting Nmap 7.01 ( https://nmap.org ) at 2018-07-15 10:10 CDT
Nmap scan report for sg4860.local.lan (192.168.9.253)
Host is up (0.00056s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2 (protocol 2.0)
| ssh2-enum-algos:
| kex_algorithms: (2)
| curve25519-sha256@libssh.org
| diffie-hellman-group-exchange-sha256
| server_host_key_algorithms: (4)
| ssh-rsa
| rsa-sha2-512
| rsa-sha2-256
| ssh-ed25519
| encryption_algorithms: (6)
| chacha20-poly1305@openssh.com
| aes256-gcm@openssh.com
| aes128-gcm@openssh.com
| aes256-ctr
| aes192-ctr
| aes128-ctr
| mac_algorithms: (8)
| hmac-sha2-512-etm@openssh.com
| hmac-sha2-256-etm@openssh.com
| hmac-ripemd160-etm@openssh.com
| umac-128-etm@openssh.com
| hmac-sha2-512
| hmac-sha2-256
| hmac-ripemd160
| umac-128@openssh.com
| compression_algorithms: (2)
| none
|_ zlib@openssh.comService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 2.28 secondsYou can also just ssh -vv to get what is can be used as well against that server. But nmap format output is easier to see ;)
-
@johnpoz is correct. It will only fail if you have a really old/outdated version of PuTTY or an older SecureCRT (Before 8.0.x IIRC).
If you want to use ChaCha20-Poly1305 they added support for that in SecureCRT 8.2.
-
@jimp Thanks. I had gotten this sorted out.
now im banging my head against setting WOL (wake on lan) to work over WAN(internet). I have that working in my oepnwrt router but im new to pfsense so dont know much.
Is that something you know about :)Thanks again.