Force redirection of DNS for OpenVPN traffic
-
Hi
I have a NAT rule on the LAN to ensure that all DNS traffic is redirected through the DNS Resolver on pfSense (which has pfBlockerNG and DNSBL running on it).

I want to ensure that, when connecting over OpenVPN, any inbound DNS requests are also routed to the pfSense resolver. However, they don't appear to be caught by the NAT rule meaning that if the OpenVPN client specifies its own DNS server, it will bypass the protections on pfSense. If I create an identical NAT rule but specifying the OpenVPN interface instead of LAN it still doesn't work.
What am I missing please?
Andrew
-
No matter what you do, you cannot prevent an OpenVPN client from NOT using the pushed default gateway routes and sending DNS queries directly out their own internet connection instead of the OpenVPN tunnel unless you have the clients themselves completely locked down (and that would be a trick).
So not sure how much security making this work will provide.
That said, a port forward on OpenVPN seems like it should work. You might want to post what you have actually done there.
-
Many thanks. Yes, I take the point re clients routing outside of the VPN. I actually trust the clients though - this is a domestic setup so it's invariably me that's connecting.
The issue is more trying to ensure the DNS goes through pfSense if for some reason a device doesn't respect 'push "dhcp-option DNS ..."' but nevertheless does route its DNS traffic over the VPN.
Re the rule, I just took the existing one, created a new copy rule and changed the interface from LAN to OpenVPN:
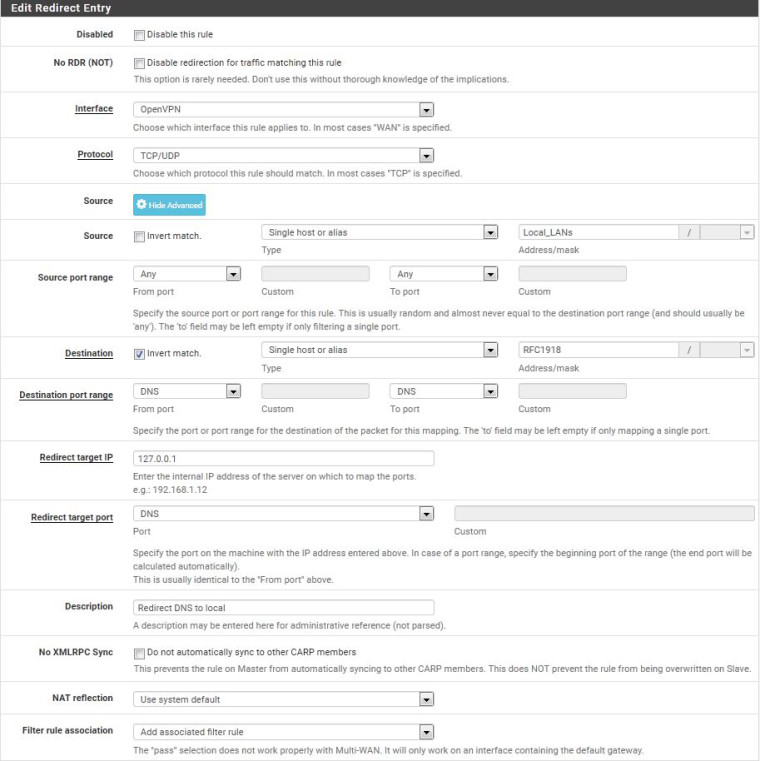
If I enable logging on the associated firewall rule, it doesn't show any packets being caught by the NAT rule.
-
I bet your Local_LANs alias doesn't include the IP subnet used by your VPN clients. This means your rule will never match DNS traffic coming over the VPN. I would set the source network to just "any" because any DNS traffic coming over the tunnel can't be from anywhere else but the client.
-
Thanks. The Local_LANs alias does include the OpenVPN subnet. I'll try selecting "any" anyway and see if it makes any difference.
-
I worked out what was going on.
Looking at the pfSense generated server config file, the push "redirect-gateway def1" directive wasn't there so no web traffic was going over the VPN anyway.
I'd ticked both the "Redirect IPv4 gateway" and "Redirect IPv6 gateway" but for whatever reason pfSense wasn't putting the directive in. Not sure if that's a bug or whether I'm misunderstanding what those config options in pfSense are supposed to do?
With the directive in there and the NAT rule set up, all works as it should.
Thanks.
-
The setting gets pushed to the client. It is not put into the config file.
As I was saying earlier, the client is free to ignore it.
I do not believe that the server can override hard settings on the client and I do not believe the config exporter includes any settings to that effect.
Client has a local setting to push all traffic over the tunnel - the server can't do anything about that except block the traffic it doesn't like, regardless of the server setting.
Server pushes the redirect-gw routes but the client is set to ignore them - the server can't do anything about that so the client traffic goes out client WAN.
Server pushes the redirect-gw routes and the client is set to accept them. Client traffic flows over the tunnel and the server can control this by pushing or not pushing the redirect-gw settings.
-
Thanks Derelict.
Yes, I understand. My point is that I tick the Redirect IPv4 Gateway option in pfSense but it doesn't push the redirect-gw option. Everything works ok if I put the push redirect-gateway option into the custom box in pfSense so that it's in there manually.
-
Have you checked to see if something like "don't pull routes" is enabled on the client.
It works for everyone else. The logs will tell you.
-
Yes, the client is configured correctly. I've been using the server/client config for many months on another OpenVPN server, and have now been trying to recreate the server end in pfSense (everything on client untouched).
Even when it wasn't working propertly on pfSense the client accepted the route ok for the LAN (i.e. push route as a custom option). However, pfSense wasn't pushing the redirect gateway directive to the client despite the option being checked in the GUI. It wasn't there either if you open the pfSense generated server config file (in var/etc/openvpn).
If I add it manually in pfSense, everything works (no changes on the client side).
-
If it were me I would want to figure out why. The server either pushes
redirect-gateway def1or it doesn't. The client either accepts and acts on it or it doesn't.The need to use manual push routes has all but been deprecated by the Local Networks setting in the server config itself.
I would take a good, long look at all of the new options that have been added to the GUI config and transition to GUI widgets any custom options that are now implemented as GUI widgets.
