Use Block of IP given by ISP in Pfsense
-
Hello everyone, recently due to various reasons our company has been asked to get a block of ips from our ISP. I went ahead with the request and got the following below,
Network Address: 200.xxx.240.32
Gateway(Modem): 200.xxx.240.33
Usable Range: 200.xxx.240.34.38
Broadcast: 200.xxx.240.39
Subnet Mask: 255.255.255.248Our network setup is as following
We have a SmartRG360n DSL Modem in bridge mode which feed into our pfsense box. Our ISP provides us a PPPoE Link with a dynamic ip.
So for the wan side of our pfsense box, we have ip 190.197.xxx.11. I have a 172.16.0.0/24 for Lan.
I am trying to get a 1:1 Nat working between a web server with private ip 172.16.0.50 with 200.xxx240.34. I have read up some tutorials and was tyring to get it working by using a virtual ip (IP Alias). when I try to add pfsense gives the following error
Jul 24 15:35:56 php-fpm 317 /firewall_virtual_ip.php: The command '/sbin/ifconfig 'pppoe0' inet '200.XXX.240.34'/'29' alias ' returned exit code '1', the output was 'ifconfig: ioctl (SIOCAIFADDR): Destination address required'
I researched and added finished added the VIP with command /sbin/ifconfig 'pppoe0' inet '200.XXX.240.33'/'29' alias 190.197.XXX.11
I then setup the 1:1 nat rule and made the appropriate rules in the wan interface to allow traffic to the ports I need open.
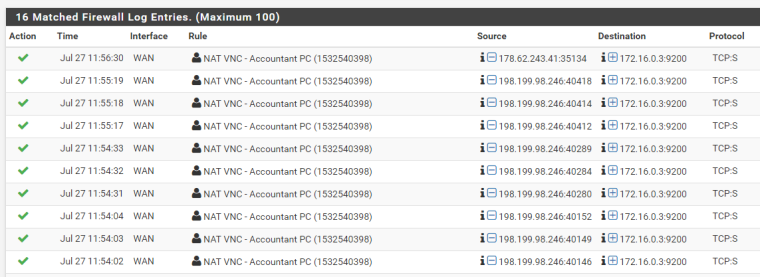
After all this, I found that the port still remains closed, the firewall logs shows that traffic is reaching the server in 172.16.0.50 address but somehow gets no reply.
I have tried looking for solutions provided in the links below but none of them seem to work, can anyone please tell me if I am doing something wrong?
https://networkengineering.stackexchange.com/questions/41052/assign-public-ip-of-29-block-directly-to-a-connected-device-in-pfsense
https://serverfault.com/questions/309187/pass-through-public-ip-addresses-to-pfsense
https://www.reddit.com/r/PFSENSE/comments/6n8x3r/public_ip_on_hosts_behind_pfsense/
Also not sure if it is relevant but with no vips added or anything else, I keep getting wan traffic from the public ips, example below
Act Time IF Source Destination Jul 24 16:45 WAN 5.188.40.99 200.XXX.240.35:3390 Jul 24 16:45 WAN 5.188.40.99 200.XXX.240.38:3390 Jul 24 16:45 WAN 218.201.184.244 200.XXX.240.36:23 Jul 24 16:45 WAN 218.201.184.244 200.XXX.240.36:23 Jul 24 16:45 WAN 177.56.201.196 200.XXX.240.33:22 -
why are you trying to manually add vips by command-line?
-
I was adding the VIPS via command line because when I try to add them via the gui, pfsense gives the following error
Jul 24 15:35:56 php-fpm 317 /firewall_virtual_ip.php: The command '/sbin/ifconfig 'pppoe0' inet '200.XXX.240.34'/'29' alias ' returned exit code '1', the output was 'ifconfig: ioctl (SIOCAIFADDR): Destination address required'
-
i added that /29 as a proxy-arp VIP just fine....
what pfsense version are you running ? -
I have Current Base System 2.4.3_1
-
Proxy ARP shouldn't be necessary on a PPPoE connection.
Neither should a VIP.
You should be able to just 1:1 NAT the target .34 address to the inside address and pass the traffic (destination inside address) on WAN.
If you want the address to appear in pfSense dropdowns, add it as type Other.
If you need to actually bind services running on the firewall (VPN, etc) to one of those addresses, an IP Alias VIP is likely what you want.
-
@Derelict thank you for the response, I tried it the way you mentioned. I have attached some pictures showing the rules. I noticed that traffic is now reaching the internal server however there is no response. Is it some routing problem? Thank you for your assistance.
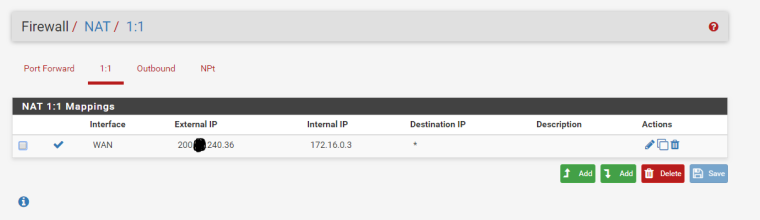
Rule on Wan Tab

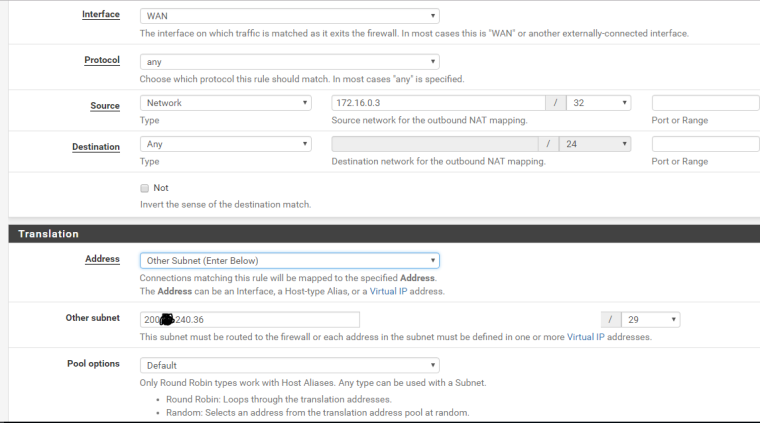
Outbound NAT Rule
Firewall Log
-
If you're going to use 1:1 NAT what you likely want to do is set up manual outbound NAT. For instance:
Source: LAN IP of server/32
NAT Address: public IP for that serverAdd that line above the default "WAN Address" line which is for your LAN subnet (e.g. 192.168.1.0/24). Otherwise traffic coming in on one IP may go out another IP and generally firewalls (on the other end) don't allow that.
On ours we do not have "other subnet" on the Translation/Address line...we have the public IP of that server listed in the box. Ours is an old setup upgraded many times, and is not using PPPoE, but we have the second public IP set as a Proxy ARP alias.
-
@teamits Hello, I use this method you presented, using the public ip as a proxy alias, making the nat 1:1 rule and using manual outbount Nat but traffic still is not going out from my internal server to the internet. A traceroute shows that it just reaches the default gateway given by PPPoE and stops there.
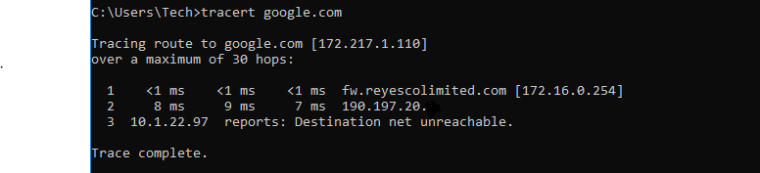
-
1:1 NAT handles outbound NAT. You don't need to do anything else. Adding outbound NAT rules in that case only gives you another opportunity to do it wrong.
-
@derelict thanks for the response, I tried it with only the 1:1 nat and no changes to the outboung nat but still no traffic from internal server out, it stops as it hits the isp gateway. the only difference which I am not sure if it is much of a difference is the response
Tracing route to google.com [172.217.8.78]
over a maximum of 30 hops:1 <1 ms 1 ms <1 ms fw.reyescolimited.com [172.16.0.254]
2 8 ms 29 ms 8 ms 190.197.20.X
3 * * * Request timed out. -
@derelict, I will defer to you on the outbound NAT. I'm pretty sure though in the past it was necessary? Like I said we have a long history dating back before pfSense to m0n0wall so possibly that was added at some point and I didn't realize it. Our setup is a little different...we have two pfSenses, one for the building and one for our office. I was looking at the office router. Our building router has the public IPs set as "IP Alias" (not proxy ARP) and there is no outbound NAT entry there. So, I'm sorry for going down that path.
@xyphos10, so 190.197.20.X is your ISP/WAN gateway (outside your office)? If it wasn't leaving the ISP "modem" then I would say maybe restart that, since I know Comcast's router/modem sometimes takes a while to recognize ARP changes. If packets are leaving your office though, that seems like maybe the ISP isn't allowing traffic from that IP, or maybe not routing the response back to you? (I do recall a case once where the ISP apparently re-used a modem somewhere else, which had the wrong/old IPs in it, and we found we could ping the IP we had just been given even if we disconnected our router)
-
@teamits 190.197.20.X is the gateway of our isp. we have a SmartRG 360n modem in bridged mode which feeds the wan side of the pfsense firewall. I have pfsense wan configures with pppoe username and password from our isp so it gets the ip directly from our isp which is 190.197.21.xxx
-
The traffic would obviously have to be sourced from 172.16.0.3 when it arrived at the firewall to benefit from the 1:1 NAT for outbound connections.