How to assign Domain Controller to VLAN Systems
-
Hi,
Myself Lokesh Kamath.
We have below mentioned configuration with 8 Network Ports.
- WAN - 203.xxx.xxx.xxx
- LAN - 192.168.20.1
- Fin-VLAN - 192.1968.30.1
- Marketing-VLAN - 192.168.40.1
- Purchase-VLAN - 192.168.50.1
- Toolroom-VLAN - 192.168.60.1
In the above configuration Domain Controller with Active Directory in LAN.
Primary DC 1 - 192.168.20.100
Secondary DC 2- 192.168.20.102Apart from DC there are 2 software's running in DC1 (Tally & Salary Soft - Finance Software)
Windows Systems are there in Fin-VLAN & Toolroom-VLAN
How can give LAN-DC 1 & 2 access to Fin-VLAN & Toolroom-VLAN. Also that software's to Fin-VLAN?
Tally work on Port # 9000 & 9999
Salary Soft Don't know the port #I tried below configuration.
I have created DC 1 & DC 2 alias.
In Fin-VLAN firewall rules i set any source from Fin-VLAN any port to Destination DC1 & DC2 to any port. This is not working (I may be wrong in creating rules).
So please guide me.
Thanks in advance
Lokesh Kamath
-
It sounds like you had it mostly right, but perhaps you made an error when creating your rules. Try again, and if it doesn't work then post a screenshot of your VLAN rules.
-
@kom
Thanks for your response.I tried that but no luck.
Firewall Fin-VLAN Rules
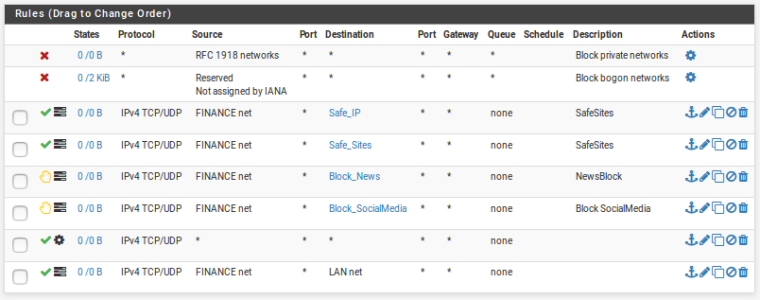
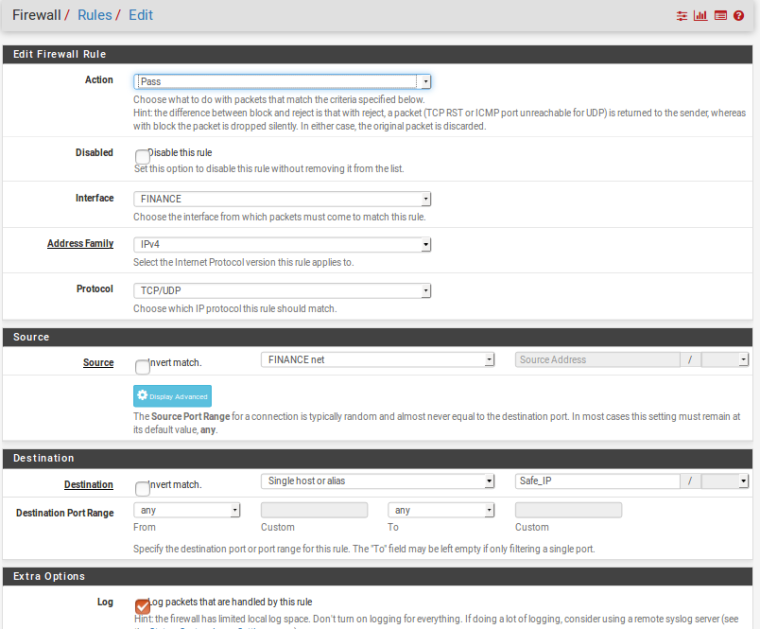
Fin-VLAN Edit
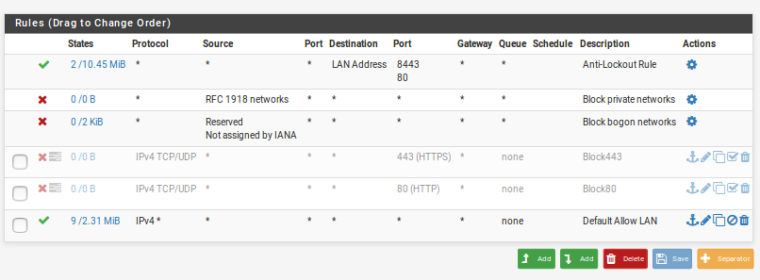
Firewall LAN Rules
Lokesh Kamath
-
What is this Finance network? I thought it was Fin-VLAN? Try changing it to 'any'. Are your domain controllers in any of those aliases for sure?
-
Why are you blocking rfc1918 and bogon on lan side interfaces? With rfc1918 blocked your not going to be able to talk to any vlans no matter what rules you put on the interfaces.
-
Thanks for your response.
@KOM Finance Network means - Fin-VLAN. Domain Controller, Backup Server, Network Printer, Network Shared Server, File Server all these System IP's are there in the Alias.
@johnpoz - I will remove that block and I will check.
Also I created Gateway for all the VLANS apart from WAN Gateway. Giving Gateway for all - Is this correct?
WAN Gateway - 203.xxx.xxx.xxx
LAN Gateway - 192.168.10.1
Fin-VLAN-Gateway - 192.168.20.1
Marketing-VLAN-Gateway - 192.168.40.1
Purchase-VLAN-Gateway - 192.168.50.1
Toolroom-VLAN-Gateway - 192.168.60.1Lokesh Kamath
-
@slkamath said in How to assign Domain Controller to VLAN Systems:
Also I created Gateway for all the VLANS apart from WAN Gateway
NO!!!
Your telling pfsense the gateway to get to network xyz is itself?? NO!! there is no gateways setup on pfsense to talk to networks its directly attached too..
Think about it for 2 freaking seconds.. How would 192.168.20 talk to 192.168.40 --- BOTH rfc1918 if you have rule that says hey BLOCK rfc1918 source from talking anywhere..
Rules are evaluated as traffic enters an interface from the network its attached too, first rule to trigger wins, no other rules are evaluated... You have a rule right at the top that says hey your blocked!! No other rules are even looked at.
And where could it EVER be possible to see a bogon as source on your own freaking network? Do you even understand what a bogon is? Why are you blocking it? You do understand rfc1918 is part of bogon ;) Pfsense pulls it out of the bogon table - but it is by definition a bogon. So You have 2 rules that state - HEY.. 192.168.x.x - your Blocked... So from those rules NOTHING would work, you couldn't even ask pfsense for dns with those rules.
-
@johnpoz
Thank You Very Much.I removed the RFC1918 and also I removed all the Gateway for VLAN.
Thank you so much. Now VLAN is talking with LAN.
Every now & then they need to disconnect network & re-connect then only mails or shared server is working. Is that any rules issue?
For that purpose i hive given access to all the Mails port (143, 993, 110, 465, 25, 995)
Marketing-VLAN
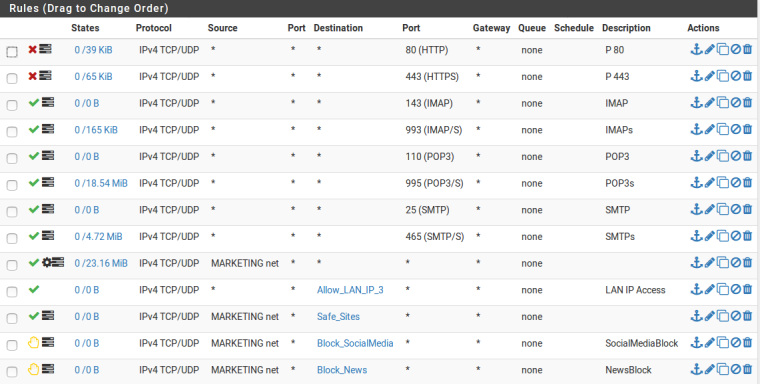
Purchase-VLAN
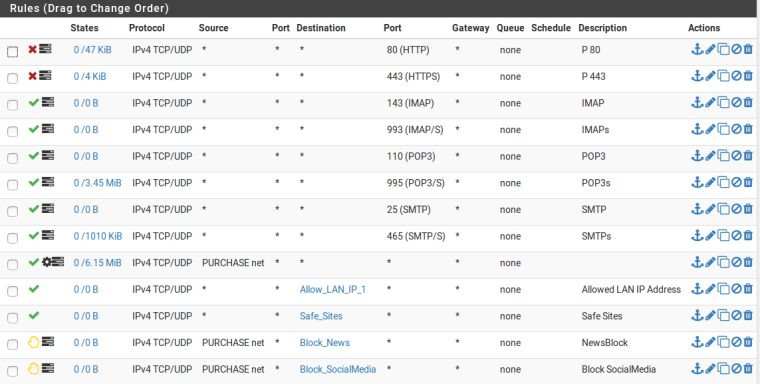
Fin-VLAN is working apart Finance Software Tally. It says The Tally Server is not in the same Gateway
Tally Server is in LAN. Tally Users are in Fin-VLAN
Tally Server IP - 192.168.10.100 (ODBC Server port 9000, Tally Port 9999)
Fin-VLAN - 192.168.20.50So any guidance.
Lokesh Kamath
-
You don't seem to understand how rules work. Rules are evaluated TOP down.. First rule to trigger wins and NO OTHER rules are evaluated.
All of those allow rules are pointless because you have that allow purchase net tcp/udp any rule..
And then you have 2 rules below that allow to specific sites?
How would you ever get to the reject rules?
-
@johnpoz
Thank you very much.What i understood was it will check 1st rule if it is not matching will go to 2nd like that so on. If the rule is not specified or not matching i thought it will be blocked.

Based on the idea given by you i have did few changes. Please correct me if i am wrong.
Fin-VLAN
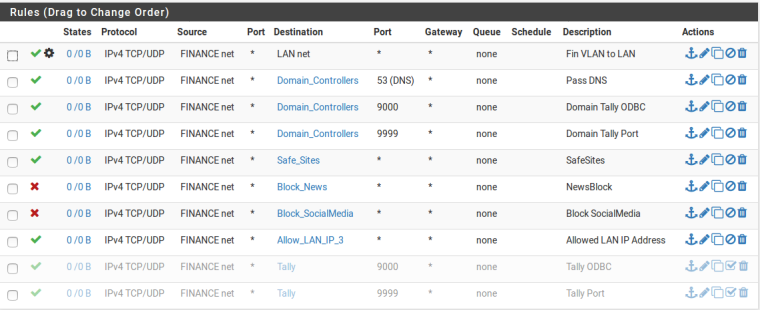
Marketing-VLAN
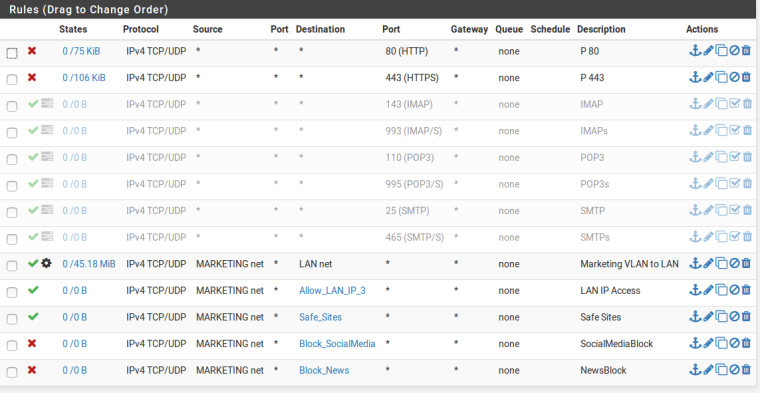
Purchase-VLAN
Quality-VLAN
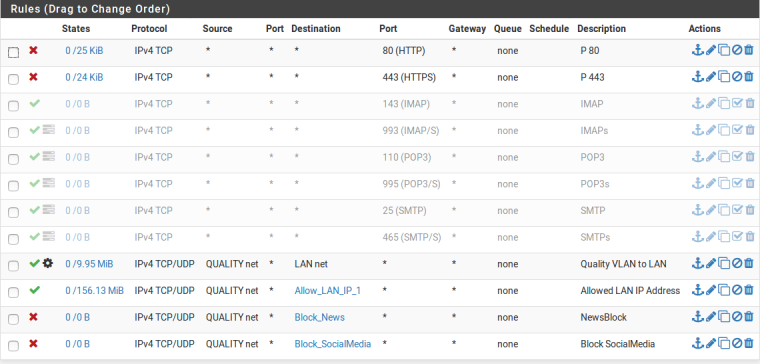
Allow Specific Sites are the sites of Government Sites which is required for few departments. Due to block of News & Social Media (Squid Guard) few sites will not work so created alias and allowing it (Don't know this is right or wrong).
I thought if the rule is not specified means it will reject directly. No idea how to reject other than that. I think I am having very poor knowledge.

Lokesh Kamath
-
@slkamath said in How to assign Domain Controller to VLAN Systems:
What i understood was it will check 1st rule if it is not matching will go to 2nd like that so on.
Exactly - but what is the point of allowing X, above a rule that allows ALL? And blocking something below a rule that allow ALL will never be evaluated.
And yes there is a default deny that is not shown - so if you run through your rules and its not allowed then it will be blocked.
Your block rules on the end of your quality net are pointless.. They would just be blocked by the default deny if not allowed above. So unless you wanted to specifically log them or reject them vs just deny those rules are pointless.
What option do you have set in that allow to lan net? The gear symbol. That rule makes no sense because it allows all lan net, so what is the point of allowing to a specific lan IP?
-
@johnpoz
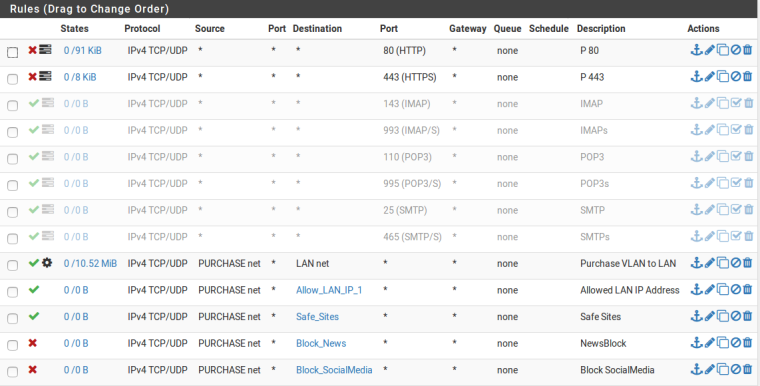
Thank you very much.How to put default deny rule (please find the pic below is it correct)?
Again did some changes.
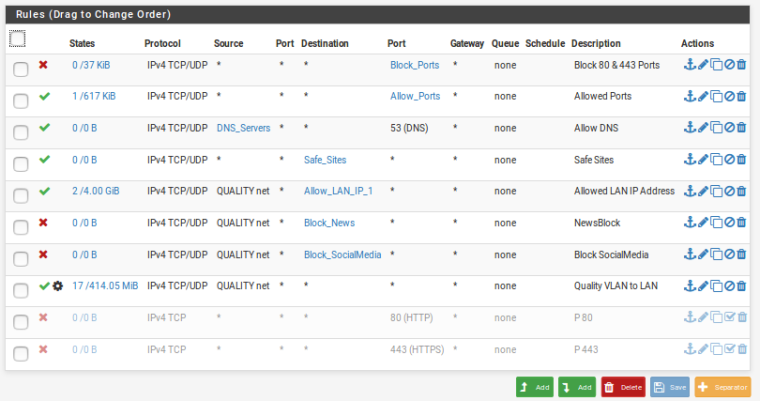
Quality-VLAN
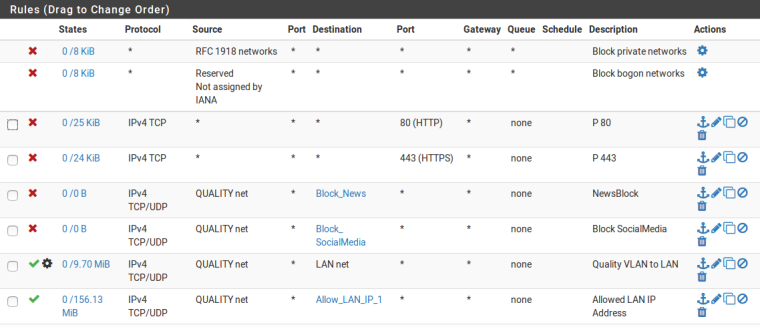
Gear Symbol is for Upload & Download limit set so it shows that symbol. In LAN there are nearly 10 IP's. All VLAN has to access those IP's (Shared Folder, Network Printer, Backup, Domain Controller, Tally).
LAN
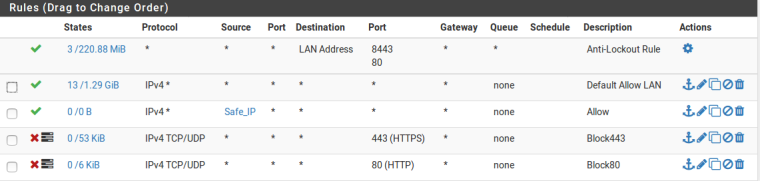
Can you suggest any book or something so that i will get some knowledge to make it correct.
Lokesh Kamath
-
I suggest reading this chapter from the pfSense book:
https://www.netgate.com/docs/pfsense/book/firewall/firewall-fundamentals.htmlSteve
-
@stephenw10
Thank you Stephen. -
Did you post the wrong pic - your qual ne has the block rfc1918 and bogon again..
Your lan rules everything below your any any is just pointless!! Not sure why this is so difficult to understand..
Imagine a source IP:PORT and DESTIP:PORT and protocol - now run through your rules top to bottom.
You have an ANY ANY rule - any protocol and source any dest.. So when would that rule not trigger and get to the safe_IP rule??
When would something not trigger that any any rule and fall through to your block rules? Your any any allows ANY, so
clearly ports 80 and 443 are part of ANY..If you don't want IPs getting to 80/443 then those rules go ABOVE your any any rule.. Those will then be blocked and other ports like say 123 would not trigger those rules and be allowed through the any any rule.
-
@johnpoz
Thank you Very MuchSorry for the delay.
I made few changes. Please have a look. Also any mistake please guide me.
LAN - Allow Browsing is only for 5 IP's
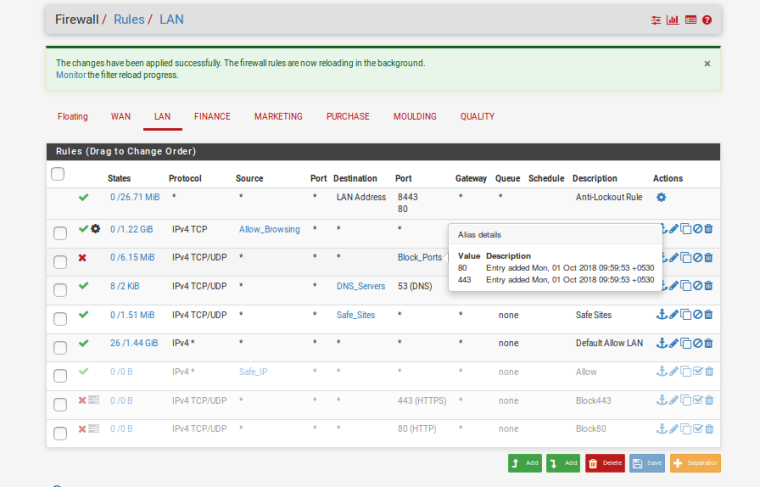
LAN-UPDATED
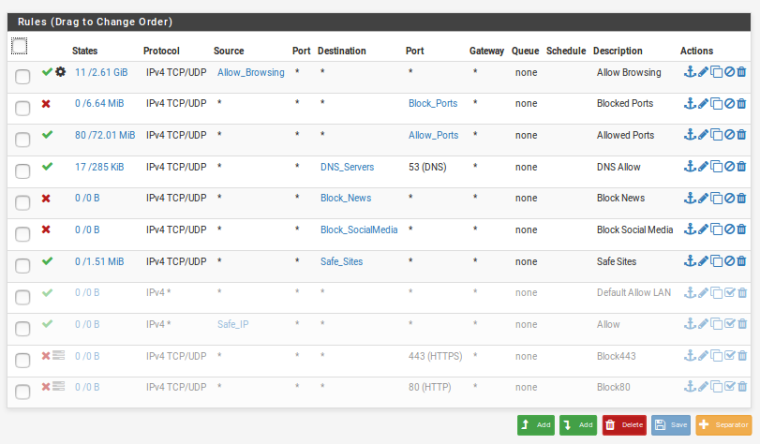
Fin-VLAN
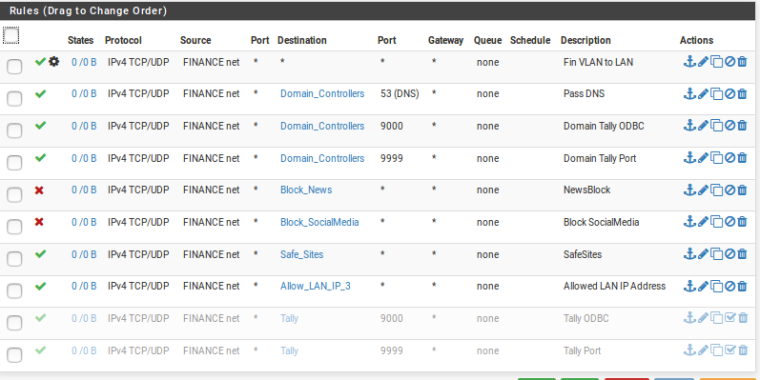
Marketing-VLAN
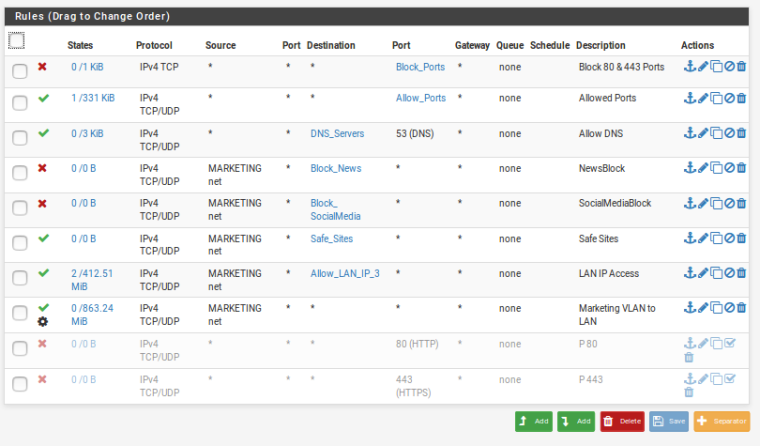
Quality-VLAN
One more issue that i am facing is
All the VLAN systems need to Disable & Enable the network to Send/Receive Mails or Accessing Shared Folder else share folder or mails will not work. (timeline of 2 to 5 min we need to disable & enable network) Where I need to change this?Lokesh Kamath
-
Looks like you still have an allow all rule on the Fin-VLAN interface that will catch all traffic before it hits any of the other rules.
Steve
-
@stephenw10
Thank you Stephen.I will change the Fin-VLAN. Thanks. Other VLAN is correct?
Lokeh Kamath
-
Well they don't look immediately wrong. Without knowing exactly what you need to do I can't say more than that.
Steve
-
Thank You Very Much Steve.
One more issue that i am facing is
All the VLAN systems need to Disable & Enable the network to Send/Receive Mails or Accessing Shared Folder else share folder or mails will not work. (timeline of 2 to 5 min we need to disable & enable network) Where I need to change this?Lokesh Kamath