SSH Login Attempts
-
I am seeing ssh login attempts in the System Log like the following:
Aug 1 11:13:26 sshd 72971 Disconnected from 94.23.195.112 port 37754 [preauth] Aug 1 11:13:26 sshd 72971 Received disconnect from 94.23.195.112 port 37754:11: Normal Shutdown, Thank you for playing [preauth] Aug 1 11:13:26 sshd 72971 input_userauth_request: invalid user mattes [preauth] Aug 1 11:13:26 sshd 72971 Invalid user mattes from 94.23.195.112 Aug 1 11:10:19 sshd 79359 Disconnected from 185.113.240.93 port 45598In System | Advanced I did have "Enable Secure Shell" checked and also "Disable password login for Secure Shell (RSA/DSA key only)". But I assumed that without adding a WAN or floating firewall rule to accept SSH (22) traffic it would be blocked by default. I was thinking it would work like the webGUI and only accept logins from the local traffic.
What is the default behavior? Does checking "Enable Secure Shell" allow outside ssh access?
Thanks
-Andrew -
@ahking19 said in SSH Login Attempts:
n System | Advanced I did have "Enable Secure Shell" checked and also "Disable
"Does checking "Enable Secure Shell" allow outside ssh access?" No.
Do you have a firewall rule on your WAN enabling SSH, SSH inbound to the WAN interface would be blocked by default ?
Looks like brute force SSH to me.
https://www.abuseipdb.com/check/94.23.195.112
https://www.abuseipdb.com/check/185.113.240.93
-
I don't currently have an active WAN firewall rule to allow inbound port 22.
I did have a rule that was port forwarding 22 to an SFTP server but that rule is disabled, although it exists. Haven't used the SFTP server in 10-12 months so I could delete the rule.
-Andrew
-
post up your wan rules.. NO turning on enable ssh does not auto create wan rule to allow traffic.
Do you have any floating rules?
-
I used this on my Pi running FreeBSD if ever you need to block SSH brute force attacks:-
https://www.cyberciti.biz/faq/freebsd-openbsd-pf-stop-ftp-bruteforce-attacks/
-
pfsense has built in lockout of failed attempts
https://www.netgate.com/docs/pfsense/firewall/sshlockout.html
Sure there is a way to adjust the number of fails - but I do not think its in the gui anywhere.
-
@johnpoz Here are the rules
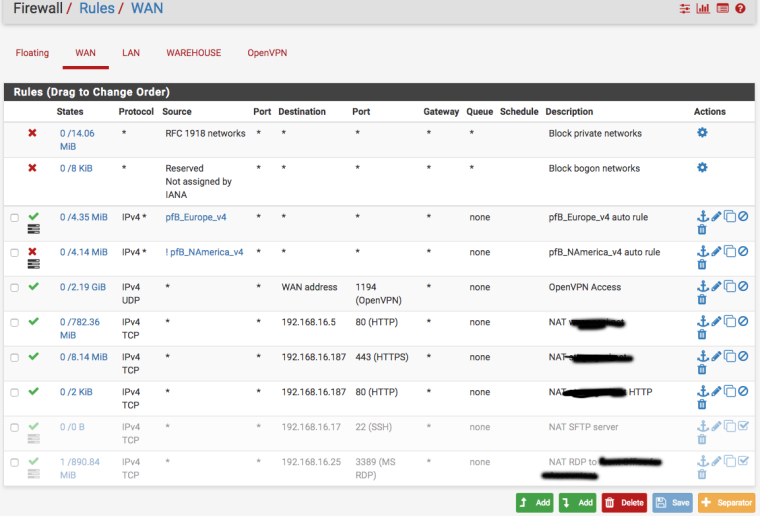
-
How about the floating rules ?
-
Dude your rule right there on top allows ANY Ip in that pfb_europe_v4 to anything... Why in the world would you have such a rule???
-
No floating rules
-
That first rule allows access to anything.. Coming from anything in that alias.. So no shit getting brute force on ssh, and your gui to as well.
Why do you think you need such a rule?
-
@johnpoz said in SSH Login Attempts:
Dude your rule right there on top allows ANY Ip in that pfb_europe_v4 to anything... Why in the world would you have such a rule???
What John said, if you look in the firewall logs, you'll see it as its logging it.
-
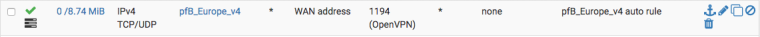
Damn, was temp rule for team working in France. Updated rule to only allow OpenVPN.
-
That rule is pointless since you have a rule just below it that allows vpn any source. Unless you just want to log those from that alias?
-
There is a block rule in between if NOT North America.
-
@ahking19 said in SSH Login Attempts:
North America.
Wouldn't it be better to change the block rule in between if NOT North America to a pass North America, then the rule beneath block any OpenVPN and log?
-
True.. on the ! NA rule.
But you could for sure write those rules a bit more clear.. But without knowing EXACTLY what your wanting to do its just guessing, etc.
-
That would be fine for OpenVPN. But also don't need HTTP & HTTPS sites available outside North America. Not sure how/if I can combine pfBlocker rule with NAT rule. if that makes sense...
-Andrew
-
Sure you can if you just use its aliases - they can be used anywhere you want.. Rule, Nat, etc.
-
Thanks. I'll take a look at using the pfBlocker aliases.