IPsec VTI with Palo Alto
-
Hello,
I'm testing the IPsec VTI feature with pfSense 2.4.5 dev and a Palo Alto firewall.
An existing tunnel with a vyatta router is working. The tunnel with pfSense not.
The difference is on the requestes phase 2 sa. The pfSense tries to create a phase 2 with the public ips.
Sep 27 09:51:13 charon 05[KNL] received an SADB_ACQUIRE with policy id 8 but no matching policy found Sep 27 09:51:13 charon 05[KNL] creating acquire job for policy x.y.z.251/32|/0 === x.y.z.250/32|/0 with reqid {0} Sep 27 09:51:13 charon 05[CFG] trap not found, unable to acquire reqid 0The vyatta creates a tunnel with 0.0.0.0/0:
src 0.0.0.0/0 dst 0.0.0.0/0 dir out priority 2051 ptype main mark 9437185/0xffffffff tmpl src x.y.z.68 dst x.y.z.234 proto esp reqid 16408 mode tunnel src 0.0.0.0/0 dst 0.0.0.0/0 dir fwd priority 2051 ptype main mark 9437185/0xffffffff tmpl src x.y.z.234 dst x.y.z.68 proto esp reqid 16408 mode tunnel src 0.0.0.0/0 dst 0.0.0.0/0 dir in priority 2051 ptype main mark 9437185/0xffffffff tmpl src x.y.z.234 dst x.y.z.68 proto esp reqid 16408 mode tunnelHas anyone an idea?
Thanky, Martin
-
Normally it would not request a P2 with the public IP addresses. P1, sure, but not P2. Not unless you accidentally put the public addresses in the VTI P2 settings where the internal tunnel endpoints should be.
-
Hello,
I already tried to add the wan ips to Palo Altos phase 2 - no success.
Regards
Martin -
@msnetworks you should NOT add the WAN IPs to the phase 2 configuration. For phase 2 configuration you should choose an unused /30 network and configure your tunnel interfaces with two IPs out of this network.
-
Hello,
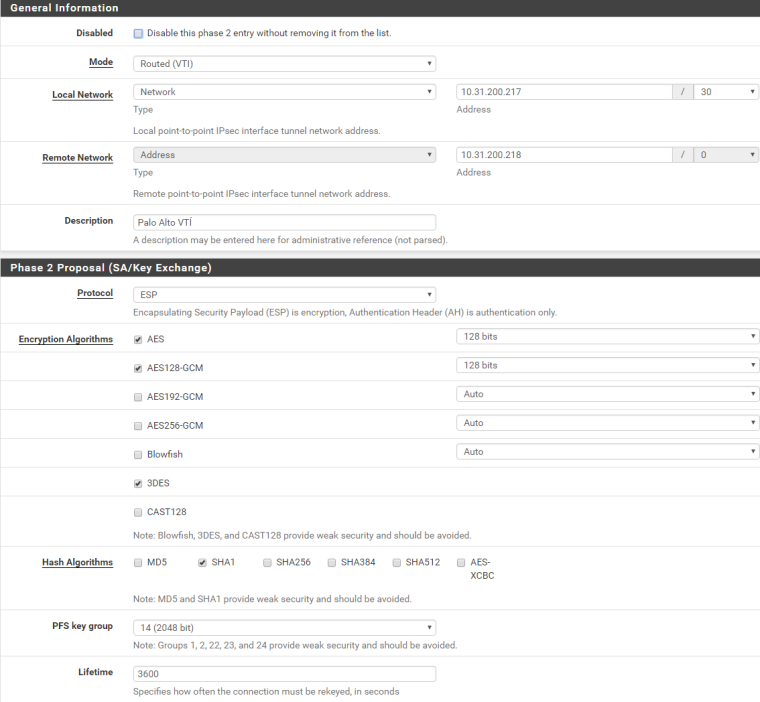
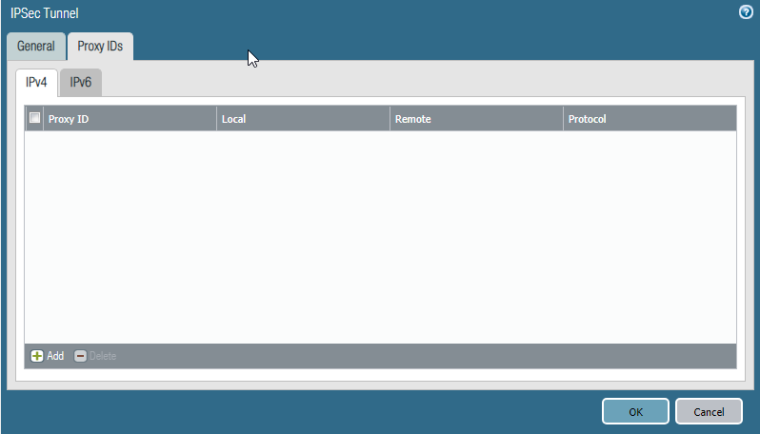
I have not configured an explicit phase 2. The proxy id section is empty.
The tunnel interfaces on pa and pfsense have both an ip address from an /30 network.
pfsense net + 1 and pa net + 2.I also checked the whole phase 2 settings.
Phase 1 comes up - but phase two not.

Regards,
Martin -
Hello,
pfSense should send a phase 2 proxy id with 0.0.0.0/0-0.0.0.0/0 to PA, but doesn't do it.
I think this is a bug?
Regards,
Martin -
Try the attached patch and see if it helps. I could not get the VTI to come up and pass traffic with only
0.0.0.0/0in therightsubnetandleftsubnet, but it did seem to connect and work with the attached patch that has both the VTI endpoints and all zeroes. I haven't testing to see if it interferes with anything else yet, though, just VTI itself (BGP connects and exchanges routes, traffic passes)0_1538745996158_ipsec-vti-0.0.0.0.diff
Use the System Patches package to apply the diff, or make the changes by hand. After applying the patch, stop IPsec, then edit/save/apply the IPsec VTI P1 or P2 and it should restart with the new policy in place.
-
Hello,
a first test was successfull. I will test it this weekend.
Thank you!
-
Hello,
the fix is working perfect with psk mode.
Is it possible to use the fix with certificate-based ipsec?
Regards,
Martin -
Try it and see?
-
@msnetworks said in IPsec VTI with Palo Alto:
the fix is working perfect with psk mode.
Is it possible to use the fix with certificate-based ipsec?
These changes only affect IPsec Phase 2 (IPsec SA), so your Phase 1/IKE/ISAKMP settings won't matter for this. So long as they match the other end properly it should work.
-
Hi,
I've tested it with certificate based authentication and ikev2. Everything works fine.
Thank you.
-
I think this is possibly also an issue with fortigates, interestingly in that scenario the tunnel comes up and works for a while then dies.
I notice an error in the phase2 where the pfsense end is sending the IP of the tunnel (172.xxx.xxx.xxx) instead of 0.0.0.0
Trying the patch although I'm not sure if that actually helped as I'm seeing a lot of
07[KNL] <con1000|1> querying policy 0.0.0.0/0|/0 === 0.0.0.0/0|/0 in failed, not foundI'm using a CARP/VIP for the VPN so that might complicate things further.
Edit: Removed the strict interface binding I'd set earlier when troubleshooting It's up at the moment but we will see if it dies again.Edit2: Seems I had a misconfigured DH group in the phase2 on the fortigate side, not actually sure how that even worked on first connect with that problem present.
-
@dragon2611 said in IPsec VTI with Palo Alto:
I think this is possibly also an issue with fortigates, interestingly in that scenario the tunnel comes up and works for a while then dies.
i have the same problem.
i create a VTI between two Pfsense 2.4.4-p1 and Pfsense 2.4.4-p2.
I add static route and policies in LAN site for remote subnet.
Tunnel goes up, i can ping from both side then after some time (may be one or two minutes) it's down but it' come back after some time...I check P1 and P2 for encryption, all is right.
-
@yathus said in IPsec VTI with Palo Alto:
@dragon2611 said in IPsec VTI with Palo Alto:
I think this is possibly also an issue with fortigates, interestingly in that scenario the tunnel comes up and works for a while then dies.
i have the same problem.
it's solved. I had a static route using same subnet on remote side.
I used a different subnet for VTI and IPSec is stable now.I put MSS on VTI Interface too, don't know if it's required or not.
-
@Yathus what was your mss setting?
-
I wouldn't put any settings in unless you know they are needed. Lowering MSS might reduce throughput (increase packets-per-second for the same payload) for no reason.
-
I'm using 1200 as MSS because it's required by my datacenter (DoS Protection)