IPSEC Phase 2 Duplicate Causes VPN Tunnel to get stuck
-
Hi all,
I was wondering if someone can help, recently i've upgraded to:
2.4.3-RELEASE-p1 (amd64)
built on Thu May 10 15:02:52 CDT 2018
FreeBSD 11.1-RELEASE-p10I have received calls to say users can not access internet services or VOIP phones have gone down, when checking the situation I have noticed that there is a replication of the phase 2 which causes the issue. It looks like the old phase 2's are hanging and the new ones are passing traffic but due to the old established being kept the VPN is getting confused. After deleting the VPN phase 2 entries which are not sending or recieving any more it starts to work.
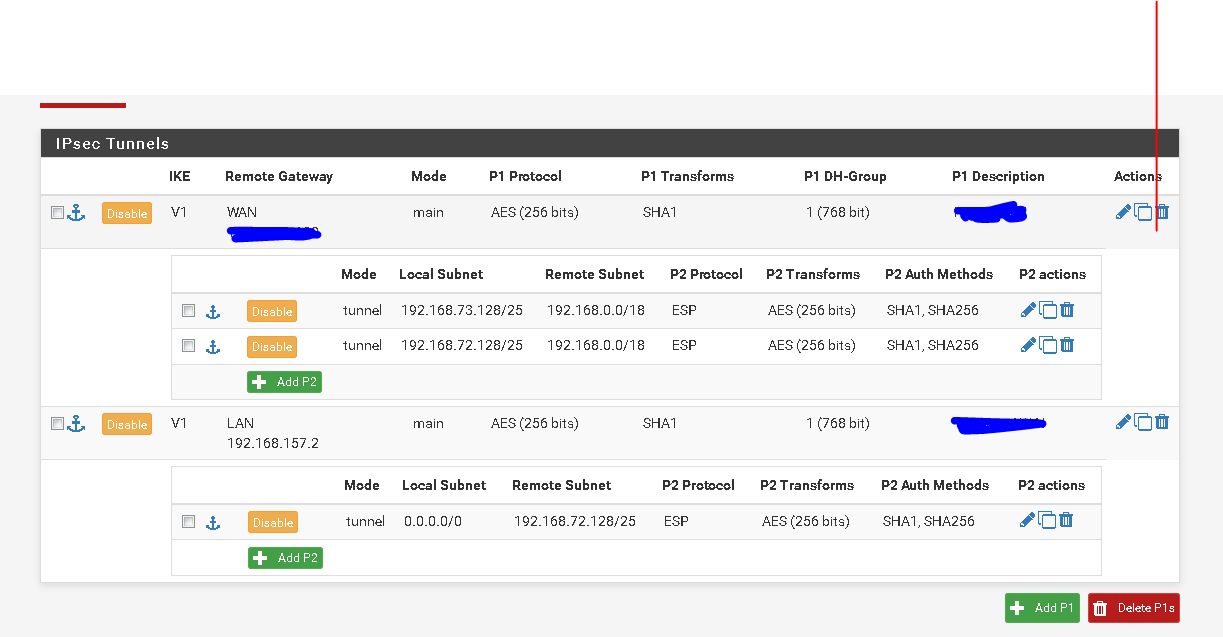
please note that this device is supporting 2 VPN's which looks like this:
MAIN BUILDING -----------> FIRST HOP 192.168.73.129/25 -------------> 192.168.157.0 & 192.168.72.129/25SECOND BUILDING
-
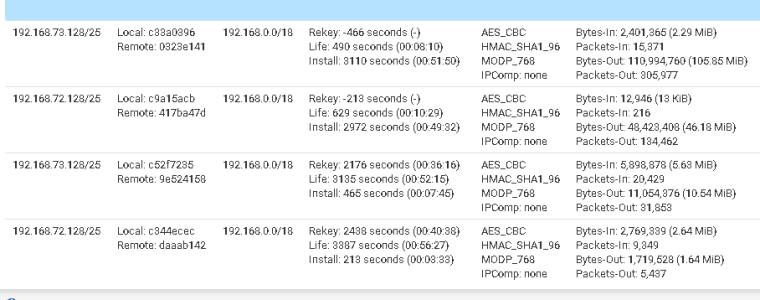
The entries with the negative rekey times should not be there.
What have you done with the phase 1 and phase 2 lifetimes, the disable rekey checkbox, and the margin times?
The multiple P2s being shown look more like a symptom of the problem, not the cause. It looks like they are simply showing you there is a problem rekeying with the other side. What is on the other side?
-
@derelict a cisco firepower NGA.
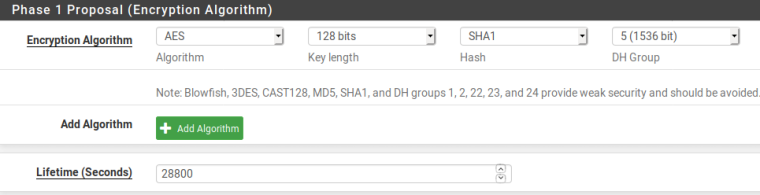
P1 standard config no changes to margintime and lifetime 28800.
P2 lifetime 3600.
For some reason I think the rekey goes into minus until the lifetime expires.
-
While it is down you can also pcap the IPsec traffic and see what SPD it is arriving for.
Something between the two endpoints is getting out of sync, apparently.
I would take a really close look at the IPsec logs and see what's happening at re-key time.
-
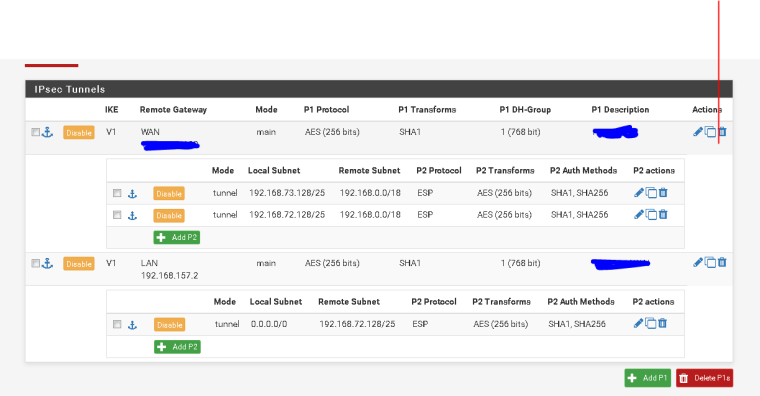
@harow Same problem. I have one P1 and one P2 connection only, and occasionally, I find multiple 'working' P2 connections when users are complaining about no connection. Reset the connections, and everything is fine.
I double checked the advanced configuration, and I definitely do not have the "Make before Break" option selected.
 . The guy supporting the other end (a Cisco RB260) tells me he is not setup for multiple P2's either.
. The guy supporting the other end (a Cisco RB260) tells me he is not setup for multiple P2's either.I'm using pfSense 2.4.4-RELEASE-p2 (amd64)
Any suggestions about how to troubleshoot this?
-
@telserv so your getting multiple phase2’s? Which is dropping a connection for a site or location?
Can you show me your config on vpn IPSec tab?
Mine is working fine now
-
@harow Thanks for the quick reply.
The three P2's are all for the same location. I have to drop all three of them for the communications to restart. The failure seems to occur once the P1 has to rekey.
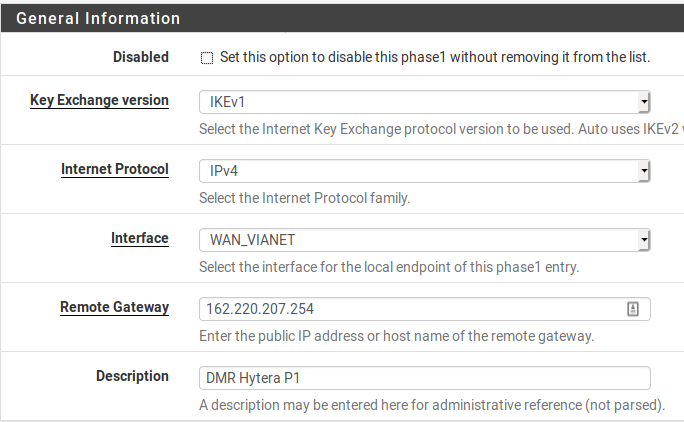
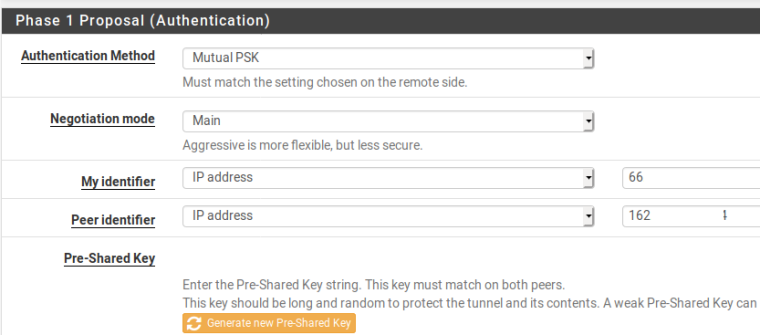
And P2
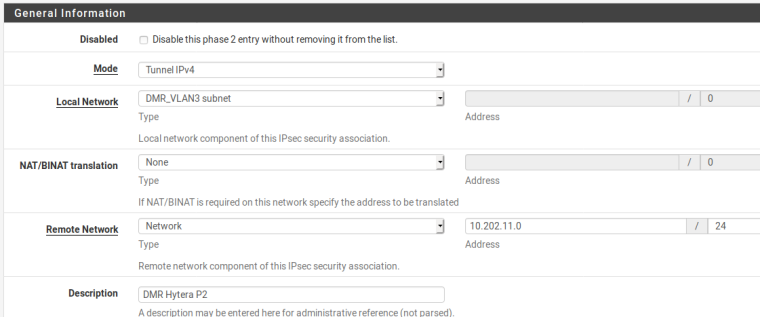
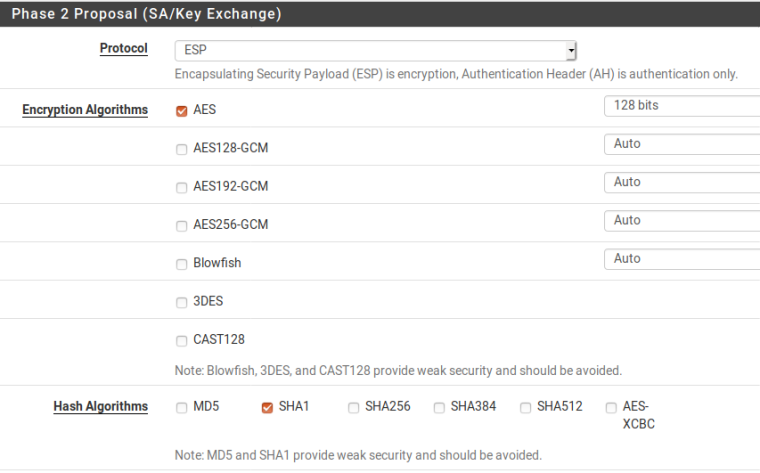
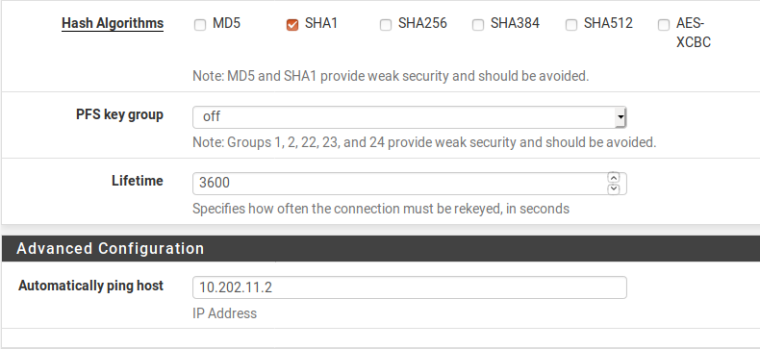
Any suggestions?
-
pfSense will show rekeyed P2 entries there.
You can get more information with
swanctl --list-sasThis is normal. The pfSense node will send traffic using the active SA. That will be the SA that has counters increasing.
It's possible the other side is getting confused by something. You would have to look at the IPsec logs to see which side is requesting the rekey.
-
Wow so let me get this right:
The following VPN is just for one tunnel but seeing multiple SA’s?
Couple of things - remote peer config needs checking for lifetime and make sure IPSec settings match on each end.
Delete and re-create the VPN using IKE V2, move away from V1 and use stronger encryption as yours is very bad. Enable PFS and use group 21+, but make sure your remote peer can use the settings first.
I’ve found that it does not disconnect the expired P2 SA, which keeps it active therefore drops comms to the subnet, this is when staff complain.
Maybe remote end device needs firmware upgrade from bug etc?
Your config looks basic, keep an eye on Vpn status and check logs when re-key, you should see multiple p2 but one should expire. If it hangs or subnet is dropped I think settings on both sides don’t match. Alternatively I think I tested a longer rekey.
If it’s over internet I can always help you take a look?
I run over 170+ VPN using PFSense and only ever had a problem with a multi point VPN, to which it’s ok now. I have w feeling restarting a multipoint VPN in a certain order works but then again could be OCD?
A 1-1 VPN shouldn’t do this behaviour unless remote device an issue? Put PFSense to PFSense see if ok?
-
Deffinately not normal listing this many for one S2S VPN.
@derelict said in IPSEC Phase 2 Duplicate Causes VPN Tunnel to get stuck:
pfSense will show rekeyed P2 entries there.
You can get more information with
swanctl --list-sasThis is normal. The pfSense node will send traffic using the active SA. That will be the SA that has counters increasing.
It's possible the other side is getting confused by something. You would have to look at the IPsec logs to see which side is requesting the rekey.
-
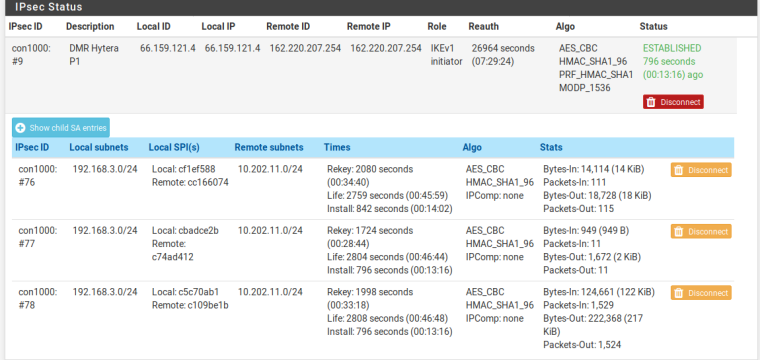
@derelict When checked, all three P2 SA's had increasing packets, so there should have only been one of them at a time.
-
@telserv said in IPSEC Phase 2 Duplicate Causes VPN Tunnel to get stuck:
@derelict When checked, all three P2 SA's had increasing packets, so there should have only been one of them at a time.
It shows at least 2 most of the time, never seen 3!
@telserv said in IPSEC Phase 2 Duplicate Causes VPN Tunnel to get stuck:
@derelict When checked, all three P2 SA's had increasing packets, so there should have only been one of them at a time.
@telserv said in IPSEC Phase 2 Duplicate Causes VPN Tunnel to get stuck:
@derelict When checked, all three P2 SA's had increasing packets, so there should have only been one of them at a time.
-
@harow Thanks for your thoughts on this, and yes you understand the situation correctly. There is only one IPsec tunnel, and on intermittent occasions it shows three P2 connections that all show increasing numbers of packets at the same time.
I'll work thru your suggestions and report what happens. Thanks again!
-
Let us know the outcome has to be the other remote peer as PFSense works so good and it’s 1 VPN
 .
.Get their config screenshotted, I seen on Cisco asa before they need to enter a command which sends alert to dead peer SA. Almost similar to DPD.
Also can’t find your remote peer model of device, you sure it’s Cisco?
-
What makes it even more strange, look at my image my P2 show -44s etc.
Yours show three P2 all active!
-
Because they are rekeyed. If the far side continues to use the rekeyed SAs, that's why they are kept around.
What does
swanctl --list-sasshow?
One INSTALLED two REKEYED?
Look at the logs. Who is requesting those back-to-back rekeys?They will be in the table until that actual lifetime expires. They will be rekeyed some time prior to that.
-
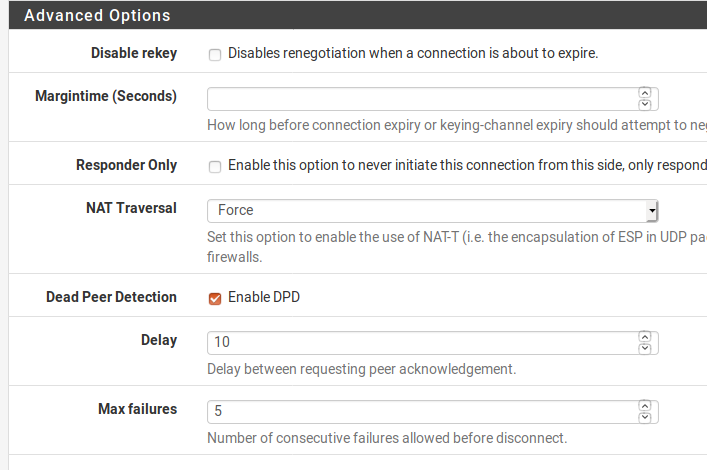
@harow Five days in, and no further problems of multiple P2's. The only thing I've changed is that the P1 is set to not initiate (respond only) to rekey. Will update again if this fails again.
-
@harow Thanks for your suggestions on this. The problem hasn't occurred in the past two weeks, after I changed the P1 configuration from Initiator or Responder to Respnder Only.