TorGuard / Port Forward / Adding VPN
-
So I'm trying to figure out why my port forwarding stops working on my TorGuard VPN once I create a OpenVPN Server.
My config is as follows:
- TorGuard Client configured on pfSense
- Interface configured called TGINT that's my OpenVPN client
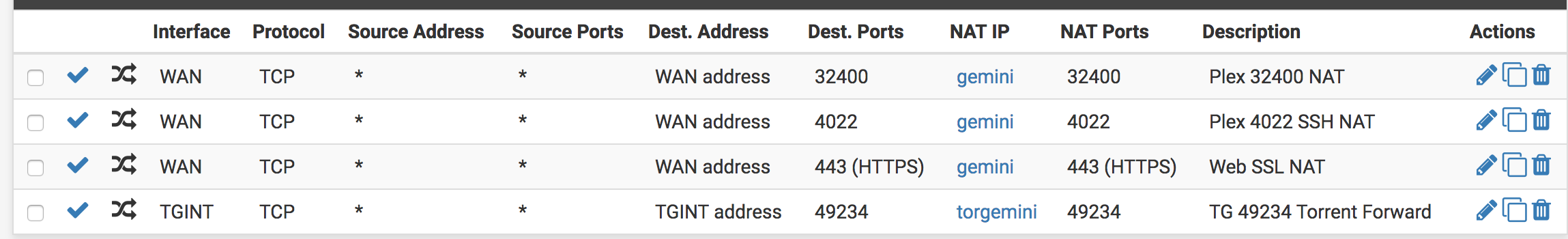
- Port forward setup on 49234 on the TGINT interface routing to a single machine on port 49234
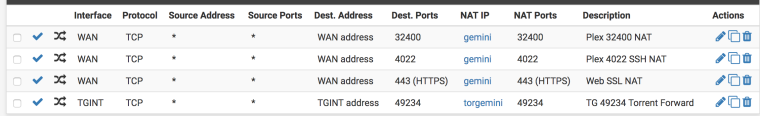
- Outbound NAT setup:
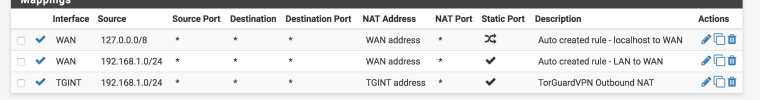
I have a test Google compute VM that I test from and everything works great:
felix@test:~$ telnet someip 49234
Trying somipe...
Connected to someip.
Escape character is '^]'.I can see the connections and all works superb.
I made a back of my working config. I went through and then configured a OpenVPN server, but as soon as I do that, my port forward stops working. I can see the traffic in the rules going through, but I get no connections established.
I can recreate it each time yet I'm not sure what I'm missing as I would like to have the OpenVPN Server setup as well so I can connect remotely in rather than using SSH.
Anyone hit similar issues or have suggestions of things to try?
-
I would be sure the traffic on the OpenVPN tab does not match the port forward traffic on the TGINT tab.
In fact, when you start using assigned interfaces on OpenVPN it is often a good practice to just delete/disable all the rules on the OpenVPN tab and assign interfaces to every OpenVPN instance and put the rules on those interfaces. If all you have is two instances, that is what I would suggest.
Else you need to avoid pass any/any/any on the OpenVPN tab so you don't match traffic that should be matched by the assigned interface rules.
-
Hmm. I will try to do some testing.
The only rule on my TGINT firewall is the port forward and nothing else.
For my LAN rules, I take an IP and instead of using the default gateway, I'm forwarding that over the TGGW. All my traffic goes out perfectly if I add or remove items.
The port forward breaks specifically when I create the Server VPN and only the 1194 WAN rule and the Outbound NAT portion.
I have no rules configured on the OpenVPN tab.
I'll try to assign an interface to the ServerVPN and go from there and see what that does.
I can see items coming in properly, but the going back out the right spot seems to be the problem but my routing seems to be ok from what I can tell:
Internet: Destination Gateway Flags Netif Expire default 100.20.56.1 UGS igb0 1.0.0.1 10.37.0.86 UGHS ovpnc1 10.37.0.85 link#9 UHS lo0 10.37.0.86 link#9 UH ovpnc1 100.20.56.0/24 link#1 U igb0 100.20.56.128 link#1 UHS lo0 127.0.0.1 link#6 UH lo0 192.168.1.0/24 link#2 U igb1 192.168.1.1 link#2 UHS lo0 [2.4.3-RELEASE][admin@phoenix.animosity.us]/root: netstat -rnfinet Routing tables After VPN Setup Internet: Destination Gateway Flags Netif Expire default 100.20.56.1 UGS igb0 1.0.0.1 10.37.0.86 UGHS ovpnc1 10.37.0.85 link#9 UHS lo0 10.37.0.86 link#9 UH ovpnc1 100.20.56.0/24 link#1 U igb0 100.20.56.128 link#1 UHS lo0 127.0.0.1 link#6 UH lo0 192.168.1.0/24 link#2 U igb1 192.168.1.1 link#2 UHS lo0 192.168.2.0/24 192.168.2.2 UGS ovpns2 192.168.2.1 link#10 UHS lo0 192.168.2.2 link#10 UH ovpns2 -
So I sent item by item and didn't allow the auto rules to be generated and recreated everything by hand taking your advice and making an interface for the HomeVPN.
Everything seems to be working now and I kept my port forward so I think somewhere along the way, the auto rules probably did something. I'm afraid to test as it's all working now.
Thanks for your help and the suggestion as it worked.
-
So one more oddity in the whole process.
If I reboot, the port forward stops working.
To get it working again, I simply just re-apply the firewall rules with no changes to them and it works again.
Is there a way to capture a before / after that would assist in figuring out why it isn't working on the reboot?