I need HELP on DNS RESOLVER!
-
Hi,
@emirefek said in I need HELP on DNS RESOLVER!:
I was blocked all dns server in lan side. I was allow only pfsense box to getting dns. Because I use pfBlocker on box.
For the blocking part, I guess you over-did something.
"dig" told you that "no servers could be reached", that includes your DNS server (unbound) on pfSense.
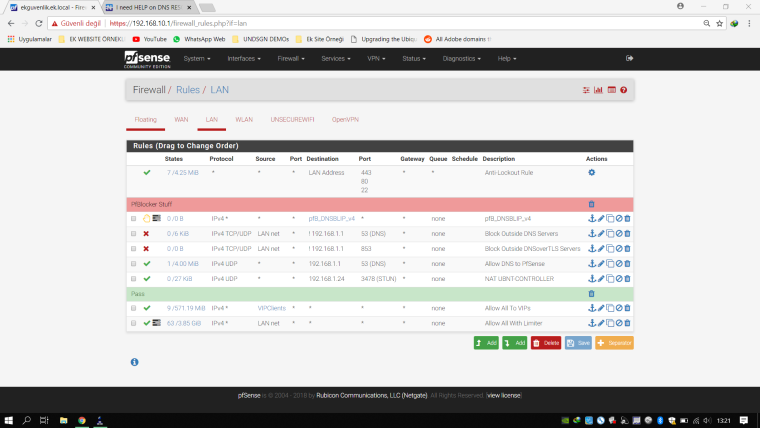
So, start with the basic tests : pfSense DNS (unbound) is reachable on port 53 of the LAN and WLAN interface ? service is running ? Firewall rules ok ? Remember : on the LAN interface there is a pass-all rule that permits all traffic coming in, on an extra OPTx interface like WLAN you should put in some useful rules, otherwise all is blocked. Please show your rules on both interfaces.Are you sure your RedHat (centos ?) box uses pfSense as its DNS ?
On systems like Windows and Linux devices, using the command nslookup shows right away which DNS it is going to use, this should be your pfSense IP.
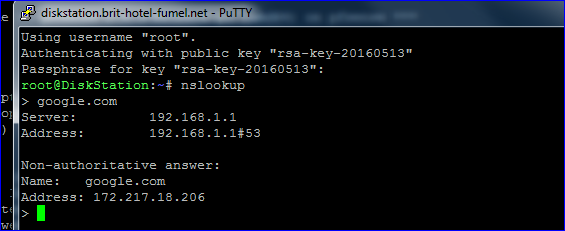
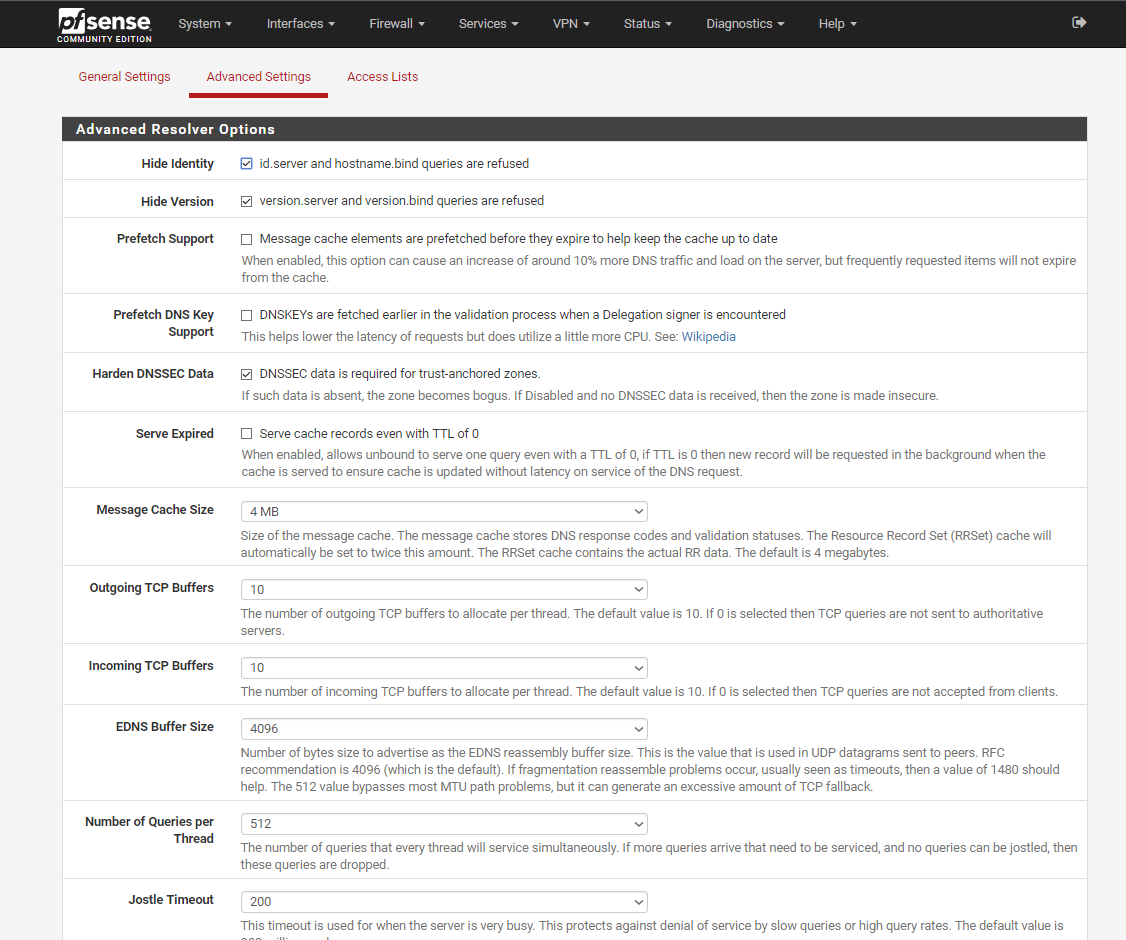
edit : the first image : the IPv6 shown is my LAN IPv6 IP.
-
Thanks for response @Gertjan . Im sure Centos taking dns from pfsense box. And unbound is reachable to all interfaces I will add screenshots of rules. Service is running. And no crash errors. Im adding screenshots you need.
Windows Machine(on screenshots) is on WLAN interface IP range diffrent from Centos Server.
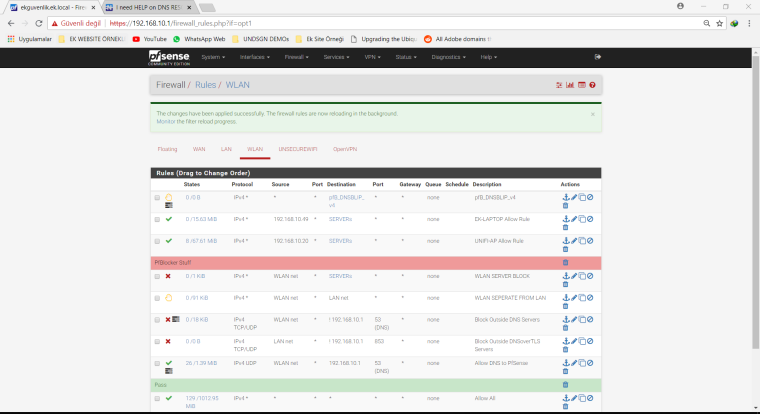
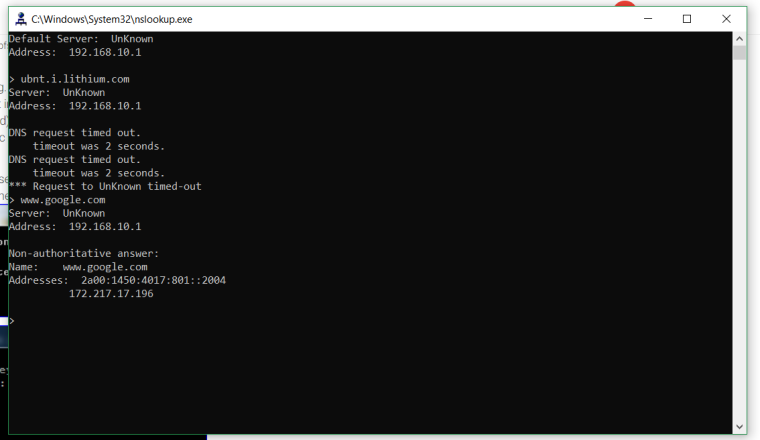
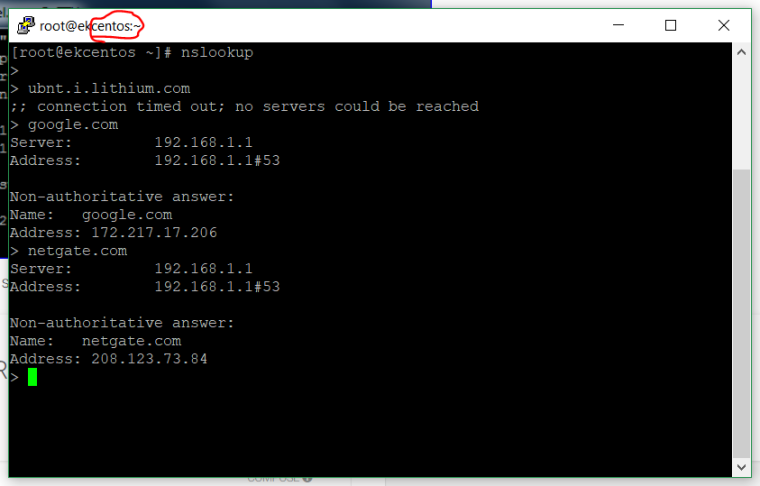
EDIT: @Gertjan If can you reach me with PM you can look box with remote desktop?
-
you sure dns is running on 192.168.1.1, doesn't look like anything can talk to it on dns.. Can you ping it?
BTW your rules don't make a lot of sense.. Rules are evaluated top down, first rule to trigger wins, no other rules evaluated. Its pointless to allow something (unless your going to log it) above a rule that is any any.. Is just a rule that makes no sense..
Do you have downstream networks connected to your lan? If so then you going to prob run into a asymmetrical routing problem as well.. Unless that downstream router NATS.. If so then allowing * as source vs lan net doesn't make a lot of sense either...
-
Thanks for response @johnpoz DNS Server is on pfsense(unbound) I was share my dns resolver setting on first post(as screenshot). I have 1 WAN and 2 LAN one of them LAN other is WLAN no failover WANs. I know how to work with rules they will drop states one by one. And Allow any any Is for logging bottom of all rules. And I was change "Lan Net" to "any" thanks for suggest. But nothing fixed. I was try disable all rules and nothing fixed again.
-
Oh I see now your getting cached replies from 192.168.1.1, so you can talk to it and it does answer but its not resolving that fqdn..
user@uc:~$ dig ubnt.i.lithium.com
; <<>> DiG 9.10.3-P4-Ubuntu <<>> ubnt.i.lithium.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 42571
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;ubnt.i.lithium.com. IN A;; ANSWER SECTION:
ubnt.i.lithium.com. 0 IN CNAME cs71.wac.edgecastcdn.net.
cs71.wac.edgecastcdn.net. 0 IN A 72.21.91.97;; Query time: 2 msec
;; SERVER: 192.168.3.10#53(192.168.3.10)
;; WHEN: Mon Sep 03 06:56:53 CDT 2018
;; MSG SIZE rcvd: 101That is a cname, so would would have to be resolved - what does diag dns lookup on pfsense show you?
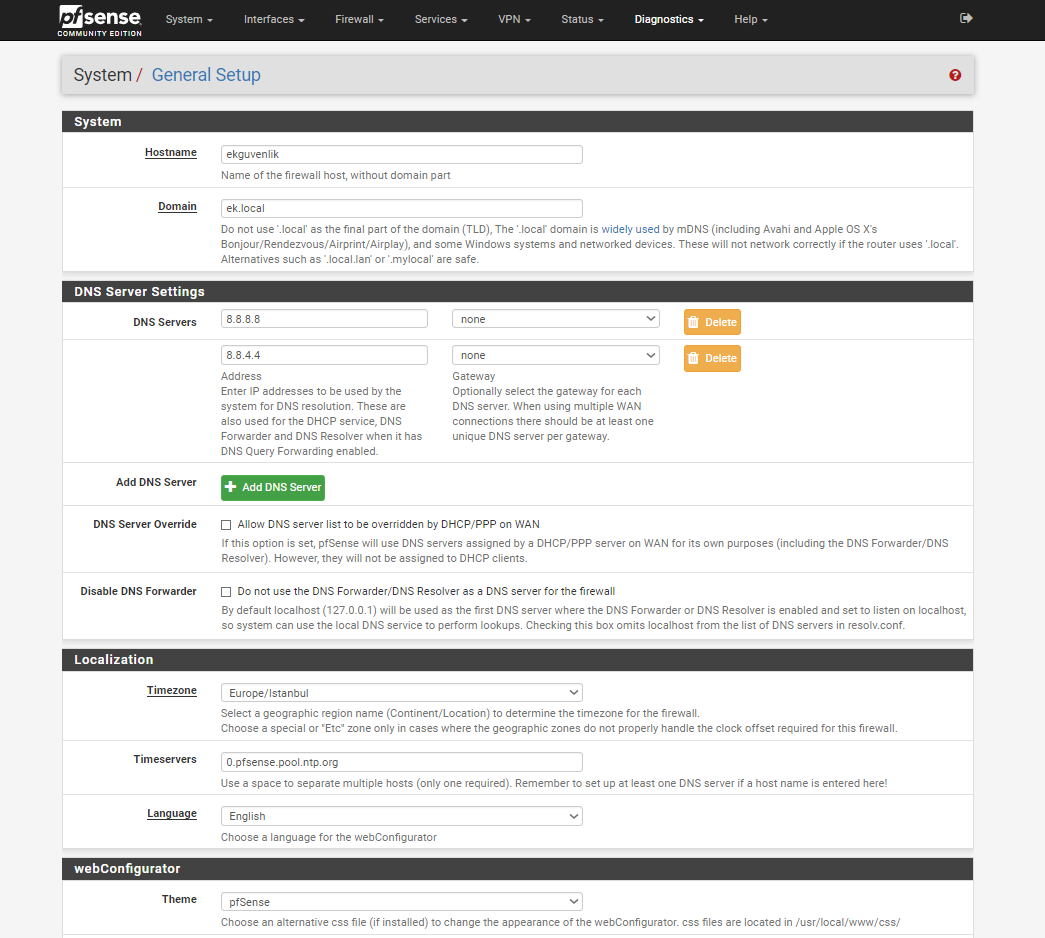
Why do you have google dns listed in your general setup if your using resolver? Make ZERO sense to do that! If your going to resolve then really pfsense should only point to itself, loopback
-
@johnpoz thanks for suggest I was delete all dns sources on general setup. And after that I did full pfsense box reboot. And I run dig command again and it shows another output now Im gonna share it with you. LAN and WAN cannot solve ubnt.i.lithium.com but Pfsense box can solve it. Before adding screenshots. I'm giving dns resolver settings.
Network Interfaces: LAN - WLAN - LocalHost
Outgoing Interface: WAN - Localhost
other settings are same with first screenshots.Dig command on centos, nslookup on win10 and pfsense box dns lookup:
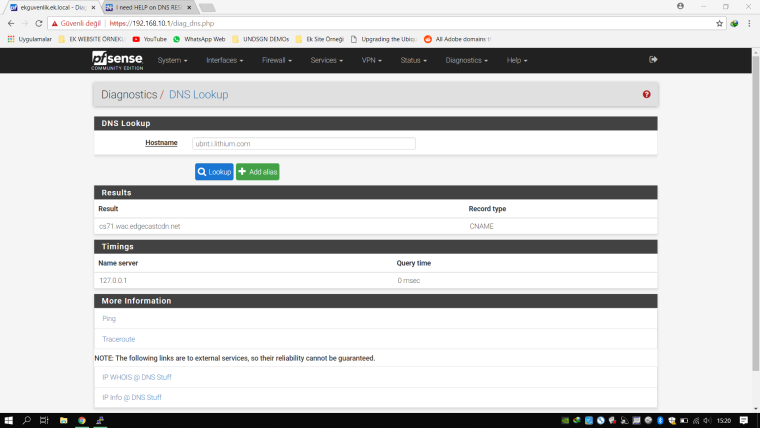
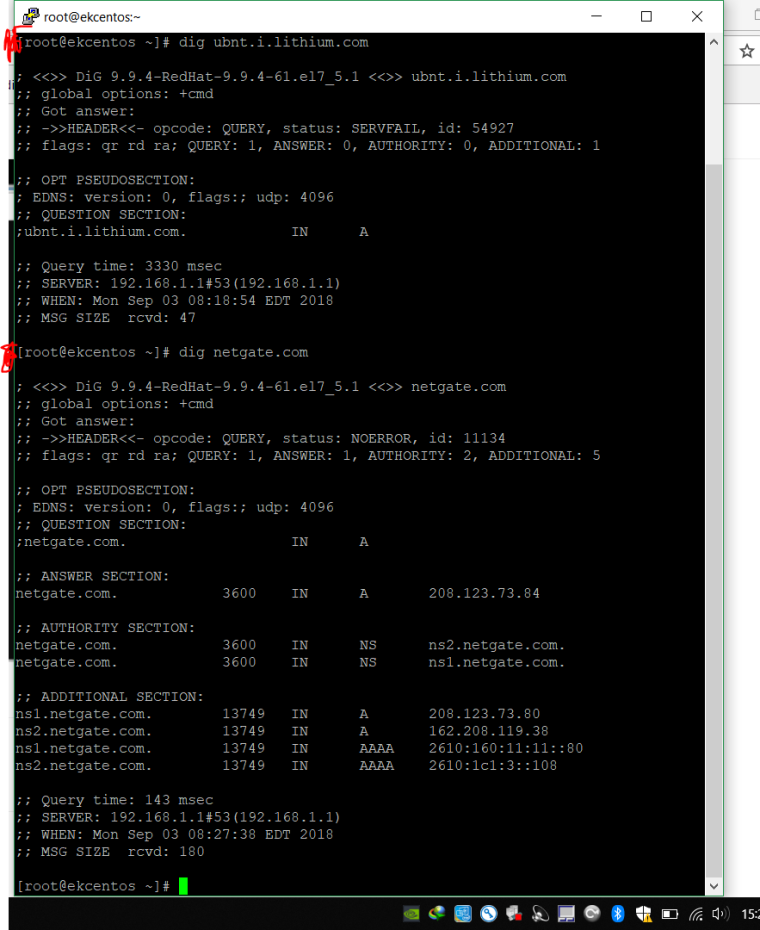
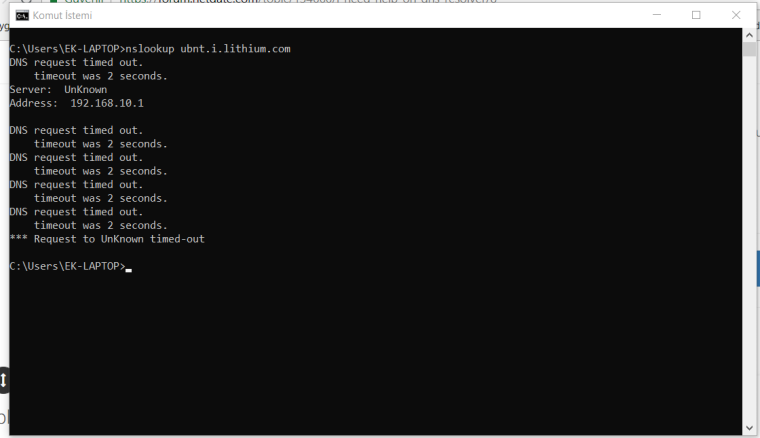
-
Test also this : https://zonemaster.iis.se/?resultid=1bec49eac0feafc5
I guess the zone "ubnt.i.lithium.com" is a mess ......
https://zonemaster.iis.se/?resultid=4308ec04d38fcb73 seems ok -
@gertjan @johnpoz Huh thanks but PfSense box can solve it. Interfaces cannot solve him.
Note: Devices at LAN and WLAN can solve hostname with google dns. But If I point unbound. They cant cannot solve hostname.EDIT: No one needs this information but I want to give it. I can solve "i.lithium.com" and "lithium.com" on LAN and WLAN
-
I know ;)
From my pfSense and one Windows PC, it resolves just fine - although I got back an IP like 72.21.91.97
and after that another IP : 93.184.220.97I went to Services => DNS Resolver Advanced => Settings => Log level and set it to level 3.
Result : https://pastebin.com/51vZi2xX which proofs my Resolver received the requests from my Windows device, and unbound starts to doing "the thing ....".
Btw : my LAN and other OPTx firewall rules :
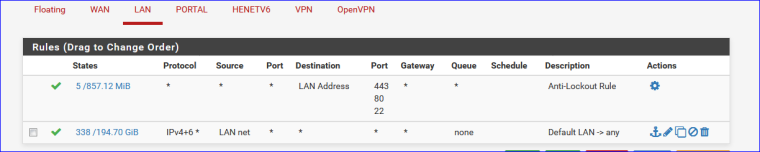
-
Hehe I caught something nice in logs. @Gertjan @johnpoz @yellowbrick
I think dns resolver can solve domain. But It cannot stream it to local network. because its cname when I look dns resolver logs. no output about "cs71.wac.edgecastcdn.net" no one try to reach server. They are stuck on "ubnt.i.lithium.com" after that I try to solve "cs71.wac.edgecastcdn.net" on LAN side and pfsense dnslookup and you will see screenshots below no one can solve this hostname pfsense box too.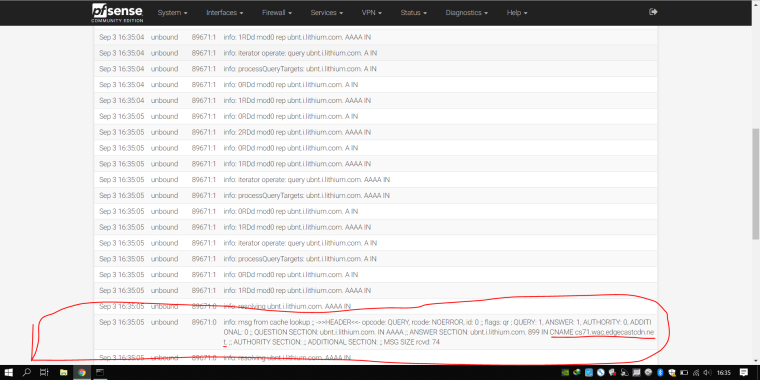
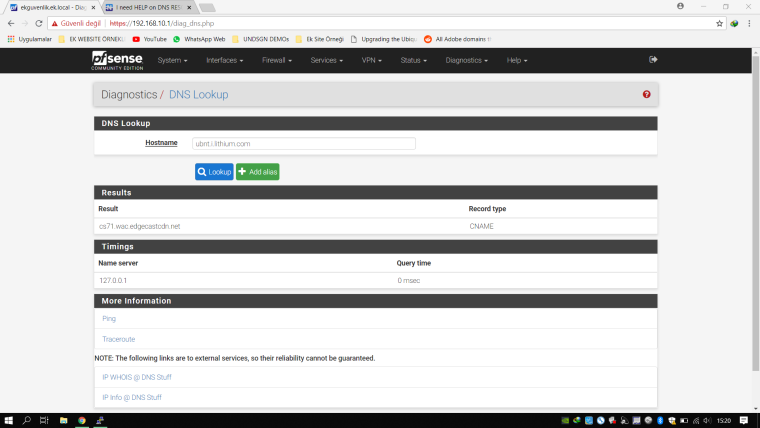
After that I try ping and nslookup and dig to "cs71.wac.edgecastcdn.net" on lan, wlan side no one can reach because box cannot solve this hostname. But Im getting logs about this now domain.
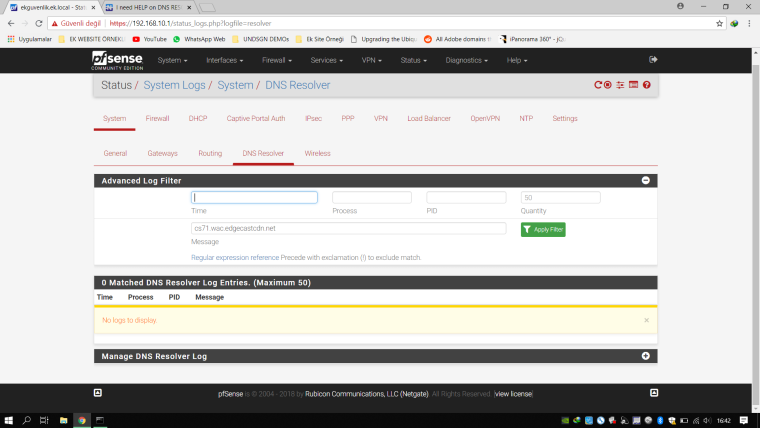
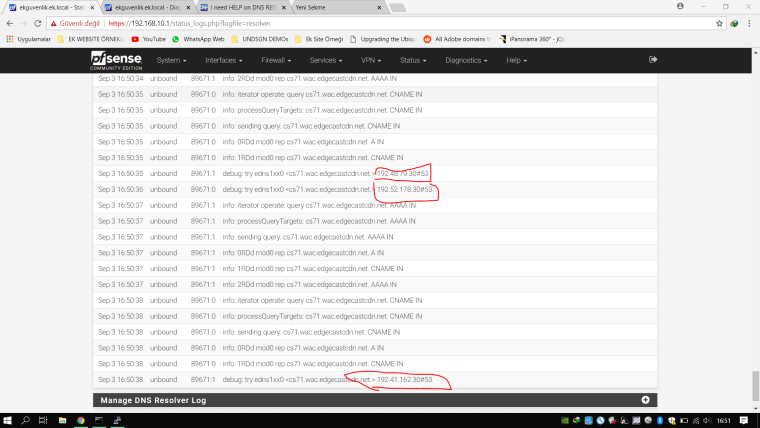
In this logs I get this IP and I cannot found something usefull same outputs everywhere related this hostname. Then I try to reach this IP.
PING ON PFSENSE BOX:
PING 192.41.162.30 (192.41.162.30): 56 data bytes
64 bytes from 192.41.162.30: icmp_seq=0 ttl=54 time=63.971 ms
64 bytes from 192.41.162.30: icmp_seq=1 ttl=54 time=63.075 ms
64 bytes from 192.41.162.30: icmp_seq=2 ttl=54 time=63.915 ms
--- 192.41.162.30 ping statistics ---
3 packets transmitted, 3 packets received, 0.0% packet loss
round-trip min/avg/max/stddev = 63.075/63.654/63.971/0.410 msTHEN I TRY TRACEROUTE ON PfSense Box:
1 81.212.171.204.static.turktelekom.com.tr (81.212.171.204) 5.063 ms 8.821 ms 5.137 ms
2 93.155.0.146 (93.155.0.146) 5.936 ms 5.808 ms 5.478 ms
3 81.212.108.162.static.turktelekom.com.tr (81.212.108.162) 5.954 ms 6.220 ms 6.479 ms
4 16-bursa-h2-1---16-bursa-t3-3.statik.turktelekom.com.tr (81.212.244.145) 6.501 ms 7.990 ms 6.530 ms
5 00-gayrettepe-xrs-t2-1---16-bursa-h2-1.statik.turktelekom.com.tr (81.212.248.78) 14.719 ms 14.797 ms 14.508 ms
6 305-vie-col-3---00-gayrettepe-xrs-t2-1.statik.turktelekom.com.tr (212.156.140.116) 57.184 ms
305-vie-col-3---00-gayrettepe-xrs-t2-1.statik.turktelekom.com.tr (212.156.140.188) 54.735 ms 62.927 ms
7 83.231.187.25 (83.231.187.25) 59.980 ms 59.758 ms 60.243 ms
8 ae-3.r01.vienat01.at.bb.gin.ntt.net (129.250.2.37) 57.501 ms 58.023 ms 57.462 ms
9 ae-7.r25.amstnl02.nl.bb.gin.ntt.net (129.250.2.111) 62.239 ms 61.583 ms 71.028 ms
10 ae-8.r03.amstnl02.nl.bb.gin.ntt.net (129.250.2.109) 62.696 ms 62.066 ms 62.185 ms
11 81.20.65.178 (81.20.65.178) 61.976 ms 61.782 ms 61.981 ms
12 * * *
13 * * *
14 * * *
15 * * *
16 * * *
17 * * *
18 * * *
EDIT: TurkTelekom is My ISP(Its little dirty. Our team is working on office.)Resolver log: https://pastebin.com/1db0p7wt
I Can "81.20.65.178" reach it but I think it isnt related with edgecast. I think Its for dns stufs. Im stuck in here If you need more informaiton or logs please tell me I need to fix that issue
-
Guys @Gertjan @johnpoz @yellowbrick I need your help? Nothing fixed yet.
-
@emirefek said in I need HELP on DNS RESOLVER!:
ubnt.i.lithium.com"
Did another test just now :
Flushed dns on my PC.
Flushed Resolver cache (by setting log details to level 2).
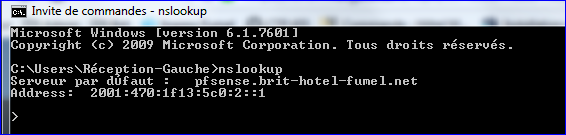
On my PC :C:\Documents and Settings\Gertjan.BUREAU>ipconfig /flushdns Configuration IP de Windows Cache de résolution DNS vidé. C:\Documents and Settings\Gertjan.BUREAU>nslookup Serveur par dÚfaut : pfsense.brit-hotel-fumel.net Address: 192.168.1.1 > ubnt.i.lithium.com Serveur : pfsense.brit-hotel-fumel.net Address: 192.168.1.1 Réponse ne faisant pas autorité : Nom : cs71.wac.edgecastcdn.net Address: 93.184.220.97 Aliases: ubnt.i.lithium.com.This is what pfSense told me (read from bottom to top) :
09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: query response was nodata ANSWER 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: reply from <lithium.com.> 208.74.204.2#53 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: response for ns4.lithium.com. AAAA IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: Verified that unsigned response is INSECURE 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: NSEC3s for the referral proved no DS. 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: Verified that unsigned response is INSECURE 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: NSEC3s for the referral proved no DS. 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: query response was ANSWER 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: reply from <edgecastcdn.net.> 72.21.80.6#53 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: response for ubnt.i.lithium.com. A IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: query response was REFERRAL 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: reply from <net.> 2001:503:231d::2:30#53 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: response for ubnt.i.lithium.com. A IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: query response was nodata ANSWER 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: reply from <lithium.com.> 208.94.148.13#53 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: response for ns5.lithium.com. AAAA IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: resolving net. DNSKEY IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: resolving ubnt.i.lithium.com. A IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: query response was CNAME 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: reply from <lithium.com.> 208.80.124.13#53 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: response for ubnt.i.lithium.com. A IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: resolving ns4.lithium.com. AAAA IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: resolving ns5.lithium.com. AAAA IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: query response was REFERRAL 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: reply from <com.> 192.43.172.30#53 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: response for ubnt.i.lithium.com. A IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:45 unbound: [96547:0] info: resolving com. DNSKEY IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:45 unbound: [96547:0] info: resolving ubnt.i.lithium.com. A INLooks good to me. Not sure when reading the logs, but nslookup on my PC gave an answer.
Check if you have the same.
If some device (PC) doesn't show DNS logs on pfSense, then that device has no DNS (so : no answer!) or that device doesn't use pfSense as a DNS. -
They do have a bit of a problem to be honest with their setup... So the roots for .net only show 2 NS for that domain
dig @e.gtld-servers.net edgecastcdn.net NS ; <<>> DiG 9.9.5-3ubuntu0.17-Ubuntu <<>> @e.gtld-servers.net edgecastcdn.net NS ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 16422 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 2, ADDITIONAL: 5 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;edgecastcdn.net. IN NS ;; AUTHORITY SECTION: edgecastcdn.net. 172800 IN NS ns1.edgecastcdn.net. edgecastcdn.net. 172800 IN NS ns2.edgecastcdn.net. ;; ADDITIONAL SECTION: ns1.edgecastcdn.net. 172800 IN AAAA 2606:2800:1::5 ns1.edgecastcdn.net. 172800 IN A 72.21.80.5 ns2.edgecastcdn.net. 172800 IN AAAA 2606:2800:1::6 ns2.edgecastcdn.net. 172800 IN A 72.21.80.6 ;; Query time: 17 msec ;; SERVER: 2001:502:1ca1::30#53(2001:502:1ca1::30) ;; WHEN: Tue Sep 11 12:39:14 CDT 2018 ;; MSG SIZE rcvd: 168But if you ask the SOA for that domain for its NS.. you get back 4 of them.
dig @ns1.edgecastcdn.net edgecastcdn.net NS ; <<>> DiG 9.9.5-3ubuntu0.17-Ubuntu <<>> @ns1.edgecastcdn.net edgecastcdn.net NS ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 22695 ;; flags: qr aa rd; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 9 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;edgecastcdn.net. IN NS ;; ANSWER SECTION: edgecastcdn.net. 3600 IN NS ns1.edgecastcdn.net. edgecastcdn.net. 3600 IN NS ns2.edgecastcdn.net. edgecastcdn.net. 3600 IN NS ns3.edgecastcdn.net. edgecastcdn.net. 3600 IN NS ns4.edgecastcdn.net. ;; ADDITIONAL SECTION: ns1.edgecastcdn.net. 172800 IN AAAA 2606:2800:1::5 ns2.edgecastcdn.net. 172800 IN AAAA 2606:2800:1::6 ns3.edgecastcdn.net. 3600 IN AAAA 2606:2800:e::5 ns4.edgecastcdn.net. 3600 IN AAAA 2606:2800:e::6 ns1.edgecastcdn.net. 172800 IN A 72.21.80.5 ns2.edgecastcdn.net. 172800 IN A 72.21.80.6 ns3.edgecastcdn.net. 3600 IN A 192.229.254.5 ns4.edgecastcdn.net. 3600 IN A 192.229.254.6 ;; Query time: 10 msec ;; SERVER: 2606:2800:1::5#53(2606:2800:1::5) ;; WHEN: Tue Sep 11 12:41:52 CDT 2018 ;; MSG SIZE rcvd: 292This really shoudn't stop you from resolving - but it does reflect a lack of proper dns control..
Did you run the dig +trace command pfsense?
[2.4.3-RELEASE][root@sg4860.local.lan]/: dig cs71.wac.edgecastcdn.net +trace +nodnssec ; <<>> DiG 9.11.2-P1 <<>> cs71.wac.edgecastcdn.net +trace +nodnssec ;; global options: +cmd . 485599 IN NS f.root-servers.net. . 485599 IN NS d.root-servers.net. . 485599 IN NS i.root-servers.net. . 485599 IN NS g.root-servers.net. . 485599 IN NS c.root-servers.net. . 485599 IN NS e.root-servers.net. . 485599 IN NS l.root-servers.net. . 485599 IN NS h.root-servers.net. . 485599 IN NS k.root-servers.net. . 485599 IN NS j.root-servers.net. . 485599 IN NS m.root-servers.net. . 485599 IN NS a.root-servers.net. . 485599 IN NS b.root-servers.net. ;; Received 239 bytes from 127.0.0.1#53(127.0.0.1) in 0 ms net. 172800 IN NS a.gtld-servers.net. net. 172800 IN NS b.gtld-servers.net. net. 172800 IN NS c.gtld-servers.net. net. 172800 IN NS d.gtld-servers.net. net. 172800 IN NS e.gtld-servers.net. net. 172800 IN NS f.gtld-servers.net. net. 172800 IN NS g.gtld-servers.net. net. 172800 IN NS h.gtld-servers.net. net. 172800 IN NS i.gtld-servers.net. net. 172800 IN NS j.gtld-servers.net. net. 172800 IN NS k.gtld-servers.net. net. 172800 IN NS l.gtld-servers.net. net. 172800 IN NS m.gtld-servers.net. ;; Received 846 bytes from 2001:500:1::53#53(h.root-servers.net) in 106 ms edgecastcdn.net. 172800 IN NS ns1.edgecastcdn.net. edgecastcdn.net. 172800 IN NS ns2.edgecastcdn.net. ;; Received 177 bytes from 192.5.6.30#53(a.gtld-servers.net) in 39 ms cs71.wac.edgecastcdn.net. 3600 IN A 72.21.91.97 ;; Received 69 bytes from 72.21.80.5#53(ns1.edgecastcdn.net) in 11 ms [2.4.3-RELEASE][root@sg4860.local.lan]/:This will tell you if pfsense would have a problem with resolving it.. I added the +nodnssec option to make the trace look cleaner - ie not include the dnssec info that roots and .net servers hand out
-
Things didn't get any better this morning : https://zonemaster.iis.se/?resultid=87deb85f04a58f9e
@emirefek : what about testing google.com *** ? So we can focus on your issues, not the one of the guy with severe DNS problems ?
*** well, maybe google.com isn't perfect neither. This one is.
-
@johnpoz
I typed your commands one by one and these are my outputs. And all outs from pfsense boxes comand promptdig @e.gtld-servers.net edgecastcdn.net NS
; <<>> DiG 9.11.2-P1 <<>> @e.gtld-servers.net edgecastcdn.net NS ; (2 servers found) ;; global options: +cmd ;; connection timed out; no servers could be reacheddig @ns1.edgecastcdn.net edgecastcdn.net NS
dig: couldn't get address for 'ns1.edgecastcdn.net': not founddig cs71.wac.edgecastcdn.net +trace +nodnssec
; <<>> DiG 9.11.2-P1 <<>> cs71.wac.edgecastcdn.net +trace +nodnssec ;; global options: +cmd . 24997 IN NS m.root-servers.net. . 24997 IN NS g.root-servers.net. . 24997 IN NS a.root-servers.net. . 24997 IN NS j.root-servers.net. . 24997 IN NS l.root-servers.net. . 24997 IN NS d.root-servers.net. . 24997 IN NS k.root-servers.net. . 24997 IN NS b.root-servers.net. . 24997 IN NS i.root-servers.net. . 24997 IN NS h.root-servers.net. . 24997 IN NS c.root-servers.net. . 24997 IN NS f.root-servers.net. . 24997 IN NS e.root-servers.net. ;; Received 811 bytes from 127.0.0.1#53(127.0.0.1) in 0 ms ;; connection timed out; no servers could be reachedthese are my results. I dont know but I cannot solve that damn domain.
And little info my setup on vmware esxi with pppoe -
@Gertjan I can solve this domain mate. This output from pfsense box.
dig test-domaine.fr
; <<>> DiG 9.11.2-P1 <<>> test-domaine.fr ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 38644 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;test-domaine.fr. IN A ;; ANSWER SECTION: test-domaine.fr. 10092 IN A 5.196.43.182 ;; Query time: 0 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) ;; WHEN: Fri Sep 14 12:56:48 +03 2018 ;; MSG SIZE rcvd: 60 -
Logic
 I'm the DNS administrator of that domain.
I'm the DNS administrator of that domain.But your test tells me that your Resolver (DNS) works fine.
For what it's worth : when you setup pfSense (that is : assign LAN, WAN) and then you set up your WAN interface any device on your LAN should be able to access the net with any troubles.
Initially : do not touch firewall rules, VLAN's, DNS, nothing.Btw : again : you are not responsible for not resolving of sub domains. The fact that something works on this side of the planet doesn't mean it isn't broken on your side.
Seek contact with the guy that manages ubnt.i.lithium.com - or put in a DNS host over ride. -
looks to me like you can not talk to roots..
-
@johnpoz I can talk with blabla.root-servers.net. I try 5 or 6 of them with random choose.
-
Then why does your trace not get an answer back ??
You should of gotten back the next level - the NS for .net when you did your trace..
example
net. 172800 IN NS k.gtld-servers.net.
net. 172800 IN NS l.gtld-servers.net.
net. 172800 IN NS m.gtld-servers.net.
;; Received 846 bytes from 2001:500:1::53#53(h.root-servers.net) in 106 msMine talked via ipv6 when I did the trace - but ipv4 would do the same thing.. You just stopped at roots..
How did you test talking to them - a ping or an actual dns query?
example
C:\>dig @m.root-servers.net net NS ; <<>> DiG 9.12.2 <<>> @m.root-servers.net net NS ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 23008 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 13, ADDITIONAL: 27 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;net. IN NS ;; AUTHORITY SECTION: net. 172800 IN NS m.gtld-servers.net. net. 172800 IN NS i.gtld-servers.net. net. 172800 IN NS a.gtld-servers.net. net. 172800 IN NS h.gtld-servers.net. net. 172800 IN NS k.gtld-servers.net. net. 172800 IN NS b.gtld-servers.net. net. 172800 IN NS c.gtld-servers.net. net. 172800 IN NS l.gtld-servers.net. net. 172800 IN NS g.gtld-servers.net. net. 172800 IN NS d.gtld-servers.net. net. 172800 IN NS j.gtld-servers.net. net. 172800 IN NS f.gtld-servers.net. net. 172800 IN NS e.gtld-servers.net. ;; ADDITIONAL SECTION: a.gtld-servers.net. 172800 IN A 192.5.6.30 b.gtld-servers.net. 172800 IN A 192.33.14.30 c.gtld-servers.net. 172800 IN A 192.26.92.30 d.gtld-servers.net. 172800 IN A 192.31.80.30 e.gtld-servers.net. 172800 IN A 192.12.94.30 f.gtld-servers.net. 172800 IN A 192.35.51.30 g.gtld-servers.net. 172800 IN A 192.42.93.30 h.gtld-servers.net. 172800 IN A 192.54.112.30 i.gtld-servers.net. 172800 IN A 192.43.172.30 j.gtld-servers.net. 172800 IN A 192.48.79.30 k.gtld-servers.net. 172800 IN A 192.52.178.30 l.gtld-servers.net. 172800 IN A 192.41.162.30 m.gtld-servers.net. 172800 IN A 192.55.83.30 a.gtld-servers.net. 172800 IN AAAA 2001:503:a83e::2:30 b.gtld-servers.net. 172800 IN AAAA 2001:503:231d::2:30 c.gtld-servers.net. 172800 IN AAAA 2001:503:83eb::30 d.gtld-servers.net. 172800 IN AAAA 2001:500:856e::30 e.gtld-servers.net. 172800 IN AAAA 2001:502:1ca1::30 f.gtld-servers.net. 172800 IN AAAA 2001:503:d414::30 g.gtld-servers.net. 172800 IN AAAA 2001:503:eea3::30 h.gtld-servers.net. 172800 IN AAAA 2001:502:8cc::30 i.gtld-servers.net. 172800 IN AAAA 2001:503:39c1::30 j.gtld-servers.net. 172800 IN AAAA 2001:502:7094::30 k.gtld-servers.net. 172800 IN AAAA 2001:503:d2d::30 l.gtld-servers.net. 172800 IN AAAA 2001:500:d937::30 m.gtld-servers.net. 172800 IN AAAA 2001:501:b1f9::30 ;; Query time: 77 msec ;; SERVER: 202.12.27.33#53(202.12.27.33) ;; WHEN: Fri Sep 14 08:03:45 Central Daylight Time 2018 ;; MSG SIZE rcvd: 825