HEADS UP: Be aware of Trusted Recursive Resolver (TRR) in Firefox
-
@jpgpi250 said in HEADS UP: Be aware of Trusted Recursive Resolver (TRR) in Firefox:
haven't had any problems using the rules, they have been active for over a month.
Not what I asked ;) My question is related to you have hits.. So you have something trying to use doh.. Did you do that on purpose? To test you rules - or is there something on your network actually trying trying to use doh?
I would for sure investigate what source IP is triggering those hits, and see WTF its up with it and why is trying to use doh..
My doh rules have no hits..
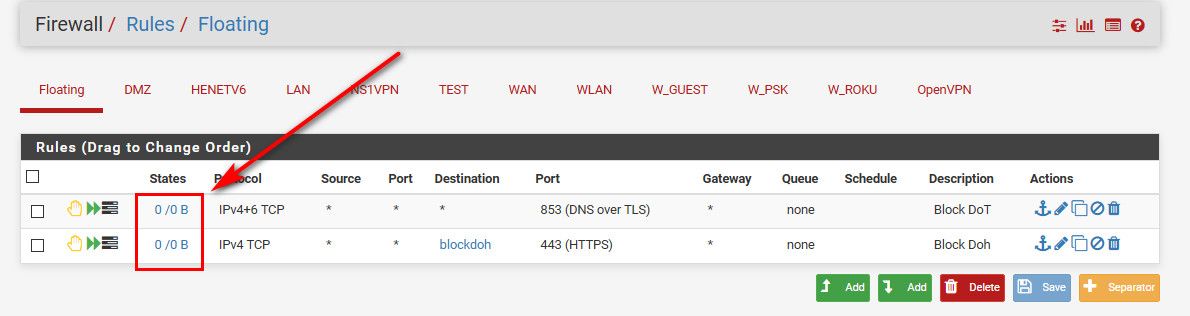
I know they work because I tested them before.. but then I reset the rule counters on purpose.. Because If I see that tick up, I sure and the F would be chasing down the device that tried it..
Since I block the resolving of said doh domains anyway, these rules should never get any hits.. Because the client would not even be able to resolve the doh domains to use... But these rules are in place to catch some client that hard coded the name and IP of doh.. Take a guess - I am not a fan of doh or dot... But atleast dot is easy to block.. Doh is some sneaky ass shit.. That is just WRONG that some of these browsers and shit are auto opting someone into using their dns..
-
@johnpoz
I started this proactively, I doesn't look like I currently have any clients, trying to use DoH. I tested my rules, using this DoH client (it isn't very good, but I only needed to verify the rules worked)
Blocking the domain names (DNS blocking) is only a partial defense to block DoH. Most clients need to resolve the domain, in order to send a DoH request. Using a DNS blocker (pihole, pfBlockerNG, Adguard Home, …) helps achieving this, however, there is a new technique, already in use by some providers that doesn't require the domain to be resolved, prior to the DoH request.
I assume devices and apps, that try to force DoH, this to ensure that blocking their DNS name doesn't prevent tracking and data collection, will soon pick up on this. I found an example here, the resulting string doesn't contain an IP or a domain name.Apart from that, Some providers offer normal DNS (port 53) and DoH on the same IP address. Example:
- resolver1.opendns.com
- resolver2.opendns.com
Using the IP list(s), blocking only port 443, ensures the normal DNS requests (port 53) still work.
-
@jpgpi250 said in HEADS UP: Be aware of Trusted Recursive Resolver (TRR) in Firefox:
Using the IP list(s), blocking only port 443, ensures the normal DNS requests (port 53) still work.
Dude your preaching to the choir.. I specifically went over why I also have the IP based rules ;)
If I were you, I would clear the counters on you rules.. So you can see by just a glace of your rules if anything has tried to use doh.
-
Just a heads up - Google Chrome's Secure DNS (DoH) is arriving soon. Thankfully it looks like it will be easy to disable:
https://blog.google/products/chrome/more-intuitive-privacy-and-security-controls-chrome/
-
Why and the F do they make this the default? If they want to support it great, just don't make it something I have OPT OUT of... Such features should always be opt in as the default stance..
Out of the box the browser should use the OS for dns.. It doing anything other that should be required to opt in!!
-
at least
if your current service provider supports it
from what i understant it will use doh only if the dns you have configured support it
?
You can also configure a different secure DNS provider in the Advanced security section
they didn't accept money from cloudflare or from any other dns services
if it's the case, it's not that bad and always better than firefox -
interesting how this android phone is ignoring my dhcp settings (8.8.8.8 is not one of my dns) and try to use dot,
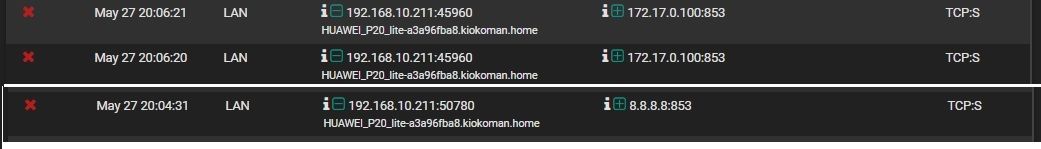
the phone have chrome installed, not firefox but maybe is some other apps running on it
-
-
Some (most ?) Android devices do natively their Internet connectivity check towards 8.8.8.8.
Android 9+ have "Private DNS" settings enable/disable/auto for DoT.
Both things together may explain your logs.
-
@kiokoman said in HEADS UP: Be aware of Trusted Recursive Resolver (TRR) in Firefox:
from what i understant it will use doh only if the dns you have configured support it
?So you saying if I already point to say 1.1.1.1 and they do doh, then it will use doh vs just open?
I guess that is not as bad as some of the others.. But if using say 192.168.1.1 it won't?
-
@Bob-Dig idk it's not my phone, if it's "Private DNS" settings than it was probably on by default, my family does not know what dot / doh is
@johnpoz exactly
-
D darcey referenced this topic on
-
D darcey referenced this topic on
-
D darcey referenced this topic on
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
U Uglybrian referenced this topic on