Is this the *proper* PfSense/Pi-Hole setup?
-
Hi
I am trying to set up the proper pi-hole configuration in my PfSense install.
I found various posts across the net, but each had a somewhat different approach (PfSense to Pi-hole, disabling resolver/forwarder, etc).The one that made the most sense to me was in these forums: a year old posts by @johnpoz in response to a user asking the same question.
I basically have a few VLANs and would like all of them to query pi-hole first, then move on to Cloudflare (1.1.1.1).
-
My pfSense box is at 192.168.1.1
-
My pi-hole is at 192.168.20.3
The original posts by @johnpoz are here below:
So, if I followed these instructions correctly, I configured the following settings:
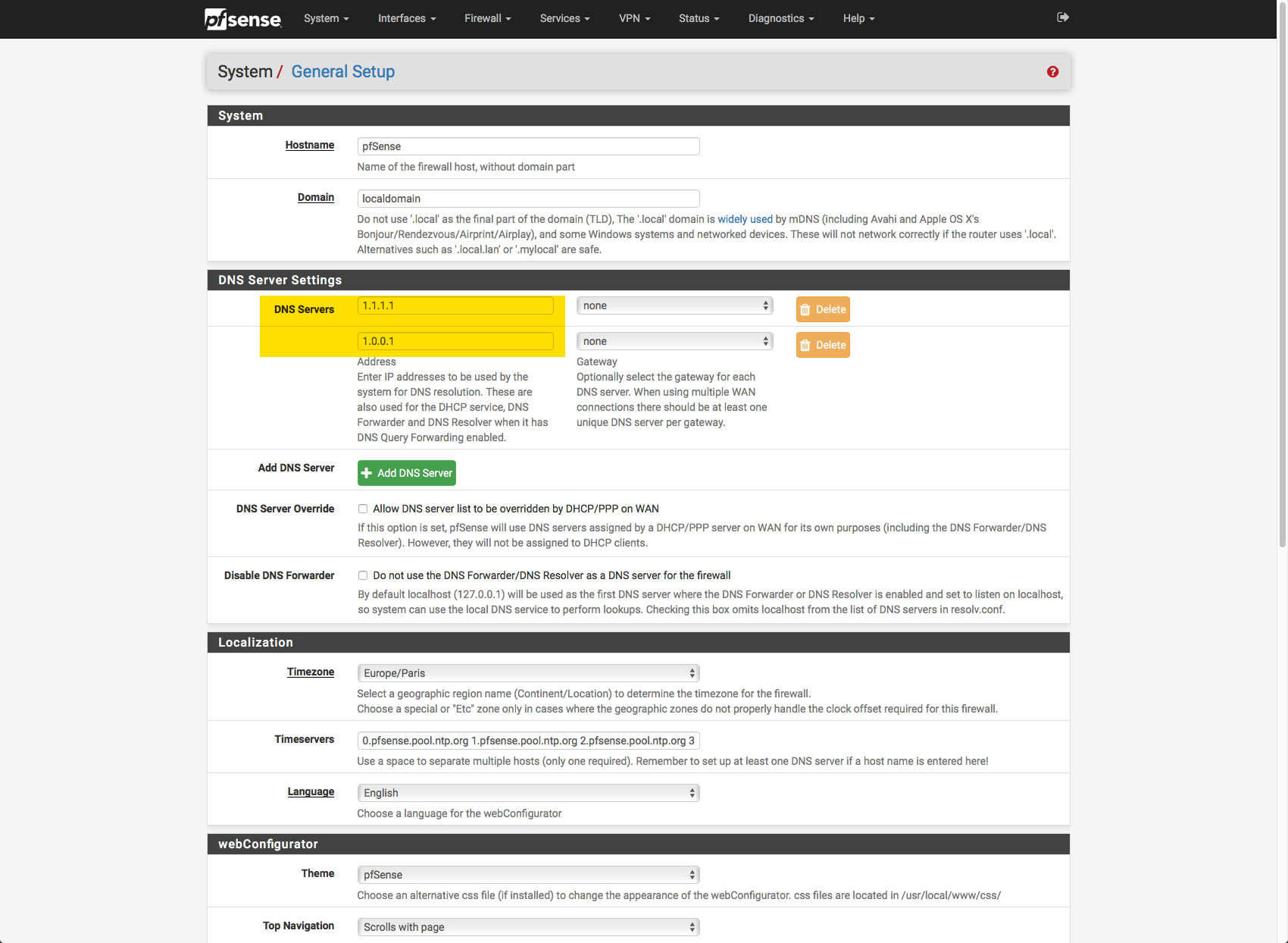
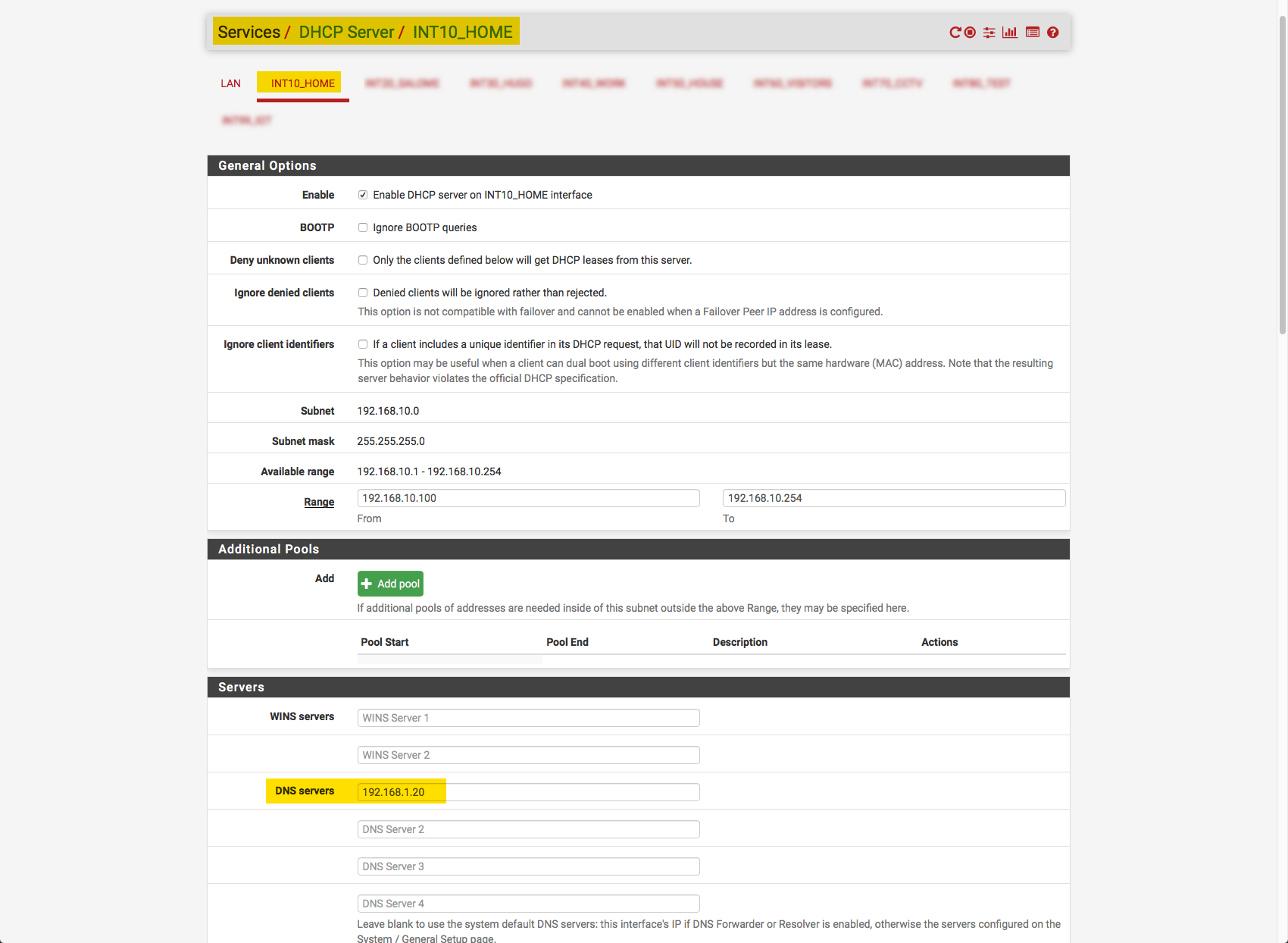
1/ For each VLAN I point to the pi-hole in the DNS setting:
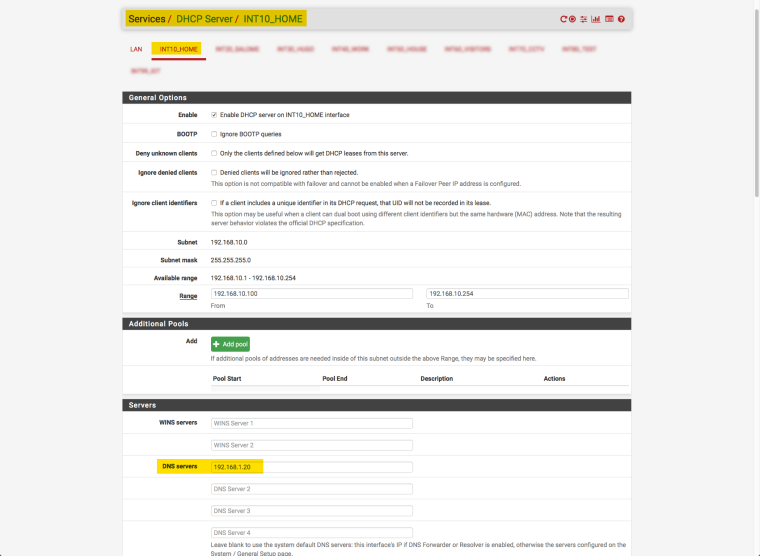
2/ In the firewall settings (NAT/Port forward), I force all DNS queries to go to my pi-hole to avoid DNS bypasses
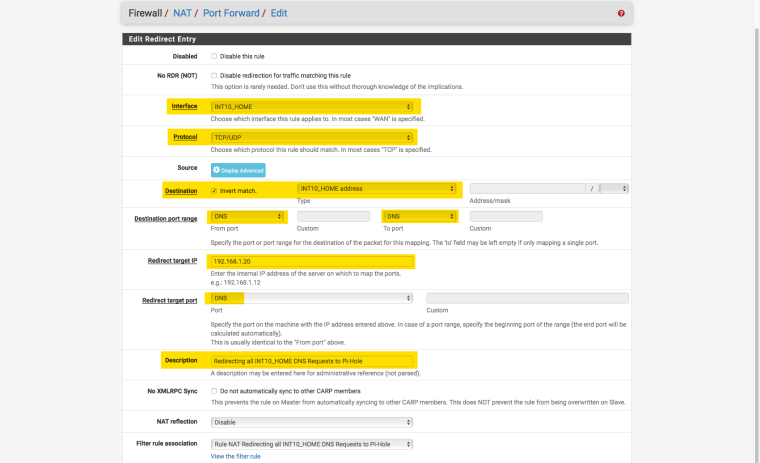
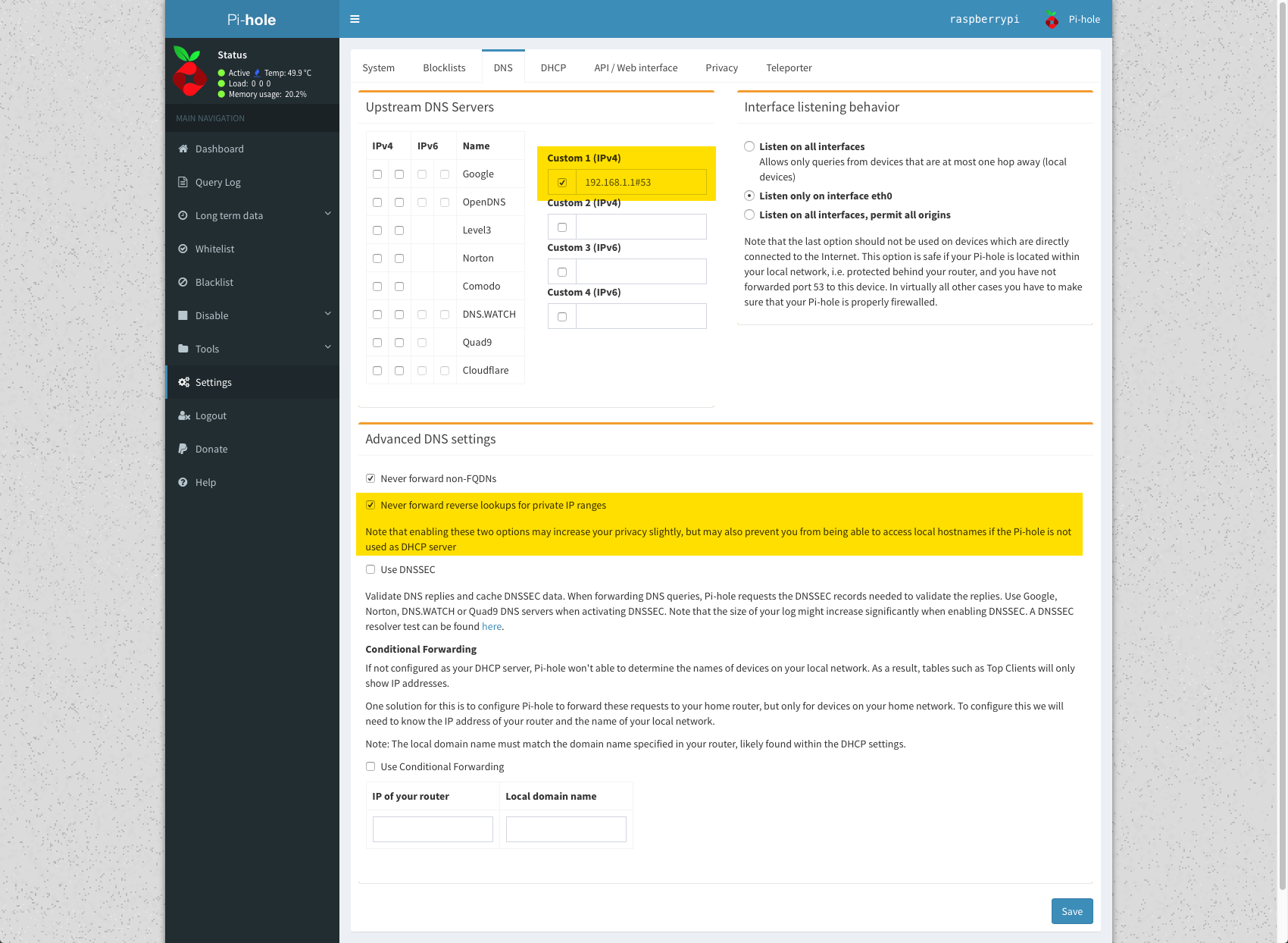
3/ In my pi-hole, I point to my PfSense box at 192.168.1.1
The "Never forward reverse lookups for private IP ranges" is ticked by default. Should I untick this?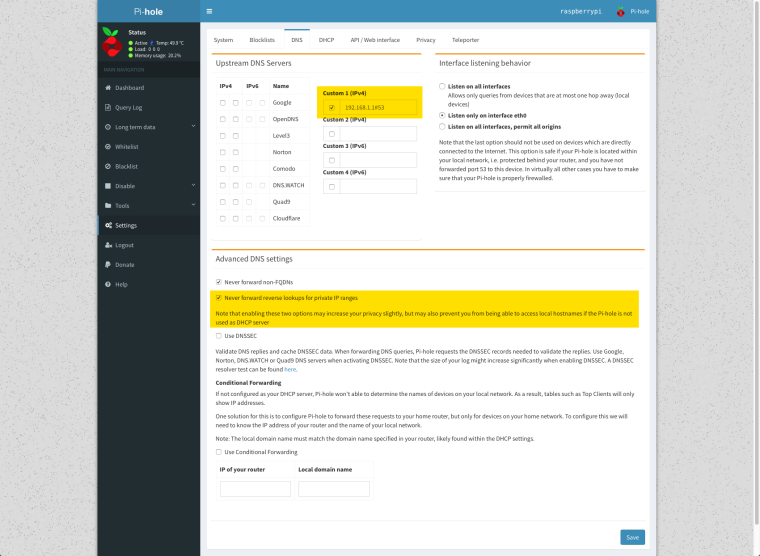
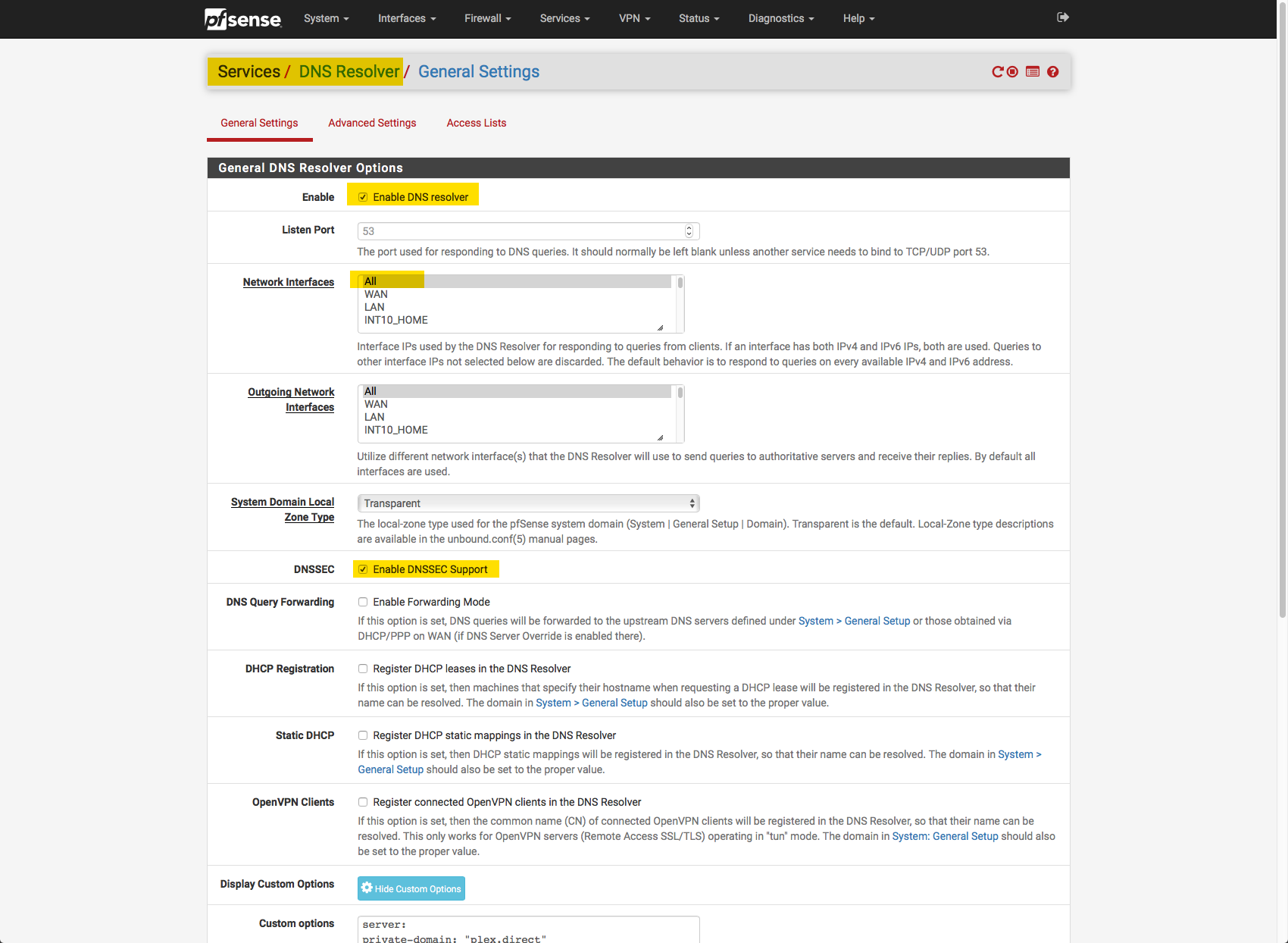
4/ My PfSense DNS Resolver is configured as follows:
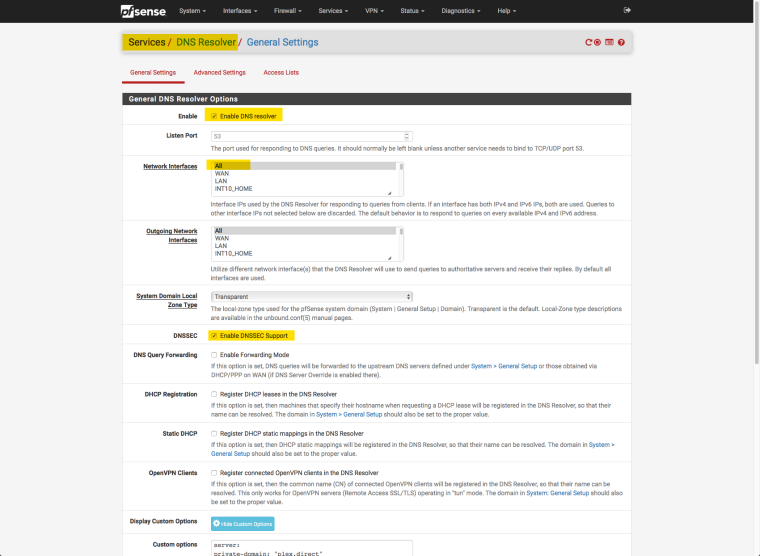
5/ My PfSense General Settings finally point to the Clouflare servers (1.1.1.1):
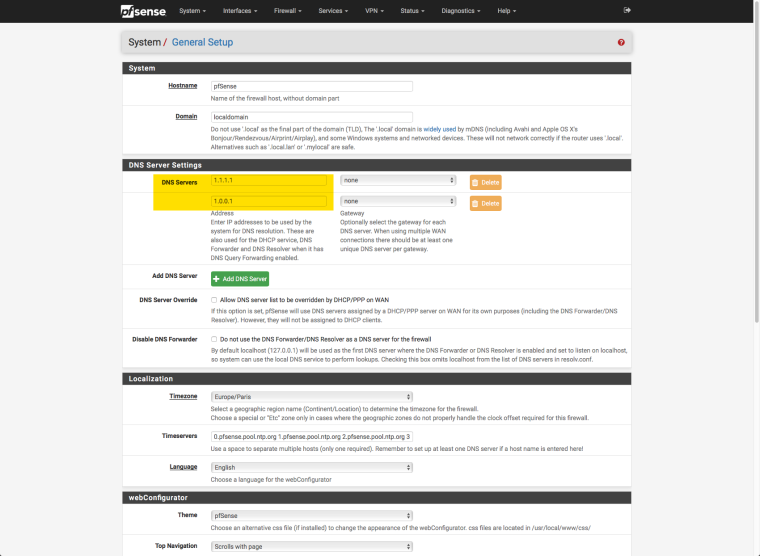
Is this the right way to configure things? Did I miss any setting?
Many thanks in advance for any feedback :)
-
-
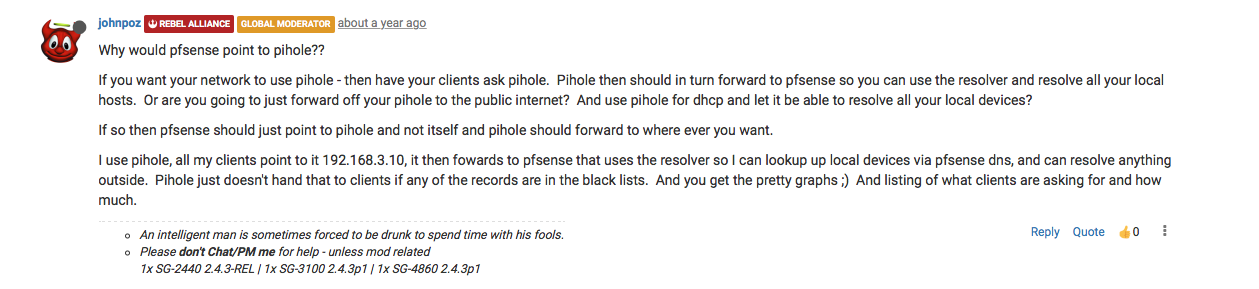
If you never forward rfc1918 ptr then you will not be able to do ptr on your local devices that pfsense holds records for. So you should prob untick that - I have it ticked so I can do a ptr query on say 192.168.9.100...
5 - not sure the point of that.. You don't want pfsense to resolve local stuff? So in your firewall rules when it blocks say 192.168.9.100 you don't want it to be able to resolve that?
Pfsense should point to itself for dns.. ie 127.0.0.1.. If you want to use cloudflare vs resolve - then you would set that up in unbound - have it forward vs resolve. Pfsense would still point to itself..
C:\>dig -x 192.168.9.100 ; <<>> DiG 9.12.2 <<>> -x 192.168.9.100 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 46680 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;100.9.168.192.in-addr.arpa. IN PTR ;; ANSWER SECTION: 100.9.168.192.in-addr.arpa. 3019 IN PTR i5-win.local.lan. ;; Query time: 18 msec ;; SERVER: 192.168.3.10#53(192.168.3.10) ;; WHEN: Fri Aug 31 10:01:20 Central Daylight Time 2018 ;; MSG SIZE rcvd: 85 -
Hi @johnpoz
Many thanks for the quick reply :)
Tbh, I think I'm barely scratching the surface of my DNS understanding, so apologies if I ask for some more clarifications:
1/ In the Pi-Hole config (3. screenshot here above) should I untick both these options?
- Never forward non-FQDNs
- Never forward reverse lookups for private IP ranges
Would this allow pPi-Hole to "convert" the local network IP addresses shown in all the stats into host names I defined for all my devices in the PfSense DHCP server (I assigned all my devices fixed IPs and host names)
2/ To be honest I thought Resolve and Cloudflare were complementary, not a matter of one vs the other. While I do some more reading about this, would you please be able to tell me what settings/values exactly I need to change based on my screenshots above?
E.g. looking at the Resolver settings for instance, it seems to me I should check the 'Static DHCP' setting as well.I greatly appreciate any additional help you can provide on this :)
-
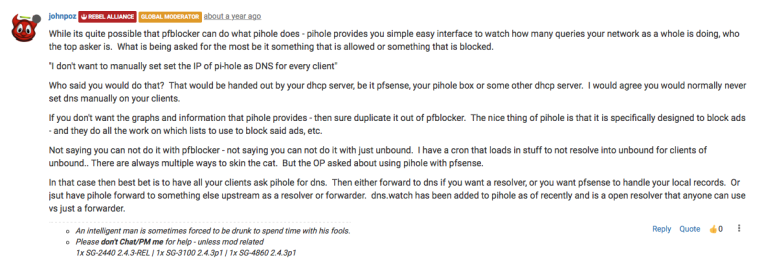
There is never a reason to forward non-FQDNs.. Unbound not going to resolve them either, and public dns not going to resolve.. No actual valid NS should resolve a nonFQDN.. So zero reason to forward those..
Well take that back if you forwarding to something that would/could resolve nonFQDN - that is when you would want to forward them upstream. But no in any sort of sane configuration you wouldn't forward those.
As to the reverse - if you were forwarding to public ns, then no you would never forward those. But in your case what you will be forwarding to pfsense and pfsense will resolve your local stuff.. Then yes you would want to forward that to pfsense, so uncheck that one.
If your setting up all yoru devices as dhcp reservations, ie static - then sure in unbound have it register your static stuff.
2/ - no resolver and cloudflare are NOT complementary... You either resolve or you forward, you normally do not do both. The only time you would would be in say a domain override situation where you have a local or specific NS that is authoritative for a non pubic domain... Lets call it domain.privatetld - in such a case then you would be "forwarding" to that vs resolving.. But its a conditional forwarder.