Pfsense Port Forwarding issue behind Uverse Modem
-
Good Day all!
I made sure to check the information below first before posting:
https://forum.netgate.com/topic/6225/port-forward-troubleshootingI know its probably something simple, at least I hope it is. I am new to the whole PFsense thing in regards to running the system behind a POS Att Uverse fiber gateway, but any way i am stumped in the sense for port forwarding some ports. I wanted to start off by just adding a simple RDP(3389) before adding any other ports for forwarding to allow external access to a desktop from my work location, but I can not for the life of me get this port forwarding to work. It was not a problem when I had my spectrum router and was able to put it into bridge mode the simple way, but ATT F**ks that up for you.
My Setup is as follows:
Arris NVG599 router(SUbnet changed to 192.168.2.254)----> PFSENSE Router
(PFsense Gateway 192.168.2.88
PFsense LAN 192.168.1.0/24)---> Desktop(192.168.1.55)
I have placed the PFsense router in IP Passthrough in the NVG firewall to allow all traffic to my pfsense box.The gateway info is below:
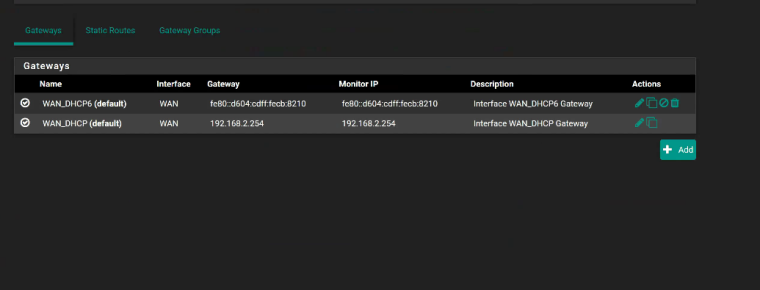
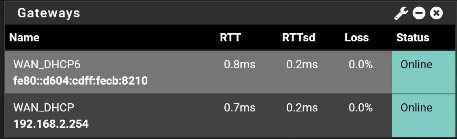
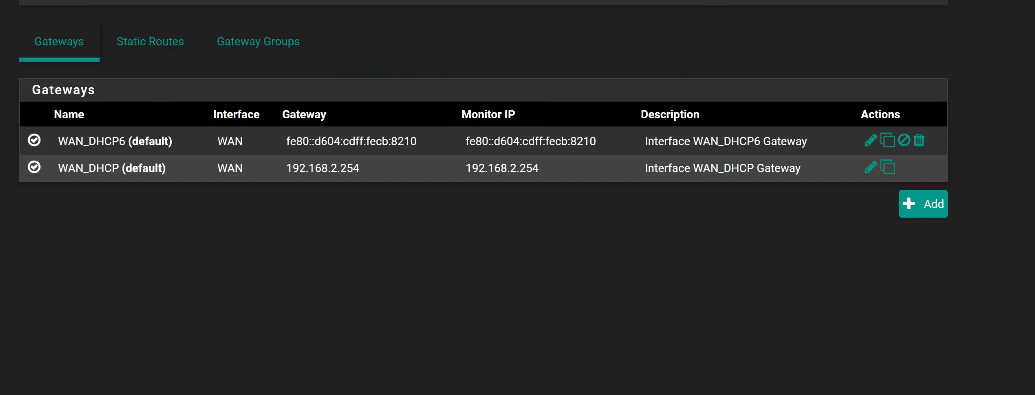
IPV4 Gateway-
NAT:
On Advanced---> Routing---->Firewall and NAT:
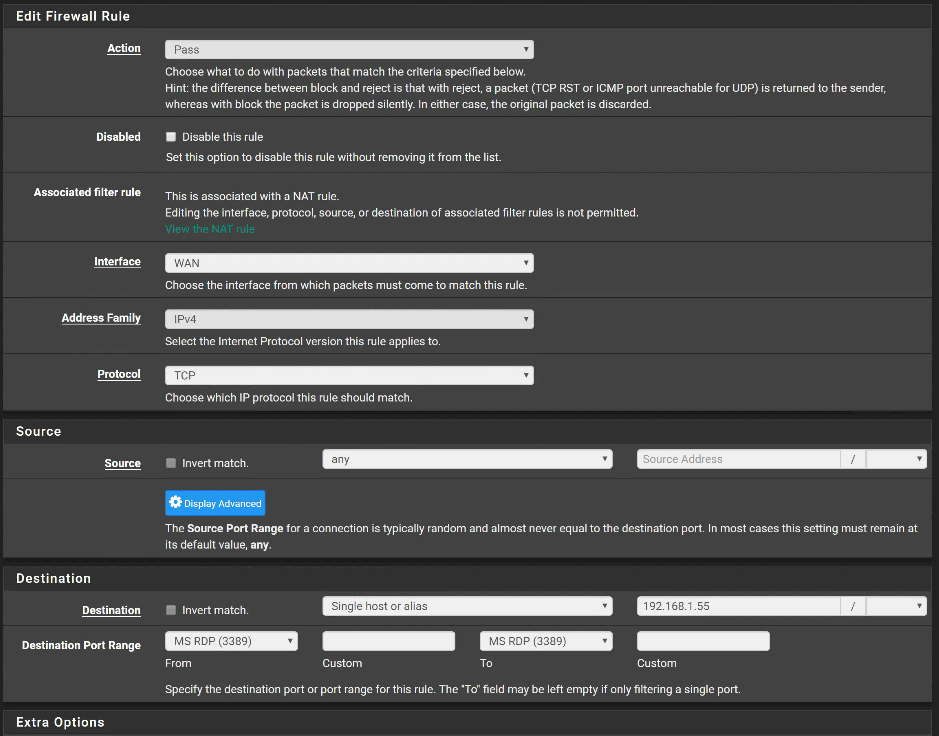
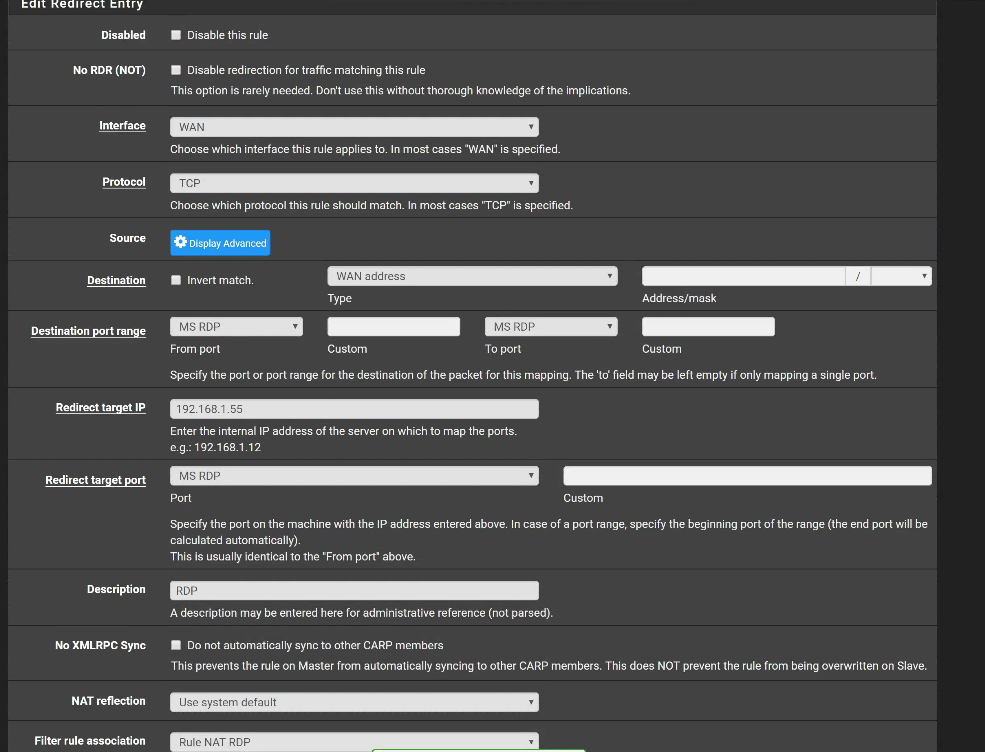
Firewall>NAT>Port Forward Rule:
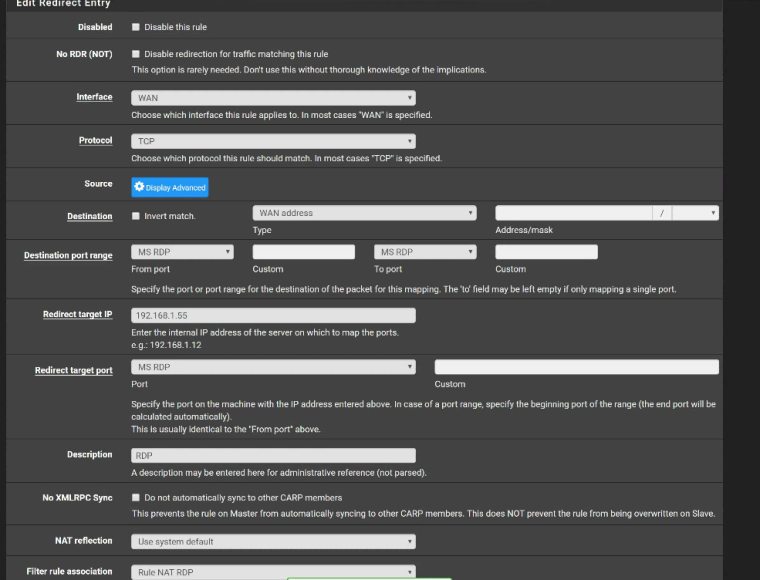
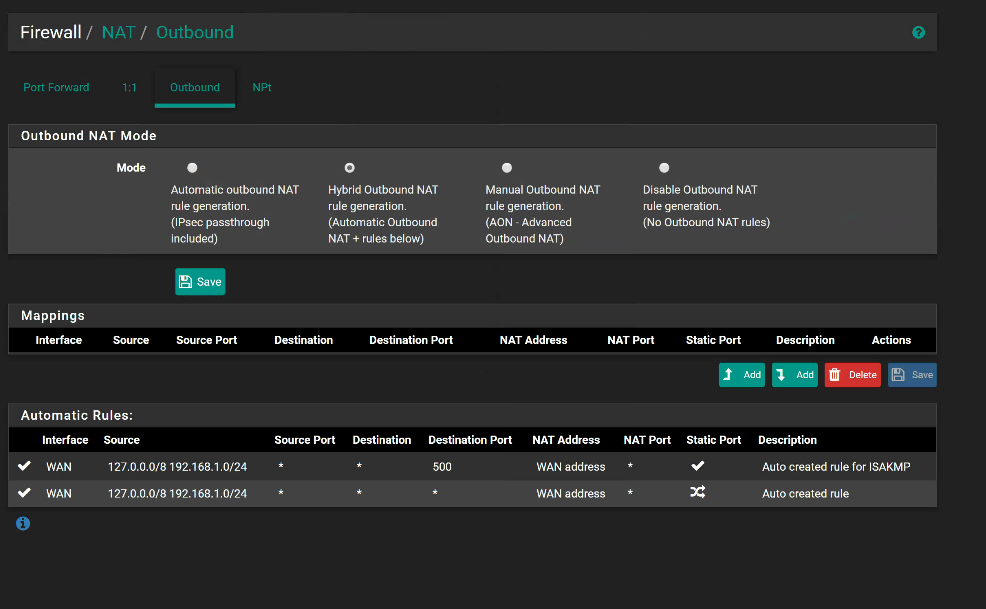
NAT Outbound:
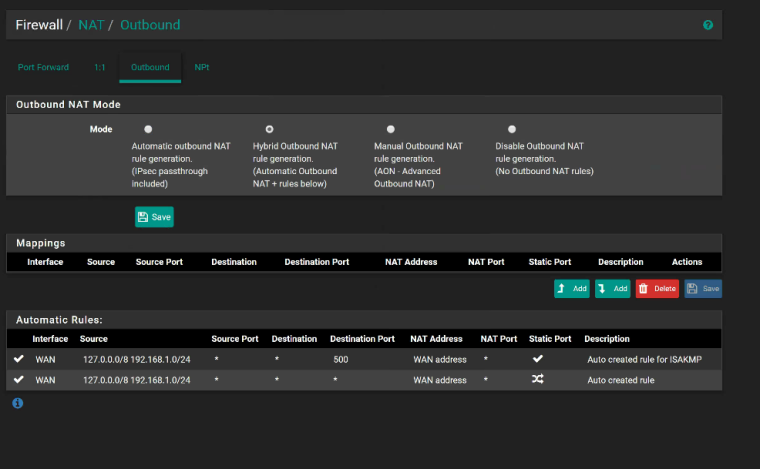
Firewall>Rule:
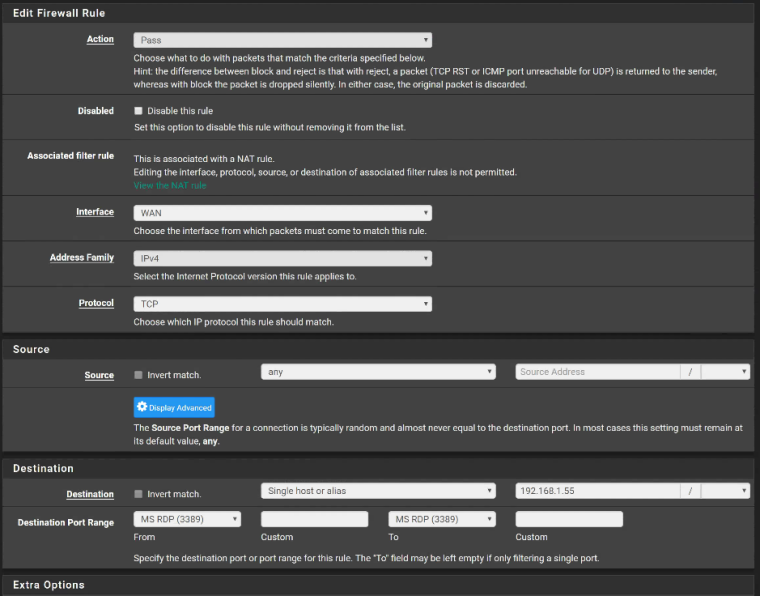
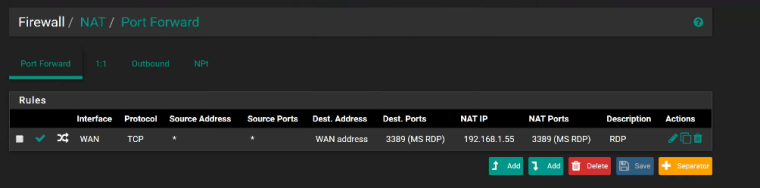
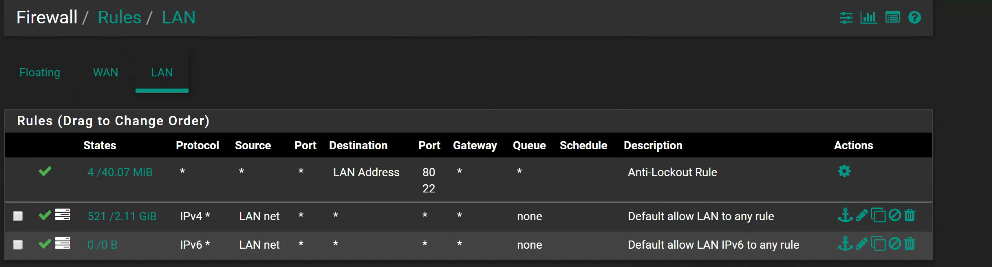
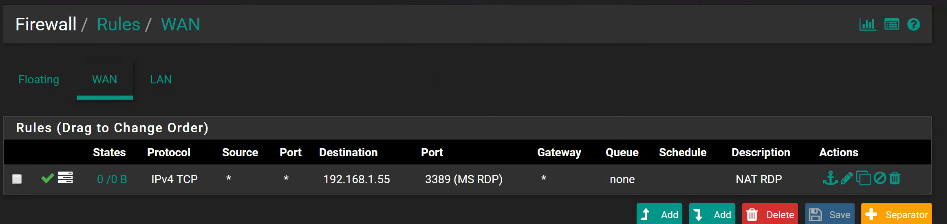
Rules:
WAN:
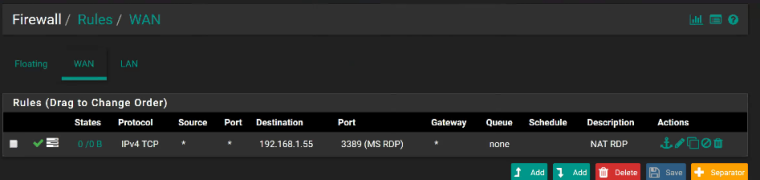
LAN:
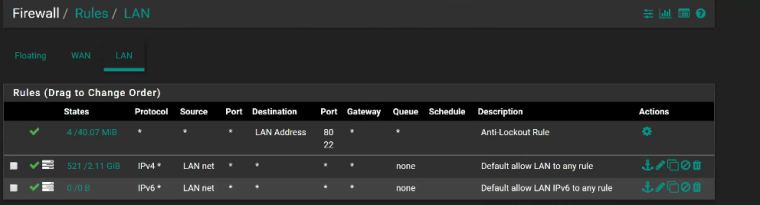
I am wondering if something is either incorrect with the gateway or with the NATTing. I am able to get out to the world and ping out but I can not get the external to internal port checks to work either.
Like I said this was not an issue when I had my first router in bridge mode, just when we switched to Uverse fiber after relocating. Any assistance would surely be appreciated and thanks in advance. Let me know if I need to provide anything else.
-
@cewjr9842 said in Pfsense Port Forwarding issue behind Uverse Modem:
Good Day all!
I made sure to check the information below first before posting:
https://forum.netgate.com/topic/6225/port-forward-troubleshootingSo what did the packet captures show, does the traffic arrive at the pfSense WAN interface, does it leave the LAN interface? If you followed the docs you should be able to answer this.
-
To be honest first step in troubleshooting is validating that traffic actually gets to pfsense WAN.. Simple packet capture while you try and access that port from remote. canyouseeme org is good site for testing this.
If you validate traffic is getting to you - and still not working.. Sniff on lan - does pfsense send it on to the IP you want to send it too, ie this 192.168.1.55 address..
If so and you get no response then problem on client - firewall on client. Windows out of the box sure and the hell not going to allow for rdp from some public IP address. Is the the service actually running and listening..
All of these troubleshooting steps are gone over in the doc you listed..
Your not trying to test this port forward from a device on your 192.168.1 network are you? That would be a nat reflection and whole different ball of wax to why it might not be working.
A quick glance at your forward and your rules look ok - so my take would be upstream either your isp, your router or where your testing from is blocking 3389? Its not a very good idea to open 3389 to the public internet btw..
There was a recent thread where person was troubleshooting port forwarding - and from simple sniff (packet capture) in diag menu of pfsense it was clear the device he was trying to forward to was sending back RST which is why it was not working.. pfsense port forwarding was fine.
Also btw rdp can use both tcp and udp..
-
Sorry I Left all that out, on what I did last night while troubleshooting.
I did use canyouseeme and ran a packet capture and for some reason I did not get any information on the packet capture to my wan. :Error: I could not see your service on WAN on port (3389)
I also ran it using Network Port Checker & Scanner Tool
and got the results below: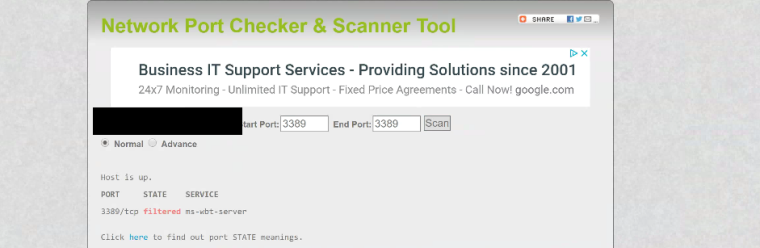
-
@johnpoz Like I was telling grim, i did try to do a external capture using
canyousee me and also a network tool checker and got the results below: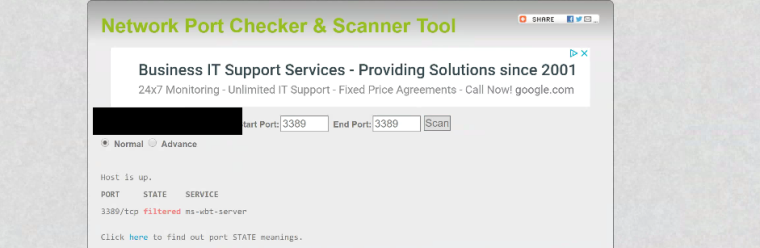
When I try the packet capture on the LAN i get information going out to the interweb.
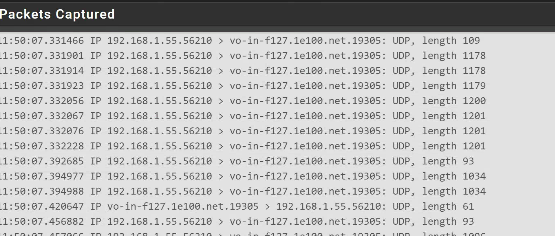
When I was testing outbound I was testing from my work PC at another location to my routers firewall, as well as my android phone not connected to my network. it still is a fail.
Also on the rule aspect I did try touse 3389 for RDP rule using TCP and UDP but still neither would work. Im stumped at this point because it should not be this difficult as i never had issues before. -
Well if your packet capture shows no matching incoming traffic on the WAN then the problem is upstream of pfSense. Either your "modem" (which is actually a nat gateway) is not forwarding the packets or your provider is blocking the port.
-
@grimson understood. I just checked again, and yep, i am not getting any thing when trying to point to my WAN. Im trying to Wireshark now to see if I can at least see if it matches what I an seeing in pfsense packet capture right now.
-
@Grimson @johnpoz Now i'm going to tell you something that is dumb as hell. So since i put my router in IP pass through for my pfsense something told me to try and add RDP port 3389 to the uverse modem and try allow it to my pfsense IP address and it works now, which is stupid to me honestly. I thought IP pass-through was to allow all traffic to a particular address and to not block it at all. this makes literally no sense at all. SO i have to add ports to the uverse modem and ports to the pfsense box to allow any external access. Once again I hate at&t with a passion!! Is this something I can bypass or am I stuck with this dumb ass solution?
-
@cewjr9842 said in Pfsense Port Forwarding issue behind Uverse Modem:
Once again I hate at&t with a passion!! Is this something I can bypass or am I stuck with this dumb ass solution?Some light reading for you.
http://www.dslreports.com/forum/r29903721-AT-T-Residential-Gateway-Bypass-True-bridge-mode -
@chpalmer I wish it was that possible, since I have Internet and TV with them.
I would definitely do it if i only had internet. -
Just as a suggestion.. And while this is ofcourse "Security through obscurity", at least use a different random port on the WAN side, and then forward that to local 3389. Then when connecting just specify the port number "rdpserver.FQDN.net:12345" or "127.213.12.123:12345", etc.
Of course the best option is set up a VPN and lock off RDP from WAN. But at the very least it keeps the bots away for the most part.
Or add an additional port for RDP to use locally via REGEDIT (it can have more than one). either way you can use the default/3389 on LAN and the new port for remote.
And to add, I also despise AT&Ts forced gateways. One reason they are always on the bottom of my list of ISPs.
-
@napsterbater Thanks napsterbater. I was just trying to RDP/3389 as my first step to testing port forwarding on the pfsense router before adding any other ports but I didn't know that at&t was so sh***y to the point where they would block a passthrough/supposed DMZ'ed IP address to allow all items to that one address, but I should have known better. I wish another ISP was available in my location, i would leave them with the quickness. But to have to add port forwarding in my pfsense and then port forwarding in the Uverse gateway, is ludicrous and makes no sense for a DMZ'ed address. Thanks again fro the suggestion and I appreciate you alls time and help on this!