1: NAT done but SSH not accessible
-
I configured a 1:1 NAT to a DMZ server. The external ip pings globally but ssh connection not happening tho the DMZ server. I have set a rule at Interface : WAN -> Protocol ->any--- Source->any-- to Single host DMZ server. Still SSH is not happening externally.
-
Well did you follow the port forwarding troubleshoot guide. Did you validate that traffic even hits pfsense wan?
Did you validate pfsense sends it on to server or not?
https://www.netgate.com/docs/pfsense/nat/port-forward-troubleshooting.html
Without you actually posting up your nat and rules its impossible for anyone to guess what part your missing or what is wrong.
BTW - ssh is not "any" its tcp.. So why would you make the rule any?
-
There is a checkpoint firewall and it does the NAT without any problem in the same server configuration. As I am changing to pfsense firewall, The SSH is blocked. I will try to open all TCP connection to DMZ single host. The internet is working on DMZ.
-
So you have a firewall upstream of pfsense, and your forwarding traffic to pfsense wan IP on this natting firewall. If so did you remove the block rfc1918 rule on the wan?
Again why are you going to open up ALL tcp ports? You don't know what tcp port the sshd is running on?
If pfsense is downstream of router doing nat - why are you natting on pfsense for rfc1918 to rfc1918 networks?
-
Please listen to my complete plan
- I am planning to replace checkpoint with pfsense.
- I have created WAN, LAN & DMZ.
- I have a multi-wan load balancer for bandwidth load balancing and redundancy.
- I have created a IP alias VIP for one of the usable IP address.
- I have done NAT for VIP -> DMZ server.
- The NAT is not working after doing the NAT and setting rules.
- The NAT works fine with the checkpoint firewall but when I replace checkpoint with Pfsense, The NAT doesn't work.
- I have enabled access for RFC 1918 networks in the WAN
Are you clear now?
The rule created in WAN and the NAT configuration are in the pictures attached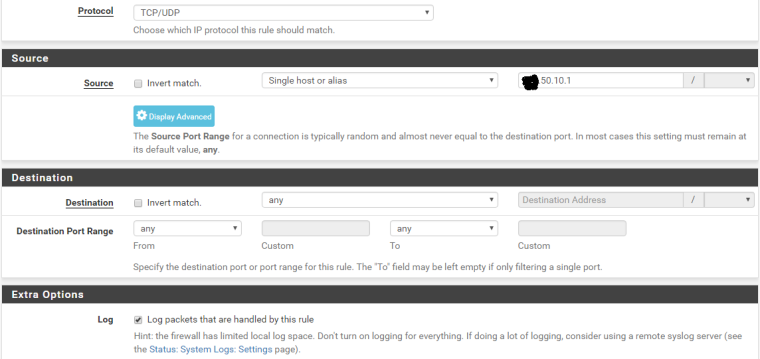
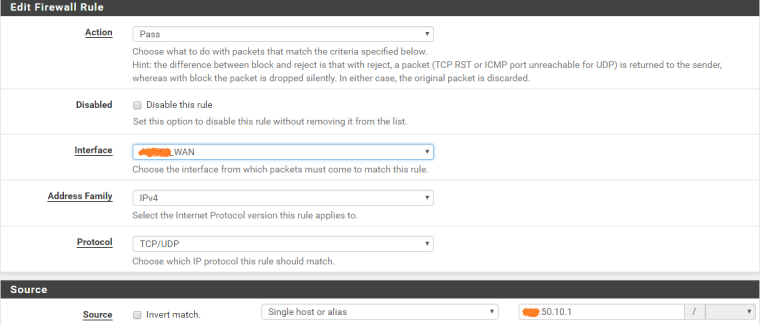
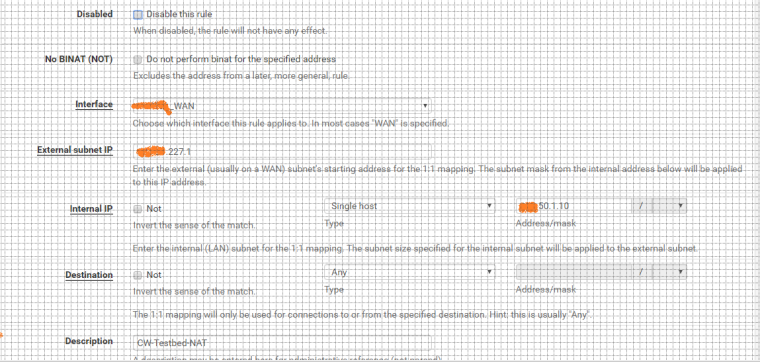
- I have enabled access for RFC 1918 networks in the WAN
-
So this is a VIP? You sure tis working? Why do you have source limited to single IP? Is that the ONLY place your going to be doing ssh from?
If these are rfc1918 address why are you hiding them? Why do your screenshots look like graph paper? with the grid on them?
Lets go over this yet again. Is the traffic even hitting your wan? Do a simple sniff.. Does the traffic get there, does it go out your lan to your client your trying to forward to?
Please go through the troubleshooting guide - where is it failing at.. You have verified traffic hits your wan, towards your vip? And that pfsense is NOT sending the traffic out the lan to your dest IP?
It really takes all of 2 minutes tops to figure out where you have issue in a port forward.
-
Not used multi WAN but is your Destination of ANY correct ?
Don't you need two NAT statements or an alias with the two WAN addresses as the destination.
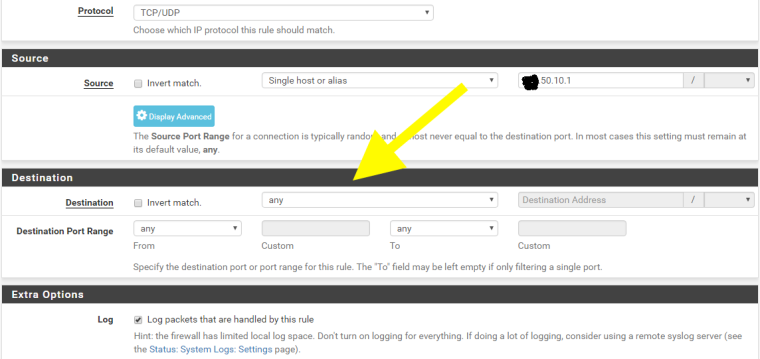
Here's how I NAT my g_ipv4_friendly alias to my sftp box via a single WAN interface :-
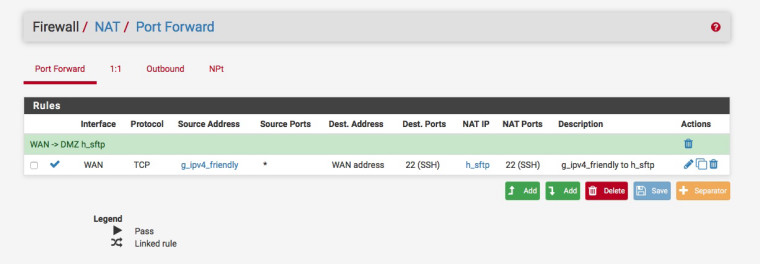
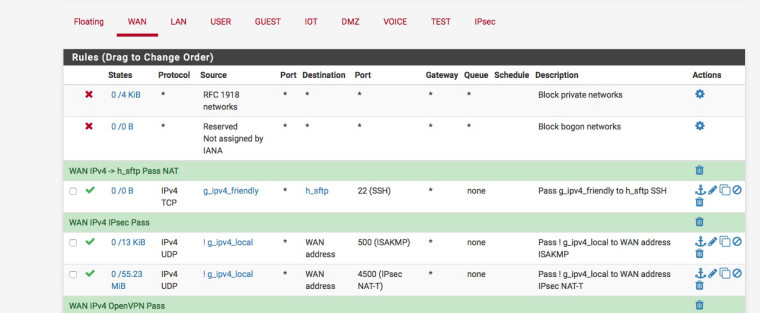
-
@johnpoz Hi John.. Thanks for your effort. yes I am directing FQDN to this VIP address so I can access it globally. Globally the usable WAN VIP is pinging. But the traffic is not NATing to the DMZ server. I will do the sniff and post the results. I really have to fix this.
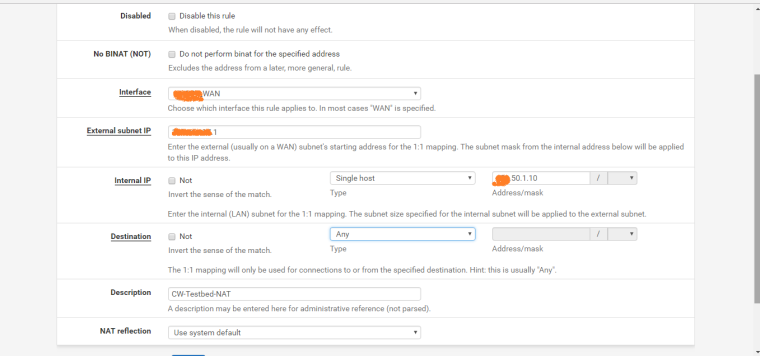
-
@nogbadthebad Hi! Thank you for your reply. I have tried changing the destination to WAN address in the WAN rule and also in the NAT rule. But still no luck. I don't know why I am not able to do this simple NAT. I have done far tough things in pfsense.
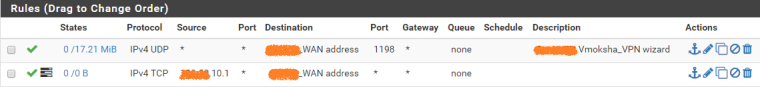
-
Is that bottom rule where SSH should hit?
If so why isn't a port set!
Draw a diagram of your network, to be honest its a nightmare trying to figure out what's what when you chop off the top of the descriptions.
https://www.netgate.com/docs/pfsense/nat/port-forward-troubleshooting.html
-
The dest would NOT be your wan address if your trying to do your 1:1 on your VIP..
The is really basic stuff here - first things first, is freaking validate the traffic is hitting this vip. That is always step 1 when troubleshooting anything to do with a port forward. Actually validate traffic gets there.. Since pfsense can do nothing if its never seeing the traffic.
https://www.netgate.com/docs/pfsense/nat/1-1-nat.html
With a 1 to 1 nat the dest would be the internal IP on the firewall rule..
-
This post is deleted! -
@nogbadthebad I thought NAT simply forwards the traffic from a static IP to an internal ip. Because I want multiple services with mutiple ports to be accessible. that's why I chose NAT. Should I specify the ports even in NAT? Opening all the ports i snot right. Let me put it simple. Imagine I have configured a usable static IP as a VIP. I want that VIP to provide me access to an internal server for multiple services. How do you do it. Tell me the process I will follow exactly. I tried mutiple videos and documents but no luck. Yes, the 2nd one is the rule for NAT.
-
@johnpoz Thank you John.. I do not get the VIP logs in the firewall logs. I don't know why. If I delete the VIP the FQDN doesn't ping. If the VIP is up it pings. I tried installing Sniff package but it doesn't show in the services. I will go through the document more abd will update you.
-
You don't need a sniff package - its right under diag, package capture..
MY gawd this is getting frustrating.. It takes all of 30 seconds to take a sniff and test this..
You don't need to setup any firewall rules or anything. Setup your VIP... Send traffic to it on 22, while your doing the packet capture... Do you see this traffic?
Once you see this... Then setup the 1:1 nat.. That is all of 30 seconds more..
If it does not work, then sniff on your lan side interface with packet capture. Send traffic to vip - do you see the packets going to the private IP?If you do, but no answer then problem is on your server your send it too. If you don't see it sending then you did your 1:1 nat wrong..
The firewall rule you need will be to the private IP address in your 1:1 NAT.. Do you really need pictures for this??
-
Here I don't really have an IP I can use.. but on my /30 on wan at work I created a /32 vip using the broadcast address..
I then pinged it from home connection... While sniffing... See the traffic hitting it from my home 64.53 address..
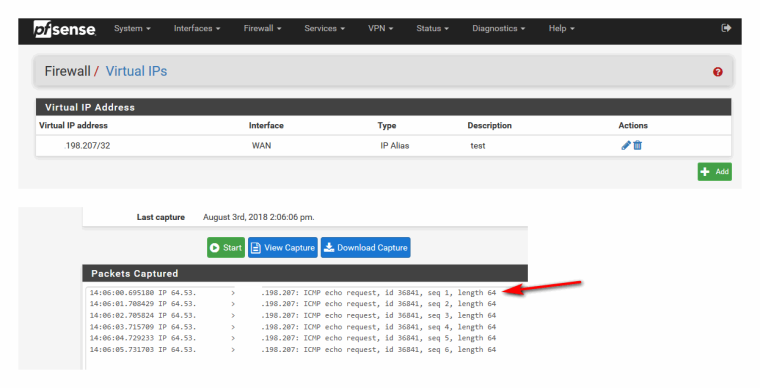
It doesn't answer ping.. It then add firewall rule to allow ping - and bam it pings..
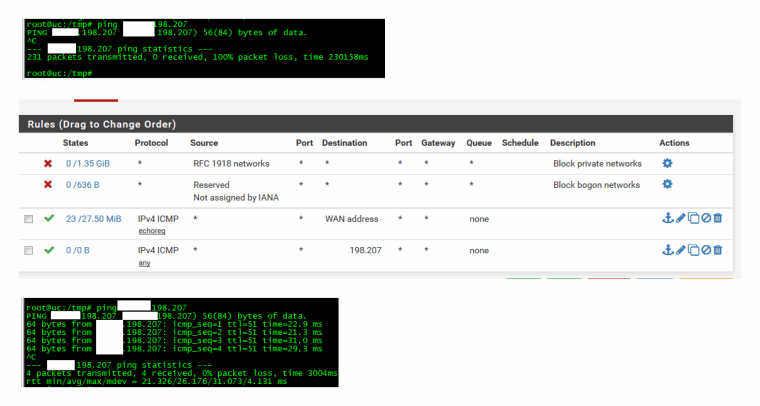
-
Here so I created 1:1 nat, then firewall rule to allow ssh from my home IP to the dest private IP..
I then created ssh connection to this while sniffing on lan side interface... You can see pfsense send on the ssh traffic. But it doesn't get an answer because IP is actually inside IP of another pfsense in NY from where I am at in Chicago.. And its default route to get to public would go out its wan vs coming back this way.
This is why you have to sniff and validate if pfsense is sending the data or not - the problem could be on your host box.
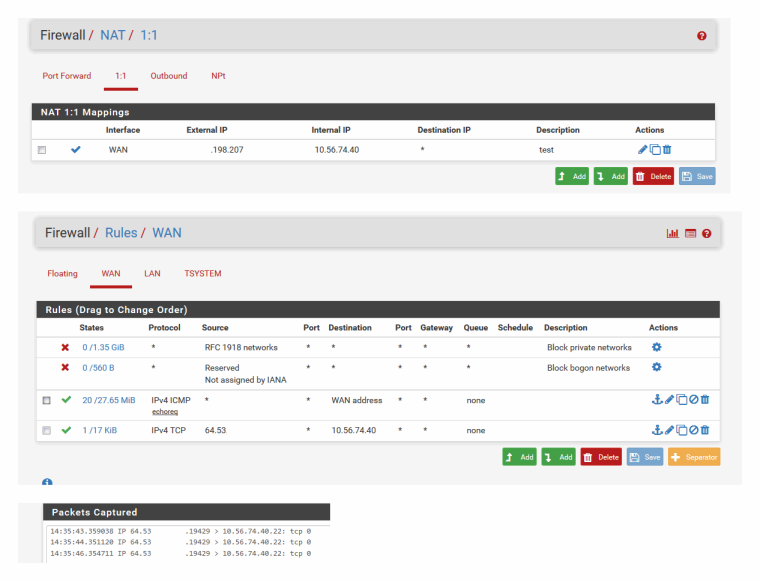
-
You are probably right. I tried a sniff on WAN VIP through WAN interface. But there is no request for the VIP. I am sorry for the delay as I was not working on my weekend. I will try configuring the rules and try again
-
If you would of followed the troubleshoot guide from 4 days ago I linked too... Just saying..
-
I am literally trying. I am doing this NAT for the first time. Thank you very much for your help. I have not checked the result. But still let me complete this and will post the result.