How do I monitor traffic requests via internal IP?
-
Hi,
I am looking to get a handle on what my 13 year old son might be browsing on the internet. I find browser history on the device tends to be removed.
Is there a way i can sort via IP/DNS what is happening on my network?
Ideally when he has friends over I would like to see by internal IP what sort of websites they are visiting (192.168.1.4 is going to facebook.com, reddit.com/r/pfsense, etc).
Thanks,
Rich -
The internal IP won't tell you a thing about where they're going. Even behind NAT, the destination is the real world address. The local IPs are only for the devices on your network. So, if you were going to, for example Google's DNS server, your outgoing packets would show 8.8.8.8 as the destination address with 192.168.1.4 as the source and those addresses would be reversed on incoming packets.
-
Is there a way with PFsense to see what internal IP is requesting outside data?
If IP 192.168.1.4 is requesting data from google.com, doesnt the PFsense box send that data back to 192.168.1.4?
My goal is primarily to see where each internal IP is requesting data from.
Sort of like this:
https://kb.netgear.com/24224/How-do-I-view-the-activity-logs-of-my-Nighthawk-routerItem 4 shows it can tell the date, internal IP, external IP requested,
Thanks,
Rich -
You can certainly use Packet Capture to find packets going to a specific address, but I don't really think that's the way to go. You want something that can identify when a TCP connection starts, get the destination address and then check it against a list of sites. The captured packet info will also identify the source. However, I expect this sort of thing is beyond the capabilities of pfSense, without some other package being installed. Perhaps a different way to approach this is to just block certain sites.
-
If you use OpenDNS server, they include DNS logging as part of a free account. That would at least tell you what domains are being used by your network.
There is commercial software available for the purpose you presented too.
-
Hi,
Added to all this : Keep in mind that all investigations related to this "how can I see what my kid sees" will be pointless the very moment you confront him with what you are doing.
In several weeks, months at most, your kid will use his favorite search engin - his school at least, a Google-look-alike at best - and he will find out what a VPN is (not where it stands for, neither how it works) and he'll be using it.
You'll be seeing nothing and he has the entire net at his disposal.I had to deal with this situations twice in my live, and what finally worked best : a hidden "screenshot taker" (every 5 seconds or so). When they slept (this was the hard part) , I snatched the device and made up my list ... I gave them normally 50 € a month, and for every no-no site it would become 1 € less.
My kids owe me a couple of k€ these days - and they still never found out what hit them.
Btw : this solution also works when they are not @ home. -
Gertjan makes some valid points.. And might be the best solution for teenage boys and their skills at circumvention ;) ie if you have notice the browser history deleted they have already found one method of hiding.. They prob also know about private browsing, etc.
You could log with your dns for sure - but you would be amazed at how many dns queries get made..You could use something like pihole in conjunction to log/block bad sites. Pfblocker can also block but not sure how well it logs. While pihole gui interface is very slick and user friendly on getting a handle what IP is making queries, how many - what is the top queried fqdn, what is the top blocked, which IP is doing the most, etc. etc.
-
I missed one point : back in the old days kids didn't have smartphones.
-
Another reason to do this. Chatty devices. Sonos or Roku for example.
I'd leave it to others to discuss if tracking your kids on-line activities is good/bad/effective.
I, also, just recently switched to pfSense from another gateway solution. I used a Pi-Hole in combination with Unbound to filter and then hide (DNS over TLS) dns queries from my ISP. It worked very well, if not a little slow at times on a Raspberry Pi.
pfblockerNG is terrific. What isn't there, that I do miss from Pi-Hole, is the ability to quickly glance at what DNS lookups a device is doing. That's an unbound thing, not a pfblockerNG thing I'm guessing. I have had a quick look at the unbound.conf man page and nothing jumped out as a setting to simply log requests. I have turned logging up to "5" and looked, quickly, through the log. It appears that all the information is there but it would take a real effort to put it all together. DNS is UDP, so the order of requests and responses are all over the place.
A quick web search gave me some tools to "paw" through unbound logs, but nothing I was really excited about. I did see dnstap, looks interesting and I wonder if the Pfsense team would be interested in that at some point down the line.
Right now I have a list of hosts to block from my Pi-Hole usage that I use in PfblockerNG. That list will get stale pretty fast. It's frightening the number of hosts I can block and my devices continue to function normally, updating occasionally and doing what I paid for.
I may just put my Pi-Hole back in service, send clients to it via DHCP(v6) and then forward those requests to the pfsense gateway for unbound to handle.
-
What generation of pi you run hole on? I have it on 3 and just screams - not notice any sort of slowdown at all. I then forward it to pfsense so unbound can resolve it.. Not a fan of forwarding my dns to anywhere.. I will resolve thank you very much ;)
Other option is you can just run pi-hole on some VM.. Be toying with moving it to my nas on a vm - but have the pi laying around not doing much of anything - so it makes good use running pihole..
And yes the web interface to pihole is very slick is looking up info, blocking it, etc etc.. Great for tracking what those iot devices are wanting to look up.. Freaking roku's really want to find... logged based fqdn..
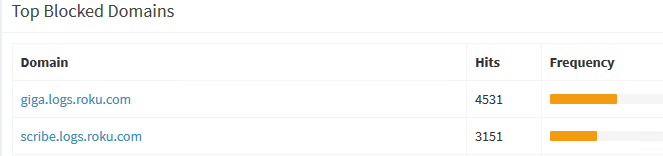
They work fine not being able to resolve them..
-
I was/will soon be using a 3B+. The performance hit was from unbound not dnsmasq and the Pi-Hole stuff. I'll set it up as a pure Pi-Hole when I have a moment. Should be good to go with the new v4 pi-hole release. Just ordered a PoE Hat for it, waited forever to find one in stock. One less power block in the rack :).
I finally gave up on Roku, the ads and the tracking are happening on the same connection as the content. Just disconnected the TcL Roku TV from my network and use an Apple TV now. Less chatty, possibly more trust worthy... That's the hope anyhow...
Look forward to other active or passive DNS monitoring solutions that someone more experienced than I may propose. I do like the all on one box aspect of pfSense.
-
I have been running unbound since before it was part of pfsense and an just an addon package - have never seen a hit from it.. It is rock solid in its performance - then again as I mentioned I would never "forward" my dns request I use it as intended which as a caching resolver..
If your concerned with your isp listening in on your dns - then send your dns requests through a vpn would be my suggestion. Trying to run dns over tcp so you can put it in a ssl tunnel is yeah going to be a performance hit on your typical dns udp query.