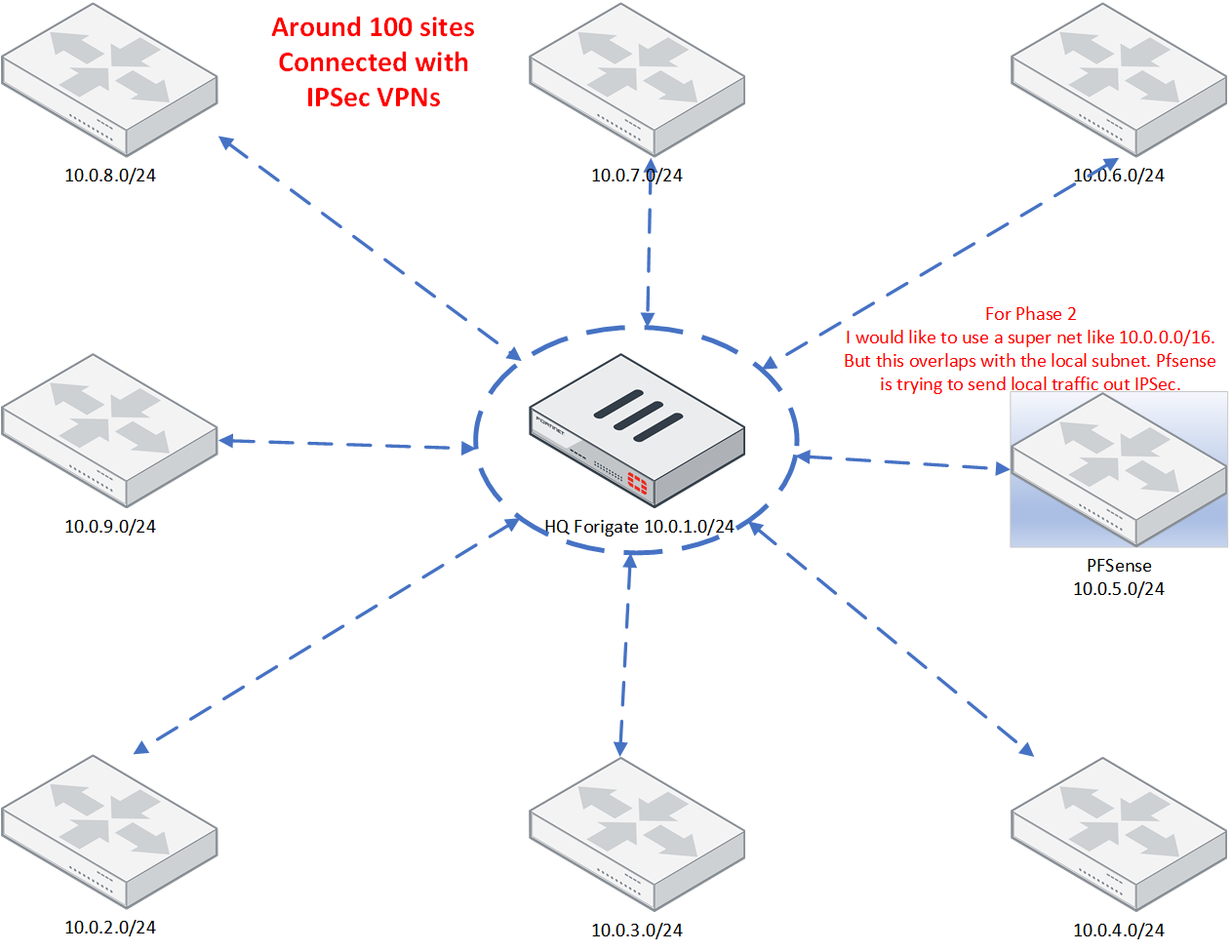
PFSense IPSec with phase 2 remote subnet overlaps local subnet.
-
I'm trying to integrate my pfSense into a larger network via IPSec VPN. The network is a hub and spoke configuration. My router is one of the spokes and the remote site (hub) is a Fortinet Fortigate, therefore I have to use IPSec. The attached image is an oversimplified representation of the network since there are a lot of sites and multiple subnets per site. The problem is I'm trying to avoid creating a lot of phase 2's. In other firewalls I've used, you can use a supernet (example a /16) in the phase 2 for the remote network. This will in this example send 10.0.anything.anything up the IPSec and let the hub router handle the routing between sites. But since the local LAN falls within that /16, the PFSense is actually sending local traffic to the IPSec, rather than it recognizing that that subnet belongs to a local interface. Is there a way to handle this using IPSec without building a bunch of phase 2's that do not overlap with the local subnets?
Thanks in advance :)
-
The firewall should bypass the LAN network there, but it will only work if 10.0.5.0/24 is on LAN, not an OPT or secondary interface. LAN must be the second defined interface. In Status > Interfaces the internal name will be lan. As in LAN Interface (lan, igb1.223)
You must also not uncheck Enable bypass for LAN interface IP in the advanced IPsec settings. That must be enabled.
-
This post is deleted! -
Ahh.. Got it. But I have 7 interfaces LAN I have to apply this to, not just one. In the pfSense website, I found Bug 5826 that describes the problem I'm having. https://redmine.pfsense.org/issues/5826 . I'll do some research to see if I get into the strongSwan config if I might be able to do this for multiple interfaces manually.
Thanks again for the help. I never noticed the Auto-exclude LAN address feature in IPSec.