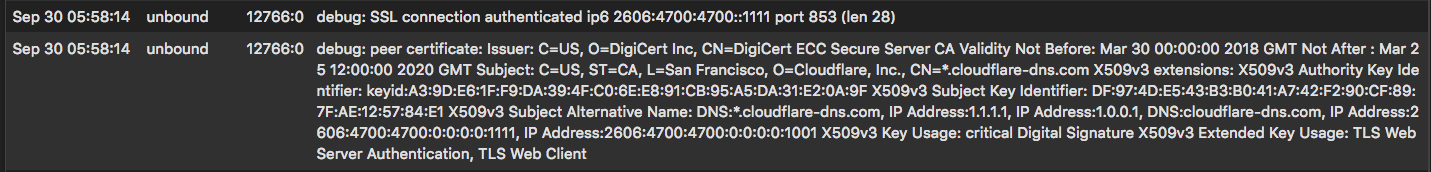
DNS over TLS with SSL validation is working in 2.4.4-RELEASE!!!
-
Unbound in 2.4.4-RELEASE has apparently been updated to a version containing the new code to check certificates on peers when using DNS over TLS. To activate this functionality, the following should be added to the custom options section:
server:
tls-cert-bundle: /usr/local/share/certs/ca-root-nss.crtThere should be a toggle in the GUI to activate this option.
Here is what a validation looks like with logging set to "4" and newest entries first:
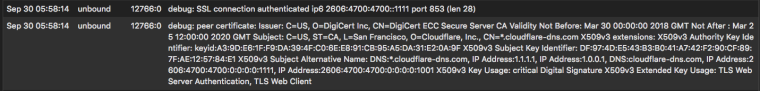
Reference:
https://www.ctrl.blog/entry/unbound-tls-forwarding -
It looks nice but it isn't actually doing anything. It won't reject a failure like it should.
See https://redmine.pfsense.org/issues/8030
It silently approves everything, even if it doesn't match.
-
Yes, this is true, but I'm excited to see that things are moving in the right direction. It is still possible to confirm certs visually in the logs. This feature will be a huge asset when the code matures. I'm not sure how fast the features will make it into pfSense absent another rebase. I'm hoping that FreeBSD sees fit to propagate the code back, but I don't know their policies on backporting features like that.